An Overview of Mainstream Cryptocurrency Exchange Account Password Leakage Data and Security Mechanism Analysis
Cryptocurrency Exchange Account Password Leakage Data and Security Mechanism Analysis OverviewThis article is jointly published by DilationEffect and Wu Shuo Blockchain.
It is not easy to analyze the security level of exchanges’ protection because it is difficult to understand the specific security investment inside the exchanges. Dilation Effect has previously selected the unique dimension of smart contract authorization to analyze the main wallet addresses of TOP exchanges and institutions in the industry and timely disclose the discovered issues. This time, we try to analyze the account security mechanisms of these mainstream exchanges from the perspectives of attackers and users, as this directly affects the fund security of specific users.
1. Password Leakage of Mainstream Exchange Accounts
Attempt to filter the relevant domain names of mainstream exchanges through public data leakage search websites (data sources include the dark web, file-sharing platforms, historically leaked account data sets, etc.). You should know that attackers will also perform the same actions.
First, search Binance.com and find that it returns more than 8,000 plaintext data of accounts and passwords! We take some fragments as examples:
- Blockchain Game of ERC-6551 Use Case
- Exclusive Interview with Web3Brand How do AI and Web3 achieve mutual development in the wave of technological advancement?
- a16z Zero-knowledge proofs are just a magic trick
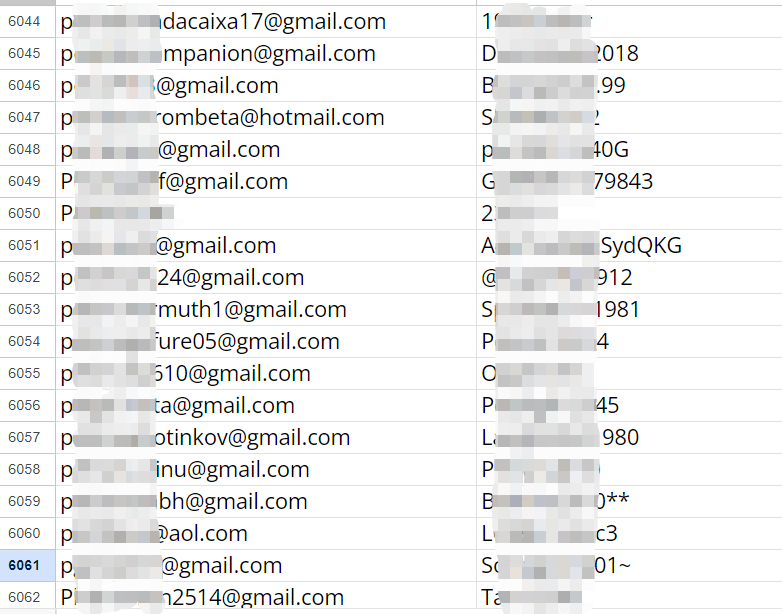
From these data, we randomly select some for login attempts and find that many accounts and passwords are completely correct. After attempting to log in, we can directly enter the next step of two-factor authentication, such as this mar***@gmail.com account:
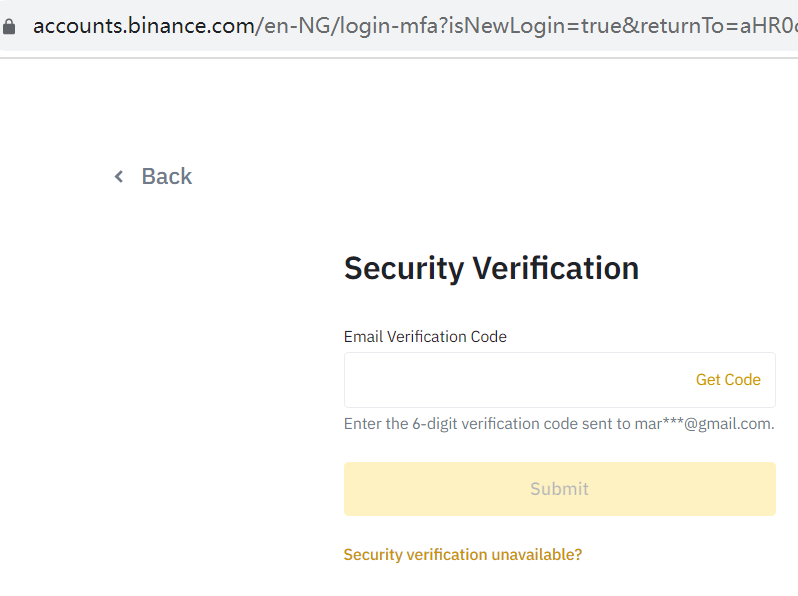
If the account and password of this user’s email are also the same as the exchange’s login email account/login password, the attacker can directly obtain the two-factor authentication email verification code and log in to the user’s Binance account. Isn’t it quite explosive? It is worth emphasizing that our verification attempts stop here, and no further actions are taken.
