Opinion | ZEC and XMR: Privacy is important, but it is not all
Privacy must be a key component of open finance, global borderless currencies, and Web 3.0. However, in the cryptocurrency ecosystem to date, privacy-related development activities mostly occur on privacy-focused blockchains . The Bitcoin and Ethereum communities put issues such as scalability and user experience first .
Developers who put the importance of financial privacy on top of all other features have built agreements primarily to support privacy protection, including assets such as Zcash and Monero, as well as Grin and Beam. New arrivals. They all make trade-offs between functionality and usability to ensure privacy is their core value proposition .
- IMF's point of view: "Synthesis of central bank digital currency" will be the future central bank currency?
- Bitcoin position analysis: the collapse of the market, the characteristics of various accounts are obvious
- Blockchain entry | Blockchain 51% power attack is not so terrible
But is privacy a core value proposition that independent blockchains should build?
A common argument for crypto investors is that due to the importance of privacy in financial transactions, blockchains that focus on privacy (such as Zcash, Monero, Grin, and Beam) should be able to accumulate value. We agree that privacy is very important in financial transactions, but we do not believe that there is a causal relationship between the two .
We anticipate that the most valuable blockchain will win in a range of different technology trade-offs, and users and businesses will find novel ways to bring privacy into these networks, rather than having network participants choose native privacy agreements and Bear the risk of balance sheet.
In addition, Layer 1 assets (such as BTC, ETH, etc.) should generally be considered as currency. These Layer 1 assets will have obvious network effects , so only a few blockchains can win this long-term battle.
If blockchain platforms with non-native privacy features (such as Bitcoin and Ethereum) have been able to provide enough privacy for most people, blockchains with native privacy (such as Zcash, Monero, etc.) blockchains It will become irrelevant.
In this article, we will discuss the following topics:
- How the technology around privacy will bring a functional compromise;
- Use the blockchain that focuses on privacy protection and the balance sheet risk inherent in encrypting assets;
- Introducing privacy into different approaches to more widely used blockchains such as Bitcoin and Ethereum;
- Under what circumstances can privacy protection be considered "good enough";
- How do we view the relationship between privacy protection and investment.
Complete privacy
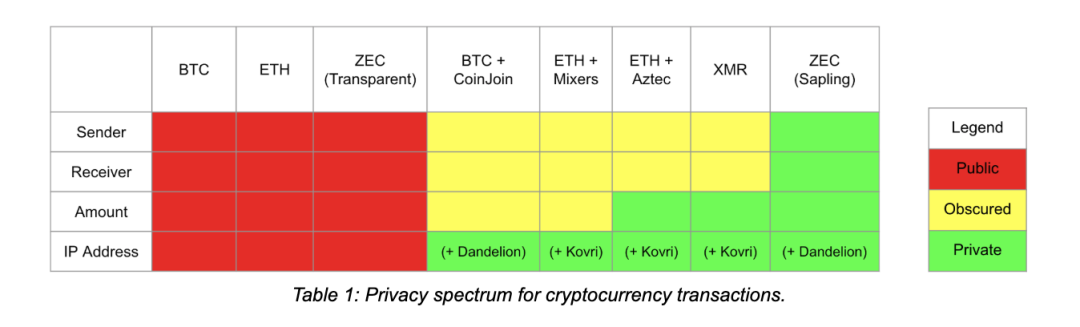
- One end is a transaction that does not hide any of the above information , such as basic bitcoin or Ethereum transactions;
- At the other end is Zcash's Sapling deal, which masks the four types of information described above (provided it is combined with fuzzy IP technologies such as Dandelion or Kovri).
Zcash's zk-SNARK architecture allows the sender to transmit a certain amount of tokens to anonymous recipients. The number of tokens transferred will not be known to third parties, and no relevant identity information will ever be recorded on the blockchain and will not be on the network. Leaked in. In theory, Zcash's privacy transaction is perfect .
