Research | The Value Capturer after the Fat Protocol Era——Middleware Protocol
Guide
1) We believe that middleware projects can integrate network resources through compatibility with many underlying blockchains like the HTTP protocol of Web 2.0 , while creating value for many DApps .
2) The middleware project itself can be sandwiched between the top-level application and the underlying blockchain architecture: connecting the top applications, integrating the underlying encrypted network resources, and finally achieving resource sharing, function sharing, and DApp developers Provides great convenience.
3) There is a lot of interoperability and composability potential between the protocols and protocols in the financial middle layer, which can allow some derivative application scenarios to emerge. Sinking, combinable and modular. Their greatest value in the future is to provide a basic framework and basic business logic for many top-level applications.
1.0
Viewing the middle layer protocol from the perspective of traditional Internet value distribution
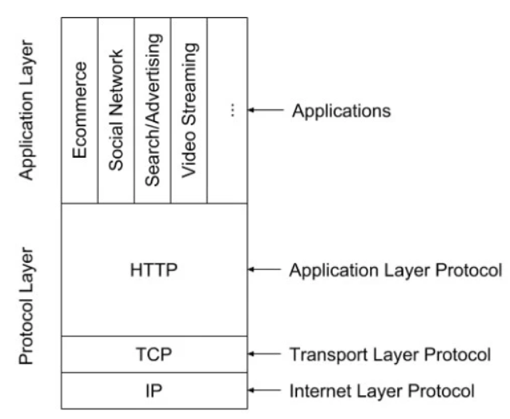
On the one hand, although most of the value of Web 2.0 is created by middle-tier protocols, since protocols such as HTTP are free standards, the value they create is actually stolen by various applications. In the era of Web 3.0, the unique creation of Token completely subverted the value delivery model: the native Token in the middle stack gave them the ability to capture value.
- Inspiration of stablecoins: analysis of the "Black Thursday" crisis and construction of a new borrowing and buffering model
- Bitcoin as ransom, WannaRen ransomware hits twice
- "Digging" 500 years to recover the cost of equipment? V God calls HTC mobile mining a fool's game
On the other hand, Web 2.0 mainly relies on the huge HTTP protocol to support the most influential applications, but there will be a wide variety of protocols in the middle layer stack of Web 3.0 to support top-level applications. The reason for this difference is that the main applications or business areas in the encrypted network need their own unique Token economics design, so they need a unique protocol to integrate the Token economics of the application.
