Read the digital securities and blockchain in one article: opportunities, challenges and risks
Digital securities provide an exciting use case for blockchain technology. Codefi (a product suite for DeFi business applications), like blockchain software technology company ConsenSys, is facing the challenge of digitizing and democratizing financial instruments through distributed finance. However, mastering a complex and deep-rooted system of securities and financial instruments requires a deep and detailed understanding of the current situation.
This article is a detailed account of the opportunities, challenges and risks of securities custody and digital securities through blockchain technology.
Digital hosting challenge
The traditional custodian is the representative of the beneficiary's rights. The custodian is a trusted third party that performs fiduciary duties on behalf of the beneficial owner.
- Brazil plans to abandon its existing payment system and launch an instant payment system based on blockchain technology
- Libra Association members secret: Facebook's shadow is everywhere
- Babbitt column | Bitcoin's cultural type and its historical location
The current structure exists because beneficiaries are neither willing nor able to maintain personal warehousing (due to cost and legal reasons) in CSD (credit default swaps) or trust their brokers to hold securities on their behalf. In particular, the custodian exists to protect customer securities from loss in the event of a bankruptcy of a brokerage firm.
The services provided by the custodian include: as the custodian of securities depository institutions around the world, tracking company behavior, providing balance sheets and tax reports.
The role of the custodian is the core part of fund management. The portfolio of securities managed by the fund manager can be purchased through stock subscriptions, allowing investors to enter a diversified portfolio.
Characteristics of the IMF :
- Fund shares can be sold through brokers or sold directly to customers
- Cash Exchange Fund Shares (Customer Bank or Brokerage Company Cash Account)
- The subscription and clearing records of the fund shares are carried out by the custodian through the transfer agent that maintains the ownership registration.
- The fund manager uses the net new cash to purchase new securities to the fund (if the liquidation exceeds the subscription, the fund manager sells the securities)
- Transfer agent records ownership registration and check assets with custodians and asset management companies. These reconciliations are costly and error prone.
Transfer agent role
The transfer agent retains the ownership record, including the contact information of the issuer's registered shareholder.
The broker keeps a record of the beneficiary shareholders.
The duties of the transfer agent include
- Transfer (such as recording the exchange of ownership of one or more funds)
- Issuance (issuing funds and new fund shares)
- Write off the issuer's stock
- Assisting registered shareholders in completing share transfers
Other core services provided by the transfer agent include:
- Dividend payment
- Tax report
- Annual conference service
- Direct purchase of stock/dividend reinvestment plan management
- Lost shareholder search and report filing
- Additional shares
- Stock option issuance
- Restricted stock transfer
- Representing the issuer and shareholders in communication, including sending: agent materials, statements holding asset details or statements of transaction details, tax forms, letters confirming other transactions, such as confirmation of change of address
- The transfer agent can also provide additional services to shareholders and issuers, including online account access, employee benefit compensation services, and corporate action services.
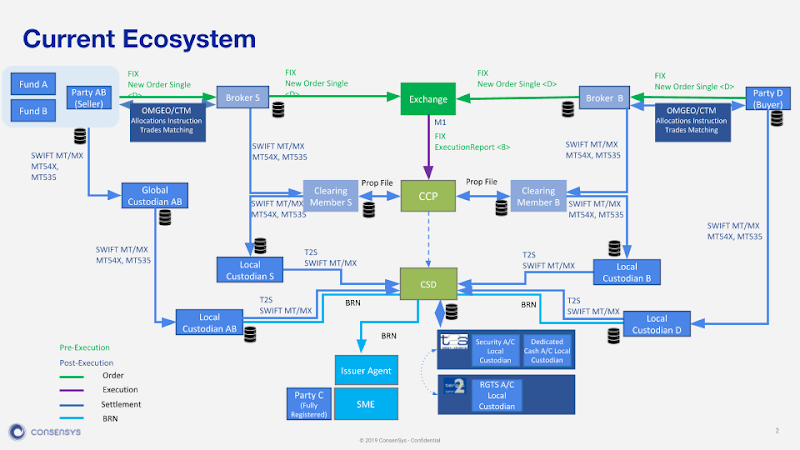
How future blockchain services will affect this function
- The ownership record of the issuer's registered shareholder (including contact information) is maintained through the blockchain registry.