Dilation Effect has preliminarily counted the password leakage situation of more than a dozen mainstream exchanges, with thousands of leakage records for each. The specific order of magnitude is shown in the following table:
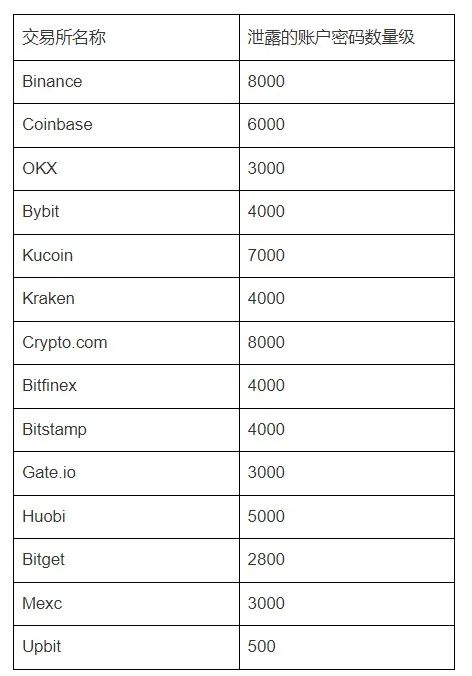
It’s somewhat shocking.
Due to time constraints, Dilation Effect did not check the accuracy of these account passwords one by one. However, by randomly selecting data, we found that each exchange’s leaked account passwords contain correct account and password information, and the initial estimate is that the average correct ratio is about 10% to 20%.
Account and password leakage does not directly lead to user fund losses because exchanges provide additional 2FA mechanisms. However, if users have not set up comprehensive settings, there is still a risk of fund theft, such as users only enabling email verification or other authentication factors being attacked.
Next, we will continue to analyze the security strength of the current mainstream 2FA two-factor authentication mechanisms.
2. Security Comparison of Common 2FA Authentication Mechanisms
First, let’s give a comparison conclusion on the security levels of various second-factor authentication factors:
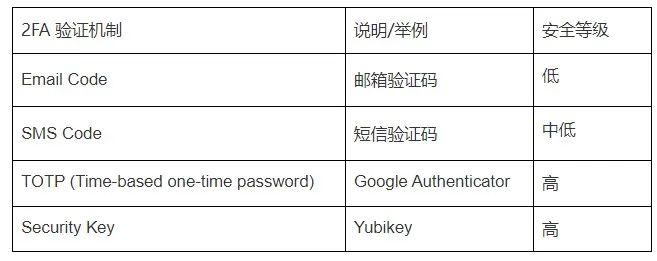
The Dilation Effect believes that ordinary user emails are relatively vulnerable in terms of security, and email verification codes are not stable security verification factors. Nowadays, if users only set up email verification codes as 2FA, then the security of this account can be considered zero. It should be recognized that in the past, major internet service providers have been attacked, resulting in large-scale username/password leaks, and email service providers also have potential unknown vulnerabilities, all of which have led to a large number of user email accounts being in an unsafe state. Overall, the security of email verification codes is very low.
