Another re-entry vulnerability? Analysis of the Stars Arena attack incident
Re-entry vulnerability analysis Stars Arena attack incidentBackground
According to the MistEye system security warning by SlowMist, on October 7, 2023, the Stars Arena social protocol on the Avalanche chain was attacked, resulting in a loss of approximately $2.9 million. The SlowMist security team has analyzed the attack and shared the results as follows.
Related Information
Attacker’s address:
https://snowtrace.io/address/0xa2ebf3fcd757e9be1e58b643b6b5077d11b4ad7a
Attack contract:
- Caroline Ellison testified in court Acting on the instructions of SBF, embezzlement of approximately $14 billion in FTX client funds.
- New Organizational Paradigm An In-Depth Explanation of the Various Aspects of DAO
- Closing the ‘backdoor’ opened by the god mode, is a DEX without an administrator key the future?
https://snowtrace.io/address/0x7f283edc5ec7163de234e6a97fdfb16ff2d2c7ac
https://snowtrace.io/address/dd9afc0e3c43951659c8ebe7aef9ee40879863ea
Attack transaction:
https://snowtrace.io/tx/0x4f37ffecdad598f53b8d5a2d9df98e3c00fbda4328585eb9947a412b5fe17ac5
Attack Core
The attacker exploited a reentrancy vulnerability and tampered with the price corresponding to their own deposit share. Subsequently, during the sell-off, similar price manipulation occurred due to the dependency on the maliciously manipulated price calculation. By accurately calculating the share price updated during reentrancy, the attacker stole funds from the contract.
Transaction Analysis
We can see that there is a reentrancy call in the attack transaction. We analyze the call method step by step by decompiling the code.
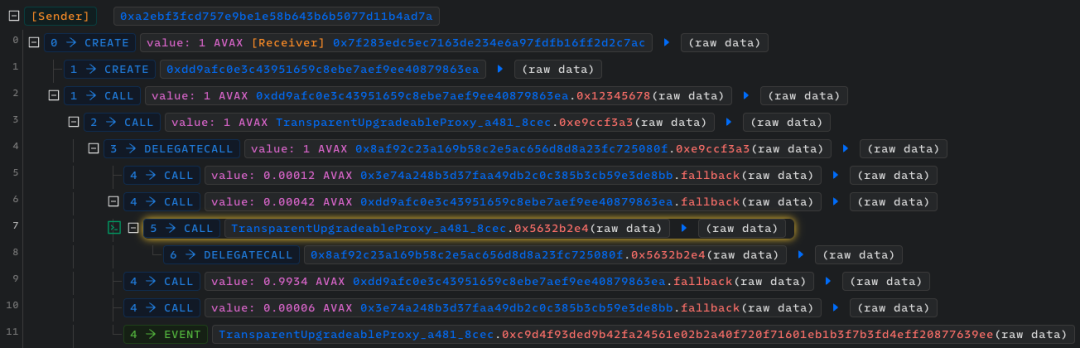
The attacker first creates attack contracts (0x7f283 and 0xdd9af) and calls the 0xe9ccf3a3 method of the Stars Arena: Shares contract through the attack contracts, then deposits 1 AVAX token.
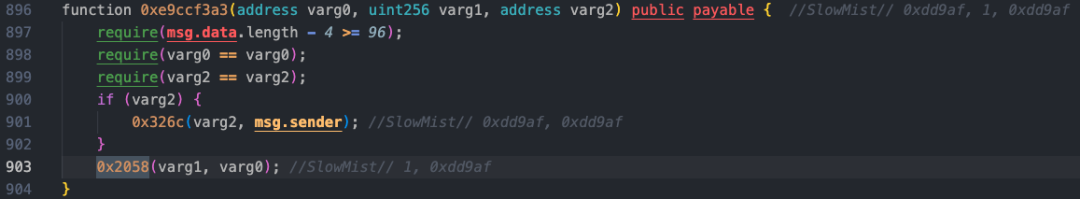
According to the decompiled code, by tracking step by step, the 0xe9ccf3a3 method used by the attacker is a function similar to a deposit, which will call the 0x326c and 0x2058 methods. The 0x326c method is only called as a parameter return, while the 0x2058 method is similar to a function that handles the purchase or exchange of a certain token. This method performs the next operation and calculates the shares and fees based on the AVAX token amount and address passed in by 0xe9ccf3a3.
