Half a year has skyrocketed nearly four times, and Bitcoin has broken the $11,000 mark! But if you don't understand these things, you will…
Half a year ago, it was still worth $3,200 in bitcoin, and now it has broken the $11,000 mark! Accompanied by the fact that each altcoins also rose.
But if you don't understand the common problems with these blockchains mentioned in this article, even if you have more digital assets , it's futile , because it turns out that current digital assets are not safe.
This article describes common problems in many blockchain areas that are expected to plague beginners in the blockchain. The basic content includes the following aspects:
- Deep Interpretation of the White Paper – Move: A New Programming Language for Facebook Libra Blockchain
- Zhu Jiaming as the chief of the digital economy leader class | strong mentor lineup, waiting for nothing
- PoS, DPoS, PBFT… Innovation consensus, PoW is outdated?
Blockchain security issues
1, 51% attack problem
What are the 51% attacks we often hear?
In fact, the core of the problem is that there must be more than half of the computing power to be able to "double flower" the assets on the chain. Below we give an example. If we imagine that one of the ten people is trying to deceive and modify the contents of the blockchain, he will have to adjust several blocks and calculate a new hash value that matches the difficulty goal. We know that it is very difficult to find a hash that meets the criteria, so a dishonest person on the network cannot beat nine honest people.
If a dishonest person tries to deceive in a block, it creates another chain in the network, but the deceptive chain can never catch up with the honest chain—because one's efforts and speed cannot beat nine people Accumulated effort and speed. Therefore, this mechanism ensures that the longest chain in the network is the most honest chain.
But if not one person is dishonest, but six people are dishonest? In this case, tampering with the records on the blockchain can be achieved. This is called "51% attack." If most people on the network become dishonest and deceive the rest of the network, the purpose of the agreement is no longer valid. But we must be aware of the weaknesses of the blockchain system: it is built on the assumption that most people are always honest.
2, witch attack
Large-scale P2P systems face the threat of problematic and hostile nodes. To cope with this threat, many systems use redundancy. However, if a malicious entity mimics multiple identities, it can control a large part of the system and undermine the system's redundancy strategy. We define this attack that mimics multiple identities as "Sybil Attack." In a witch attack, an attacker destroys the reputation system of a peer-to-peer network by creating a large number of pseudonym identifiers, which are used to achieve a disproportionately large impact.
An entity on a peer-to-peer network is a piece of software that has access to local resources. The entity advertises itself on the peer-to-peer network by presenting the identity. More than one identity may correspond to a single entity. In other words, the identity-to-entity mapping is many-to-one. Entities in peer-to-peer networks use multiple identities for redundancy, resource sharing, reliability, and integrity.
By default, it is generally assumed that each different identity corresponds to a different local entity. In fact, many identities can correspond to the same local entity. In this way, an attacker can present multiple identities to a peer-to-peer network, act as multiple different nodes, and may be able to obtain disproportionate levels of control over the network, such as affecting voting results.
Witch attacks include the following six types:
- Direct communication: The witch node communicates directly with the legitimate node.
- Indirect communication: There is no legal node that can communicate directly with the witch node. Instead, one or more malicious nodes declare that they can reach the witch node. It is this malicious node that receives or intercepts related messages by itself.
- Forged identity: An attacker can generate any witch identity to attack.
- Theft of identity: The attacker's identity theft of the node is difficult to detect before the original node is destroyed or invalidated.
- Simultaneous attack: The attacker participates in all network communication at the same time with all of his witch identities. An attacker can recycle its multiple witch identities, making it appear to be multiple nodes. This is simultaneity.
- Non-simultaneous attacks: The attacker uses only a part of the witch identity in a specific time period, and in another time period, these identity disappears and appears as another witch. This looks like normal nodes in the network are undone and joined.
The traditional way to prevent witch attacks is to use a trusted agent to authenticate the entity.
Verification techniques can be used to prevent witch attacks and eliminate camouflage enemy entities. Local entities can authenticate remote identities based on a centralized authority, which ensures a one-to-one correspondence between identities and entities, and can even provide reverse lookups. Identity can be verified directly or indirectly. In direct verification, the local entity queries the central authority to verify the remote identity. In indirect verification, the local entity relies on the accepted identity, which in turn guarantees the validity of the remote identity in question.
