Technology Sharing | Synergy between Cryptography, Blockchain and Privacy Computing
Hashing theory
No privacy, no insurance? Privacy computing constitutes a moat that users trust, and the hero behind privacy computing is cryptography, which is also one of the foundations of blockchain technology. What kind of synergy does the three have?
In the third lecture of the private computing class last night, Wu Xiaochuan, a blockchain technology expert of Zhongan Technology and the director of Fudan-Zhongan Blockchain Laboratory, interpreted the basic logic of cryptography and its The application of privacy computing technology, through the blessing of cryptography, has a good landing direction and case in the avatar identification of finance and insurance.
The main function of cryptography is encryption and decryption. If the encryption and decryption are divided into two parties, it can be seen that the current encryption party has won, because the passwords we have used have not been found a good attack method or cracked. method. Encryption is mainly divided into symmetric encryption and asymmetric encryption. Symmetric encryption requires only one key, which is efficient but has certain risks. Asymmetric encryption uses one key to encrypt and the other key to decrypt, eliminating the symmetric key. Risk of key leakage. The public key encryption used in information authentication is the electronic signature, which is also a core cryptographic algorithm used in the blockchain.
- Security Monthly Report | More than 17 typical security incidents occurred in March, the prospects and risks of Ethereum Defi coexist
- QKL123 Blockchain List | USDT market value jumped to fourth place, transaction popularity dropped significantly (March 2020)
- Opinion | Zhongjing Jinchuang Zheng Runxiang: RMB internationalization should establish a mechanism for applying RMB digital currency in the field of commodity trading
In modern cryptography, quantum computing has been a hot topic in recent years. From the paper published by Google last year, quantum computing has been greatly developed than before. The paper shows that the possibility of expanding computing may unlock a brand new Calculate ability. However, quantum computing still has a long way to go, requiring years of arduous engineering and scientific research.
1
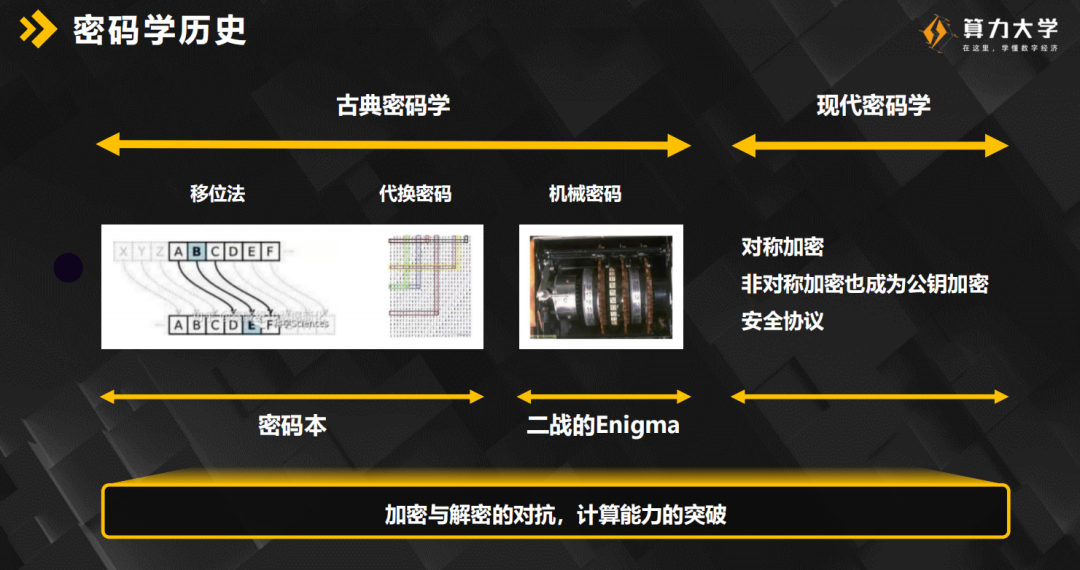
Basic knowledge of cryptography in blockchain The elliptic curve is not only the foundation of blockchain cryptography, but also the foundation of modern cryptography.