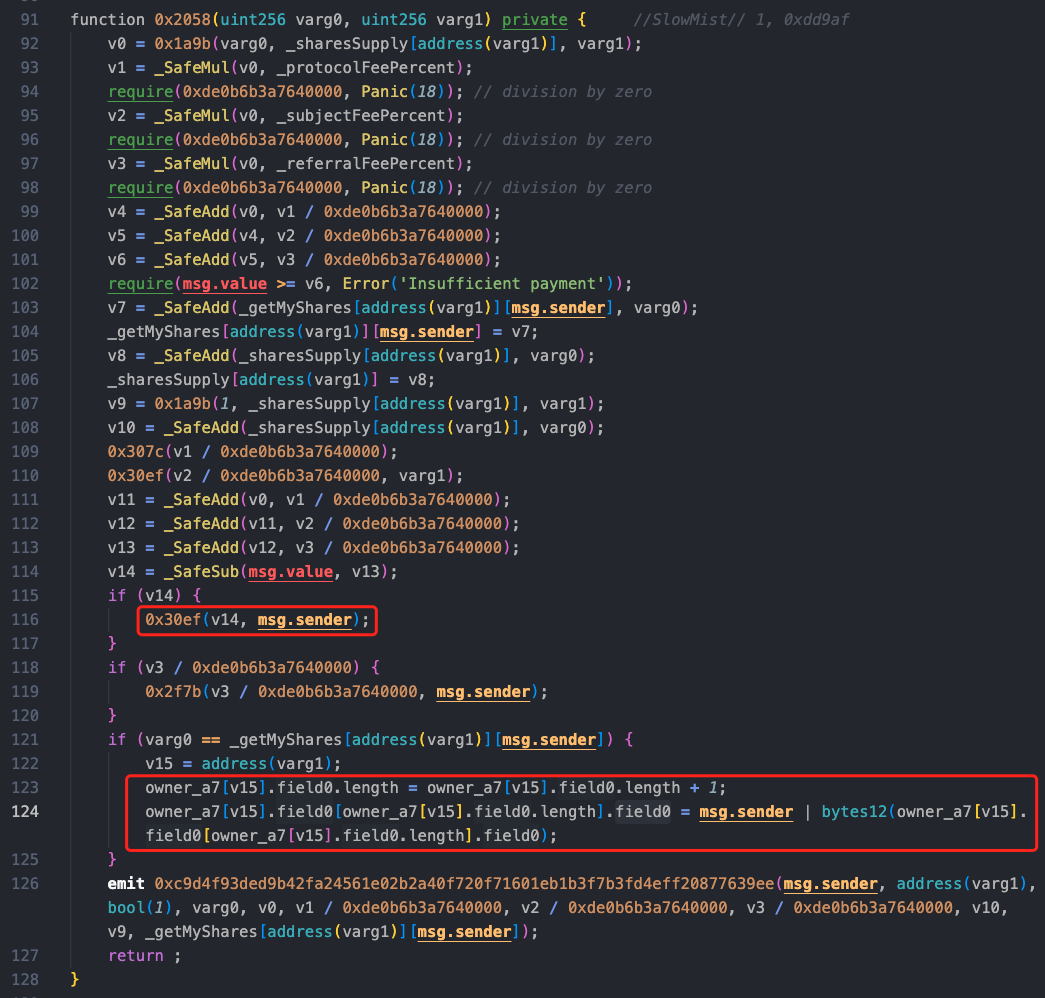
By following the call logic on line 92 of the 0x2058 method, we can see that the 0x1a9b method is a calculation function that calculates a value similar to a price, and its return value is the newly calculated v24 / 0xde0b6b3a7640000 or _initialPrice.
