Interoperability and Bridging in Blockchain Current Status
Blockchain Interoperability and Bridging Current StatusAuthor: Jacob Ko; Translation: Huohuo/Baihua Blockchain
With the increasing number of Layer 1, Layer 2, and application chains, it is more important than ever for blockchains to have secure, low-cost, and efficient ways of communicating with each other.
In this article, we will discuss why interoperability is important, the challenges it faces, and the current methods being used.
1. The Proliferation of Blockchains
The first public blockchain, Bitcoin, was launched in 2009. According to DeFiLlama data, in the 14 years since then, there has been an explosion of public blockchains, with the current number reaching 201. While Ethereum dominates on-chain activity, accounting for approximately 96% of the total value locked (TVL) in 2021, this number has decreased to 59% in the past 2 years with the introduction of alternative Layer 1 blockchains like Binance Smart Chain (BSC) and Solana, as well as the emergence of Layer 2 blockchains like Optimism, Arbitrum, zkSync Era, Starknet, and Polygon zkEVM.
- Vice President of the Hong Kong University of Science and Technology, Wang Yang Seizing the opportunity to issue government-backed Hong Kong dollar stablecoin
- Understanding Two RWA Asset Issuance Models in One Article
- Exclusive Interview with Solv Co-founder Meng Yan DeFi and Public Chains Still Have Huge Development Potential, Perfecting Infrastructure is the Key to Mainstream Adoption
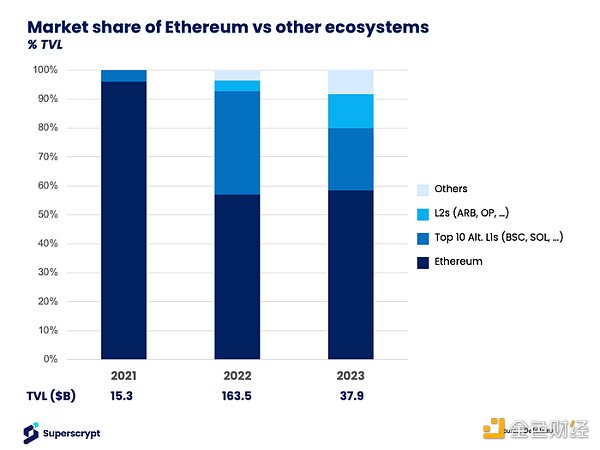
According to DeFiLlama, as of the time of writing this article, there are over 115 EVM-based chains and 12 Ethereum rollups/L2s, and the trend of activity across multiple chains is expected to continue for various reasons:
1) Major L2s like Polygon, Optimism, and Arbitrum positioned themselves early on as Ethereum’s scaling solutions, raising significant funds and positioning themselves as simple places for cheap application deployment (last year, we saw a 2,779% growth in applications built by development teams on Arbitrum, +1,499% on Optimism, and +116% on Polygon — albeit with smaller bases of around 200-400 developers).
2) Constant launches of alternative L1s optimized for specific needs. Some chains have optimized for higher throughput, speed, and settlement times (e.g., Solana, BSC), while others have optimized for specific use cases such as gaming (ImmutableX), DeFi (Sei), and traditional finance (e.g., the gated Avalanche subnets).
3) Applications with sufficient scale and users are launching their own aggregators or application chains to capture more value and manage network fees (e.g., dydx); and
4) Some frameworks, SDKs, toolkits, and “Rollup-as-a-Service” providers have entered the market, enabling any project to easily launch their own Rollup with minimal technical uplift (e.g., Caldera, Eclipse, Dymension, Sovereign, Stackr, AltLayer, Rollkit).
We live in a world of multiple chains and layers.
2. Increasing Importance of Interoperability
The proliferation of L1s, L2s, and application chains highlights the importance of interoperability, which refers to the ability and means for blockchains to communicate with each other; to transfer assets, liquidity, messages, and data between them.
