Black-producing gang exploits Apache Struts 2 vulnerability and SQL blast control server mining
Source: Tencent Mimi Threat Intelligence Center
I. Overview
The Tencent Security Miami Threat Intelligence Center detected that the group used the Apache Struts 2 remote command execution vulnerability (CVE-2017-5638) to attack the windows server. From the list of files used by the group, the attack was mainly carried out through blasting or exploit, and targeted at windows About 270 servers have been controlled by the server. There are 44 servers that have been issued mining trojans. The group has earned 35,000 yuan from mining Monero coins.
Detailed analysis
- Global blockchain private equity financing of 21.612 billion yuan in 2019
- Everything you want to know about NFT (non-homogeneous tokens) is here
- Jinan City officially launches "Blockchain + invalid resident ID card verification and valid resident ID card information application service" system
Looking at the gang HFS server file list, you can see multiple scanning and blasting tools, exploit tools, password grabbing tools, remote control tools, and port forwarding tools.
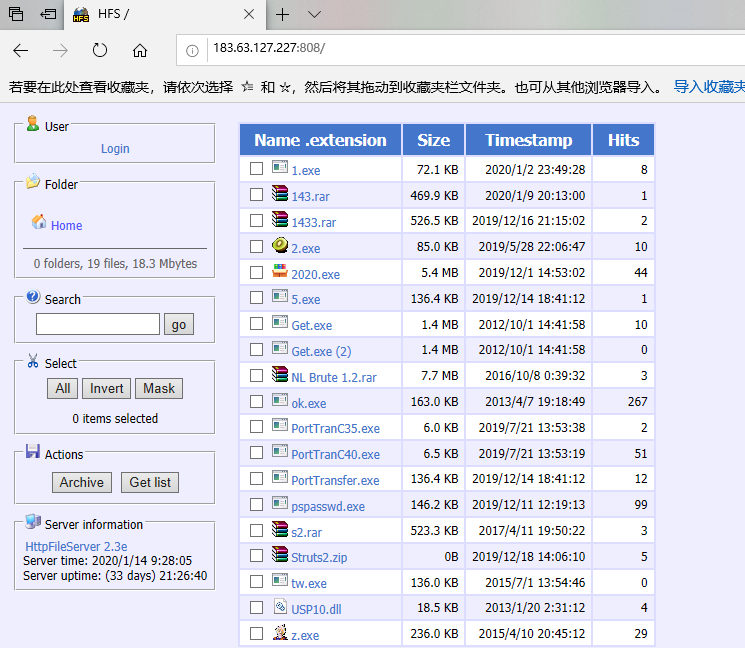
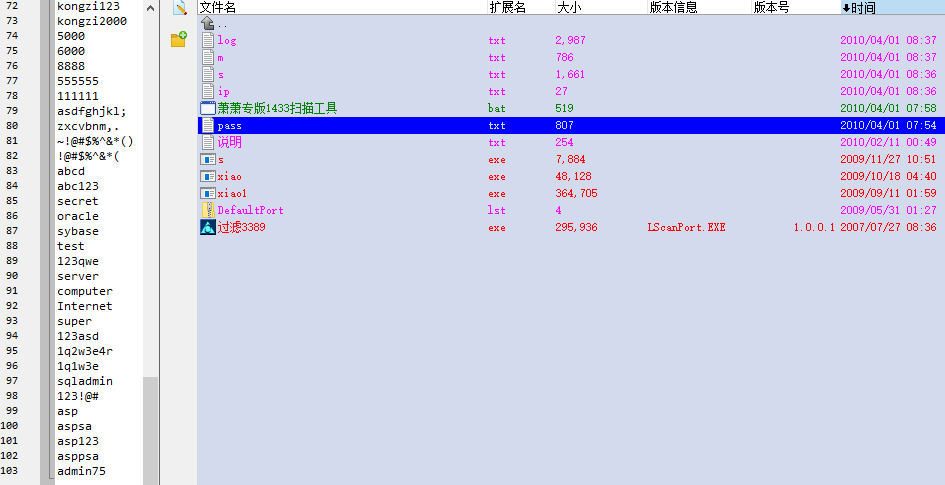
The hacker used the 1433 scanning tool to blast the sqlserver server with the password table:
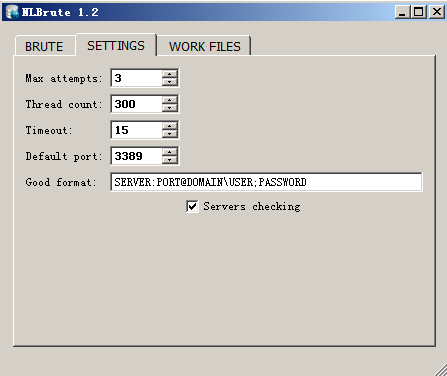
3389 Blasting tool NLBrute 1.2
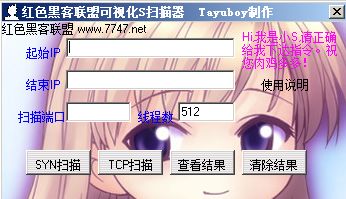
S scanner
Exploitation of Apache Struts2 Remote Command Execution Vulnerability (CVE-2017-5638)
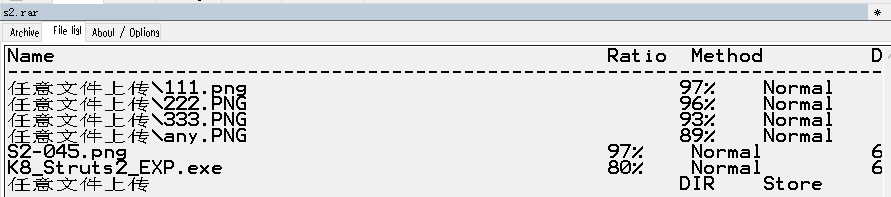
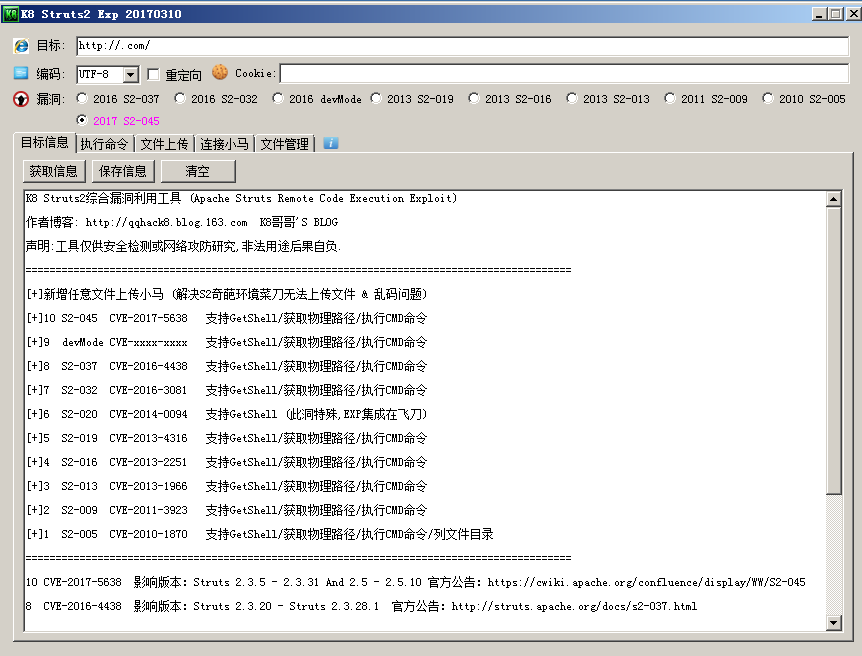