In lines 109, 110, and 116, there are low-level call invocations in the 0x307c and 0x30ef methods, and the call in 0x30ef is an external call to varg1, which is the address of the 0xdd9af attack contract passed in. The function has no constraints on reentrancy locks, and after executing the external call, this method will update field0.length and field0 parameters based on the subsequent if condition. Without a doubt, the reentrancy occurs at this point.
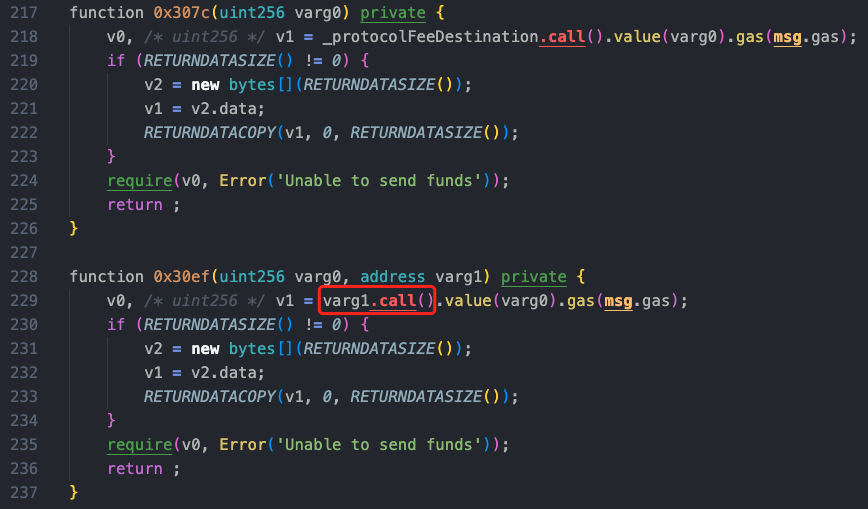
Let’s take a look at the data constructed by the attacker in the reentry call.
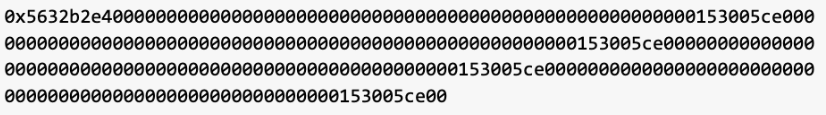
The reentry external call is made to the method 0x5632b2e4, and the attacker constructs 4 parameters, which are converted to 91000000000 by binary conversion 153005ce00.
As mentioned above, the external call to the method 0x5632b2e4 is executed before the if (varg0 == _getMyShares[address(varg1)][msg.sender]) condition. At this time, the value of field0.length is 0 and has not been updated. The attacker bypasses the condition in the method 0x5632b2e4 by this way, and modifies the states of the following 4 parameters of msg.sender, which is the attacking contract 0xdd9af, to the data constructed during the external call.
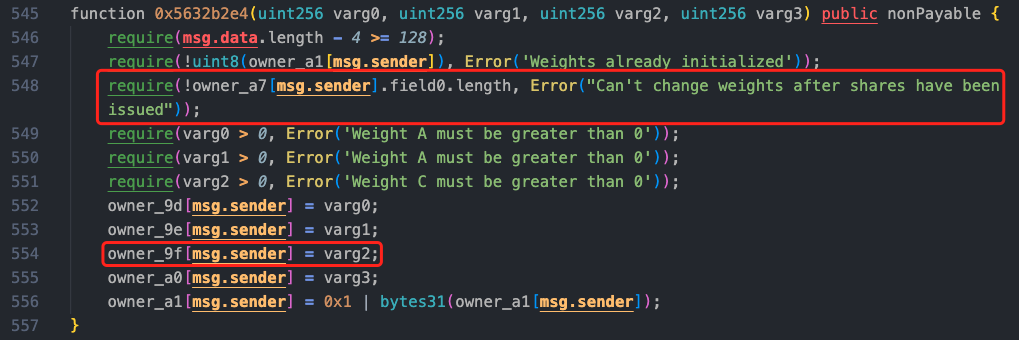
After these operations, the attacker called sellShares to sell their shares and obtained 266,102.97278 AVAX.
