After Vitalik’s account was hacked, he released phishing information. Besides phishing attacks, what other ways of fund fraud should users be alert to?
After Vitalik's account was hacked, he warned about phishing attacks. What other types of fund fraud should users be cautious of?On September 10th, Ethereum co-founder Vitalik Buterin’s X platform (formerly Twitter) account was hacked, and a phishing link was posted. The content of the link was a commemorative NFT giveaway related to Danksharding. Although the tweet was quickly deleted, the hacker still managed to steal about $700,000 in funds.
Earlier in July, Uniswap founder Hayden Adams’ X platform (formerly Twitter) account was also hacked, and a tweet with a phishing link was posted. This shows that there are still frequent security incidents such as phishing attacks in the blockchain ecosystem.
Previously, Beosin has provided a detailed analysis of phishing attacks, which you can read for more information:
UNIBOT is on fire, how to prevent phishing and fraud related to Telegram bots?
- Opinion If the Bot track cannot achieve an unforkable state, it will be very difficult to achieve sustainable revenue.
- Will Micro-Rollup be the next wave when applications become Rollup?
- Inventory of Common Scams in the Cryptocurrency Field
Has your signature been stolen? Be cautious if you have used Uniswap! Revealing the Permit2 signature phishing scam.
Apart from phishing attacks, there are other types of fund scams that users should be wary of. Recently, the Beosin team has discovered that exit scams and price manipulation events have also caused significant losses to users’ funds.
As blockchain technology becomes more mature, there are fewer code-related issues, leading to an increase in scams and problems in business logic. In this article, we will list some common fund security issues that have occurred recently to help users avoid being deceived.
In recent cases of exit scams and fraud, perpetrators mainly use methods such as contract backdoors and pyramid schemes to defraud funds. However, users can actually avoid these methods by understanding how contracts operate and the principles of the code. We will use recent projects as examples to explain and summarize the characteristics of such scams.
I. Considerations for project backdoors:
1. Modifying balances through privileged addresses:
Projects involved in scams usually have a privileged address that can freely mint, burn, or modify the balances of others. Such projects carry the risk of exit scams. When users use a large amount of funds to purchase project tokens, the project team can directly exchange all the valuable coins for themselves through privileged functions, causing the value of the project tokens to drop to zero.
Taking the CUZK project code as an example:
The CUZK token contract has a backdoor, where the privileged address can directly set an excessive amount of tokens to its own account, as shown in the following code:
ccviLianGuaiaaqqq() function will add a huge amount of CUZK tokens to the caller’s account, and finally check whether the caller is ciyuAdmintmrr, which is the address set by the contract creator during initialization (0xf719).
The project team added a huge amount of tokens to themselves (0xf719) by calling the ccviLianGuaiaaqqq() function.
Subsequently, the privileged address used the set token in LianGuaiir to exchange all WBNB, causing the CUZK coin price to drop to zero.
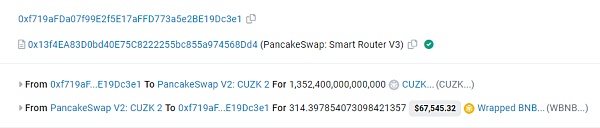
2. Hidden backdoor, indirectly adding balance
There are also some projects that do not directly manipulate the token balance of an address, but the privileged address can indirectly obtain a large number of tokens, thereby exchanging all the value coins and causing the token price to drop to zero.
Take the Flashmall project on the BNB chain as an example:
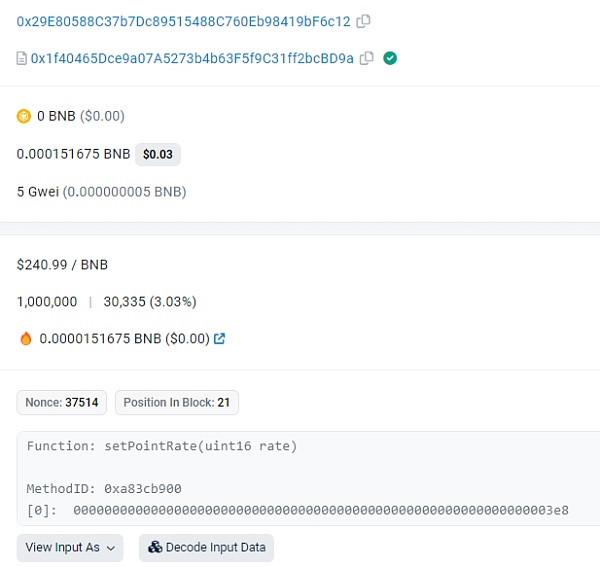
The FlashMall contract has a setPointRate function for setting the exchange rate, which can only be called by the privileged address.
