How to choose the cryptography technology? Preliminary Study on Security Model of Theoretical Capability Boundary
Author: Li Haoxuan
Source: Weizhong Bank Blockchain
After the system changes, why does the privacy data leak frequently? Is the new protocol formed by free combination of cryptographic algorithms still secure? Will the privacy protection system currently deployed still be valid after 10 years? Are the cryptographic protocols more secure and more in line with actual business needs?
Here, we will continue to share the selection of cryptographic technologies, from a single cryptographic algorithm to the security of a cryptographic protocol composed of multiple cryptographic algorithms, sort out related capability boundaries, and choose different protocols for privacy in actual business. Impact of protective effects.
- Babbitt Column | Bitcoin is a risky asset, and hedging properties have never really been verified in the market
- Research report | How to invest in crypto assets under extreme conditions?
- Opinion | BTC is likely to break $ 20,000 in 12 months, hedge funds begin to deploy cryptocurrencies significantly
As mentioned in the previous theory , the academic community introduced a series of security assumptions when constructing cryptographic algorithms. Only when these security assumptions are true, the corresponding cryptographic algorithm is secure. Similarly, a cryptographic protocol composed of multiple cryptographic algorithms needs to introduce more security assumptions due to the addition of more interacting parties.
For a cryptographic protocol, all the required security assumptions and the set of security requirements under the corresponding assumptions are called the security model .
Understanding the different security assumptions introduced in the security model is helpful for companies to objectively evaluate the effectiveness of alternative technical solutions when conducting cryptography-related privacy protection technology selection.
Many key security assumptions in the security model are independent of each other. The security model can be classified based on these key security assumptions to simplify the evaluation process. The three most common classifications are as follows:
-
Semi-honest vs malicious -
Versatile combination possible Versatile combination -
Computational resource irrelevant vs. computational resource related
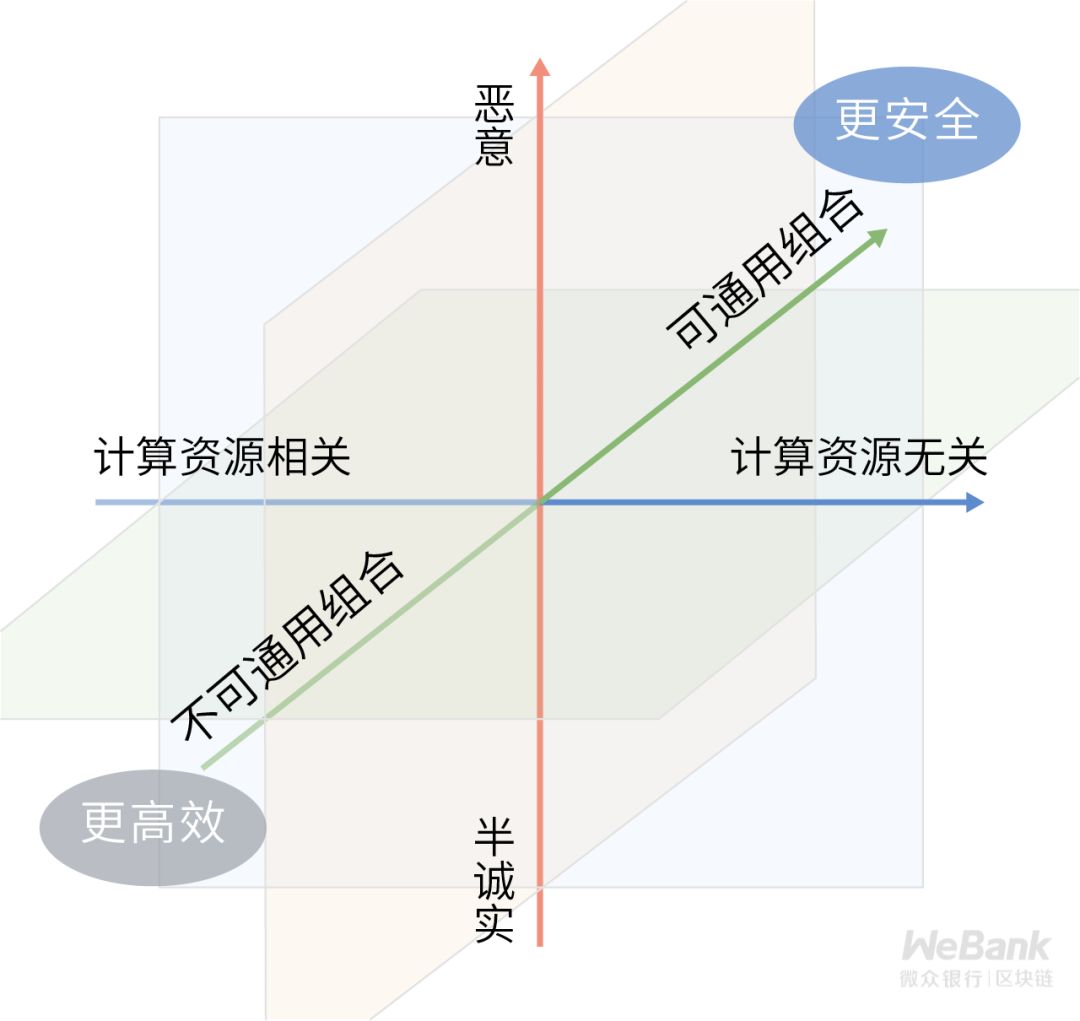
The above three classification methods are independent of each other and correspond to three dimensions in a three-dimensional coordinate axis. The following will use Xiaohua's story as a carrier to clarify the theoretical ability boundaries of cryptographic protocols one by one under the corresponding classification.
Graduation season is approaching, the protagonist Xiaohua left his hometown and came to work in the city of interest. The story between Xiaohua, the beautiful landlord, and the real estate agency begins …