How do elliptic curves get the public key in the blockchain? First, a random number K is randomly selected. K is less than the order of the selected cyclic subfield on the elliptic curve. A point is obtained by multiplying K and a base point scalar. This point is called a public key. Generally speaking, the compressed public key and non-compressed public key we heard need to take the X value at this point, and the uncompressed public key needs to take the concatenation of X and Y. After obtaining the public key, it is still different from the address on the blockchain we have seen. We still need the public key to go through several hash algorithms, and then base58 encoding, and finally get the address of the blockchain .
The signatures involved in the blockchain are mainly BLS Signatures and ECDSA. ECDSA is the elliptic curve and electronic signature used in the earliest blockchain projects, and BLS is the signature used in some projects that we often hear recently. The biggest difference is that the BLS signature is shorter and more efficient. ECDSA calculation is more complicated than BLS, which requires the use of random numbers, and the efficiency of signature generation and signature verification is low.
For more dry goods on blockchain cryptography, you can scan the QR code at the end of the article to watch the full course video.
2
Blockchain data privacy protection When it comes to the blockchain, it is easy for everyone to get involved with privacy, and everyone also thinks that the blockchain may solve the privacy problem. In fact, this is a misunderstanding. The only thing that can be done in the blockchain is anonymity, but it does not solve the privacy problem, because all the nodes of the blockchain need to be verified or calculated, which means that they need to get the full amount of data. This data is actually not protected by privacy. What data on the blockchain needs privacy protection? The data on the blockchain can be divided into three categories: native data, off-chain data, contract data / interactive data, the latter two are private data that really need to be protected, and both belong to the category of off-chain data. So how does the blockchain protect such data? At present, the technologies commonly used in the industry are zero-knowledge proof, trusted computing and other technologies, and the answer can also be found in the course video.
3
New methods of privacy protection brought by distributed ID and blockchain Data privacy is actually a subdivided field in the field of data security. Data privacy refers more to the privacy of personal information. The protection of personal information is very strict around the world, especially in Europe and the United States. The most famous are the GDPR General Data Protection Regulation and the CCPA California Consumer Protection Clause.
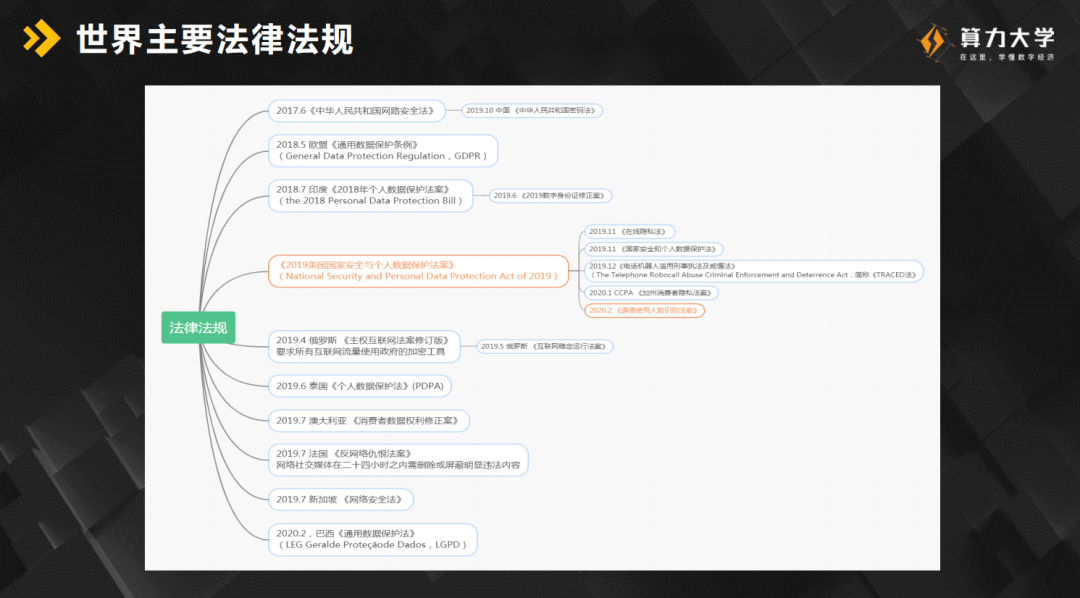
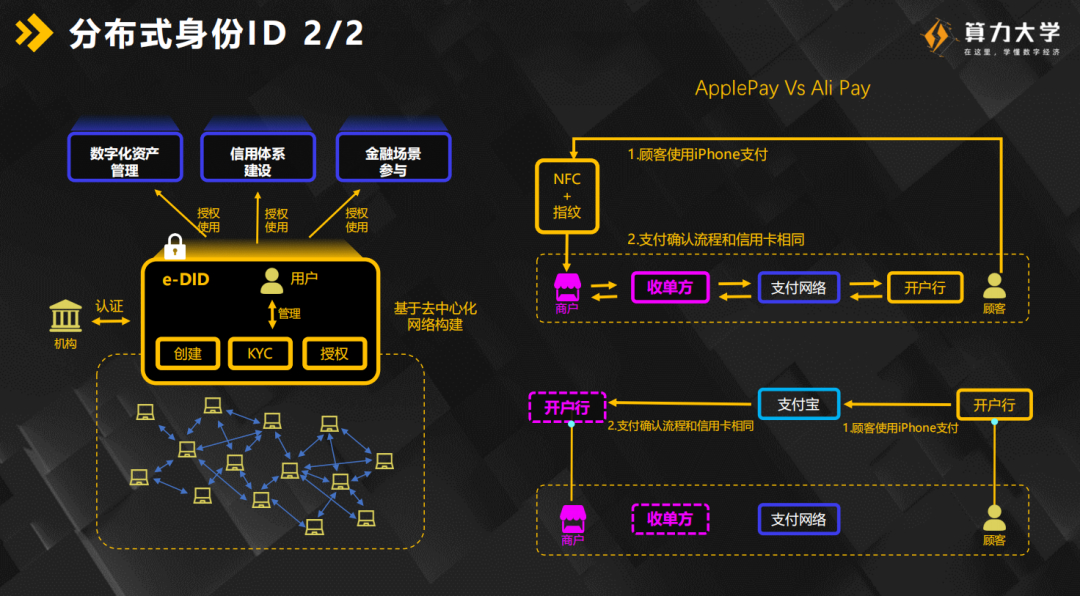