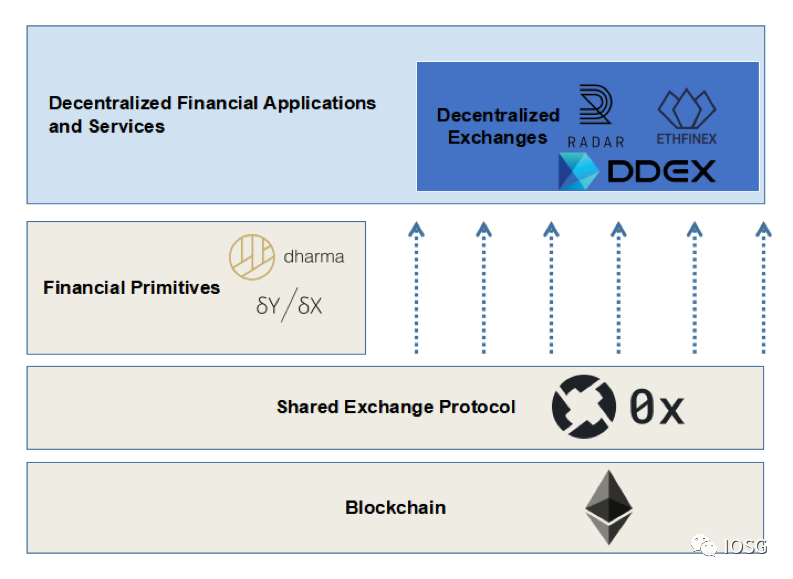
2.0 Middleware Stack
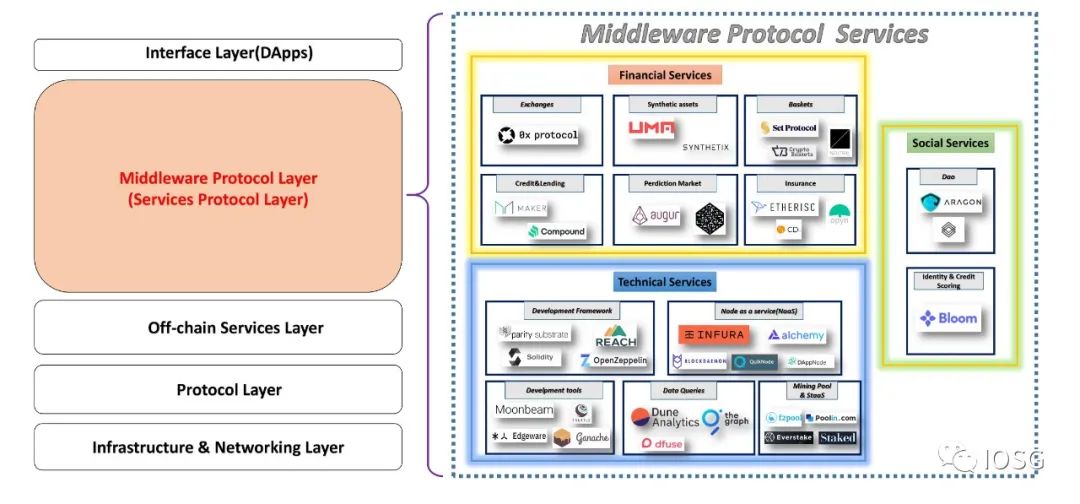
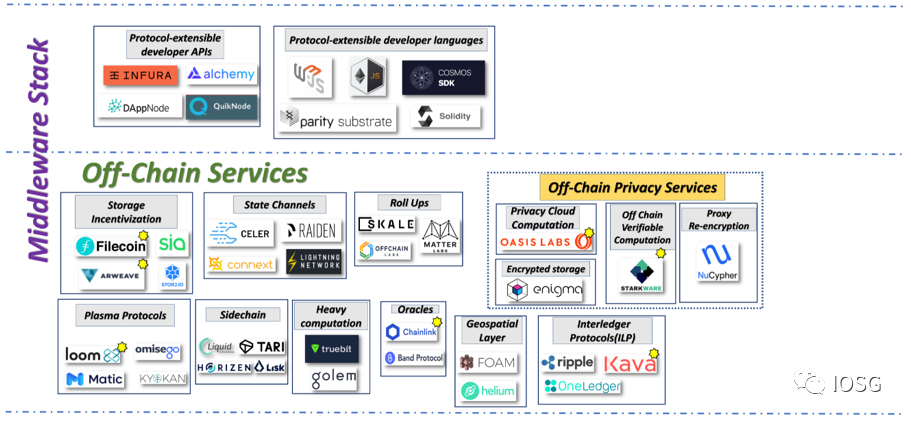
3.0 IOSG VC modular reconstruction of the middleware stack
Representative projects: Solidity, Substrate, Reach Platform
Take the Substrate development framework promoted by Parity as an example. It is a scalable and modular open source framework that can quickly build a blockchain. Its core components include: a database (simple key-value storage and implementation of PatricaMerkle Tree to support lightweight Trustless interactions between clients, network connections, transaction queues, and consensus engines (such as PoW, Aura (Authority Round), and Polkadot consensus).
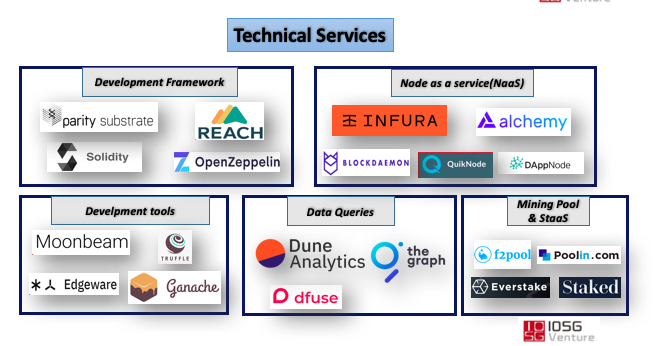
II. Node Service Operator (NaaS)
Representative projects: Infura, QuikNode, BlockDaemon, Alchemy, DAppNode
For example, Ethereum Infura provides node services to projects such as Metamask, 0x, Mycrypto, Maker, Idex, etc. These projects rely on Infura to broadcast transaction data and smart contracts to the mainnet.
III. Data Index and Query API Service (Data Query and API)
Representative projects: The Graph, Dune Analytics, Dfuse, Infura
lV. Smart Contract Development Tools
Representative projects: Moonbeam, Edgeware, truffle, ganache
V. Mining & Staking as a Service
PoW representative projects: Poolin, F2pool, BTC.com
PoS representative projects: Everstake, Stake.fish, Wetez
The mining pool under PoW connects the physical computing power of the individual mining machine to the address of a blockchain mining pool, and then realizes large-scale and simple mining and reduces the mining threshold. The Staking as a Service service provider of PoS also lowers the staking threshold: one is the professional threshold (maintaining the normal operation of the node); the other is the threshold of economic costs (not lower than the lower limit of the number of pledged tokens or unable to participate).
