Introduction to Blockchain | Cryptography in Bitcoin: Fundamentals of Digital Signature and Transfer
Let's take a step by step, let's take the easiest email as an example.
Now A sends an email to B. This email is encrypted. According to the principle of public key encryption, which is the principle of asymmetric encryption, B is the email. Then, A encrypts the email with the public key of B. After receiving B, B can unlock the email information with his own private key and know the contents.
Everyone is familiar with the process of asymmetric encryption. There is a problem here. If the information of this email is very important, of course, it is not important and does not require asymmetric encryption. I mean, if this information is about money, the most direct statement is that A wrote in the mail, "I owe B 100,000 yuan." At this time, this email has a little legal effect similar to the debt.
The problem is coming. The debts need to have a signature, signature, and other vouchers. What credentials does this email have? No, I can only say that this email is written to B, because it is B's public key encryption, and only B can use its own private key to unlock it, but there is no certificate to explain who wrote it.
- Wang Xing Mi will V Shen Shen Nanpeng, the US group "touch chain" fire cooking oil
- The first securities based on the cryptocurrency market was approved! Grayscale: The agency is still curious about cryptocurrencies
- Encrypted currency investment and Bo silly theory: Who is the last fool?
This time you need something, called a digital signature, like a real-world autograph and a fingerprint.
Digital signatures are as unique as fingerprints. How to do it?
A sends a message to B, using his own private key to encrypt this information. At this time, after receiving B, holding A's public key (public), to verify that it is issued by A, this is the digital signature.
At this time, combined with the previous method, when A is issued, A's own private key is used to sign the information, and then B is encrypted with the public key. After receiving B, B's own private key is decrypted to see the information, and A can be used. The public key verification signature, the entire process is completed.
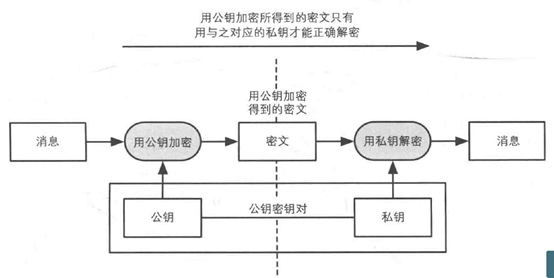
Encryption with public key is the above figure. The basic flow of public key cryptography is encrypted with the private key. The figure is the same, but it is turned over, one with a public key and one with a private key.
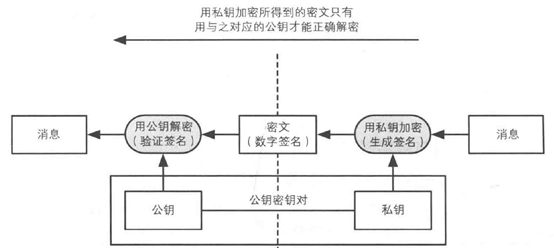
Private key encryption is equivalent to generating a signature, and public key encryption is equivalent to verifying a signature.
The public key and the private key appear in pairs. There is strict mathematical logic. The ciphertext encrypted with the public key can only be decrypted with the corresponding private key. Similarly, the ciphertext encrypted with the private key needs to correspond to it. The public key is decrypted. That is to say, if a ciphertext is successfully decrypted by using a public key, it means that the ciphertext is encrypted by the private key corresponding to the public key, and only one person in the world who owns the private key is the private key. Owner.
When you talk about it, you know, Bitcoin's trading information is also the same.
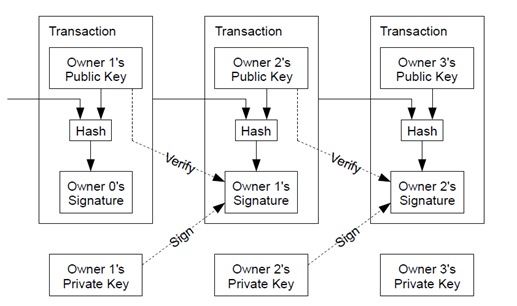
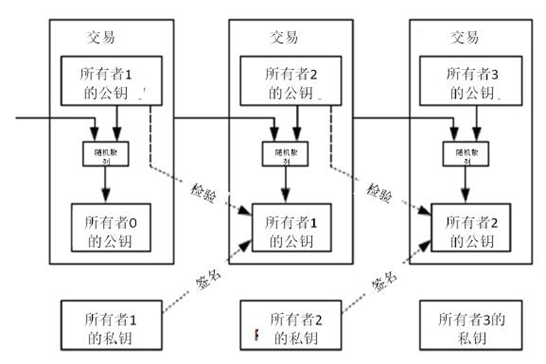
The above white papers from Bitcoin (both Chinese and English versions are placed on top), I believe that readers will be more aggressive when they first see this picture, because they do not understand asymmetric encryption (public key encryption), understand This picture has certain difficulties.
The transfer from the founding block is on this chain. The way to generate new bitcoin is mining, which is the process of generating money. And every person who trades Bitcoin, or transfers, I transfer you 10 bitcoins. This information is the digital signature of my private key pair. The person who receives the bitcoin uses my public key to verify it. I turned, and the information I transferred to you is that I encrypted it with your public key. This person can see the corresponding address. Others know that my address is forwarded to your address, but can use this address. Bitcoin only has one person with a private key . The person corresponding to the address is specifically who does not know, that is, the transparent and transparent transfer, but the principle of privacy protection.
As for the private key to launch the public key (and vice versa), the public key to launch the public key hash (instead of not), the public key hash to launch the address (which can be reversed), this process is not a very difficult thing, feel free to go online to search Know. The process of encrypting and decrypting the public key private key is done automatically on the Bitcoin network. What you see is that Bitcoin moves from one address to another.
Therefore, the entire cryptography series article has opened up the entire knowledge chain, from hidden method, shift replacement method to Wikipedia encryption method to Enigma machine, then to asymmetric encryption, hash function, and Using the mining principle of the hash function, the asymmetrically encrypted digital signature is utilized. Bitcoin is an important fruit built on this tree of cryptography .
If you have read this series of articles carefully, I believe that more people will know about cryptography and bitcoin. If you can do this, my work will not be in vain. I also hope to see you in the article. When a friend asks you what Bitcoin is, when Bitcoin transfers money, it says, " Do you know asymmetric cryptography? Do you know the role of the hash function? Let me tell you about it, " of course, You can also send my series of articles to friends, first understand the basic principles, and understand the latter.
Author: village two old
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- The ant blockchain is next to the city, helping the Yunnan Provincial Department of Finance to open the country's first blockchain electronic bill
- Libra's 21 initial members formally signed the association's charter, and approximately 180 entities initially met the membership criteria.
- Telegram "force majeure" clause or activated, no need to refund funds due to postponement of network release
- The market gradually stabilized and rebounded, XRP led the mainstream currency
- From credit card to digital wallet, where is the development of cashless sports?
- Blockchain deposit certificate to open data trust "last mile"
- 16 Nobel Prize geniuses focus on the blockchain: 7 are dedicated to specific projects and 14 are from the Economics Awards