This approach does not apply to decentralized public chains. In blockchains such as PoW as a consensus mechanism, such as Bitcoin or Ethereum, the use of computing power is the basis for obtaining billing rights, so the multi-node witch attack loses its meaning. Blockchains such as PoS-based consensus mechanisms, such as dot-coin, use the age of the currency to obtain the basis for billing rights. Similarly, multi-node witch attacks also have no effect.
3. Exchange
The vast majority of current digital exchanges are centralized, and their security risks are very large, and can basically include human security and technical system security loopholes. These exchanges have become the target of hackers because they store a large amount of cryptocurrency. The following are several well-known exchange security incidents, indicating that there are serious security risks in digital exchanges.
- In March 2018, the world's second-largest exchange was hacked, resulting in the sale of bitcoin in a large number of user accounts and the purchase of a virtual currency; hackers also arbitrarily arbitrarily circumvented bitcoin in major exchanges around the world. Although the hacker did not directly withdraw coins from the currency, it caused the book loss of the currency intrusion into the account, and indirectly caused the book loss of a large number of bitcoin holders.
- In January 2018, Coincheck, Japan's largest cryptocurrency exchange, was attacked by hackers, and the $530 million digital currency was missing.
- In December 2017, the South Korean bitcoin exchange Youbit lost 17% of its digital currency and declared bankruptcy due to a “hacking attack”.
Basically all exchange systems face technical security risks. There are six types of security issues:
- system security;
- Hardware device security;
- Trading channel security;
- Digital wallet security;
- Terminal security;
- User operation is safe.
At the same time, many projects have begun to develop decentralized exchanges operating in the blockchain. Compared to centralized technology, decentralized exchanges operating on blockchains use the three characteristics of the blockchain—distributed, transparent, and non-tamperable—to enhance the security and transparency of the exchange.
(1) Centralized exchange
Centralized Exchange is actually the exchange that users mainly use. Bitfinex, Poloniex, Coincheck, and currency security are all centralized exchanges. The way users use these exchanges is usually to register on the website. After a series of certification procedures according to the regulations of different countries, after the cryptocurrency is transferred to their designated wallet address, they can start trading cryptocurrency on it.
The transaction does not necessarily occur in the real currency exchange on the blockchain. Instead, it may only modify the asset numbers in the exchange database. What the user sees is only the change in the number on the book. The exchange only needs to withdraw the money from the user. Prepare enough cryptocurrency for export.
When the user transfers the cryptocurrency to the wallet address they provide, the exchange has the right to operate the cryptocurrency. The user must trust the site to ensure currency security in order to transfer the cryptocurrency to the exchange.
Because the centralized exchange has a private key that holds a large amount of cryptocurrency, it is very easy to attract hackers. The hacker's goal is mostly the private key that stores a large amount of cryptocurrency. Stealing these private keys means stealing these cryptocurrencies.
(2) Decentralized exchange
The most different aspect of a decentralized exchange from a general centralized exchange is that trading takes place on the blockchain. The transaction with the centralized exchange is essentially the addition or subtraction of the user asset field in the exchange's own database. The decentralized exchange is directly exchanged on the blockchain, and the cryptocurrency is sent directly back to the user's wallet. Or a smart contract saved on the blockchain.
The advantage of this direct exchange on the blockchain is that the exchange does not hold a large amount of cryptocurrency for the user, and all cryptocurrencies are stored in the user's wallet or smart contract control on the blockchain. Originally, you need to trust the centralized exchange, and now you only need to trust the blockchain and smart contracts. Most of the smart contracts used on exchanges will be open source so that everyone can confirm the details of the contract.
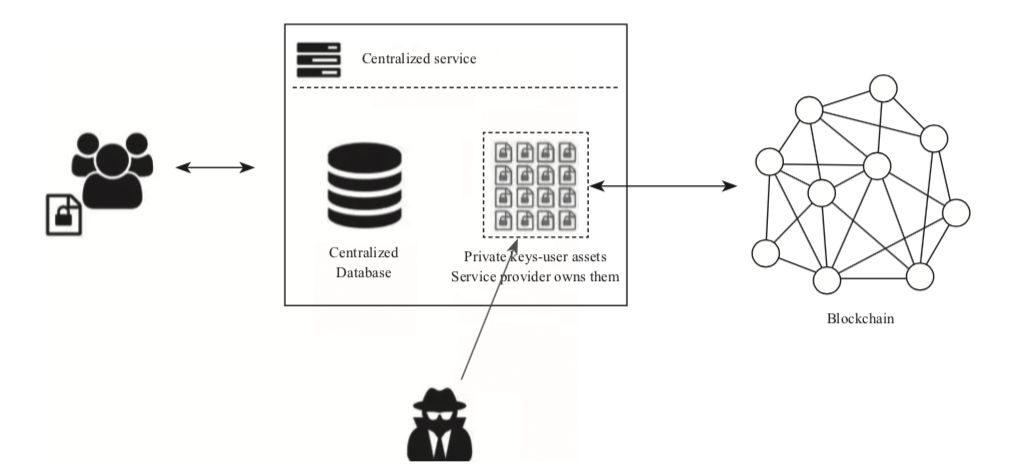
Centralized exchange technical structure
Centralized exchanges usually do not disclose the source code of the transaction details, and how it actually works is only known to its internal staff. By maintaining the transparency and security of the trading process through open smart contracts, profitable splits are also disclosed in the blockchain. I believe that users will gradually turn to decentralized exchanges because of trust issues.
