The Battle of Cross-Chain Thrones Strategies, Dominators, and Challenges.
Cross-Chain Thrones Strategies, Dominators, and Challenges.Author: PSE Trading Analyst @Daniel Hua, PSE Trading
Introduction
In the world of blockchain, each network can be seen as an independent ecosystem with its own native assets, communication rules, etc. However, this characteristic also makes it impossible for different blockchains to communicate with each other, preventing the free flow of assets and information. Therefore, the concept of cross-chain interoperability has emerged.
1. The Significance and Use Cases of Cross-Chain Interoperability
Defi is the core and foundation of the current blockchain but faces many challenges, such as fragmented liquidity, insufficient asset pool depth, and low capital utilization. The emergence of cross-chain interoperability protocols can integrate assets from different chains into a unified smart contract, maximizing user experience and capital utilization. In ideal circumstances, cross-chain interoperability protocols can reduce friction to zero.
For example:
- Zhao Changpeng’s strategic layout opBNB and its dark horse MEKE.
- Emerging Consumer Behavior in Web3 Worth Paying Attention to
- What information does the lawsuit reveal about the two co-founders of Gala Games?
(1) Putting assets from the OP chain into GMX on the ARB chain to increase the depth of the funding pool
(2) Putting assets from the OP chain into Compound on ARB for collateralized lending
(3) Achieving cross-chain transfer of NFT assets
In addition to finance, the transmission of information is also crucial. For example, cross-chain voting to support important proposals, data transmission between social dapps, etc. If Defi has opened the door to the world of cryptocurrencies, then cross-chain interoperability protocols are the necessary path to success!
2. There are Four Types of Cross-Chain Interoperability Protocols
2.1 Validation Based on Nodes or Third-Party Networks (First Type)
The most primitive cross-chain protocol uses MPC (Multi-LianGuairty-Computation) for transaction validation. Thorchain is a typical representative that verifies transactions by deploying nodes on the chain to establish security standards. Typically, this protocol attracts 100-250 node validators on the network. However, the disadvantage of this approach is that each node needs to validate the transaction, resulting in longer waiting times for users. In addition, the operational costs of nodes cannot be ignored and will ultimately be passed on to users. Furthermore, Thorchain sets up a Liquidity Pool for each trading pair using the native token RUNE of the project. Every cross-asset transaction requires converting the assets into RUNE and then into the target chain’s assets. This model requires a significant amount of funding and has friction, which is not the optimal solution for a cross-chain protocol in the long run. Tips: Thorchain was attacked due to code vulnerabilities (fake ETH symbols being treated as real ETH symbols), unrelated to the security of the validation method.
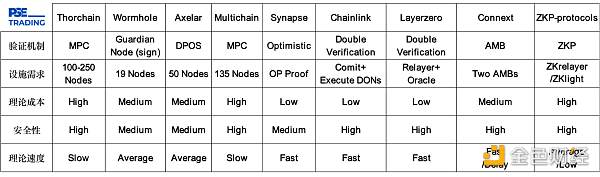
2.1.2 Improvements
Based on this phenomenon, Wormhole selects 19 validators, including well-known node validators like Jump crypto, to verify the authenticity of transactions. These validators also operate verification services on other networks such as ETH and OP. However, this approach carries the risk of excessive centralization. The author believes that complete decentralization is not necessarily always the best choice because some degree of centralization can reduce costs. Ultimately, projects need to achieve large-scale adoption and maximize economic benefits. Tips: Wormhole was attacked due to contract vulnerabilities, where attackers used external contracts to validate transactions and steal assets, unrelated to the security of the validation itself.
Compared to other cross-chain protocols, Axelar is a POS-based public chain. Axelar packages verification information from other networks and sends it to its main network for verification before sending it to the target chain. It is worth noting that the cost of verification is inversely proportional to security. As the number of verification information increases, more nodes are required to participate in verification and maintain network security. In theory, there is no upper limit on the number of nodes. The increase in the number of nodes will cause the cost of transfers to skyrocket, which Axelar will face in the future.
