Popular science | Customs passwords in the digital age: privacy calculations help data "refining"
Source: HQ Think Tank, the original title "Yan Li, HQ Think Tank: Privacy Computing Helps Data" Refinery ", It Is A Passcode In The Digital Age
Computing power
In the digital age, data has become the most important factor of production, known as new gold and new oil. For data as a commodity and asset to usher in the great development, it is necessary to realize the rights, circulation and privacy protection of data. Privacy computing provides a solution based on multi-technology collaboration and cross-disciplinary support to achieve reasonable data flow and value capture. So, what exactly is privacy computing? What is its underlying logic and essence? How does it work? What industrial scenes have landed so far? Last night ’s first lecture on privacy computing class, Yan Li, the founder of the computing power think tank, cut through the data perspective and sorted out the origin, development stage, application scenarios and business value prospects of privacy computing for the audience as a whole. Examples of landing in two major areas, boldly predicting that multidimensional developments such as supervision, collaborative technology and digital new infrastructure will jointly shape 2020 will be the first year of the landing of the privacy computing industry.
As the production factor of the digital economy, data is the core of it. And data privacy is becoming a pain and itch of the times. The pain point is the misuse of data, and the itch is that the new privacy protection regulations issued by various countries make the Internet giants pay more attention to privacy protection policies and experiences, helping users to obtain convenience while obtaining privacy protection.
- Babbitt Column | Bitcoin has experienced two extreme quotations in half a year. What do they have in common?
- Babbitt Column | Blockchain-Mathematics Reshapes Trust from Human History
- China's blockchain landscape moves west: Gansu 14 cities deploy blockchain service network
1Data separation of three rights, ownership and use rights must be separated
The ownership of the data cannot be bought or sold. There is a separation of three rights in data rights. Ownership, use and processing of data. Data assets can only transfer the right of use, the ownership is the user's.

The privacy calculation is to calculate the data without exposing the original data, and the calculation results can be verified. It cannot be simply understood as a technology to protect users' privacy services. Its focus is more on the basis of realizing data usage rights transactions, that is, the basis of realizing the value of data. Do not trade data itself, only trade data calculation results.
Therefore, privacy calculation provides a reasonable and orderly transfer of data use rights, while allowing the value of data to cross-subject use to amplify the value of the calculation solution.
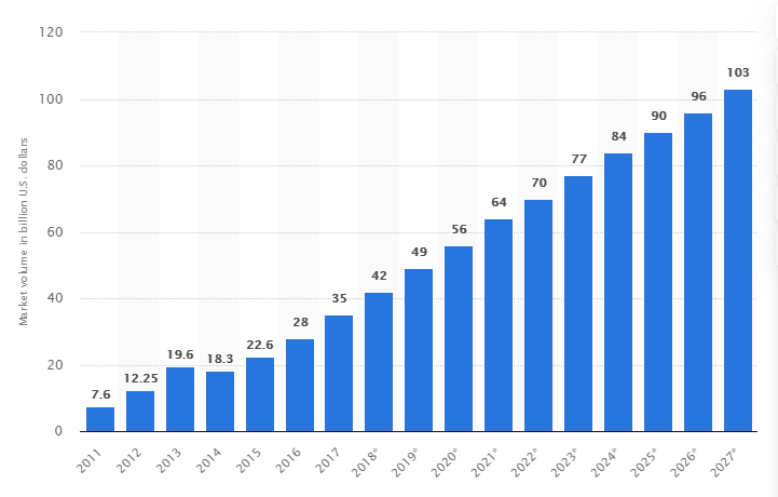
2020 can be called the first year of privacy computing. By 2027, the global data market is expected to grow to 103 billion U.S. dollars, more than double the expected market size in 2018, of which 45% will be market share based on application data. %, Which is 46.4 billion US dollars.
2 Several Technical Paradigms of Privacy Computing
Among the data held by centralized institutions such as Internet giants and operators, in addition to identity data and behavior data, productivity value data has the most privacy computing value. Private computing technology currently focuses on the following technical paradigms: multi-party secure computing, homomorphic encryption, zero-knowledge proof, and trusted execution environment.