[Note: The development of Zcash has generally gone through OverWinter -> Sprout -> Sapling (Sapling)
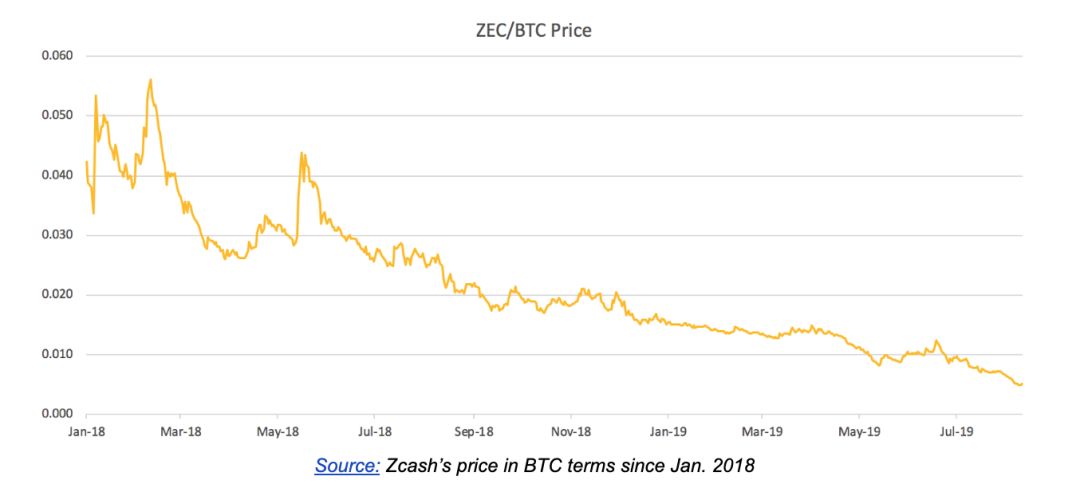
Although Zcash has been on the market for nearly three years, only 5% of the storage in ZEC uses SNARKs privacy technology (about half of which use traditional SNARKs technology). Approximately 95% of ZECs are stored in public addresses without privacy protection .
In 2019, the cryptocurrency market generally rebounded, but ZEC is a notable exception.
There are several reasons.
First, the core innovation of cryptocurrency is the ability to programmatically achieve scarcity that is easy to verify without trusting either party .
Scarcity makes social scalabillity possible, as people from different cultures and industries can verify that the token they hold is a guaranteed percentage of the known whole. But unfortunately, perfect privacy protection hinders the auditability of cryptocurrencies .
For example, in March 2018, Zcash discovered a vulnerability in their encryption technology that could lead to infinite inflation in ZEC tokens. As the Zcash Foundation itself admits, it is impossible to know if any party has exploited the vulnerability to issue ZEC tokens until the Sprout address is deprecated. Users can verify how many tokens are sent to the covert pool, but they can't know if these tokens were forged by the attacker.
In other words, a completely private transaction will prevent investors from verifying that Zcash is as scarce as expected.
Second, optimizing privacy in the way of Zcash brings a heavy cost penalty . Each time a completely private transaction is created, the sender must calculate a series of precise calculation steps to generate a proof that the miner can use zero-knowledge technology verification. These steps are very expensive from a computational cost perspective, and the Sprout version is too cumbersome to be widely adopted.
Later, the Zcash team designed the Sapling version to explicitly optimize token transfers, avoiding any redundant features (such as Ethereum's stateful smart contracts, or Monero's multi-signature contracts), although These features may appear in Zcash in the future. But the more efficient and perfect privacy transaction consumes Zcash's programmability .
With the end of the bull market bubble in 2016 and 2017, today's market is more inclined to less private, but more secure, programmable and scarce cryptographic assets such as Bitcoin and Ethereum .
But despite this, the future of borderless cryptocurrencies seems unlikely to be completely transparent. Anti-censorship requirements have a degree of financial privacy protection .
So the question now is: How much privacy protection is it good enough?
Privacy in the "hidden people"
The privacy policy of "hidden people" refers to having cryptocurrency transactions follow a set of rules that make it difficult for third-party observers to identify the actual sender, recipient, or sending amount for a particular transaction. The more transactions that follow these rules, the more participants there are, and the more difficult it is for an observer to anonymize the transaction .
Contrary to completely private transactions such as Zcash, this “hidden crowd” strategy provides users with the privacy and security of transactions by obscuring the way , because third-party observers can see what is happening, but No clear judgment can be made on the sender, receiver or number of transactions. All judgments are probabilistic at best , and in most cases, both the sender and the receiver can achieve "plausible deniability" (ie, concealing themselves).
Bitcoin holders are using the CoinJoin privacy protection program as a tool for their “hidden people”.