There are already several decentralized exchanges in the world, such as EtherDelta and the Kyber Network, which are relatively early start-up exchanges. Due to the short time of development and operation, they are still not mature enough and need to be gradually improved. Compared with centralized exchanges, one of the weaknesses of decentralized exchanges is that there is no matching engine and the transaction efficiency is low.
4, Ethereum smart contract security vulnerability
Traditional computer programs typically run on a node or cluster and are owned and controlled by an organization or individual. Such computer programs can be manually manipulated at any time and can be controlled at any time. However, smart contracts on the blockchain are a new computing paradigm. Once a smart contract is deployed, it is difficult to modify and its execution is automatically performed without human intervention. Therefore, if a smart contract has a security hole, it is difficult to prevent hacker attacks. At the moment, professional and technical personnel are striving to find the right way to improve the safety and reliability of smart contracts and help to ensure the safety of everyone's funds. According to a recent survey of Ethereum smart contracts, in the eyes of security researchers, smart contracts are new, so there are still many flaws and vulnerabilities.
The so-called "smart contract", the basic connotation is that some contractual nature of the terms can be embedded in the hardware and software we use every day, in order to let those defaulters pay a price when they violate the contract. Szabo refers to the physical vending machine as the “prototype of smart contracts” because the physical vending machine collects the coins that the user has invested according to the price displayed on the screen, drops the products selected by the user and correctly corrects the changes.
Take Ethereum as an example. Ethereum is an open source public blockchain platform with smart contract functionality. Smart contracts based on blockchains can be seen by all users on the blockchain. However, this can result in all vulnerabilities, including security holes, being visible. If the smart contract developer is negligent or under-tested, and the code of the smart contract is flawed, it is very easy to be exploited and attacked by the hacker. And the more powerful the smart contract, the more complex the logic, and the more likely it is to have a logical loophole. At the same time, the smart contract language Solidity itself and the contract design may have loopholes.
Ethereum open source software is mainly written by community geeks. Currently, there are known vulnerabilities such as Solidity Vulnerabilities, Short Address Vulnerabilities, Transaction Order Dependencies, Timestamp Dependencies, and Reentrant Attacks. Vulnerabilities may be exploited when the contract is invoked, and features that are difficult to update after the smart contract is deployed also make the impact of the vulnerability more widespread and durable.
In addition, the Ethereum Virtual Machine (EVM) has many hard limits on what smart contracts can do. These all involve platform-level security and may even threaten the security of a user-specific contract.
According to computer scientist Ilya Sergey of University College London, professional and technical personnel are not fully aware of the security vulnerabilities and potential risks in smart contracts. He has been involved in a survey of smart contracts. Sergey and colleagues analyzed nearly 1 million Ethereum smart contract samples with an innovative tool. It was found that about 34,000 of them were safety hazards, including the one that led to the Parity incident. Sergey said that the analysis work of himself and other members of the team is like interacting with vending machines. The researchers randomly pressed a button and then recorded the condition of the machine in the event of an accident during operation. In his words: "I think there are still many security vulnerabilities that we have not found so far, and we need to continue to analyze and classify them."
How to improve the security of smart contracts in practice? Give the following suggestions, try to comply with the actual programming, your contract will be more secure.
- More complete writing tests.
- It is recommended to provide fault tolerance and automatic error bounty.
- Prepare for the worst situation. Vulnerabilities in smart contracts should be as safe as possible to recover.
- Add additional security mechanisms. The manager of the contract can freeze the contract in an emergency.
- Limit the amount of contract funds deposited to raise the threshold for successful attackers.
- Don't write all your code from scratch, and refer to the winner's contract as much as possible.