- Brokers no longer need to maintain records of beneficiary shareholders: when the beneficial ownership changes, the registry will be updated through smart contract logic.
The functions of the automatic transfer agent include:
- Transfer (for example, a shareholder may require that one fund be converted to another fund on a currency, unit or percentage basis. The automated agent will then generate an exchange for the requested transfer activity)
- Issuance (original issuance of records and marking of existing assets. This may include tokens representing underlying assets, tokens representing different total holdings of the fund's strategy, and tokens representing fund shares. In addition, may also be used Cash coupons (such as stable coins) for customer shopping and automatic payment/payment procedures
- Cancellation of issuer stock
Other core services offered through smart contracts:
- Dividend payment
- Tax report
- Direct purchase of stock/dividend reinvestment plan management
- Additional shares
- Stock option issuance
- Restricted stock transfer
- Sending information to shareholders on behalf of the issuer, including sending: proxy materials, statements holding asset details or statements of transaction details, tax returns, letters confirming other transactions, such as confirmation of change of address
- Record investor-initiated net subscriptions, liquidation/redemption and transfers
- Recorded revenue for shared classes and attributes is assigned to distributors
- Track company behavior and ensure that rights are properly distributed
- Beneficial ownership of registered shares
- Communicate voting, rights, company actions, reports, etc. to shareholders
- Check fund share against net contribution/liquidation based on the fund's periodic net asset value (NAV)
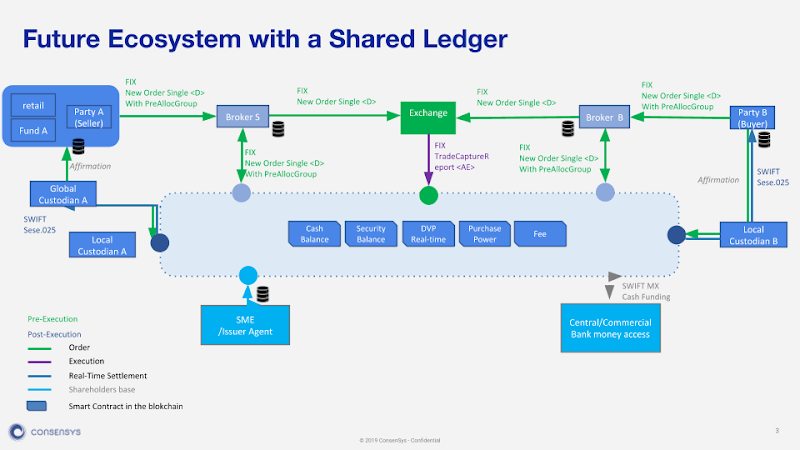
Digital securities custody
- Since the rights of shareholders are established through digital signature exchange and chain redistribution records, the traditional custodian's function (for the benefit of the owner to keep assets) is taken over by the blockchain technology itself.
- That is, even if the core registry function is taken over by technology, there are still multiple value-added hosting features. These include:
- Capture shareholder-level net activity and verify hold (this can span multiple chains representing different markets or asset classes, just as today's global custodians hold totals for customers across multiple custodians)
- Independently verify company behavior and confirm revenue attribution (such as ensuring that smart contracts are executed to design and correctly distribute revenue)
- Notice of shareholder action, such as elections, voting or other voluntary events
- Representing BO (Business Object) for regulatory and tax reporting (many beneficiaries may not want to create their own tax and regulatory reports, nor do they want to know the latest authorizations. Logically, this service can be outsourced to a trusted Three parties)
- Key escrow, key storage, key recovery (the beneficial owner wants to protect and securely store their keys and ensure that they are recoverable when they are lost)
- Maintenance and upgrade of the wallet function (outsourcing the need for wallet service updates)
- Security audit and security testing
- Compliance (suitability, qualifications, portfolio risk) (independent third-party verification of compliance functions)
Regulatory issues
US regulators have been paying attention to the challenges posed by digital asset custody recently. Traditional third-party hosting allows brokers to comply with control standards established in accordance with customer protection rules.