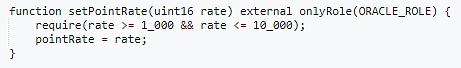
This run-off event mainly consists of the following steps:
Set exchange rate -> Exchange -> Set exchange rate -> Exchange
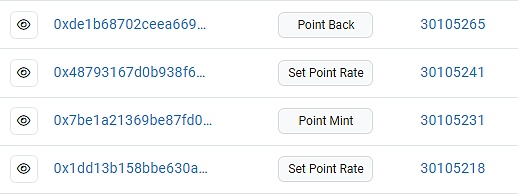
The detailed steps are as follows:
1. The privileged address sets the rate to 10000.
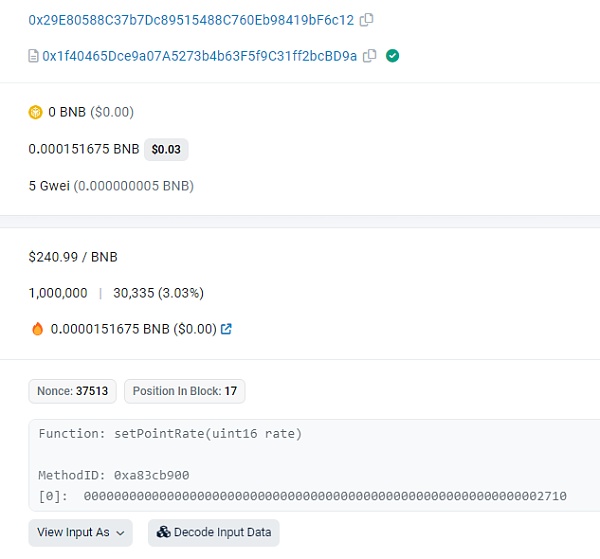
2. The address 0x613C can exchange MUSD for 10 times the amount of MCoin.
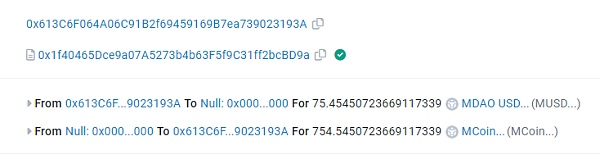
3. The privileged address sets the rate to 1000.
4. The address 0x613C can exchange MCoin for the same amount of MUSD.
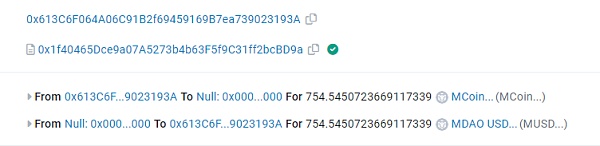
5. Through multiple conversions, 0x613C has acquired a large amount of MUSD, and finally exchanged all USDT.
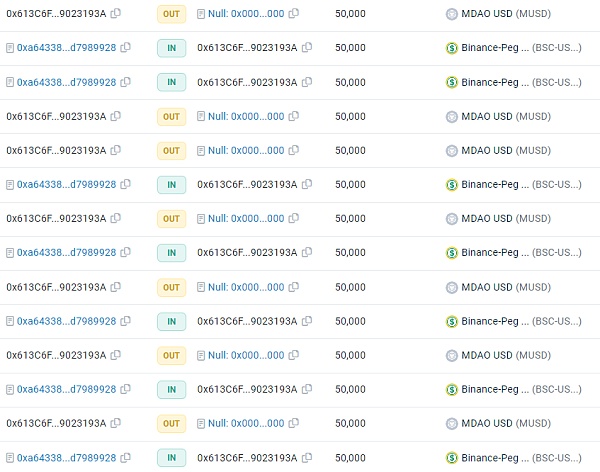
The following is the code for the exchange between MCoin and MUSD, and the quantity is determined by pointRate.
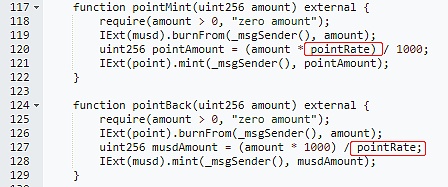
Summary: Whether a contract has a backdoor mainly depends on whether there is a privileged function that can manipulate tokens of any address, or whether there is a privileged address token issuance logic function. In addition, if the project party holds the majority of the liquidity tokens, it may also lead to a run-off. Users can judge the risk level by checking whether the contract has abandoned the privileged address, or whether the privileged address is a normal business contract address. At the same time, it is also necessary to check whether the liquidity tokens are owned by an EOA account or a normal business contract.