SMS verification codes also face many attack scenarios. For example, in targeted attack scenarios, attackers can deploy fake base stations near a high-value user to intercept their SMS messages. Another example is the SIM swapping attack that the Lapsus$ hacker group is currently fond of. Simply put, the SIM swapping attack involves using social engineering to impersonate a user and transfer their SIM card to the attacker’s name. Especially with the emergence of eSIM, attackers can complete the application and activation online, making the attack easier. Twitter founder Jack Dorsey’s Twitter account has been attacked in this way before. Another issue is legal interception by telecommunications operators, but we won’t go into detail about this scenario. Those who understand it, understand it. Therefore, the security level of SMS verification codes is also relatively low.
TOTP and Security Keys face fewer threats. The Dilation Effect recommends that users at least enable Google Authenticator as a basic security setting, and users with higher security requirements can use physical Ukeys. If you only set up email verification codes or SMS verification codes, it’s only a matter of time before your account is attacked.
In addition, some exchanges have started to support hardware keys, which are a strong security mechanism for users to replace traditional passwords. It is recommended that users gradually become familiar with their use.
III. Recommendations for Exchanges
Exchanges should immediately initiate emergency response procedures, investigate the leakage of user account passwords, and guide affected users to change their passwords and improve their account security settings. At the same time, daily monitoring of user account password leaks should be actively conducted. If you don’t know how to find your own user’s password leak data, you can contact Dilation Effect for communication ([email protected]).
We recommend that exchanges adopt a “Secure by Default” design philosophy and consider more about the security of user accounts, so that after users complete the security settings, their accounts can be in a relatively secure state. Some design principles that can be referred to are that users must complete the binding of Google Authenticator to meet the security baseline, so when users register, they should be guided to complete the settings as much as possible, and sensitive operations including withdrawals can only be conducted after completing the settings.
IV. Recommendations for Ordinary Users
Awe of network security. Attackers are diligent, while the understanding of network security among users is relatively scarce. Even V God’s Twitter account was hacked a few days ago. Users should not ignore their account security settings just for the convenience of withdrawing funds, and often regret it after being attacked. Therefore, it is recommended to at least bind Google Authenticator to your account.
In addition, there is a treasure website where users can regularly check the leakage of their email passwords, which is worth bookmarking:
https://haveibeenpwned.com
About Dilation Effect
DilationEffect is a recently established Web3 security community composed of experts in network security from around the world, focusing on sharing objective and neutral Web3 security perspectives.
- DilationEffect is the first team in the industry to propose the risk of asset theft when iPhone users download wallet applications using shared Apple IDs, and has also conducted exclusive analysis and disclosure on:
- The smart contract authorization risk of the main wallet addresses of top institutions such as Binance, KuCoin, Jump, etc.
- The security risks of the Defi cross-chain lending protocol Prime Protocol invested by Jump
- The risks brought by using GMX’s GLP and related tokens (mGLP, etc.) as collateral assets for lending protocols
- The centralized security risks of the most popular aggregated cross-chain bridge protocol Bungee in the industry
DilationEffect will continue to release various Web3 security perspectives, comment on the security of Web3 products and protocols in the industry, and provide timely and effective security reminders to ordinary users.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Stanford Blockchain Week Highlights MEV, L2, ZKP, On-chain Order Book…
- Visa Deep Dive into the High-Performance Blockchain Network Solana, Why is it the Choice for Visa Payments and Stablecoin Settlement?
- Principles, Current Applications, and Risk Mitigation of Intent
- Excitement in the NFT Winter Doodles Releases Limited Edition Holed Shoes, Sold Out in 72 Hours
- Analyzing the potential risks of the TG BOT track from a domestic legal perspective
- Vitalik’s Full Text on the Evolution of Ethereum in Singapore Ten Years of Ethereum and Current Challenges
- Weekly Selection | Market Weakness, TG BOT Track Has a Unique Landscape; MakerDAO Wants to ‘Defect’ from Ethereum; Lido Faces Centralization Doubts Again