To protect customers, broker-dealers must demonstrate that assets are separated by ownership/control procedures to protect customers from the risk of theft, fraud or loss of broker-dealer bankruptcy. Recently, FINRA has compared the customer protection rules successfully implemented in the past 50 years with the incidence of theft and transfer of crypto-asset markets.
“In short, customer protection rules require broker-dealers to protect client assets and separate client assets from company assets, thereby increasing the likelihood that customers' securities and cash will be returned to them when the broker-dealer goes bankrupt. ”
The challenge for digital asset custody is how to ensure that keys , digital signatures, and other methods of protecting digital assets retain the basic customer protection provided by third-party hosting in the current model , retaining full control over the client's assets, allowing them to act with the agent. Completely isolated.
In the case of digital assets, the challenge is that the control of the assets is achieved through encryption keys. Currently, most cryptographic assets rely on address and key exchange, rather than ensuring that assets are not transferred or mixed by combining customer escrow agreements with broker instructions. If the key is copied or corrupted, the asset can be transferred. If the key is lost, the asset will be lost.
This challenge can be ideally solved through a combination of technical and process solutions.
For example, partial key sharing and partial key escrow may allow a user to store a portion of their key on a separate party, provided that the anonymous subscription allows the component to be assembled without the involvement of the key owner. Alternatively, the key can be hosted by dual input control so that the hosted service can only access the key if the owner requests authorization at the same time in order to revert back to the owner, for example via biometric access or some other unique authentication method. control.
This is not to say that the solution will be trivial. Regulators continue to work with brokers to identify alternatives to digital asset custody, but there are currently no common industry standards that meet both customer protection rules and ease of implementation. In other words, the potential benefits of security, the increase in capital turnover, and the friction and efficiency of digital securities provide this area an important area of discovery for the future. Companies that are the first to address this challenge may have a first-mover advantage in this area that is expected to become an important area of the financial industry.
One solution that has been explored is hardware security modules (HSMs) such as Intel SGX. However, hardware security is also limited: HSM is a relatively fragile solution, because if a security flaw is discovered, physical hardware may need to be replaced, which creates a greater logistical burden than a software patch.
Digital hosting considerations
Institutional customers with higher risk values are generally more inclined to choose and optimize security than convenience. Protecting assets is critical, but security solutions can't be too cumbersome to negatively impact trading capacity in fast markets. This may be related to cold storage and multiple independent security controls
The solution is versatile. Often, asset owners or their custodians will try to use different forms of security from the exchange, and will likely also use different forms of security for brokers who trade with them to add a second defensive hacker attack. Line of defense.
In some cases, a custodian may choose to use a combination of hot storage and cold storage: hot storage is used for transactional mobility and deployment speed, and cold storage is used to prevent catastrophic loss of hot wallets when hacked. The customer's liquidity requirements and their trading patterns will affect the balance or UTXOs stored in each type of wallet.
However, any hybrid solution is particularly vulnerable when assets are transferred. Many hacking attacks occur when dealing with wallet transfers.
The unresolved questions are: Can the broker access digital security? Is digital security transferable or redistributable without the final beneficiary's affirmation (by key exchange or digital signature)? Can the key be replicated? Since the traditional model assumes that effective control is equivalent to exclusive control, it implies a secure method that proves that control capabilities (such as keys) are not replicable. This is inconsistent with the way most current key solutions are designed. Before this issue is resolved, there is still a barrier to widespread adoption of digital securities that protect the rights of existing investors.
