How to choose the cryptography technology? Revisiting the Security Model of Engineering Capability Boundaries
Author: Li Haoxuan
Source: Weizhong Bank Blockchain
Unbreakable cryptographic algorithms are also afraid of physical attacks? Why does a physical signal leak threaten the effectiveness of privacy protection? What is the privacy protection plan about the deployment environment? How to design a privacy protection scheme in an untrusted execution environment?
Here, we will continue to analyze the security model, from the theoretical level capability boundary in the privacy protection technical solution to the engineering level capability boundary during actual development and deployment, sort out relevant security assumptions in engineering implementation, and applicable business scenarios.
- Ethereum 2.0 will release the latest version of the code specification v0.11.1, giving a green light to the multi-client test network release
- MakerDAO's first debt auction ends, Paradigm becomes biggest winner
- Xi Jinping: Using cutting-edge technologies such as blockchain energy to promote urban management innovation
In the previous theory, we introduced a variety of different security models to measure the theoretical strength of cryptographic privacy protection technology solutions. However, the effectiveness of a privacy protection technology solution if it only considers security at the theoretical level and ignores security at the engineering level is questionable.
As early as 1985, Wim van Eck proposed in his paper that attackers can use the electromagnetic radiation signals generated by the software to run, combined with statistical analysis methods, to decipher the confidential information content being processed by electronic equipment. This is a typical side channel attack, a risk that cannot be ignored in the field of cryptographic engineering.
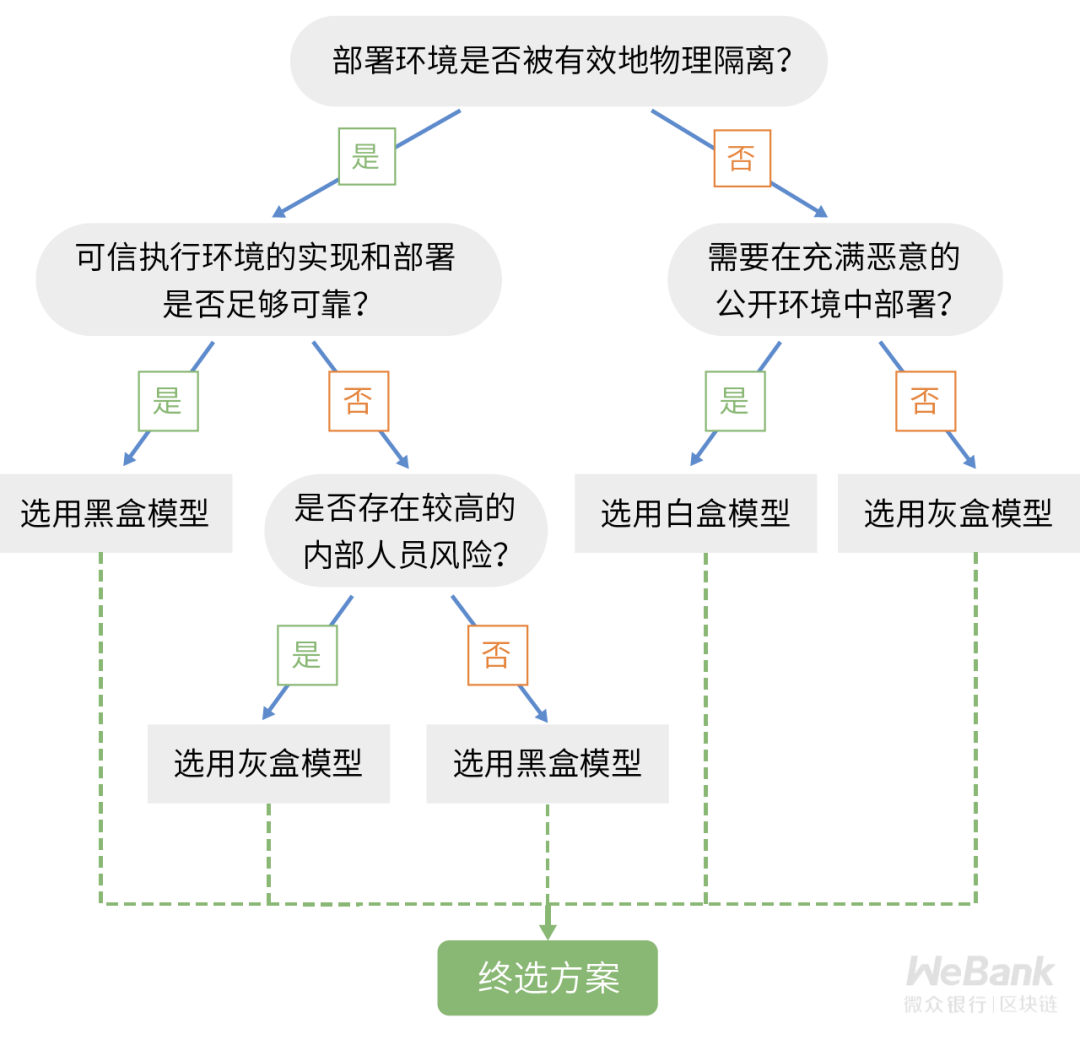
Similar to the security model in the field of cryptography theory, we can also define the corresponding security model for the security risks in the field of cryptography engineering based on its security assumptions. The three most common types of security models are as follows:
-
Black box security model -
Grey box security model - White box security model
In the above three types of security models, the trust requirements of the cryptographic system for the deployment environment are gradually reduced. In this theory, we will continue to tell the story of Xiaohua, taking the encryption process when Xiaohua sends beautiful information to her friends as an example, and elaborate on the impact and inspiration of these three types of security models on the selection of corporate privacy protection technologies.

