Blockchain games out of bugs, hard forks to protect user rights?
Bug
- Player A challenges player B
- Player B accepts and submits a move
- Player A responds and submits a move
- Player A reveals the trick
- Player B reveals the trick
- Smart contract ruling battle results
- Duel animations are generated on cheezewizards.com and players can see the results
- Player A challenges player B
- Player B accepts and submits a move
- Player A responds and submits a move
- Player A reveals the trick
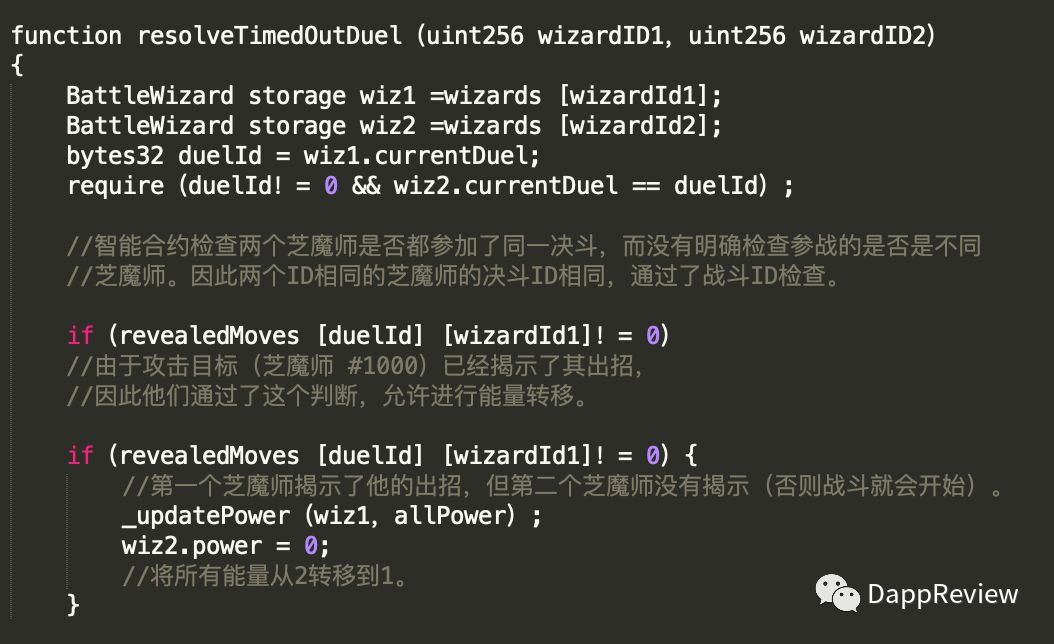
- Player B deliberately times out without revealing a move (90 minutes)
- Player B maliciously calls the resolveTimedOutDuel(rTOD) function, which turns both entrants into player A, causing player A to be both a winner and a loser.
Where is the bug "fun"?
View bugs at the code level
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Chainalysis Asia Pacific cryptocurrency trend development report (October 2019)
- Privacy Backtracking and Investment: Oligarchs are significant and future value can be expected
- Libra responds to G7 full text: Improving opportunities for cross-border payments
- The cryptocurrency developer 108 will (1): the craftsmen who hide behind the code
- The four operations of the correct investment in the encryption market: how to minimize losses to make a profit?
- New Balance's latest sneakers are coming soon, plus the blockchain hidden gameplay do you know?
- Deputy Governor of the Bank of France: Encrypted assets have the potential to replace the traditional banking system, stabilizing the currency or will have a systemic impact