Is it possible to cancel the role of the transfer agent? If the transfer of ownership requires positive affirmation by the ultimate beneficiary and the method of transfer is unique and cannot be repeated, then it is possible to eliminate the use of the transfer agent. However, achieving this result faces significant technical challenges.
risk
The custodians of traditional securities markets assume several important risk management functions for asset owners. These risk management functions need to be met by equivalent functions in the field of digitally tagged assets:
- Counterparty risk
- Loan risk (mortgage and re-mortgage)
- Mixed assets and traceability
- In addition, managed services may help manage the additional risks specific to smart contracts and digital securities:
- Theft or theft of the key
- Loss of key
- Unexpected logical path and coding error
Other challenges
In addition to these risks, there are many core competencies that need to evolve to a certain degree of certainty and assurance to meet the authority of the regulatory body. Each of them needs to be developed not only independently, but also to a certain degree of integration to ensure a coherent and integrated whole.
These challenges include:
- Identity and participation. How to uniquely identify a participant and bind it to a digital signature; how to create and assign addresses and nodes;
- Governance and dispute resolution; what kind of consensus and voting methods will be used to guide the market; how voting rights will be established; how disputes will be resolved.
- Legal authority and enforceability. How the automation of intelligent contract logic for digital securities will be tied to the choice of regulatory law; how to arbitrate differences in interpretation; in the case of unexpected results in coding logic, each smart contract needs to cite a separate legal agreement.
- How the managed network will communicate with other networks . Includes markets and exchanges that may not be based on distributed ledgers; what messaging standards and technology solutions are required (such as guaranteed delivery or broadcast channels).
- How designers of new automation solutions will ensure that they are in sync with evolving legal standards and existing business logic . Incorporating existing single-party business logic into complex multi-party logic systems can accelerate the development of new logical models;
- How technology solutions based on atomic swaps and near real-time settlements will evolve to accommodate the liquidity savings benefits of deferred billing and netting; how best to support lending and mortgage models.
- Whether digital assets comply with the security definitions that apply to SIPA protection . If a digital asset claims to have a future value added or future cash flow, the asset is likely to be classified as a security. The value of utility tokens lies in the services/utilities they provide for funding and access, it may not be digital securities, and it is likely that SIPA protection will not be extended.
- Is it possible to determine whether a broker dealer owns or controls digital asset securities .
- How to protect the key ; can the key be copied ; how to handle the key escrow, and whether the access key needs to be verified .
- Whether the distributed ledger is an authoritative record of stock ownership .
- The ledger is the only recording system, and there are still other ways of ownership . Native digital security may be able to prove the status of a single authoritative record by a complete chain of ownership from the outset, but the flagged regular assets may not. For example, if an asset is tagged, rematerialized, and then tagged, the complete source chain may not be preserved. In addition, the method of marking traditional assets must prevent double spending, in which case the token issuer will be obligated to prove that if the asset is associated with the corresponding token, the asset cannot be removed from the hosting. Otherwise, there may be a situation where equity is duplicated and expenditures are doubled.
- Does the broker or executing agency need to use the transfer agent as the proposed “control location” to meet the ownership or control requirements under the customer protection rules? For example, when the issuer or transfer agent maintains a traditional single security holder list, Whether the role is enforced when using the distributed ledger technology to also publish ownership records.
Original link:
Https://media.consensys.net/digital-securities-and-blockchain-custody-and-fund-administration-905a449569cb
Author: Clark Thompson
Compile: Sharing Finance Neo
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Babbitt column | Questioning and thinking about Staking: Why is it not a good model?
- Opinion | ZEC and XMR: Privacy is important, but it is not all
- IMF's point of view: "Synthesis of central bank digital currency" will be the future central bank currency?
- Bitcoin position analysis: the collapse of the market, the characteristics of various accounts are obvious
- Blockchain entry | Blockchain 51% power attack is not so terrible
- Detailed explanation of the FundWin vulnerability system: Can the project party be suspicious of “doing evil”?
- 8Q | Don't open the scene: Big coffee gathers DVP, big white hat and hacker