Black box security model
Xiaohua, who was born in science class, is very confident in his technical ability and intends to surprise his friends with beauty by encrypting information …
Xiaohua chose the industry standard AES encryption scheme to convey his private information to the beauty in a special way. Xiaohua used the computer in the public computer room to develop and run the corresponding technical solution, which produced ciphertext information.
Unfortunately, the computer in the public computer room was implanted with a Trojan by an attacker. The Trojan decoded the plaintext of Xiaohua's private information by reading the power consumption and other intermediate state information during code execution.
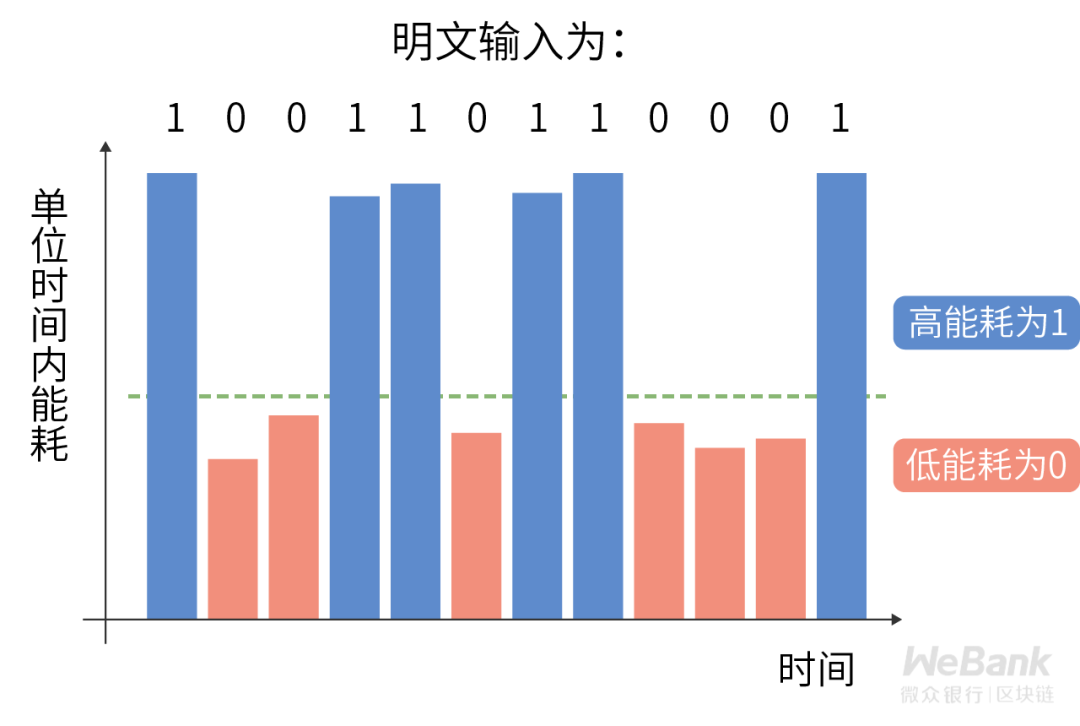
In fact, in addition to software technology solutions based on cryptographic technology, even hardware technology solutions based on trusted hardware modules will be affected to varying degrees by the above-mentioned privacy risks. However, we still think that these solutions are safe and available in common business environments. What is the reason?