As suggested by Connext, blockchain interoperability can be divided into three parts:
1) Transfer: The transfer of message data from one chain to another
2) Validation: Proving the correctness of the data (usually involving proof of consensus/state of the source chain); and
3) Execution: The target chain performs certain operations on the data
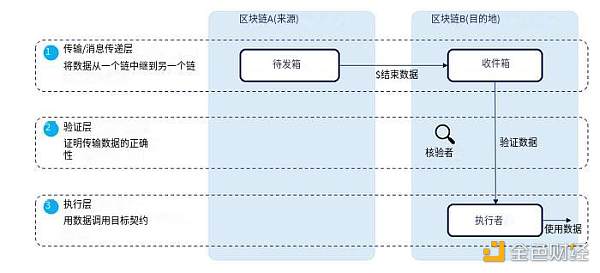
Source: Message bridging stack adapted from Connext
The benefits of being able to transfer assets and liquidity between chains are simple – it allows users to explore and transact in new blockchains and ecosystems. They will be able to leverage the advantages of new blockchains (e.g., conducting transactions or trades on a lower-cost Layer 2) and discover new lucrative opportunities (e.g., accessing higher-yielding DeFi protocols on other chains).
The benefit of transferring messages is unlocking a whole set of cross-chain use cases without moving their original assets. Messages sent from Chain A (source) trigger code execution on Chain B (target). For example, a dapp on Chain A can pass messages about user assets or transaction history to Chain B, allowing them to participate in activities on Chain B without moving any assets, such as:
1) Borrowing on Chain B using assets on Chain A as collateral
2) Participating in community benefits in a cost-effective manner (e.g., minting a new NFT series, claiming event tickets and merchandise) without transferring their NFTs to Chain A
3) Utilizing their decentralized ID and on-chain history established on one chain to participate in DeFi and obtain better rates on another chain
3. Challenges of Interoperability
While interoperability brings many benefits, it faces several technical challenges:
1) First, blockchains often have difficulty communicating with each other: They use different consensus mechanisms, cryptographic schemes, and architectures. If your token is on Chain A, buying tokens on Chain B with them is not a straightforward process.
2) Second, at the validation layer, the reliability of interoperability protocols is only as good as the validation mechanisms chosen to verify that the passed messages are indeed legitimate and valid.
3) Third, providing multiple building locations for developers can result in applications losing composability, which is a key building block in web3. This means developers cannot easily combine components from another chain to design new applications and unleash greater possibilities for users.
4) Finally, a large number of chains lead to decentralized liquidity, reducing capital efficiency for participants. For example, if you provide liquidity to a pool on Chain A to earn yields, it becomes challenging to extract LP tokens from that transaction and use them as collateral in another protocol to generate more returns. Liquidity is the lifeblood of DeFi and protocol activity – the more chains there are, the harder it becomes for them to thrive.
Currently, there are some interoperability solutions to address some of these issues, but what is the current situation?
4. Current State of Interoperability
Currently, cross-chain bridges are the main facilitators of cross-chain transactions. There are currently over 110 bridges, each with varying levels of functionality and trade-offs in terms of security, speed, and supported number of blockchains.
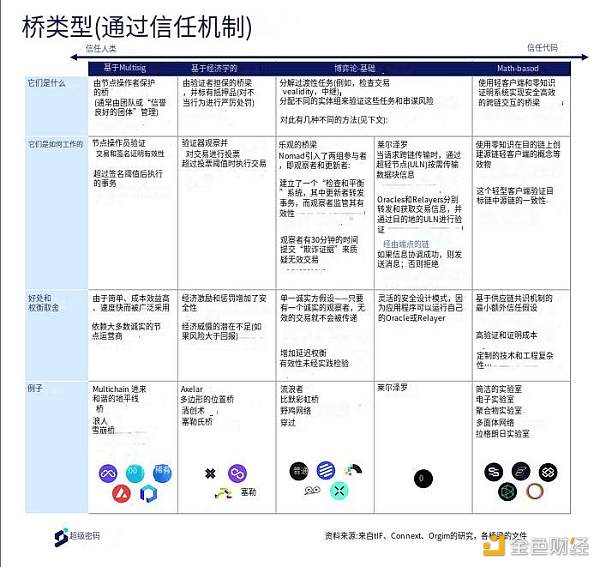
As LI.FI describes in their comprehensive Bridging 101 article, there are several different types of bridges:
1) Wrapped and Minted Bridges – Protect tokens on Chain A with multisignature and mint corresponding tokens on Chain B. In theory, the wrapped tokens should hold the same value as the original tokens, but their value is only valid if the bridge is secure. In the case of a bridge being hacked, users would not be able to exchange the wrapped tokens back when attempting to bridge from Chain B to Chain A (e.g., portals, multichain).
2) Liquidity Networks – Parties provide token liquidity on either side of the chain to facilitate cross-chain swaps (e.g., Hop, Connext Amarok, Across).