Semi-honest vs malicious

When Xiaohua first arrived, the most urgent thing at the moment was to find a place where she could stay overnight. Xiaohua obtained the list of listings through an intermediary, and finally selected a set of relatively satisfactory listings. Under the cooperation of the intermediary, she contacted the landlord beautifully.
In this process, the intermediary, as a participating third party, is bound by legal norms and social ethics, and generally does not tamper with the contents of house contract rents, house information, and so on. However, the housing contract contains a large amount of personal privacy data, and the intermediary can easily obtain relevant behavior information of both parties of the lease, and there is a significant risk of privacy data leakage.

The above rental interaction agreement relies on the security assumptions that the intermediary can correctly implement the rental interaction agreement. A security model based on this type of security assumption is called a semi-honest model in cryptography, also known as an honest and curious model, or a passive attacker model.
Semi-honest model
Participants will definitely implement the cryptographic protocol correctly, but will try to extract private data from the intermediate results generated by the cryptographic protocol execution process.
At present, most cryptographic protocols use a semi-honest model. This type of security model has significant advantages in terms of efficiency and protocol design difficulty. At the same time, when most services are deployed, participants will be constrained by factors such as laws and regulations in the real world and will not conduct extreme malicious attacks.

Xiaohua expects to complete the listing matching and signing process with Meimei through the cryptographic rental agreement under the semi-honest model described above. This technical solution will effectively protect Xiaohua and beautiful identity information, rental details, etc.
However, the accident happened. The intermediary did not fulfill the agreement as promised, and with the assistance of top hackers, tampered with part of the agreement process. Xiaohua and the beautiful private data were eventually leaked.
In order to deal with the above privacy risks, it is necessary to introduce a stronger security model in cryptography-a malicious model, also known as an active attacker model.
Malicious model
Participants may not comply with the cryptographic protocol at all, and will take any means to attack the cryptographic protocol to extract private information.

Xiaohua learned the last lesson and redesigned the cryptology renting agreement based on the malicious model. Although the intermediary and his hacker companions used eighteen martial arts, they failed to break the new agreement.
Xiaohua and beautiful privacy data are finally protected, but at a high price.
Under the malicious model, constructing a secure cryptographic protocol usually requires the introduction of zero-knowledge proofs or secure multi-party interactions at every link that may be attacked. Compared with the cryptographic protocol under the semi-honest model in the same business scenario, the cost of calculation and communication and the design of the protocol itself will be much higher, and it may even become unavailable, affecting the final user experience.
The practical cryptographic privacy protection schemes have certain performance requirements. Here we need to analyze the “motivation” of attackers in specific business scenarios to choose whether to use the semi-honest model. If the attacker lacks the motivation to attack under the malicious model, such as the potential return is less than the expected return, or the attack will only harm the attacker itself, the business solution design can use the semi-honest model relatively safely.
In real business, benefiting from legal norms and social ethical constraints, the potential attack most systems face comes from threats under a semi-honest model.
In particular, business scenarios in highly regulated industries and other application scenarios with low malicious motives. Compared to the malicious model, building a privacy protection technology solution under a semi-honest model can significantly improve system performance and user experience.