This introduces the definition of the black box security model, assuming that the execution of the technical solution is a completely closed black box to the outside world.
If we abstract the overall privacy technology protection scheme into a function y = f (x) about the private data x, for an attacker, we can only get y, and we cannot get any intermediate that f (x) generates during the operation. status information.
Intermediate state information includes directly sensitive information and indirect sensitive information:
- Directly sensitive information: internal variable values, code execution trajectories, etc. during calculation
- Indirect sensitive information: execution time, equipment energy consumption, memory usage, electromagnetic radiation, etc.
Most cryptographic algorithm implementations, such as the standard implementation of the AES encryption algorithm, are based on the black box security model.
This means that even if the corresponding cryptographic algorithms and protocol designs reach the upper limit of theoretical capabilities, information theory security may still leak private data under the premise that the assumptions required by the black box security model are broken.
Conversely, for a controlled business environment, no attacker can enter the computer room, or it is difficult to remotely obtain these intermediate state information through other methods, and the corresponding software and hardware modules are configured and used correctly, then the corresponding technical solution is still safe.
Considering the trade-offs between privacy and efficiency, the technical solution under the black box security model has relatively low engineering implementation complexity and can provide efficient system implementation. It can be used in business scenarios in which the risk of intermediate state information leakage is low and the deployment is controlled.

Grey box security model
Xiaohua learned from the last lesson, optimized the implementation of the encryption algorithm, and shielded the leakage of common intermediate state information such as execution time and equipment energy consumption. The new scheme seems to have taken effect, and the Trojans previously deployed by the attackers could not obtain valid information to decipher Xiaohua's private information.
Xiaohua's optimization to a certain extent reduces the trust requirements of the privacy protection technology solution for the deployment environment. Compared with the previous black box security model, the security model here is the gray box security model, which allows a certain degree of intermediate state information leakage.
The gray box security model requires technical solutions to prevent the leakage of private information due to commonly used intermediate state information. Commonly used intermediate status information generally refers to various physical signals that are easy to observe from the outside during the implementation of the technical solution, such as execution time, equipment energy consumption, electromagnetic radiation, and acoustic signals. This type of attack is commonly referred to as a side channel attack, a bypass attack, or collectively a gray box attack.
In order to deal with these gray box attacks, the algorithm needs to be rewritten based on the original black box security engineering implementation, so that under different inputs, the physical signals to be guarded behave the same. Taking the most common execution time analysis attack as an example, under the gray-box security model, the execution time of the technical solution is always kept equal for all inputs, so as to avoid leakage of information about private data due to differences in execution time.
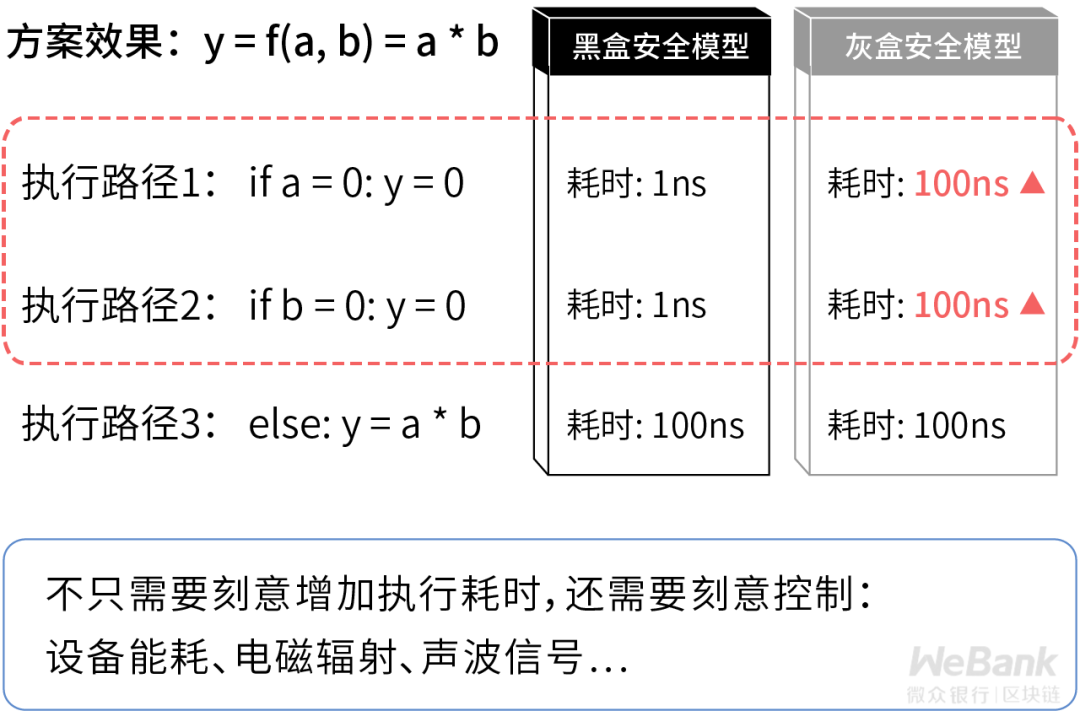
However, the side effects of this type of gray box security technology solution on system efficiency are also obvious. Even if some execution paths can be executed more efficiently, they need to be deliberately reduced in efficiency to match the one with the least efficient execution path in business logic to ensure external observables such as the time used and energy consumed in the execution process Physical signals do not show significant differences under any input.