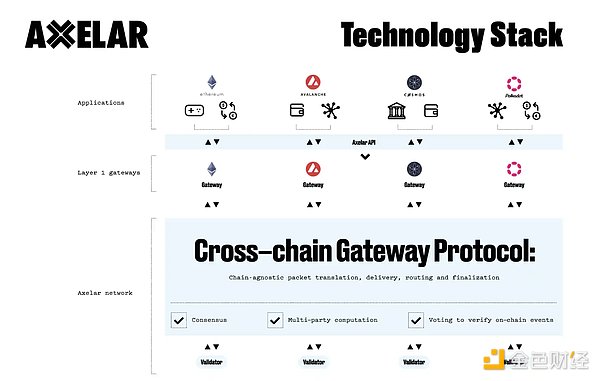
2.2 Optimistic Verification (Second Type)
The success of OP represents the security, low cost, and speed advantages of optimistic verification. Therefore, cross-chain protocols such as Synapse also adopt this verification mode. However, Synapse uses the Lock/Mint method to exchange assets, which carries the risk of being attacked by hackers, as will be explained in section 2.3.1. In addition, optimistic verification can only meet current needs, and more secure and reliable verification methods will be needed in the future, while still maintaining speed and cost advantages. The author will now introduce dual verification to replace optimistic verification.
2.3 Dual Verification (Third Type)
The most widely discussed dual verification protocols in the market are Layerzero and Chainlink. In conclusion, the author believes that dual verification has the most promising development prospects in the current cross-chain protocol field, and it outperforms other protocols in terms of security, speed, and response time.
(1) Layerzero
One of Layerzero’s innovations is to deploy ultra-light nodes on each chain, which transmit data to off-chain Relayers and Oracles (provided by Chainlink) for verification, avoiding heavy computational tasks compared to the first type of protocol. Oracles generate block headers and other information, and Relayers verify the authenticity of transactions. Transactions are only released when both are error-free. It should be emphasized that both operate independently, and assets will only be stolen if hackers simultaneously control the Relayer and Oracle. Compared to optimistic verification, it has higher security because it verifies each transaction.

Cost and security advantages: The author conducted experiments using Stargate (using Layerzero technology)
1) From OP to ARB, the transaction is completed in 1 minute – $1.46
2) From OP to BSC, the transaction is completed in 1 minute – $0.77
3) From OP to ETH, the transaction is completed in 1 minute and 30 seconds – $11.42
In summary, the dual verification mode is in an absolute leading position.
(2) Chainlink
Committing DON collects transaction information, and the target chain ARM collects information from the source chain ARM to reconstruct the Merkle tree and compare it with the Merkle tree of Committing DON. After a certain number of nodes ‘validate’ successfully, the transaction will be submitted to Executing DON for execution, and vice versa. Note: ARM is an independent system. Chainlink’s technology and Layerzero’s principles have a similarity rate of 90%, both adopting the “collect information + verify information (verify each transaction)” mode.
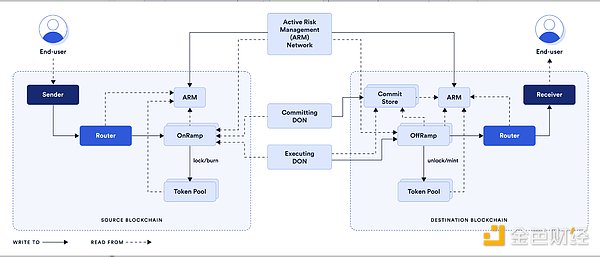
Currently, the projects supported by Chainlink are Synthetix (cross-chain transfer of sUSD) and Aave (cross-chain governance voting). From a security standpoint, although ARM and Executing DON belong to two different systems, they are both controlled by Chainlink itself, which may pose a potential risk. In addition, in the case of the same technology, Chainlink is more likely to attract some older projects with deep cooperation to use its services and achieve bundling. Layerzero, on the other hand, is more likely to attract new projects to deploy, but in terms of supported networks and ecosystems, Layerzero has the upper hand. Furthermore, project teams generally prefer to deploy their products on popular ecosystems.

2.3.1 Layerzero Impossible Triangle
Security: There are four ways to transfer assets across chains.
1) Lock/Mint: The cross-chain protocol deploys a fund pool in each network. When a user wants to transfer ETH from Chain A to Chain B, they need to lock the ETH on Chain A and then mint the same amount of wETH on Chain B. When returning from Chain B to Chain A, the wETH will be destroyed and the locked ETH on Chain A will be unlocked. The risk of this method is that the security relies entirely on the cross-chain bridge. If the amount locked is large enough, hackers will choose to attack the fund pool.