Versatile combination possible Versatile combination

Xiaohua's story continues. Considering that the house may be self-occupied in the future, Meimei hopes to propose some features in the cryptographic rental agreement that support flexible changes in lease terms. This requires changes to existing technical solutions and the addition of some new cryptographic algorithm modules.
New questions follow: Is the privacy protection technology solution still effective after the change?
The two types of security models corresponding to this problem are universal combinable models and non-universal combinable models, which are usually referred to as UC models and non-UC models. UC is derived from English Universal Composable, and the corresponding definition is as follows:
Universal combination model (UC model)
The cryptographic protocols and cryptographic algorithm components used in this model meet the security requirements of UC. Through the combination theorem, these UC-secure cryptographic algorithm components can be arbitrarily freely combined, thereby constructing more complex but still secure protocols.
Non-universal combination model (non-UC model)
The cryptographic protocols under this model are modified, recombined, and split. The new protocols obtained afterwards may not have the security of the original protocols.
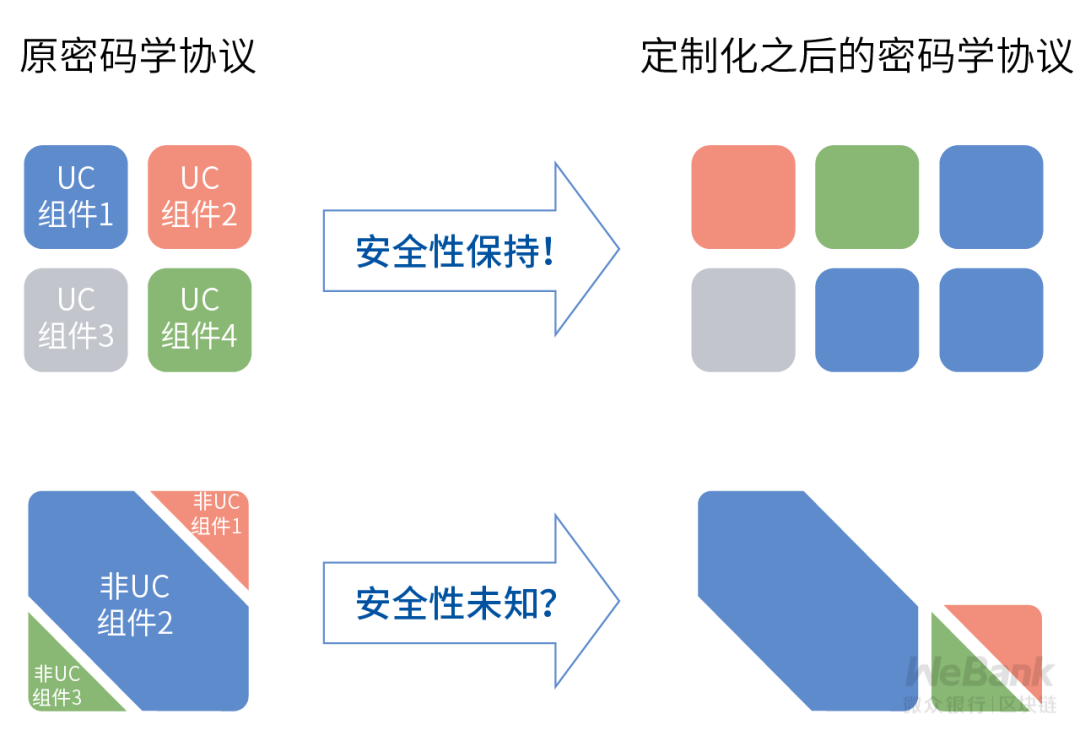
In the above Xiaohua's story, if the original cryptographic rental agreement did not meet the security requirements of the UC model, after changing the agreement according to the beautiful requirements, the new agreement is likely to be no longer secure, and a small accident may leak Xiaohua and Beautiful privacy data.
Due to the need for very rigorous certification to meet the security requirements of the UC model, the cryptographic algorithm components available under the UC model are relatively limited. Most current privacy protection technology solutions are under the non-UC model.
For businesses, the caveat here is to verify that the customization process has undermined the effectiveness of the privacy protection technology solution.
In the course of business landing, it is inevitable that in-depth customization of existing solutions is required. In the process of customizing cryptographic protocols, special attention needs to be paid to whether the changed cryptographic protocols can still provide the expected privacy protection effect of the business.