It can be seen that the execution efficiency of the gray box security technology solution is always determined by the least efficient execution path in the business logic, which brings certain challenges to the optimization of system efficiency.
Compared with the black-box security model, the gray-box security model requires more trust in the deployment environment than reality. To some extent, it takes into account internal personnel risks, such as privacy risks that can only be prevented through governance, and has more practical anti-attack capabilities .
Under the gray-box security model, the application of technical solutions is mainly used to prevent internal personnel risks, or to deploy and run business in an outsourced environment that is not completely trusted.

White box security model
The good times didn't last long. After the attacker found that the Trojan horse that had been deployed had failed, he upgraded the Trojan horse program. Xiaohua's gray box security solution was not perfect. The attacker obtained the value of the internal variables during the execution of the technical solution. Deciphered.
Although the gray box security model has some protection to the intermediate state information, it cannot guarantee that all the intermediate state information can be effectively protected. If this can be achieved, the strongest white-box security at the engineering level is achieved.
Returning to the formula that defines the black box security model, the privacy technology protection scheme can be abstracted as a function y = f (x) on the privacy data x. Under the white-box security model, in addition to x, an attacker can obtain any intermediate state information generated by y and f (x) during the operation.
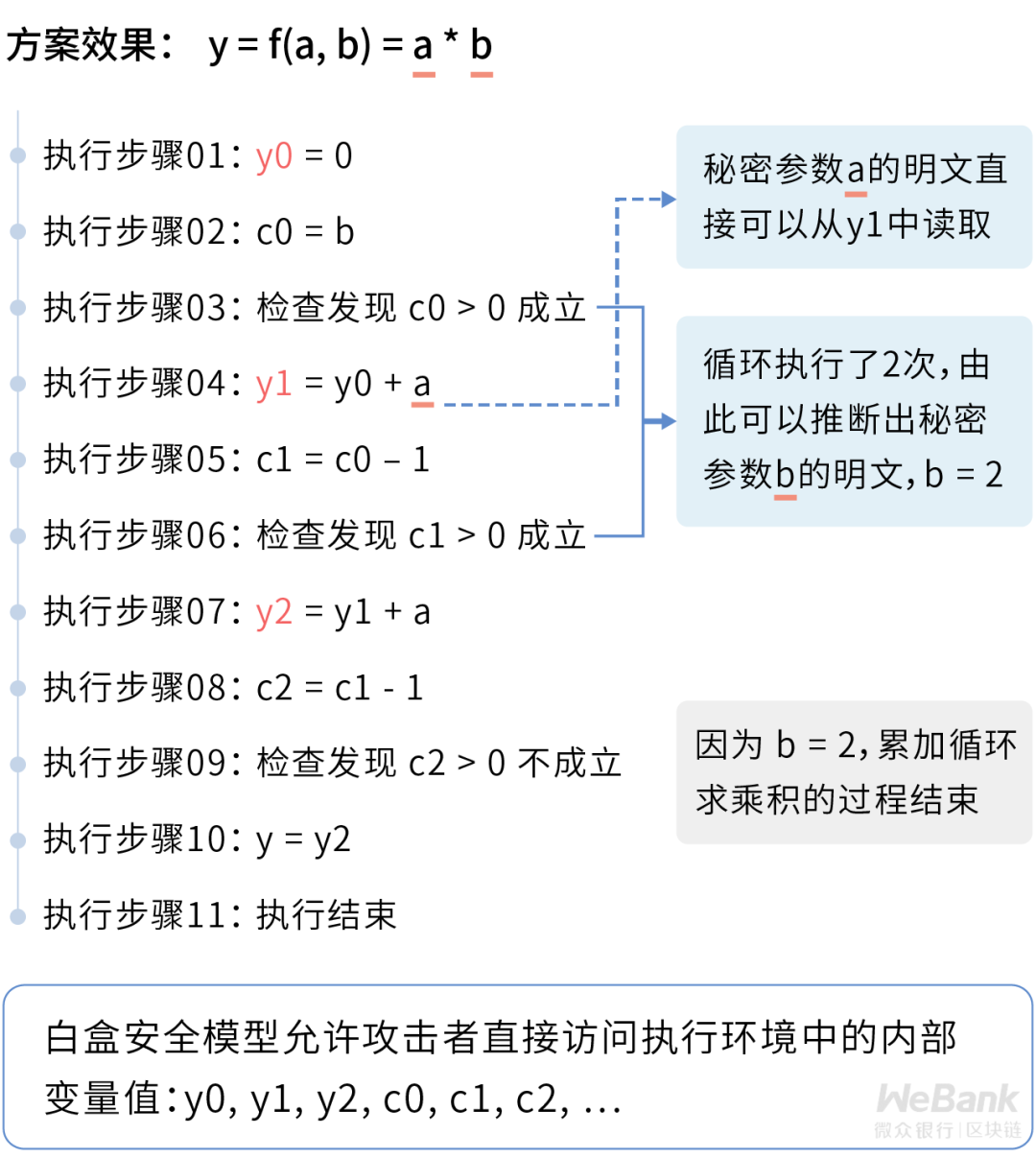
The white-box security model assumes that the execution environment is completely transparent to the attacker, and it sounds very mysterious. But how are keys protected? Isn't plain text input seen directly? Faced with such a powerful attacker, how can we protect the privacy of data?
The effect is indeed very mysterious. At present, the existing research has weakened the definition of the white box security model. Usually, the protection target is limited to that even if the attacker controls the entire execution environment, the key cannot be easily extracted through memory reading and other methods .
In order to achieve white-box security, it is necessary to further disrupt the storage of obfuscated keys and rewrite the algorithm based on gray-box security, so that the correct key can be used indirectly during the execution process. This project security requirement further increases the complexity of the project implementation. For example, the white box security implementation of the AES encryption algorithm is more than 10 times slower than the black box security implementation.