2) Burn/Mint: Tokens are minted in the form of Omnichain Fungible Tokens (OFT), allowing a certain amount of tokens on the source chain to be burned and the corresponding amount of tokens to be minted on Chain B. This method can avoid the risk of attacks due to excessive funds in the fund pool, theoretically making it safer. OFT mode is usually chosen at token issuance and facilitates circulation between dapps. Older projects can also convert their tokens to OFT, but it may be difficult to implement due to multiple party interests. For example, how to handle the native tokens in other dapps after the change. Therefore, only new projects can adopt this model. In summary, older projects do not need to take risks and can continue to develop according to the existing path, so they choose security and cannot be applied to older projects.
3) Atomic Swap: The protocol establishes fund pools on both chains to store a certain amount of tokens. When a user cross-chains, they will deposit the assets into the fund pool on Chain A, and Chain B will extract the corresponding amount from the fund pool on Chain B and send it to the user. Essentially, it is an addition and subtraction process, with high security.
4) Intermediate Token: For example, Thorchain in 2.1 will cause wear and tear and have a long waiting time.
The most widely used method currently is Atomic Swap, but in the future, it will definitely move towards the Burn/Mint model to achieve zero-loss cross-chain and maintain security. Another reason why older projects are concerned about using Layerzero is the manipulation of oracle prices. There have been numerous cases of oracle attacks, and the technology is not yet fully mature. Therefore, most protocols will adopt a cautious attitude.
Review: The verification parameters in Layerzero’s Relayer and Endpoint are set by the project party themselves, which poses a risk of malicious manipulation by the project party. Therefore, the review process is particularly strict, resulting in not many projects being approved by Layerzero. If we give up the review process and allow old projects to use Layerzero, the security cannot be guaranteed. By choosing security, it becomes particularly difficult for new projects to pass the review. This has put Layerzero in a dilemma, and it will take some time for Layerzero to develop.
2.4 Modular Cross-Chain Protocol (AMB Verification, the fourth kind)
Connext is a modular cross-chain interoperability protocol with a hub-and-spoke modular structure. The verification of Chain A and Chain B is delegated to the respective chains’ AMB (Arbitrary-Message-Bridge) – the Spoke for Chain A&B. The generated Merkle tree proof is stored on the Ethereum mainnet, with Ethereum serving as the hub.
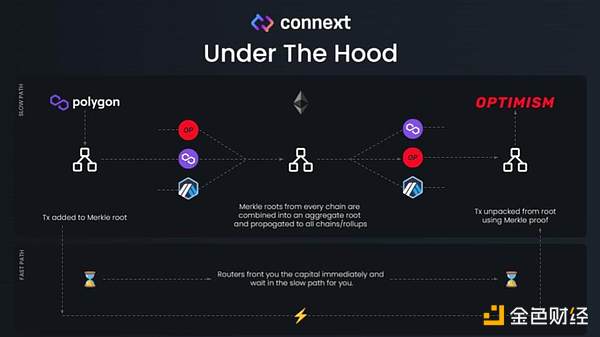
This protocol has the highest security level because we trust the security of the Ethereum network. It uses the principle of shared security. If we use Layerzero’s technology, what we actually need to trust is the project party itself, which theoretically is more secure than the so-called double verification. In the long run, some OP cross-chain protocols may have security issues, and the future trend will move towards ZKP or double verification. On the other hand, for the security verification of cross-native tokens, each chain uses its own AMB module for verification, and the transmission time for these verifications may be inconsistent. Official AMBs usually require longer verification time, and sometimes users may need to wait for up to 4 hours or even longer to complete the verification. This may limit the scalability of the Connext protocol in terms of overall economic benefits and widespread use.
3. ZKP Cross-Chain Interoperability Protocol
The competition in the existing cross-chain protocol field is already quite fierce, and many project parties have set their sights on ZKP, hoping to catch up with the concept of ZK roll-up by using technologies such as ZKrelayer and ZKlight-endpoint, emphasizing the highest level of security. However, the author believes that the application of ZKP in the cross-chain field is still premature in the next 5-10 years and is difficult to compete with existing cross-chain protocols for the following reasons:
(1) High time and cost for proof generation. Zero-knowledge proofs can be divided into ZK STARK and ZK SNARK. The former generates large proofs but takes less time, while the latter generates small proofs but takes more time (the larger the proof, the higher the cost). Most ZKP cross-chain solutions choose ZK SNARK because if the cost of cross-chain is too high, no users will choose that solution. So how to solve the pain point of long processing time? Some protocols choose to add a “fast channel,” similar to the OP mode, which first goes through this transaction and then undergoes verification. This is not strictly a ZKP and belongs to an OP Plus version.