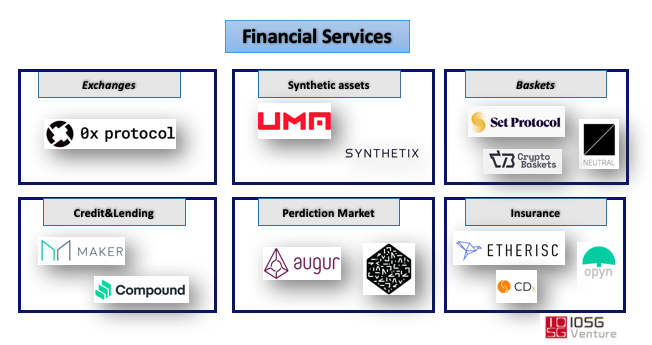
Representative project: MarkerDAO
II. Decentralized transaction agreement
Representative projects: 0x Protocol, Loopring
Representative projects: Synthetix, UMA
UMA is a decentralized financial protocol based on Ethereum. It is a business agreement that connects both bulls and bears. UMA provides a smart contract template that allows anyone to create a synthetic asset that tracks the price of any value subject. Its mechanism is very simple, anyone can create tokens that track the price of anything in Synthetic Token Builder based on UMA Protocol, from foreign exchange rates to stock prices. A successful case is currently based on the stable currency tracking index SwanDAI created by Synthetic Token Builder. SwanDAI is a synthetic asset that tracks the deviation of the price of DAI from its US dollar in an exponential growth mode. 100 times up), the contract will be delivered at the exponential price when it expires, so it can let people hedge the risk of DAI decoupling the dollar.
II. Forecast Market Agreement
Representative projects: Augur, Erasure
Erasure Protocol is a protocol developed by the hedge fund competition platform NUMERAI. The protocol has a series of key primitives with a wide range of application scenarios, including record tracking, payment and recourse . These three economically formed primitives are deployed on the Erasure basic template , Anyone can use it when building web applications. So far, Erasure has developed two applications, Erasure Quant and ErasureBay, based on the agreement.
III. Decentralized Insurance Agreement (Insurance)
Representative projects: Etherisc, Opyn
Opyn's ERC20 option agreement Convexity Protocol provides users with financial insurance services using the concept of financial instruments. We believe that the credit default swap agreement and option agreement they have launched are very likely to serve as the middle-tier agreement in the field of DeFi financial insurance. Derived a wider variety of end-user financial insurance products.
IV. Token Package Agreement (Baskets)
Representative projects: Set Protocol, Bskt, Neutral, Crypto Baskets
Representative projects: ARAGON, DaoStack
We use Aragon as a middleware agreement because it is actually a DAO project that is more focused on providing a secure and universal backbone network for the formation of general organizations, rather than building products around specific decision-making mechanisms. By leveraging the foundation established by the Aragon team, end users only need to use the tools provided by Aragon to quickly form an organization that meets their own specific specifications (see Figure 7).
Representative project: Bloom
Bloom Protocol is an identity authentication protocol based on Ethereum, which can be used to develop credit-related products such as identity verification, risk assessment, and credit scoring.
4.0 Value attributes of middleware: network resource integration, token value transmission and protocol composability
On the one hand, based on our understanding of the middle layer protocol , we made a classification and combing of the specific subdivision direction of the middleware protocol in the encrypted network. With the Web 3.0 we did at the end of 2019, our understanding of the middle layer stack Some important updates have been made:
1) Reclassify the on-chain and off-chain protocols among the middle-layer protocols . The purpose of this is to abstractly classify the complicated and complex protocol functions in the middle layer protocol, so that developers can stand in a higher dimension to think about the problem.
2) Separation of on-chain protocols and off-chain services We can more clearly see that many on-chain protocols are composable , which is particularly evident in the open financial ecosystem of Ethereum. These middle-tier protocols related to open finance are not involved in the Web 3.0 technology stack in 2019.