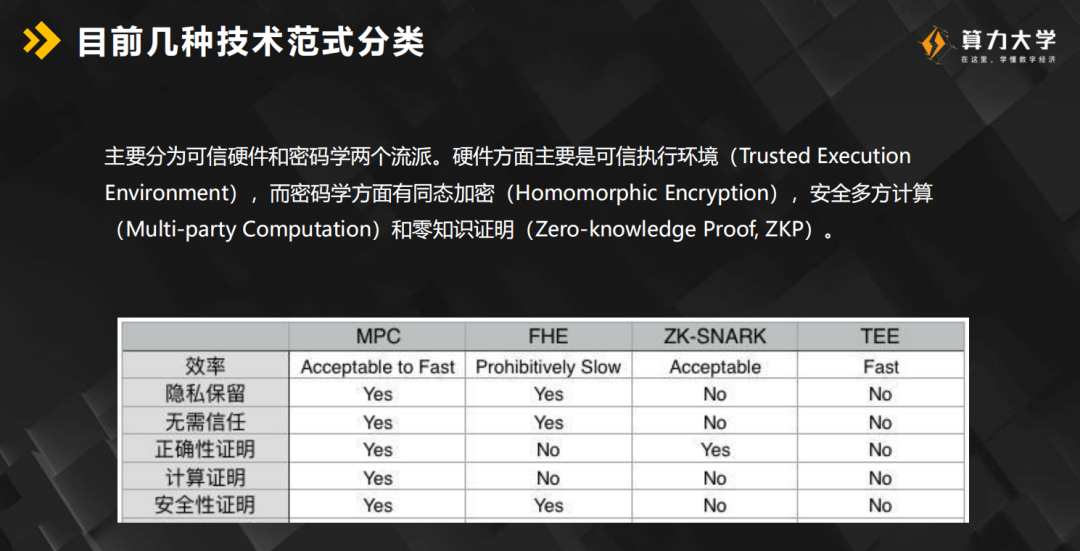
Secure multiparty computing
A set of protocol groups based on modern cryptography. This tool group contains many components including zero-knowledge proof (ZKP), probabilistic encryption, information theory message authentication code (MAC), various distributed communication protocols, and inadvertent transfer (OT ) And the most important basic technology: secret sharing and secret shard computing.
2. Homomorphic encryption
Homomorphic encryption (HE) is a form of encryption that allows calculation of ciphertext to produce encrypted results. The encrypted results match the results of the operation as if they were performed on the plaintext. Using such tools, you can outsource storage or computing without compromising data privacy. Because HE allows computing encrypted data while keeping it encrypted, it has been widely studied as a candidate for secure computing.
3. Zero-knowledge proof
One party (the prover Peggy) can prove to the other party (the verifier Victor) that she knows the value x without conveying any information except that she knows the value x. Blockchain projects are trying to use ZKP as a trusted offline computing solution. The disadvantage is that ZKP cannot prove the actual workload done in the remote environment, nor can it guarantee that the calculations are obtained from malicious hackers.
4. Trusted execution environment
It is a tamper-resistant processing environment that runs on a tamper-resistant kernel. The ideal TEE guarantees the authenticity of the executed code, the integrity of the runtime state, the integrity of registers, memory, and sensitive I / O, and the confidentiality of the code, data, and runtime state stored in persistent memory. Pros: Provides remote proof that it can be trusted by third parties. The downside is that hardware manufacturers are eager to come up with trusted hardware solutions, but lack common standards for different platforms. Hacking proved that SGX is not yet able to carry protocol-level data security protection. With TEE, you can trust the hardware, but not the person who controls the hardware. So it needs to be combined with a licensed network where all nodes are pre-approved and the environment is certified and trusted.
3 Which industries are more widely used for privacy computing purposes?
Almost all companies focusing on the field of privacy computing have chosen to enter the industrial application from the two fields of finance and medical, which have the strongest privacy protection and the most demand for privacy protection. In the context of this year's new digital infrastructure, the needs of financial digitization and medical digitization need to be met urgently.
In the medical, insurance, and black-and-white list sharing among banks, different institutions in the same industry want to use each other's user information and not share information. For privacy calculation, the results can be output to the service provider, and the receiver is responsible for the query and pays a certain query fee, which is cleared and cleared in a timely manner on the system.
At the same time, privacy computing has a large number of application cases in the four vertical fields of finance: banking, insurance, supply chain finance, and IoT finance.
How does privacy computing output data value in these areas? What specific typical application cases are there in the market? Experts from business giants and research institutions such as Weizhong Bank, Zhongan Technology, Gibeck, Molink Technology, Singapore Management University, etc. will jointly analyze the privacy computing business passwords in the next 5 days. Explain the huge data oil bonus released by this emerging track.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- DeFi Monthly Report | MakerDao encounters the most severe test in history
- Article describes the type, scale and trend of stablecoins
- On the Equity of Currency Stocks and Token Economy: How to Coordinate to Generate Synergy
- USDT issues more than 10 billion in six days. In a bear market environment, stablecoins become the biggest winners
- Free and Easy Weekly Review | "House N" Reflects the Weakness of Privacy and Sees How the "Sky Eye" of the Chinese Academy of Sciences Breaks the Game
- Discussion on anti-counterfeiting, anti-intrusion and tampering, and blockchain technology to improve the security of drone operations
- Super Planet Token GDP Price "Zeroed" Issuing Convertible Bonds With Annual Interest Rates Up To 250%





