The theft of the "codebook" in the war movie is serious. Is there such a thing in the blockchain?
Author | Seeds
Production | Vernacular Blockchain (ID: hellobtc)
Xiao Hei and Da Bai just watched "Midway Midway", while they were sitting in the theater lounge and chatting.
"What do you think of the victory of Midway Island, in addition to the bravery of the players?"
- Guangming Daily: "Blockchain" is not so profound, it is actually around us
- On the future of electronic money: What will the currency system look like in 2070?
- Blockchain Science Fiction: "Computing Power" (Part 1)
Dabai thought for a while, "Well, is that the intelligence department?"
"Yes, the battle on Midway Island is an outright intelligence victory. Fortunately, it happened 36 years ago, when asymmetric encryption technology had not yet appeared, otherwise it was another situation.
After listening to their chat, Xiao Hei became very interested in asymmetric encryption. Today we will talk about what is asymmetric encryption?
Symmetric encryption is also called single-key encryption, which means that the same key is used to encrypt and decrypt information. The disadvantage of symmetric encryption is that the key distribution is difficult, and it is intercepted by the enemy. Just like our house keys, both the lock and the unlock are the same, and if you accidentally stole it, you were hit. "
Asymmetric encryption has a pair of keys, which are a private key and a public key, which are encrypted and decrypted with each other, that is, public key encryption, private key decryption, or private key encryption, public key decryption . The private key needs to be kept secret and kept in a safe place. Only you know it, like a bank password. The public key can be made public, just like our public bank account number.
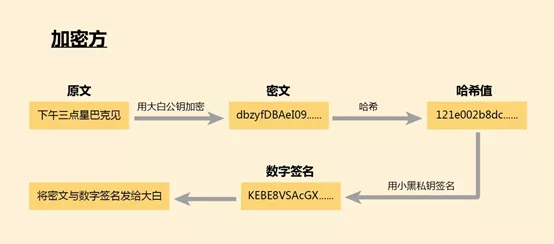
For example, we now have a pair of keys: a public key and a private key, and we have agreed to meet at Starbucks at 3 pm . I now use your public key to encrypt and get a string of ciphertext, and then hash this ciphertext to get a string of hash values.
I then encrypted the hash with the private key again to get a digital signature. By the way, encrypting with a private key is also called a digital signature, which is different from our electronic signature at the bank counter. After you do this, send you two pieces of information: ciphertext and digital signature.
How can I decrypt it after receiving the information?
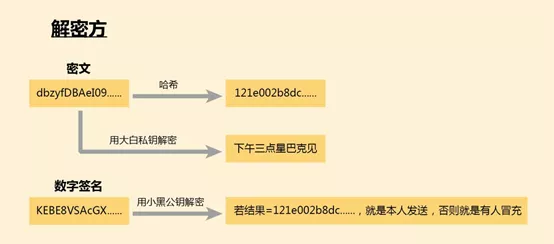
First look at the digital signature in the figure below. You can decrypt it with my public key. If it can be decrypted, it means that the information was indeed encrypted by my private key, and it was me and not others. "
Even if someone knows the hash value, it's useless. He doesn't know the original text. The purpose of signing with a private key is to indicate my identity. In daily life, we often use signatures to indicate that I agree to a contract, which is to verify my identity. If this step is gone, just like someone just signed my name on the document, it must be messy.
"Identification is OK, what about decrypting the original text? "
In this cipher text, do you say that no one has tampered with it, after all, who can send messages to me? You hash it once, you get the hash value, and compared with the hash value decrypted by the public key just now, the same is that it has not been tampered with.
The final step is to decrypt the ciphertext with your private key, and you get the original text, and you're done.
In which aspects of life do you think asymmetric encryption will be applied? Welcome to share your views in the message area.
——End——
"Disclaimer : This series of content is only for the introduction of blockchain science popularization, and does not constitute any investment opinions or suggestions. If there are any mistakes, please leave a message to point out. Article copyright and final interpretation rights belong to the vernacular blockchain. A
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- KPMG launches KMPG Origin, a blockchain traceability platform, to improve transparency in multiple industries including financial services
- National University of Singapore Visiting Professor Bai Shifang: FinTech Promotes Tech Finance
- Shock! No one in Japan uses Bitcoin! | 8 Questions
- Ethereum 2.0 client enters code security audit phase, testnet will be released next week
- Can EOS 'centralization problem be solved by sharding?
- Why do more people prefer deflationary cryptocurrencies?
- QKL123 market analysis | Look at the degree of price deviation through these two indicators (1129)