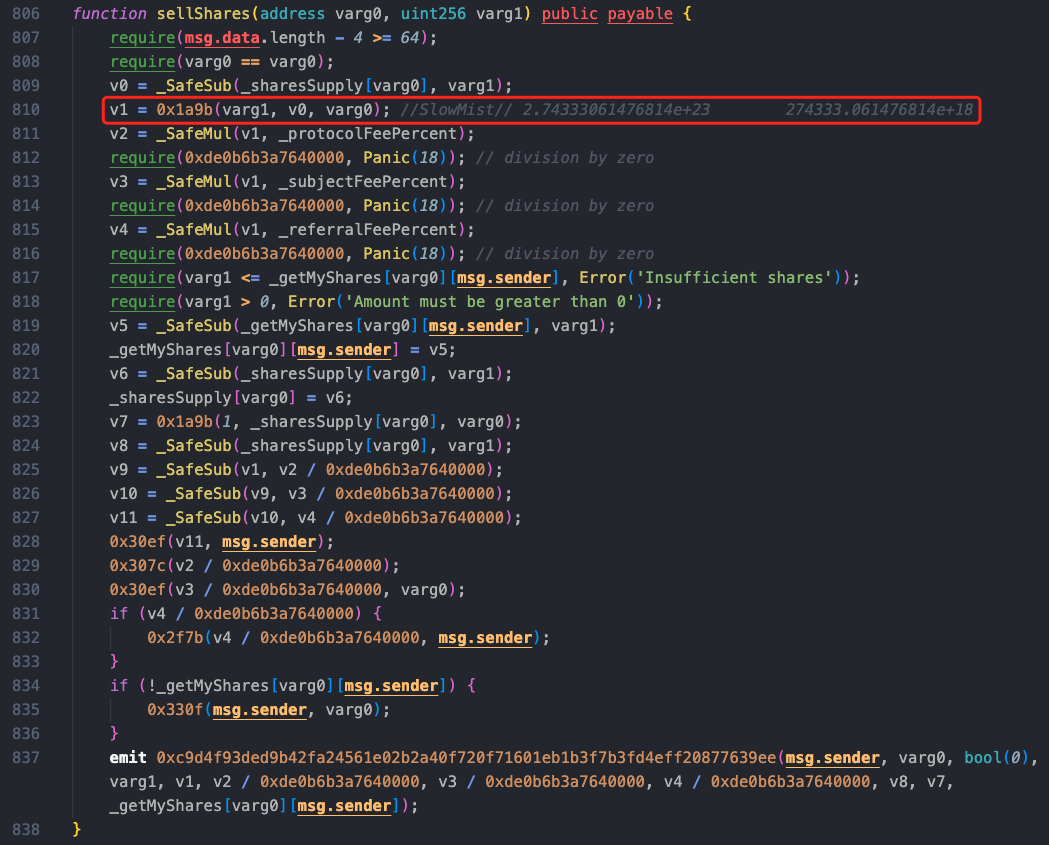
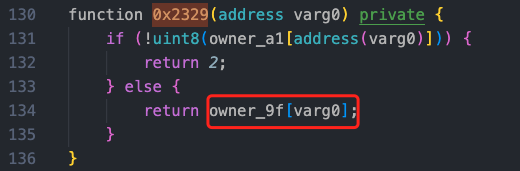
Going deeper into the sellShares function, the function first calls the method 0x1a9b, and there was a call in the previous method 0x2058, which is a function for handling token purchases or exchanges. We can see that the method 0x2329 in the method 0x1a9b will update owner_9f[varg0], and this parameter has been modified to the value constructed by the attacker, 91000000000, during the reentry.
Returning to the method 0x1a9b, the value is recalculated based on the previously constructed malicious value (the calculated amount is shown in the comments).