Greg Maxwell first proposed the concept of CoinJoin in 2013, which refers to a number of different participants combining their multiple single-input, single-output transactions into one multi-input, multi-output transaction . This splits the direct connection between the sender and the receiver , and if all the outputs are the same size, it also obscures who receives the BTC. Recently, applications such as Wasabi Wallet and Samourai Wallet that use the CoinJoin solution to minimize trust requirements have become popular.

By default, Ethereum's base layer is not as private as Bitcoin by default, because Ethereum uses an account-based model instead of Bitcoin based on the Unconsumed Transaction Output (UTXO) model. This means that in the Ethereum network, an address is reused in many different transactions, rather than assigning a new address to each transaction.
However, one advantage of smart contract platforms such as Ethereum over Bitcoin is that they allow for more advanced transaction types . A smart contract can provide privacy in the “hidden crowd” of all assets sent to it, and even provide complete privacy for all assets sent to it. Currently, several of the smart contracts that support privacy protection are already running on the main network, and more use cases are under development.
Ethereum “mixers” such as Argent's Hopper , Heiswap and Tornado offer different ways to protect privacy in the “hidden people”, which is comparable to Bitcoin's CoinJoin solution .
Through these Ethereum “mixers”, users can deposit a fixed amount of a specific asset (such as 0.1 ETH or 10 DAI) into a smart contract, waiting for enough users to make a similar amount of deposits, thus building a large anonymous set. The original amount is then extracted into a new address that is not associated with the original address .
But since the amount of money each user has to deposit into the contract must be exactly the same, these privacy solutions will be difficult to attract large deposits, which will limit the expansion of these programs to a sustainable, independent business.
The Aztec Protocol has developed a series of modular smart contracts that allow asset confidentiality , address privacy, and zero-value output , essentially to create a pool of privacy assets in Ethereum . Users need to send their public encrypted assets to a smart contract, which then generates a " private version " of those assets into their privacy pool and assigns a new private address to the user for trading. The more assets the privacy pool attracts, the more people there are, and this provides more protection for all participants .
Providing privacy protection for existing blockchains is not just an additional feature of Layer2. In the near future, small public chains with strong governance capabilities such as Decred and Tezos will add protocol-originated privacy protection. Like Bitcoin and Ethereum, these public-chain platform communities see the value proposition of privacy transactions and are working to make privacy protection a feature that is available to the community, rather than the ability to use native financial privacy protection as a core product . In addition, the Tezos community is directly stealing Zcash's Sapling design!
All of these public chain efforts are trying to improve the current gold standard for privacy in the “hidden people”: Monroe Coin (XMR).
As mentioned above, only 5% of ZECs are currently fully private, but 100% of XMRs follow a set of rules that create privacy/security by hiding .
Monroe transactions use three basic types to hide the sender, receiver, and number of transactions: ring siganatures, stealth addresses, and ring confidential transactions (RingCT)
- The ring signature allows the sender to sign the transaction using n different keys, obscuring which key is the sender's key.
- The covert address allows the recipient to use a one-time address for each transaction, thereby hiding the recipient's real public key.
- The closed secret transaction realized the fuzzification of the transaction amount and concealed the actual transaction amount.
Since all XMR transactions must use these features, all XMRs belong to the same anonymous set and are hidden in the same crowd. This raises the potential for a potential FloodXMR attack , which we'll cover below.
At the same time, Monroe's performance in the bear market in 2018 is not much better than Zcash . See below:

Regardless of the underlying public chain, these “hidden people” privacy schemes can only provide “keep a reasonable denial”, but the larger the crowd, the more they can hide themselves.
How much privacy protection is it good enough? This question can now be understood as follows: when the transaction takes place in Wasabi Wallet's bitcoin anonymous set, or in the Aztec Protocol's Ethereum anonymous collection, or in the anonymous concentration of Monroe, then if the third party wants to The transaction is going to be anonymized. How much will it cost to realize the anonymization of the transaction? Which cost will be the highest? (The higher the cost, the more it means)
Let's continue reading.
Deanonymization cost
The Monroe community refused to accept this cost estimate, saying the cost was too low. They also refute the algorithm, saying that the analysis is too simple and does not take into account any situation in the world, such as multiple attacks at the same time, or price fluctuations.