After successfully invading the server, the mining module 2020.exe is issued.
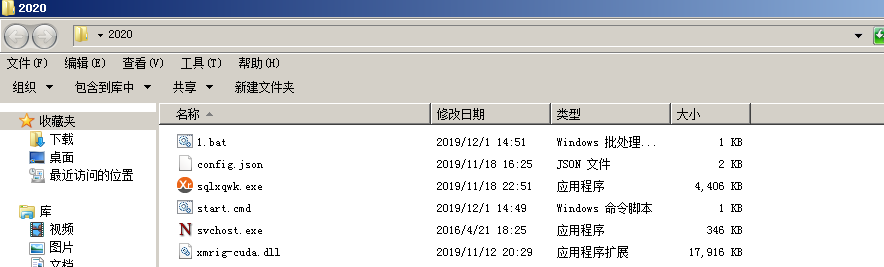
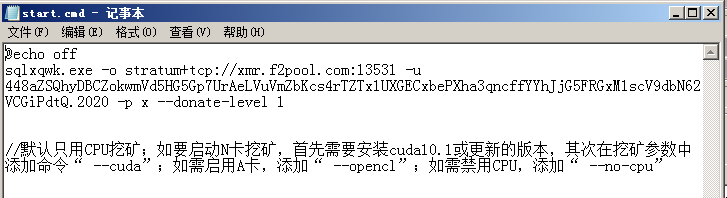
Mining Pool: xmr.f2pool.com:13531
wallet:
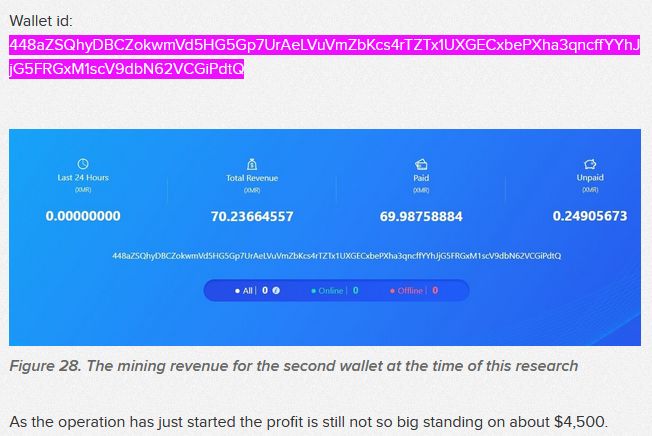
8aZSQhyDBCZokwmVd5HG5Gp7UrAeLVuVmZbKcs4rTZTx1UXGECxbePXha3qncffYYhJjG5FRGxM1scV9dbN62VCGiPdtQ
At present, 90 XMRs have been dug, with a market value of about 35886 RMB

Port forwarding tool ok.exe infected by ramnit worm
The port forwarding tool on the hacker server has been infected by ramnit, and the entry point has been modified in the last .text section
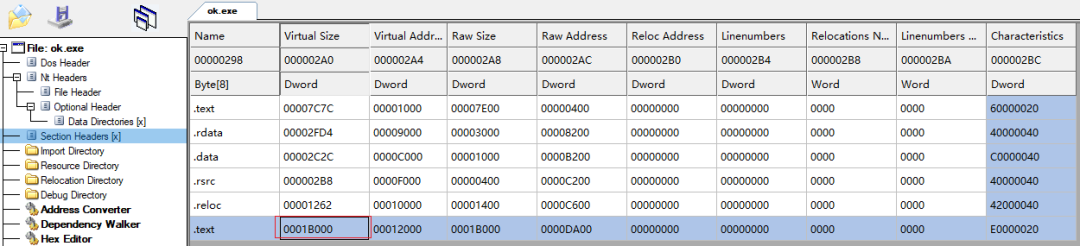
Ramnit C2: 82.112.184.197:447, 45.55.36.236:447, 8.7.198.46:80
After removing the ramnit infection code, it is actually a port forwarding tool
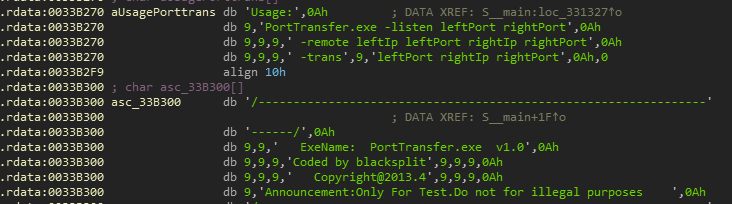
Therefore, the hacked windows server will also be infected with the Ramnit worm. The Ramnit worm is a computer worm that affects Windows systems. Ramnit infected removable media, such as USB drives, are also hidden in the master boot record. Mainly infect files with .exe, .dll, .htm, and .html extensions. During the peak of 2015, Ramnit had infected more than 3 million computers.
Third, homology analysis
According to the wallet address, it can be associated with the bulk wallets of the "CryptoSink" operation announced by the F5 research team in March last year. At that time, 70 Monero coins were mined. It can be seen that the mining attack activity is still the same as "CryptoSink" Big relationship.
Fourth, security recommendations