- Pay attention to the limitations of the development platform.
5. Test indicators for blockchain security
The security of blockchain mainly examines six aspects: identity authentication, access control, encryption system and privacy, cryptographic algorithm, anonymity and anti-attack capability. The following is a specific test indicator analysis.
- Authentication: Authentication mainly tests 5 indicators: the way of authentication, the scenario of authentication, the prevention of identity fraud, private key management, and the entry and exit of nodes require authentication.
- Access Control: The access control mainly tests 7 indicators: different levels of account permissions, different classification account permissions, super account permissions, account-to-account authorization, account authorization time limit control, account permission change, and permission change form.
- Encryption system and privacy: The encryption system and privacy mainly test four indicators: transaction information encryption, signature application scenarios, private key storage for signature use, and private key loss to protect user property.
- Cryptographic algorithm: The cryptographic algorithm mainly tests 4 indicators: cryptographic algorithm type, national secret algorithm, encryption machine, pluggable custom cipher algorithm.
- Anonymity: Anonymity mainly tests 5 indicators: whether the transaction is anonymous, all anonymous or partially anonymous, the sub-account keeps the transaction transparent to its parent account, the sub-account keeps the transaction anonymous to other parent accounts, and the transaction is transparent to the audit or super-privileged account.
- Anti-attack capability: The anti-attack capability mainly tests 4 indicators: defend against DDoS, hacker and other network attacks, anti-attack capability, maximum tolerated node failures, and maximum tolerant node spoofing.
Technical limitations of blockchain
1, blockchain impossible triangle
The blockchain system cannot achieve the three goals of complete decentralization, security, and scalability at the same time. How do you understand that?
The so-called "completely decentralized" means that every node in the network can access resources of the order of O(c). c is the computing resource that each node in the system can have, including computing power, bandwidth, and storage. O is the symbol for complexity. O(c) means that the complexity is equivalent to c multiplied by a constant. That is to say, the nodes are completely equal in the network, and there is no centralized node monopoly resource. Security refers to the ability to protect O(n) multiple resources. n is the size of an abstract ecosystem. Extensibility refers to the ability to process O(n) transactions, where O(n)>O(c) is required. To understand, if you want to be able to handle O(n) transactions while protecting O(n) resources, you can only concentrate on a few nodes, otherwise it will bring competition for resources and expand the attack surface.
None of the current blockchain platforms can achieve the goal of complete decentralization, security and scalability at the same time. Bitcoin is designed to provide a secure decentralized electronic cash system, so it sacrifices transaction performance. Ethereum is similar to Bitcoin, and it also uses a completely decentralized design, which is faster than Bitcoin, but the security is relatively poor. EOS, BTS and other transactions are faster, but the degree of decentralization is greatly reduced, becoming part of the decentralized system.
2, data redundancy
The inherent redundancy mechanism of the blockchain makes it robust and error-tolerant. Each node saves a complete block of data, even if some nodes fail, it will not cause the entire network to collapse. At the same time, the node of the downtime will always synchronize the new transaction correctly after restarting. On the other hand, the data is indeed n times more redundant than traditional centralized systems, where n is the number of full nodes in the network.
Therefore, the blockchain is actually a technology that has a certain cost to apply. If the application can't create more value through the blockchain than the centralized system, it is not suitable for blockchain technology.
3, blockchain security
Another common question is, is data safe in the blockchain? First of all, we declare that there is no absolute security in this world. Only relative security, the relationship between spear and shield always exists.
It can be said that the blockchain is an upgraded version of the current Internet security and has higher security than the traditional Internet. Blockchain is the underlying technology in Bitcoin. On the traditional Internet that cannot establish trust, blockchain technology relies on cryptography, distributed consensus algorithms and cleverly designed incentives without the intervention of any third-party central organization. Mathematical methods enable participants to reach a consensus, ensure the existence of transaction records, the validity of contracts and the non-repudiation of transactions, and greatly improve the security of the system.
But the fiery market of digital currency based on blockchain has made hackers covet and the amount of stolen money keeps on record. The incidence of theft has also raised concerns about the security of digital currency?
With the research and application of blockchain technology, the blockchain system will face unique security challenges due to its characteristics, in addition to the threats of malicious programs such as viruses and Trojans and large-scale DDoS attacks. .
Mainly reflected in the following aspects.
