Bankless Security Guide – 10 Key Steps to Protecting On-Chain Assets
Bankless Security Guide - 10 Steps to Protecting On-Chain AssetsAuthor: WilliamM.Peaster; Translator: Marsbit
Counterfeit phishing scams imitating Bankless are on the rise.
Successful phishing attacks depend on three main factors:
1. A fake opportunity that looks real enough (usually a website claiming to be an airdrop or NFT minting page)
- Account Abstraction (AA) The Future Web3 Wallet Experience
- LianGuaiWeb3.0 Daily | Binance Labs announces strategic investment in AltLayer
- Interpreting Lens V2 Will ERC-6551 Bring the iPhone Moment for Web3?
2. The victim trusting the fake opportunity and signing a malicious transaction;
3. The victim having valuable token approvals in their attacked wallet, which the attacker can exploit through malicious transactions.
With decent publicity and a website, any one of us can be deceived by phishers.
Fortunately, we can integrate a series of practices and resources to eliminate the possibility of signing erroneous transactions or minimize their impact.
Here are 10 important steps to defend against crypto scams in 2023:
1. Create a Vault
Strategy: Create a multi-signature wallet for crypto assets
Recommended tool: Safe wallet
A multi-signature wallet, commonly known as a “vault,” is similar to a secure bank storage for crypto. It provides higher security for crypto transactions by requiring multiple private keys (i.e., wallets) to authorize transactions.
Therefore, multi-signature acts like a digital fortress that ensures the security of your assets even if one of your keys is compromised.
Nowadays, one of the easiest ways to create multi-signature is to create a secure account. You can add any addresses you want as signers, but it’s simple to start with a 2-of-3 multi-signature. Additionally, consider using a hardware wallet (such as a Ledger device) as one of your signers to add an extra layer of security.
2. Enable a Risk Wallet
Strategy: Create a wallet dedicated to daily activities with risk
Recommended tool: Delegate
Never use your vault for daily crypto activities like claiming airdrops or minting NFTs. For these purposes, set up a separate dedicated wallet and only recharge ETH as needed.
You shouldn’t store all your on-chain assets in a frequently used wallet. Consider services like Delegate to delegate the permissions of your vault wallet to a risk wallet without moving or jeopardizing any assets. For example, you can participate in a whitelist minting event for NFTs eligible in your vault.
This way, even if you accidentally sign a bad transaction with your risk wallet, your long-term savings won’t be affected.
3. Use Transaction Preview Tools
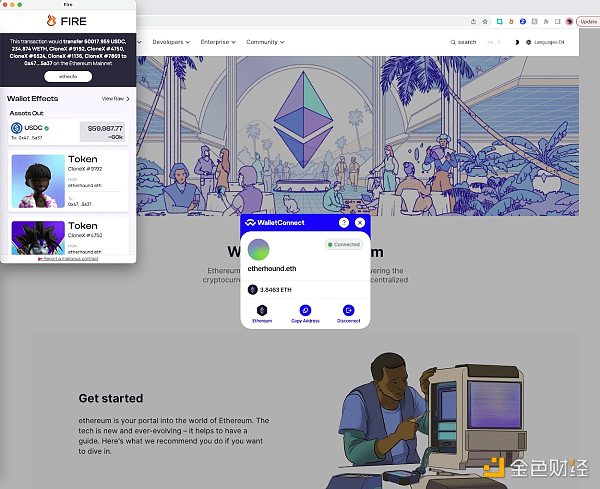
Strategy: Download a transaction preview tool to alert yourself to malicious transaction attempts.
Recommended tools: Fire, Pocket Universe, Stelo
Wait a minute, what if I don’t transfer $60,000 and all the NFTs to this random address? This is where the preview tool helps you visualize the information before approving any content.
These tools are free browser extensions that you can download, and they will provide you with pop-ups explaining all proposed transactions. These extensions are magical barriers against phishing attacks, so make sure to use one of them in all your transactions.