In view of the characteristics of this black gang, we recommend that corporate users refer to the following methods to relieve risks:
1. It is recommended to modify the default port of the remote desktop or restrict the IP addresses allowed to access;
2. Upgrade Apache Struts 2 to the latest version to fix security holes. Affected versions Struts 2.3.5-Struts 2.3.31, Struts 2.5-Struts 2.5.10;
3. Modify the sqlserver password. Do not use weak passwords. Weak passwords can be easily invaded by blasting. The compromise of the SQL server may also lead to a serious risk of information leakage.
IOCs
Mining pool: xmr.f2pool.com:13531 Wallet: 48aZSQhyDBCZokwmVd5HG5Gp7UrAeLVuVmZbKcs4rTZTx1UXGECxbePXha3qncffYYhJjG5FRGxM1scV9dbN62VCGiPdtQ
URL hxxp: //183.63.127.227: 808 /
MD5 fabd73f8bf2bc803703778457c068936 81c965ac62471ab62e85ca441d0031e6
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Babbitt Column | Trustworthy Lightning Network: Or Solve the Problem of Expensive and Slow Bitcoin Transfers
- Russian officials: cryptocurrency bill expected to pass this spring, will define digital assets
- Japan's Financial Services Agency: Proposes to reduce leverage on crypto margin trading to less than double, or implement this spring
- How does the secret whale "liquidator" help DeFi run smoothly?
- Bitcoin hashrate continues to climb, rising 167% over the past year
- Babbitt Site | Li Lihui: We should be more wary of global digital currencies, and super-sovereignty and super-banking will lead to financial disruption
- Facing quantum computing threatens digital currency to grow in confrontation