3) Arbitrary Message Passing Bridges – Can transmit any data (tokens, contract calls, chain states), such as LayerZero, Axelar, Wormhole.
4) Use Case-Specific Bridges – (e.g., stablecoin and NFT bridges) involve burning on Chain A before releasing stablecoins/NFTs on Chain B.
These bridges employ different trust mechanisms supported by various trusted parties and incentives to ensure security:
1) Team Human relies on a set of entities to prove the validity of transactions;
2) Team Economics relies on validators with staked collateral to deter malicious behavior, with validators facing significant penalties. This is only effective when the economic benefit of misconduct is lower than the penalty reduction;
3) Team Game Theory assigns various tasks (e.g., checking transaction validity, relaying) to different parties in the cross-chain process;
4) Team Math performs on-chain light client verification, utilizing zero-knowledge technology and succinct proofs to verify the state of one chain and then release assets on another chain. This minimizes human interaction and is technically complex to set up.
Ultimately, the range of trust mechanisms spans from humans to economically incentivized humans to math-based verification. These approaches are not mutually exclusive – in some cases, we see certain methods combined to enhance security. For example, LayerZero’s game-theory-based bridge incorporates Polyhedra (which relies on zk proofs for validation) as an oracle for its network.
How have bridges performed so far?
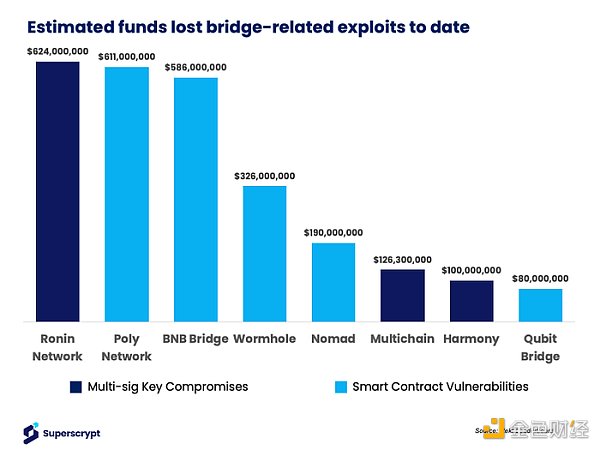
Thus far, bridges have facilitated a significant transfer of capital – as of January 2022, the total value locked (TVL) in bridges reached a peak of $60 billion. With such a large amount of capital at stake, bridges have become prime targets for exploits and hacks. In 2022 alone, multisignature key leaks and smart contract vulnerabilities resulted in losses of $2.5 billion. A 4% annual capital loss rate is unsustainable for the flourishing of the financial system and attracting more users.
The attack has been ongoing in 2023, with multi-chain addresses being stolen $126 million (representing 50% of the Fantom bridge and 80% of the Moonriver bridge assets), while their CEO has been in control of all their “multi-signature” keys. After this hack, the TVL (Total Value Locked) on Fantom, which bridged a large amount of assets, dropped by 67% in the following weeks.
Ultimately, some of the biggest bridge vulnerabilities and subsequent consequences can be attributed to multi-signature vulnerabilities (Ronin $624 million, Multichain $126.3 million, Harmony $100 million), highlighting the importance of the trust mechanism adopted by bridges.

Having a small number of validators (such as Harmony), grouped validators (such as Ronin), or a single validator (such as Multichain) is a key factor leading to some of these vulnerabilities, but attacks can come from multiple avenues. In April 2022, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the U.S. Department of the Treasury jointly issued a cybersecurity advisory notice highlighting some tactics used by the Lazarus Group, which is sponsored by the North Korean government.
5. Where do we go from here?
Clearly, reliance on human verification mechanisms can easily become a target, but secure and efficient interoperability is still needed. So where do we go from here?
We are now seeing the emergence of trust-minimized validation methods – and that’s where we get excited.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Hive Digital CEO Blockchain and AI can mutually benefit each other
- Why is Ethereum’s position as the king of public blockchains difficult to shake?
- a16z AI combined with blockchain creates four new business models
- Interview with Sui’s Vice Chief Information Security Officer at Mysten Labs Considerations, Design, and Practice of Sui Blockchain Security
- Sei’s ultimate marketing rule Make headlines through news, and use sunshine airdrops to sweep the cryptocurrency community.
- 10 Ways NFTs are Boosting the African Tourism Industry
- Insights and Reflections Why is it difficult to hear the voices of female entrepreneurs in Web3?