(2) High infrastructure requirements. ZKP has high requirements for infrastructure, requiring a large amount of data calculation and performance support. Once ZKP is widely used, it will cause insufficient computing power, and the protocol will need to spend a lot of money to purchase infrastructure, which is currently not cost-effective.
(3) Uncertainty of Technological Iteration. Among the existing cross-chain protocols, the security of the double verification method is already high enough to meet the current security requirements. Although ZKP may not be needed now, future technological iterations may change this situation. Just like whether third-tier cities needed elevated highways twenty years ago, the need may not be apparent in the short term, but in the long term, ZKP may become the cornerstone of cross-chain development. Therefore, although it is not yet the time for ZKP, there is a need for teams to continue researching and exploring, and to stay attentive because the speed of technological development is unpredictable.
4. Summary and Reflection
The cross-chain interoperability protocol is crucial for the development of blockchain. Among various cross-chain protocols, the double verification mode has performed well in terms of security, cost, and speed, especially Layerzero and Chainlink, the two industry leaders. Although the technical implementations of the two are basically the same, Layerzero has a richer ecosystem, giving it a competitive advantage at the moment. However, due to its security and auditing mechanisms, Layerzero’s ecosystem development has been slower, but it is believed that there will be more development opportunities in the future. As for ZKP cross-chain, although its application is still relatively distant, it is expected to develop in this direction, and we should continue to stay attentive.
The author maintains an optimistic attitude towards Layerzero and the cross-chain field, but also raises some potential issues. Most existing cross-chain protocols belong to L0 (transport layer), mainly used for asset transfer and information transmission (social, governance, etc.). In terms of asset transfer, the existing cross-chain bridges are pseudo-cross-chain, the author believes that true cross-chain means that an asset truly crosses to another chain (Burn/Mint), rather than Lock/Mint or Atomic Swap. However, to achieve this, it would require tearing down all existing old projects and letting new projects take their place, with token issuance following the OFT model. But the difficulty of implementation is too great and requires a long period of transition.
In reality, we still live in a world that relies on “third parties,” and the chains are still isolated from each other. In terms of information transmission, the chains can rely on the transport layer for message delivery between them, but the current demand is not significant. For example, if there is a need for message delivery between Lens and Cyber, it would require cross-chain functionality. However, firstly, it is still uncertain when the social field will develop on a large scale, and secondly, if the majority of dapps are deployed in the Lens ecosystem, they already have the ability to communicate freely with each other, so there is no need for cross-chain functionality. Cross-chain only has significant demand in a highly competitive environment.
This also leads to the topic of Layer2 superchains as a new threat. For example, the success of OP superchain will lead to more Layer2 adopting similar technologies for development, and they can seamlessly connect (assets) with each other. The success of future blockchains will not be able to accommodate too many users and transactions with solely OP and other roll-ups, and it will give rise to more Layer2 solutions. The essence of seamless connection is to share a settlement layer. In this way, asset transfers do not need to go through third parties, but obtain transaction data from the same settlement layer and validate them on their respective chains. Similarly, cross-chain protocols would like to see competition between OP, ARB, ZKsync, and Starnet, without any obvious hierarchy, so that cross-chain transfers can be enabled between these chains’ ecosystems. Otherwise, if one Layer2 occupies 80% of the market share, there would be no need for cross-chain functionality. However, the future is still full of variables, and this is just the author’s concern, to be determined in due course.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Aiming for the opportunity of the next bull market Ordinals ecosystem
- LianGuaiWeb3.0 Daily | CZ Binance Leads the Way in Regulatory Compliance
- Who profited from the Federal Reserve’s nearly $100 billion loss due to interest rate hikes?
- Four financing events worth paying attention to last week DeForm, FirstMate, Stroom Network, BuidlerDAO.
- Multichain has fallen, what can save the cross-chain bridge?
- Ethereum SAAS Staking One-Week Data Record
- DeFi Regulatory Woes Uniswap in Heaven, Tornado Cash in Hell