4. Review Token Approvals
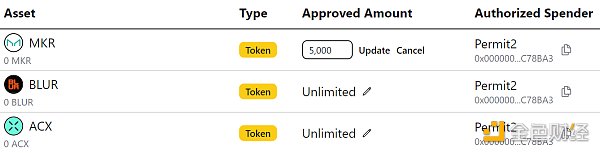
Strategy: Remove unlimited token spending approvals
Recommended tool: Revoke.cash
Many Ethereum-based applications, such as DeFi protocols, will require you to approve “unlimited” token spending to avoid constantly re-approving funds for use in these applications.
What’s the problem? If your wallet is compromised and you have a bunch of ongoing unlimited token approvals, the attacker can drain everything.
Therefore, you need to regularly monitor pending approvals and revoke or minimize unlimited approvals whenever possible. The revoke.cash platform makes editing your approvals easy, so don’t overlook it.
5. Preliminary Research
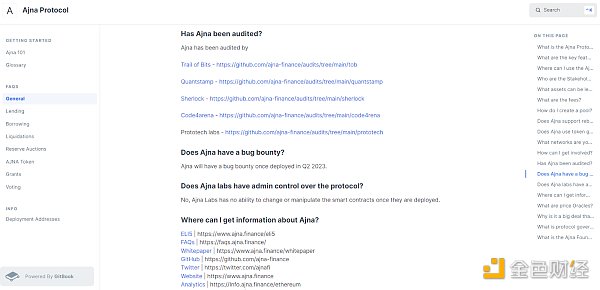
Strategy: Do some research on the project you’re interested in before diving in.
Recommended websites: DeFiLlama (current resources), CryptoWiki (historical information)
Never act blindly in the cryptocurrency space, always do your homework.
For example, recently I’ve been researching the Ajna protocol, which is a new ungoverned DeFi lending protocol. I went straight to its documentation, FAQs, whitepaper, etc., so that I could start understanding it and assessing its nuances and risk factors.
Take the time to understand the basics before diving into anything. Don’t put yourself in unnecessary danger by blindly imitating. If you can’t find good documentation and similar educational resources, that itself is a big red flag.
6. Monitor Your Positions
Strategy: Use portfolio trackers to closely monitor your cryptocurrency positions.
Recommended tools: DeBank, MetaMask Portfolio, Zapper, Zerion
In the cryptocurrency space, it is crucial to closely monitor your assets, and in this regard, portfolio trackers are your best friends. They provide you with an overview of what you hold across various wallets and platforms, allowing you to easily monitor your cryptocurrencies in real-time.
Remember, understanding your position is not just about observing returns; it is also a crucial part of risk management. By regularly monitoring your assets, you can identify abnormal activities that may indicate security vulnerabilities and take action to protect the remaining assets in a timely manner.
(Note: While MetaMask is indeed a sponsor of Bankless, its inclusion in this recommended tool list has nothing to do with its sponsorship, but rather it is a decision made by the author of this article.)
7. Stay informed about the latest news in the ecosystem
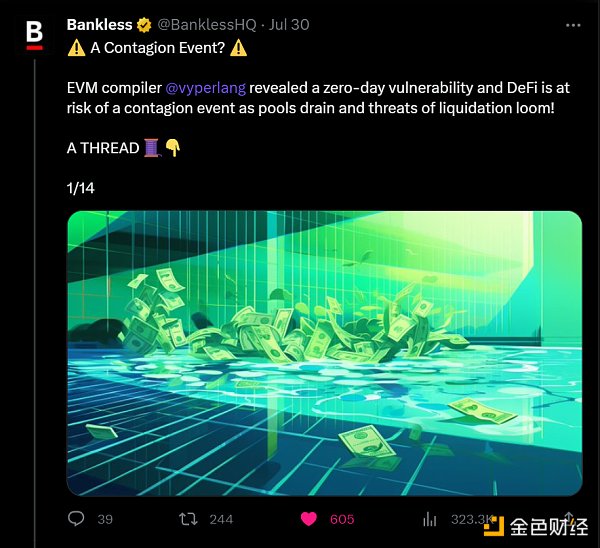
Strategy: Stay updated with crypto news, such as recent hacking attacks.