Back to Xiaohua's story again.

Xiaohua signed a five-year rental contract with Meili through a cryptographic rental agreement. In these five years, there have been many new breakthroughs in computer technology research, and the upper limit of available computing power has increased by 1 trillion times. The frustrated hacker has made a comeback, so is Xiaohua's cryptographic rental agreement at risk?
This introduces the classification of the third type of security model, that is, whether it is affected by the development of computing power.
Computational Resource Independent Model
Even if the attacker has unlimited computing resources, the cryptographic protocol is still secure.
Computing Resource Related Model
The known optimal decoding methods for cryptographic protocols require much more computing resources than the attackers currently have.
Computational resource-independent models, often called unconditional security models or information theory security models, are the strictest security models in information theory. Even the ultra-high-performance quantum computer that may be hotly debated at the moment can not decipher the privacy protection scheme under this security model.
There are very few solutions available under the computational resource-independent model. The only commonly used solution is based on a one-time-one-cryptography protocol, and requires additional security assumptions regarding the secure generation and transmission of infinite-length keys.
Most cryptographic protocols fall into the latter category, namely computing resource related models. Generally, the mathematical protocol is used to prove that the cryptographic protocol can be reduced to a certain computationally difficult problem, thereby ensuring that it is difficult for an attacker to complete the calculation within a limited time. At this time, it is also called a provable security model.
From the above classification, it can be seen that the security of Xiaohua's cryptographic rental agreement is very likely to be affected by the development of computing power.
For enterprises, to evaluate the effectiveness of cryptographic protocols in privacy protection schemes, it is necessary to combine the sensitivity and timeliness of privacy data. An example analysis is as follows:
- A medical manufacturer needs to perform privacy protection on the purchaser's purchase amount, identity, details and other data. The timeliness of protection may take 5 years or more. Therefore, the technical solution that needs to be selected needs to provide a longer period of security in order to meet the security requirements of the computing resource related model.