On the other hand, on the basis of the fat protocol theory , we believe that the middleware protocol can absorb the value of network security through the compatibility of many underlying blockchains like the HTTP protocol of Web 2.0, while creating application value for many DApps. The reasons are as follows:
1) The emergence of interoperability protocols (such as Polkadot, Cosmos) enables state and value to be interoperable on different blockchain platforms . Because middleware is not limited to a single blockchain, it can steal value from compatible blockchains. Although the blockchain protocol is fork-free (because most protocols are open source), the mentality and network effects of all users may not be able to migrate to a brand-new protocol in a short time (the new fork protocol cannot be The network effect of completely inheriting the original agreement in time, according to history, in most cases can only be the inheritance part). So when the middle layer has visibility, brand and users on a certain blockchain, if it is newly compatible with a blockchain and provides services for it, then its network effect on other blockchains (awareness, brand, users) Etc.) may give it some advantages in the new chain.
2) The interoperability and composability of the protocols and protocols can potentially lead to some derivative protocols . For example, we can see that on the basis of 0x Protocol, there are also protocols like dy / dx, dharma. We found that most of the DeFi protocol projects have played a more and more sinking, composable, and modular role in the open financial ecosystem. Their greatest value is not in providing user-friendly UX and UI directly. Instead, it provides efficient product development logic for the top-level End-user Interface level Dapp on the one hand, and on the other hand, due to the Lego-style composability between modules, some new application scenarios have been spawned. All of these have led to the "protocol" projects that have actual use scenarios, which have great value for investment.
3) There are quite a few protocols in the middleware stack that play an important role in "token value transmission". These middle-tier protocols all bundle value with their native tokens through methods such as mortgages, commissions, and royalties (such as in MakerDao Mortgage the underlying asset ETH to obtain the stable currency DAI, and then need to pay Maker's native token MKR as a rate to stabilize the DAI price). The economics created by this incentive and differentiated middle-tier protocol may be much larger than the economy created by the bottom layer of the blockchain driven by calculation, in other words, the tokens in these middleware protocols are captured The huge value of will far exceed the tokens of any blockchain.
5.0 References
https://www.placeholder.vc/blog/2019/2/14/the-defensibility-of-middleware-protocols,2019-02-14.
[2] Lang U., Gollmann D., Schreiner R. (2001) Cryptography and Middleware Security. In: Qing S., Okamoto T., Zhou J. (eds) Information and Communications Security. ICICS 2001. Lecture Notes in Computer Science, vol 2229. Springer, Berlin, Heidelberg
[3] Maurizio Canton. Why Middleware is the Vital Link for Blockchain Success [EB / OL].
https://financialit.net/blog/why-middleware-vital-link-blockchain-success, 2017-03-23.
[4] Henry He. Blockchain in 2019 will be all about the middle-layer protocol [EB / OL].
https://venturebeat.com/2019/01/26/blockchain-in-2019-will-be-all-about-the-middle-layer-protocol/,2019-01-26.
[5] Howard Yuan. Web 3.0 develops a new engine: These Layer 3 middle-tier blockchain companies deserve attention [EB / OL].
https://www.chainnews.com/articles/435967841809.htm, 2019-12-12.
[6] Clayton Roche. Why is DeFi Crazy for Synthetics? [EB / OL].
https://www.asiablockchainreview.com/why-is-defi-crazy-for-synthetics/,2019-09-25.
[7] FlatOutCrypto.The Open Finance Series Part 1: MakerDAO [EB / OL].
https://hackernoon.com/the-open-finance-series-part-1-makerdao-9be14ef1066c, 2018-09-12.
[8] Kyle Samani.On Value Capture at Layers 1 and 2 [EB / OL].
https://multicoin.capital/2019/03/14/on-value-capture-at-layers-1-and-2/,2019-03-14.
[9] David Hoffman.Ethereum: The Digital Finance Stack [EB / OL].
https://medium.com/pov-crypto/ethereum-the-digital-finance-stack-4ba988c6c14b, 2019-07-25.
[10] Kai Wähner. Blockchain – The Next Big Thing for Middleware [EB / OL].
https://www.infoq.com/articles/blockchain-middleware/, 2016-12-12.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Learn about Utreexo, an improved MIT Bitcoin solution in 5 minutes
- Babbitt Column | Essential Knowledge of Encrypted Digital Currency Wallet: Divide Wallet Types and Their Advantages and Disadvantages by Terminal
- Observation | How have Chinese insurance technology giants used blockchain to transform?
- New Path of International Cooperation for Chinese Enterprises Against Globalization: Blockchain Industry Alliance
- This is the real blockchain! Tens of billions of dollars are put here, 4 industry experts bring you first-line experience
- FBI warning: under the new crown epidemic, beware of four encryption scams
- QKL123 market analysis | New days of global diagnosis? American Oolong! Data those things (0414)