Recommended resources: Bankless, DeFiLlama Roundup
Sometimes, attacks on DeFi protocols and other projects can indirectly or directly impact your cryptocurrency positions. To stay ahead in terms of potential consequences, staying informed is crucial.
However, there’s no need to do all the work yourself. For example, Bankless decoded the Curve reentrancy attack in a Twitter post within a few hours of the attack’s initiation. We strive to keep you informed in a timely manner, but there are also many great additional resources in the market, such as the news aggregation chat on DeFiLlama on Telegram.
8. Pay attention to Web2 activities

Strategy: Rely on good security measures to protect your Web2 activities.
Recommended resources: Officer’s Blog
Don’t give attackers any chances, even outside the Web3 world.
Criminals can compromise your email or social media accounts in an attempt to deceive others who trust you into clicking on phishing websites. According to security officer @officer_cia, strong operational security basics include:
Using secure email providers such as Protonmail;
Using different strong passwords, avoiding reuse in multiple places;
Never associate your phone number with crypto platforms;
Using 2FA to back up your accounts, but avoiding SMS-based 2FA;
Requesting your mobile carrier to lock your SIM card;
Using up-to-date antivirus software.
9. Create an escape plan
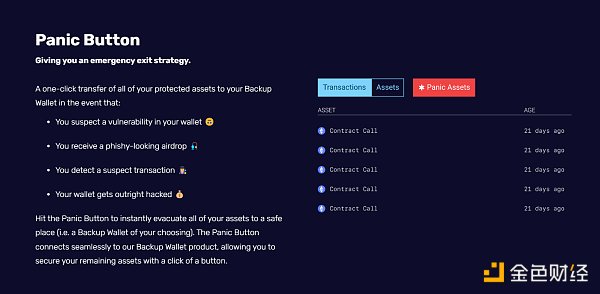
Strategy: Develop an evacuation strategy for your assets in case of worst-case scenarios.
Recommended tools: Webacy, Spotter
Even with all the tools and strategies mentioned above, it is still important to prepare for the worst-case scenario.
Webacy is a Web3 security provider that allows you to create a custom backup wallet and emergency button system for your assets. If you are under attack or even just startled, you can use the platform’s “LianGuainic” feature to transfer all or any remaining assets to a pre-designated backup wallet.
For more advanced users, there are other monitoring and protection services, such as Spotter, designed to help you detect and escape on-chain attacks in milliseconds rather than minutes.
10. Sound the alarm
Strategy: If you come across a phishing scam, sound the alarm quickly.
Recommended resource: CryptoScamDB
If you see something, say something.
If you do encounter a cryptocurrency phishing scam, sound the alarm so others can avoid the risk.
This could be a quick PSA message in your favorite chat group, or a social media post, or a report submitted to scam databases like CryptoScamDB. You can help others protect their cryptocurrency in just 30 seconds.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Q2 2023 Web3 Developer Report Surge in Developer Activity, Rapid Adoption of Account Abstraction…
- Exploring the Hidden Corner of USDT Drug Trafficking, Online Gambling, Money Laundering
- Do the sender and receiver need to be online at the same time? Low capital efficiency? Dispelling six misunderstandings about the Lightning Network.
- TG BOT Rising Upstarts in Blockchain Marketing and Grassroots Counterattack, Security Issues Await Resolution
- 10 Steps to Enhance Encryption Security
- Looking back at Yuga Labs over the past year, is APE still a good bear market bargain?
- Overview of the development status of NFT lending protocols What are the innovations and unresolved issues?