The purpose of this section is not to retell the FloodXMR attack, but to use its principles to build a common framework for us when considering the privacy pool of the public chain. The basic framework for a FloodXMR attack is this:
A certain number of XMR transactions occur on the Monroe network every day. These transactions are all mixed together, so no one other than the participants themselves knows who sent them to whom. However, since all transactions are public and the addresses are reused in the ring signature mode, the attacker himself may also participate in a large number of these transactions .
By doing so, the attacker greatly reduces the anonymity set and can more easily determine the actual sender and receiver of each transaction, effectively de-anonymizing them. Specifically, according to the above-mentioned researcher's report, a malicious participant who controls the key of 75% of the transaction output generated within one year can track 47.63% of all transaction inputs created during the same time period."
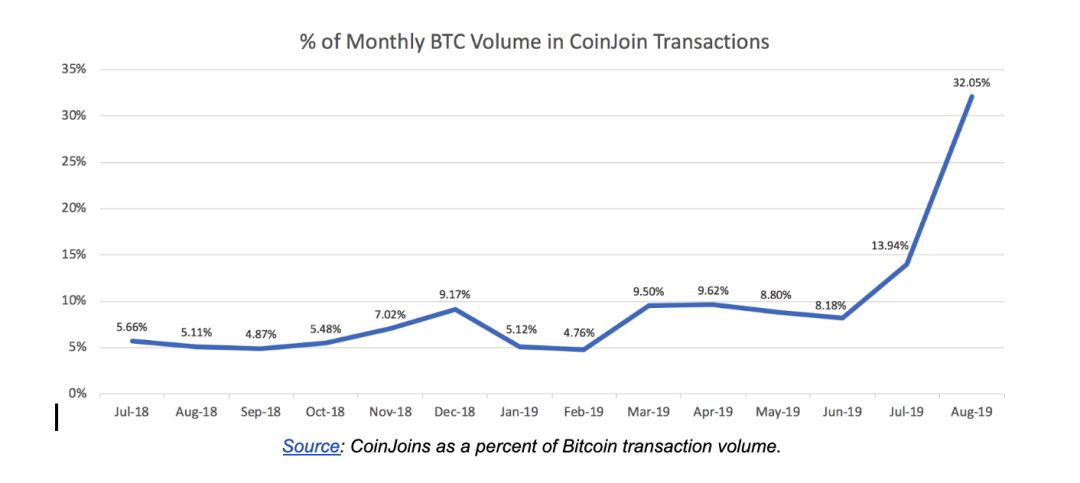
If certain assumptions are made, the attack may extend to Bitcoin's CoinJoin privacy pool (which has actually appeared) and Ethereum's Aztec Protocol privacy pool. For most of the past 12 months, the proportion of transactions using the CoinJoin program has accounted for 5% to 10% of Bitcoin transactions, and has increased in July and August of 2019. See below:
C = (Average transaction fee) x (Average daily volume) x 1.25 x (% of the market value of the privacy pool) x 365
The figure below shows BTC's Wasabi Wallet privacy pool, ETH's Aztec Protocol privacy pool (assuming it occupies 5% of ETH's market capitalization) and XMR's de-anonymization cost, average in the graph (average transaction fee and average daily transaction volume) The average value from October 19, 2018 to the time of publication is used.