(1) Algorithm implementation security
Due to the extensive application of various cryptography techniques in the blockchain, it is a highly intensive algorithm and is prone to problems in implementation. There have been such precedents in history. For example, the NSA in the United States has embedded flaws in the RSA algorithm, making it easy to crack other people's encrypted information. Once this level of vulnerability breaks out, it can be said that the foundation of the entire building that constitutes the blockchain will no longer be safe and the consequences will be terrible. Bitcoin theft incidents caused by problems with the Bitcoin random number generator have occurred before. In theory, if the random number is not sufficiently random, the private key can be derived by collision.
(2) Consensus mechanism security
A variety of consensus algorithm mechanisms have emerged in current blockchain technologies, the most common being PoW, PoS, and DPoS. But whether these consensus mechanisms can achieve and guarantee true security requires more rigorous proof and time test.
(3) Blockchain security
A major feature of blockchain technology is that data on the chain cannot be tampered with and cannot be forged, but only if the private key is secure. The private key is generated and kept by the user, and in theory there is no third party involved. Once the private key is lost, it loses its corresponding digital asset. Once caught by a hacker, the corresponding digital assets can be transferred. Most of the current security issues arise in the theft of private keys.
(4) System design security
Some platforms are vulnerable to DoS attacks due to a single point of failure in their business design. The blockchain is currently decentralized, and most exchanges are centralized. Centralized exchanges, in addition to preventing external hackers from stealing, must manage internal employees to prevent theft of internal employees. In addition, the system's business design flaws may also be exploited by hackers.
So how to ensure the security of the blockchain?
In order to ensure the security of the blockchain system, it is recommended to refer to NIST's network security framework to construct five cores for identification, protection, detection, response and recovery from the perspective of the strategic level, the entire life cycle of a company or organization's network security risk management. Components to perceive and block blockchain risks and threats. Focus on algorithms, consensus mechanisms, use and design security.
- Security is implemented for the algorithm: on the one hand, the cryptographic technology that has been verified for a long time is selected; on the other hand, the core algorithm code is strictly and completely tested, and the source code is confused, which increases the difficulty and cost of the hacker reverse attack.
- Security for consensus algorithms: Use more efficient consensus algorithms and strategies.
- For the security of use: protect the generation and storage of private keys, educate users on information security, and encrypt and store sensitive data.
- For design security: On the one hand, we must ensure that the design functions are as perfect as possible, such as using private key white box signature technology to prevent viruses and Trojans from extracting private keys during system operation, designing private key leakage tracking function, and minimizing private key leakage. After the loss. On the other hand, some key businesses should be designed as decentralized systems to prevent single point of failure attacks.
4. Weaknesses in mining and other consensus agreements
Each consensus agreement has weaknesses. Below we have several major consensus mechanisms to talk about this issue.
1) The proof of PoW workload is the mining that everyone is familiar with. Through the hash operation, find a random number that satisfies the rules, that is, obtain the current billing right, and issue the data that needs to be recorded in the current round. storage.
- Advantages: completely decentralized, nodes freely in and out;
- Disadvantages: At present, Bitcoin has attracted most of the world's computing power. Other blockchain applications that use the PoW consensus mechanism will find it difficult to obtain the same computing power to protect their own security; mining will cause a lot of waste of resources; Longer, not suitable for commercial applications.
Let's take Bitcoin as an example. Energy consumption is a big problem in Bitcoin mining systems. The bitcoin network is different from the general P2P network: the general P2P network nodes complement and cooperate with each other, and the P2P nodes of the bitcoin network compete and repeat each other. Regardless of the amount of transfer, each Bitcoin network node must complete all transfer operations independently and compete for access to book writes and mining rewards by making meaningless hash calculations. In other words, this is a costly and wasteful P2P network. Compared to traditional finance, its operating costs will be orders of magnitude higher. At present, the transfer of Bitcoin is only a few hundred times in ten minutes, but the amount of electricity consumed in one year can be compared with the electricity consumed by a small country like Ireland for one year.
As Bitcoin’s mining incentives are halved every four years, the miners’ demand for mining will be high in the future as bitcoin is being exhausted. Otherwise, the miners will lose power to secure the Bitcoin network; and the high fees may discourage users who want to use Bitcoin, so the future sustainable operation of the Bitcoin network may be a problem.
2) PoS is a consensus mechanism different from PoW. According to the proportion and time of each node's tokens, the difficulty of mining is reduced proportionally, thus speeding up the search for random numbers.
- Advantages: The time for consensus is shortened to a certain extent.