II. Pixiu Project Scam
This type of project is characterized by the ability to purchase project tokens, but when users want to sell, the transaction will fail. The main manifestation of this type of scam contract code is that when the token is transferred for the first time, some contract states will be set, and then no more transfers can be made, causing users to buy tokens, set the contract states, and then unable to sell.
Take the counterfeit EDU token project as an example:
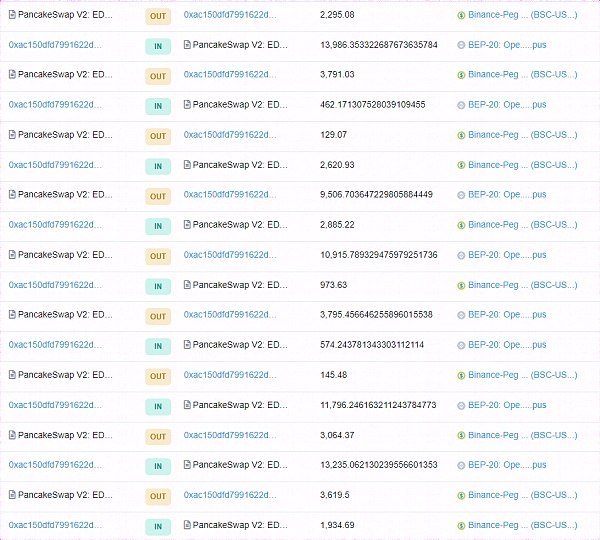
The contract address of the project is 0x4749, which is the same name as the EDU project. The token owner (0xac15) buys and sells tokens in the EDU LianGuaiir 0xE3f2 address, and sends the held tokens to Binance wallets and exchanges, creating an illusion of widespread participation (as shown in the figure below).
The following code, after the first transfer (buying coins), sets tokenGreylist[to] (to being the user’s address) to true. However, since the status of the whitelist address is not public in the code, the transfer function cannot be called again. The switch status and whitelist addresses are controlled by the owner. For users participating in the project, tokens cannot be sold by default.
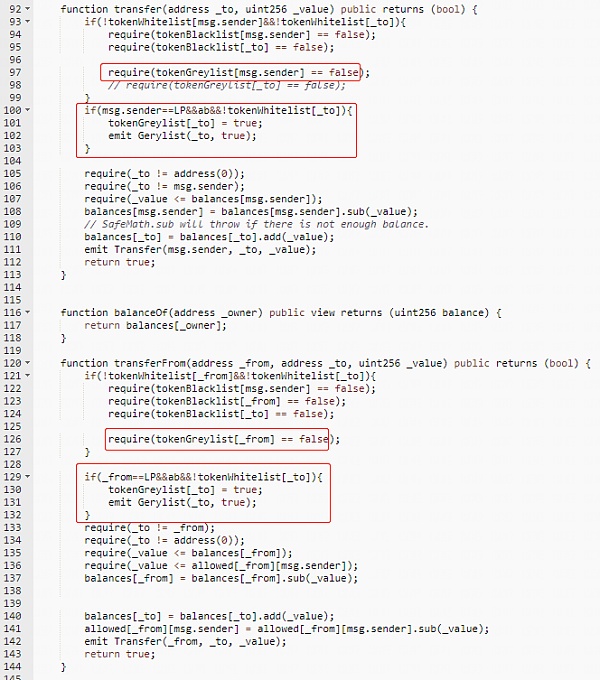
Summary: The feature of the Pixiu Pan project is that it allows buying but not selling. By examining the actual logic of transfer and transferfrom, check for any mutually restrictive conditions. Those with technical conditions can locally simulate the execution of relevant functions.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- LianGuai Morning News | G20 leaders will discuss advancing the proposed roadmap for cryptocurrency regulation in October.
- Artificial Intelligence and Work Automation
- Jay Chou’s ‘Fantasy Music Universe’ is here. Would you buy the 30 yuan digital collectible key?
- Bankless Why does the US Treasury Bond Trigger the Widespread Adoption of RWA?
- GameFi caught in controversy Is it a bubble that will eventually burst or a completely new game mode?
- 10 Tips for Web3 Entrepreneurs
- Notice on the Issuance of the Three-Year Action Plan for the Innovative Development of the Metaverse Industry (2023-2025)