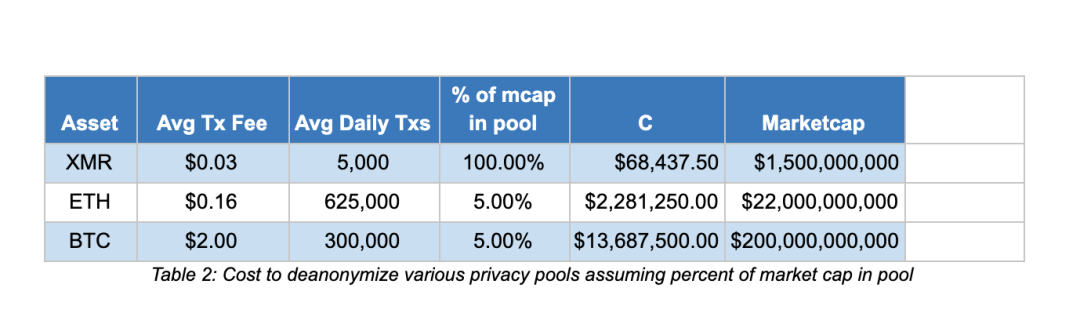
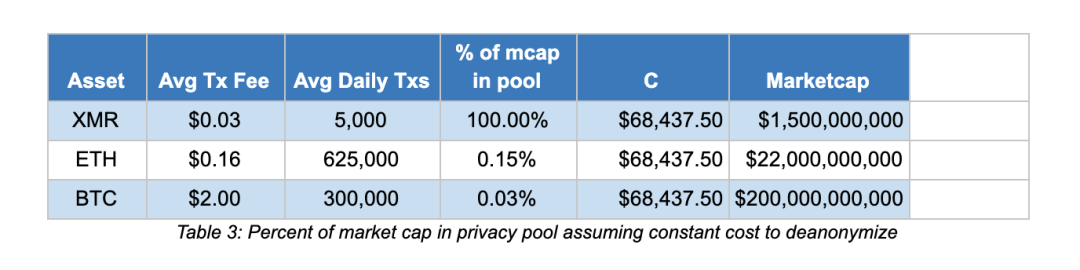
The market should have reservations about these figures, but understand that Bitcoin and Ethereum's market capitalization, transaction volume and transaction costs are much higher than Monroe, attacking the de-anonymization of Bitcoin and Ethereum's privacy pool. The cost will soon be higher than the cost of attacking the entire Monroe Anonymous Set .
However, in addition to predicting the future, there is another way to quantify the market's perception of privacy protection, which is to look at the users of the dark network (they are the ones most in need of privacy protection) and see which cryptocurrency is most commonly used by these people. . Since Monroe is currently considered to be the most private cryptocurrency, you may take it for granted that it still dominates; however, CipherTrace found that less than 5% of dark-net transactions use Monroe, and most dark-net encryption Currency trading is using bitcoin .
Written at the end
The privacy battle for cryptocurrencies will be an arms race with those trying to anonymize cryptocurrency users. If the cryptocurrency is to succeed, it must win the war.
Unfortunately, as we discussed above, the cost of performing a perfect private transaction under default conditions in Zcash is too high . This completely private approach undermines another core value proposition of cryptocurrencies: in the entire transaction history, using a license-free way to verify that the transaction has not incurred double costs, and that there is no undue inflation. Without this verification attribute, it is impossible for any cryptocurrency to have sufficient social scalability to become a global, borderless currency.
Therefore, the winning cryptocurrency must achieve some imperfect "hidden crowd" privacy, which is based on publicly verifiable public books . As can be seen from Tables 2 and 3 above, the Bitcoin and Ethereum communities are able to connect privacy pools to their own public chains, and because of the higher transaction volume and transaction costs, their deanonymization costs will soon More than the cost of deanonymization of the entire Monroe blockchain.
Clearly, privacy protection will be a feature of borderless currency, but it will not be a core feature.
The argument for privacy protection should be expressed around this understanding. Fund managers will start investing in companies that offer “privacy-as-a-service” on smart contract platforms such as Bitcoin or Ethereum, rather than investing in underlying encryption that optimizes anonymity in transactions. currency. Layer 2 solutions will by default provide privacy protection for their trading participants, which may free up large amounts of money from blockchain platforms that value transaction privacy (such as Zcash and Monero).
Fundamentally, fighting for complete privacy on the underlying chain is too expensive and therefore difficult to achieve , giving business opportunities such as Wasabi Wallet, Samourai Wallet, Argent, Heiswap, Tornado and Aztec Protocol. We believe that the funds invested in Zcash and Monroe will begin to flow to these companies or the underlying cryptocurrency they are building.
Original link:
Https://multicoin.capital/2019/09/24/privacy-is-a-feature/
Original title: "Privacy Is a Feature Not a Product"
Author: Ryan Gentry & Matt Shapiro
Edit: Jhonny
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Detailed explanation of the FundWin vulnerability system: Can the project party be suspicious of “doing evil”?
- 8Q | Don't open the scene: Big coffee gathers DVP, big white hat and hacker
- Can the blockchain help “Yang Anze” to “send money” better?
- Babbitt Interview | Author dialogue Bulletproofs: Money is the driving force encryption cryptography practices
- The Block's latest research: Which investment institutions benefit from Coinbase's currency?
- Building a “government wisdom brain” and promoting “blockchain+”, building big data across Hainan Island
- The trade-off of fragmentation technology: NEAR Protocol VS Ethereum 2.0