Although most of the technical solutions under the white box security model are currently immature, it is necessary to consider using white box security for services that need to be deployed in an uncontrollable public environment, such as public IoT applications, provided the solutions are available. Technical solutions to protect keys in terminal devices and control the risk of leakage of private data.
Exactly: There is no flaw in the clever password theory, and careful implementation of the project requires caution!
Engineering safety and theoretical safety are two independent dimensions. Theoretical safety is not equal to engineering safety. No matter how strong the theoretical safety solution design is, it will also cause the previous work to be abandoned due to improper engineering implementation.
Understanding the security risks in the field of cryptographic engineering is essential for practical application landing and secure operation. When selecting a privacy protection technology solution based on cryptographic technology, an enterprise needs to theoretically contact engineering, and select an appropriate security model according to the characteristics of its own business scenario and deployment environment to ensure the ultimate effectiveness of the privacy protection technology solution.
In these two theories, we analyze the theoretical capability boundary and engineering capability boundary in the selection of cryptographic technology. In addition to many security assumptions in algorithm theory and engineering implementation, emerging quantum computing and quantum communications also pose challenges to the effectiveness of privacy protection technology solutions. For specific analysis, please pay attention to the decomposition below.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- QKL123 market analysis | The Federal Reserve will move again, can it survive the constant stimulation? (0401)
- Bitcoin mining revenue has increased 20-fold in 6 years. Can miners continue to make profits after halving?
- Opinion | Professor of the Chinese People's Congress: China needs to promote the construction of a sovereign digital currency to build a fair and just new international political and economic order
- The secret history of Bitcoin: those who leave a message on the Bitcoin blockchain
- 4D Interview | Reveal the story behind "crypto cat" and the killer of "Flow"
- Counter-mainstream, new commune and blockchain: a movement spanning 60 years
- What is the reason for Tether's crazy increase in USDT?