- Disadvantages: There is a possibility of low cost bifurcation of evil nodes, so the security is lower than PoW. In addition, since the probability of obtaining the billing right is related to the amount of money held, and the currency is issued once and distributed at one time, the fairness is worse than PoW.
3) DPoS share authorization certification mechanism. Similar to the board vote, the holders cast a certain number of nodes, and the agent performs verification and accounting.
- Advantages: Significantly reduce the number of participating verification and accounting nodes to achieve second-level consensus verification.
- Disadvantages: The centralization of the entire consensus mechanism is higher than that of pure PoS.
4) Paxos or BFT class strong consensus consensus algorithm. Based on the traditional distributed consistency technology and data verification mechanism, it is a consensus mechanism that is widely used in the industry chain.
- Advantages: It can work without tokens, and realizes second-level consensus verification based on mature distributed consistency algorithm (Pasox, Raft);
- Disadvantages: Decentralization is not as good as Bitcoin; it is more suitable for multi-center business models with multiple parties. In addition, the scalability is also limited. When the number of consensus nodes increases, the consensus performance decreases rapidly.
5, transaction speed
Blockchain technology sacrifices system speed by using distributed redundant accounting techniques, coupled with state consistency across nodes. Make the transaction speed an important factor in the chain of disease. Blockchain transaction processing speed is one of the important considerations for commercial applications.
An important measure of the blockchain's transaction volume per second is the amount of transactions per second (TPS). Its calculation formula is:
TPS = block average transaction number / block interval
Take the most commonly used PoW (PoS) as an example. There is a limit on the volume of transactions, which depends on the current internet speed of the Internet and the computing and response speed of the computer. This is because both PoW and PoS need to transfer and process information according to these times. Simply increasing the block size or reducing the time between block generations does not effectively solve the problem because the block requires time transfer verification. If the block is too large, the inconsistency of the network nodes will increase (the number of forks will increase), which will seriously affect the security and reliability. Therefore, in the blockchain of PoW or PoS, the transaction is difficult to exceed the order of 100tx/s.
The solution, in addition to improving algorithm efficiency and network transmission speed, basically increases output at the expense of decentralization and security and reliability. This is not a bad thing, because in fact many of the current consensus algorithms have more security and reliability assumptions than actual requirements.
In order to increase the volume of transactions per second, there are theoretically the following three methods.
- Increase block capacity. BCH is an example (note that the BCH block size is 8MB). If the BCH fills each block, it will generate about 400GB of blockchain data in one year. The amount of data will be large compared to Bitcoin.
- Reduce the block interval. The downside is that security is sacrificed to some extent.
- Reduce the transaction byte size. In Bitcoin design, a transaction size is about 250 to 400 bytes. If you can reduce the byte size of each transaction, you can record more transactions in one block. The record of a transaction contains transaction records and signature information. The signature information is much larger than the transaction information, and the signature information is only useful when the miner packs the transaction into blocks to verify legality. It is actually useless for non-miners. of. Therefore, the isolation test of Bitcoin actually moves the signature information outside the transaction, and does not count the block size judgment to indirectly increase the number of transactions. But all of these methods can only linearly increase the amount of transactions per second.
The change in consensus mechanism can fundamentally increase TPS to the level of over 10,000. BTS can be said to be a good example.
Still take Bitcoin as an example. The options for increasing bitcoin per second trading volume are:
- Hard fork, that is, increase the block size;
- Soft forks, which optimize the network without changing the block size (or 1MB), such as isolation witness, lightning network, side chain, etc.
The above content relates to the security of the blockchain and the technical limitations of the blockchain. In the next article, the battalion commander will continue to address the weaknesses of mining and consensus agreements , transaction efficiency issues, and system upgrade and maintenance issues . Explore, old irons please stay tuned.
Source | Blockchain Core Technology and Applications
Author | Yu Bin
Produced | Blockchain Base Camp (blockchain_camp)
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- What does the wealth of the cryptocurrency field mean?
- Bloomberg: Bitcoin bull market pushes Asian encryption-related listed companies to rise
- Ernst & Young Blockchain Supervisor: Ethereum will be the largest blockchain, and 99% of cryptocurrencies face compliance issues
- Is the Morgan coin finally coming? JPMorgan Chase announced that it will start trial operation as early as this year
- Iranian Ministry of Energy official: involved in bitcoin mining or power outage
- False websites open Libra pre-sales, fraudsters receive IQ tax
- Blockchain is an unstoppable trend, and optimists are more likely to see the future