- Some businesses only need to ensure the privacy of their data within a few hours. In this type of scenario, you can choose a solution with a higher system efficiency but a relatively short decoding time, which can also meet the security requirements of the computing resource related model.
The use of cryptographic protocols to balance the impact of privacy protection technology solutions on business and business processes to maximize system efficiency and optimize user experience is not necessarily the stronger the security of the chosen cryptographic protocol.
In general, it is recommended to build an efficient cryptographic protocol under a security model that meets business needs, as it is sufficient.
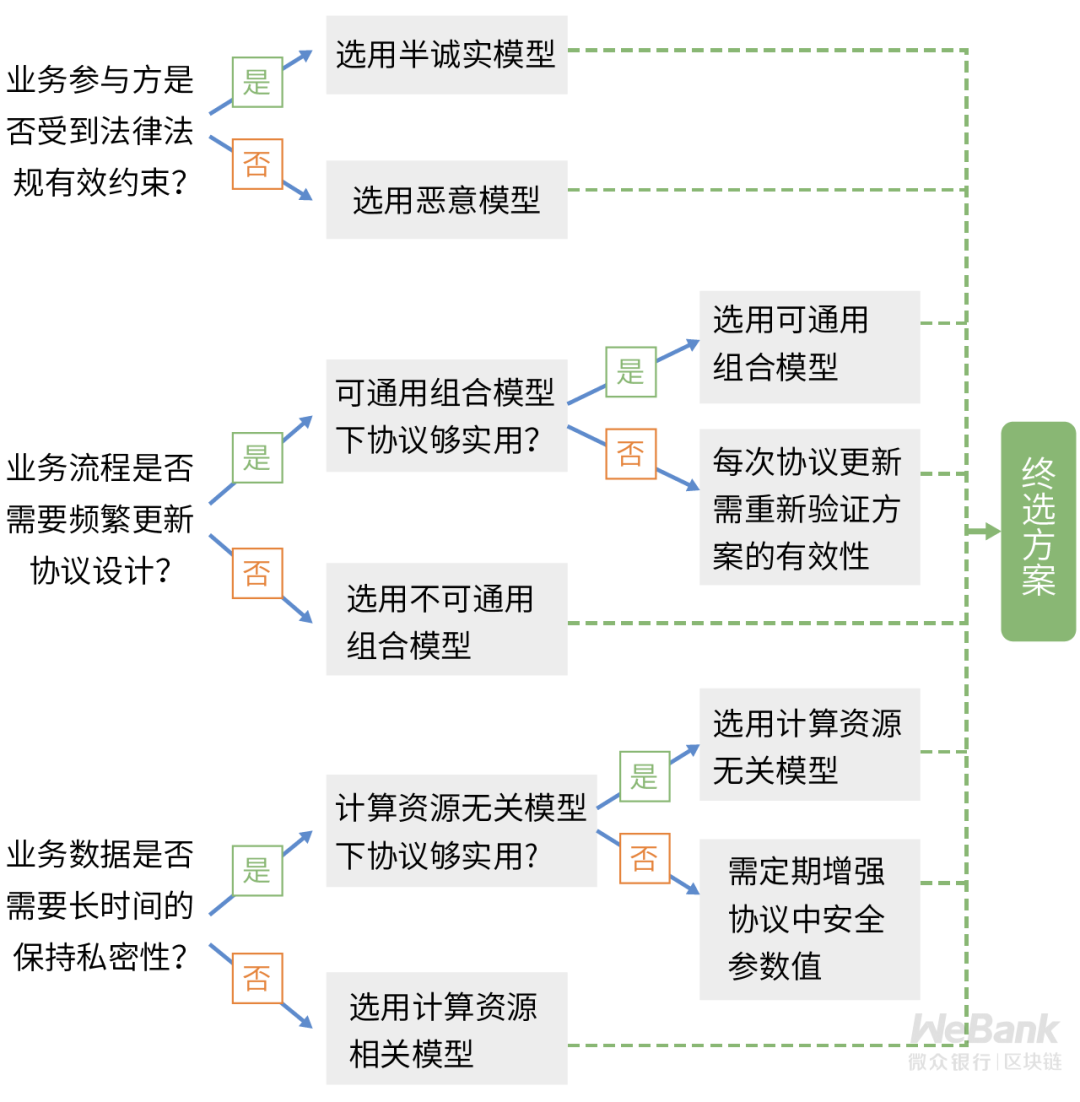
Exactly: The choice of password scheme is clueless, and the security model definition is fundamental!
The implementation of privacy protection business and the selection of security models is one of the important factors affecting the effectiveness of privacy protection. Cryptographic protocol security models are diverse. Security models with higher security levels tend to be less efficient. In fact, legal norms and social ethics in the real world constrain many business scenarios and help simplify the design of cryptographic protocols.
Enterprises need to analyze specific scenarios, select the most appropriate security model, and then customize the privacy protection technology solution that is most suitable for their own business scenarios. It is often more effective than applying a general solution directly.
In addition to the security model related to the theoretical capabilities analyzed in this article, when actually developing and deploying technical solutions, omissions at the engineering level will also unfortunately lead to privacy data leakage. For specific analysis, please pay attention to the decomposition below.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Behind "House N" in South Korea: Is Encryption Security Really Safe?
- Cryptocurrency rankings in the U.S. released! Richest cities hold $ 55,000 in crypto assets per capita
- Five Questions on New Infrastructure: Blockchain plays an important role and investment volume is insufficient
- Bybit New Product Launch Conference-Anyway, have an appointment with you
- Major Korean Exchanges Announce "Cooperate with Investigation of Room N"
- Opinion | Under the epidemic, the "hidden disease" of the supply chain is exposed, blockchain + supply chain or "hidden machine"
- Global stablecoin may face regulatory storm, IOSCO has stepped in