The GDPR strictly stipulates that the user, the data subject, has the right to access data, the right to know, the right to prohibit third-party sharing, and the right to refuse. Moreover, data controllers, which we call service providers, must clearly provide these services to users so that users can access settings at any time and be able to change these settings at any time. There are also detailed introductions on personal privacy protection aspects and some protected products in the use of software. In the protection of personal information, distributed IDs have become popular recently. The most basic logic is to re-set a set of identity IDs for each entity. For example, for any activities we are engaged in on the Internet, our mobile phone numbers are now converted Another kind of number, our ID card information is transformed into another ID card information, we use a new set of identity system to use in our existing system. The analogy with insurance is that during the process of purchasing insurance, the information filled in by the user is some other identity system. However, for this other identity system, there must be a central agency that will "Identity system" maps with the actual identity system. Who provides the mapping? It must be an institution with public authority. For example, insurance is a banking and insurance supervision institution to provide a mapping between a real virtual identity and a real identity. Even if a new virtual identity system is created, if this system is reused in large numbers many times, this new identity system can be analyzed to locate this person. In fact, the combination of distributed ID and blockchain can well replace the centralized organization to map the identity system. How to do it is also mentioned in detail in the course.
Although cryptography is developing very fast now, we can see that computing, encryption, security, multi-party computing, and zero-knowledge proofs are all developing. We can deeply feel the great promotion and application of some cryptographic algorithms. For example, in the early promotion of cryptography, it may take 10 years, and now it may only take three or four years.
But it is still very difficult to rely on cryptography to promote or popularize to achieve large-scale commercial use. How to solve the problem of data silos in the information age and how to make this data invisible, but where available, to better empower the enterprise and better serve the customers is the problem we are exploring to solve.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- The People's Bank of China: unswervingly promote the research and development of legal digital currency
- Blockchain Application Case: Eliminating Hype
- Viewpoint | Cheng Xiaoming, "Godfather of the New Three Boards": What are the pain points of enterprises that can be solved by blockchain "chain reform"
- What can a blockchain do for various companies?
- Blockchain changes production relations? Big data is not ready to serve as a means of production
- How does blockchain help security on the tip of the tongue?
- Interview | Weizhong Bank Blockchain Security Scientist: Strictly adhere to the privacy data red line, business innovation compliance