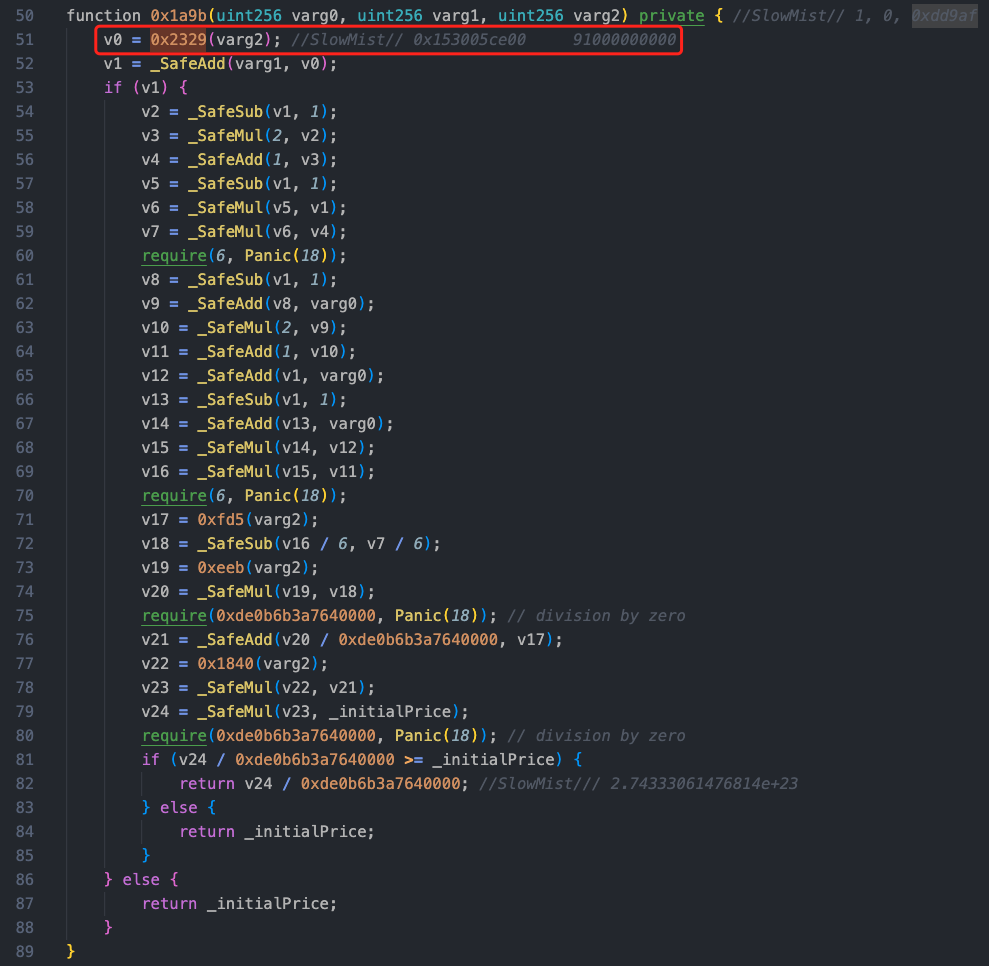
After the above calculations, the price corresponding to the new calculated shares has changed, and the result is 274,333.061476814e18. After a series of fee collections, the attacker successfully profited by using the manipulated price without modifying the shares.
Summary
The core of this attack lies in the dependency update caused by reentry attack in price calculation, which leads to similar malicious price manipulation. SlowMist Security Team suggests that project parties should deploy contracts after being audited by multiple security companies as much as possible; at the same time, they should try to meet the Checks-Effects-Interactions coding specification and add reentry locks during coding.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ethereum brings ‘bad news’ Futures ETF falls short of expectations, on-chain data at a low point
- South China Morning Post Article Why can’t the JPEX incident shake Hong Kong’s cryptocurrency vision?
- Forbes Binance’s Golden Touch, how did they turn failed ICO tokens into unexpected fortunes worth billions of dollars?
- Web3 Legal Popularization丨Can GameFi Go Online Without a Game License and Constitute Illegal Operations?
- Crypto Race Weekly Report [10/9/2023] Decrease in ETH Staking Rewards, POW Track on the Rise
- Polkadot Q3 Development Summary Native USDC will enter the ecosystem, staking and independent account data continue to grow.
- Financing Weekly Report | 14 public financing events; Web3 restaurant loyalty application Blackbird completes $24 million Series A financing, led by a16z Crypto.






