Principles, Current Applications, and Risk Mitigation of Intent
Intent Principles, Applications, and Risk MitigationIf a Transaction refers to how to perform an action, then Intent refers to the expected outcome of that action.
If the instruction of the Transaction is:
“Perform operation A first, then perform operation B, then pay C to obtain D.”
The corresponding Intent is:
- Excitement in the NFT Winter Doodles Releases Limited Edition Holed Shoes, Sold Out in 72 Hours
- Analyzing the potential risks of the TG BOT track from a domestic legal perspective
- Vitalik’s Full Text on the Evolution of Ethereum in Singapore Ten Years of Ethereum and Current Challenges
“I have the ability to make the payment, and I want to obtain D.”
Protocol centered around Intent can significantly improve user experience and efficiency. Transactions require users to explicitly specify each parameter, which has a higher barrier to entry. In contrast, using Intent, users can simply express the desired result and outsource the task of achieving the best implementation result to a mature third party.
Although Intent provides more possibilities for the ecosystem, Ethereum’s on-chain Intent-based design may also have a significant impact on off-chain infrastructure, and there are important connections to MEV-related activities and market control.
How Intent Works
Currently, the standard method for users to interact with Ethereum is to create and sign transactions and specific formats of information that provide all necessary information to execute state transitions for the EVM. However, creating a transaction can involve quite complex operations. Creating a transaction requires a lot of details about smart contracts and things like nonce management, while holding specific assets to pay for gas fees. Due to the need for users to make decisions in situations where there is insufficient information or complex execution strategies, this complexity leads to poor user experience and reduced efficiency.
The goal of Intent is to alleviate the burden on users. Intent allows users to outsource transaction creation to third parties without giving away complete control by signing a set of descriptive constraints.
In the process of a standard transaction-based flow, when validators are incentivized to perform verification, the transaction signature allows the validators to accurately follow the computational path for a specific state. In contrast, Intent does not specify exactly which computational paths must be taken, but allows for any operations that satisfy specific constraint conditions. By signing and sharing Intents, users effectively grant the recipient the authority to choose the computational path on their behalf (as shown in the figure below). It is worth noting that a single transaction can contain multiple Intents, which can match overlapping Intents, saving gas fees and improving economic efficiency. In addition, users can also pay gas fees more flexibly, such as allowing third parties to sponsor gas or make payments with other tokens.

As shown in the figure, when submitting a transaction, the user specifies the exact computational path; when submitting an Intent, the user specifies the goal and some constraint conditions, and it is up to Matchmaking to decide which computational path to take.
Current Applications of Intent
Creating Intents allows for the outsourcing of complex matters related to interacting with the blockchain while allowing users to retain custody of their assets and cryptographic identities. In fact, many concepts regarding Intent correspond to systems that have been running for several years, such as the following scenarios:
Restricted Orders: If a user receives at least 200 B tokens, they can withdraw 100 A tokens from their account.
Cowswap-style auction: Similar to limit orders, but relies on third parties or mechanisms to match multiple orders to maximize execution quality.
Gas sponsorship: Users can choose to pay transaction fees in USDC instead of ETH, with USDC in their accounts to cover gas fees.
Delegated authorization: Only allows interaction with specific accounts in certain pre-authorized ways. Intent can only be achieved if the final transaction follows the access control list specified in the Intent.
Merged transaction processing: Allows for the merging of multiple Intents to improve gas efficiency.
Aggregator: Operates only with the best price/yield, proving the execution of multiple scenarios and taking the optimal path to achieve Intent.
Currently, Intent has new applications in cross-chain MEV (such as SUAVE), ERC4337 account abstractions, and Seaport order scenarios. As ERC4337 develops, other new applications (such as cross-domain Intent) are also in the exploration stage.
In all Intent-based applications, there needs to be at least one group that understands Intent and is incentivized to execute it in a timely manner. The question of who plays this role, how it is executed, and what incentives are in place needs further exploration and practice to determine the efficiency, trustworthiness, and other impacts of Intent-driven systems.
Intermediaries and Mempool
The most obvious way for Intent to enter the hands of willing intermediaries is through Ethereum’s Mempool. However, the current design of Mempool does not support the propagation of Intent. In the long run, considering the vulnerability to DOS attacks, the possibility of widespread support for the propagation of Intent in the Ethereum Mempool is very low. It can be said that the openness and permissionless nature of the Ethereum Mempool pose barriers to the adoption of Intent.
Without the Ethereum Mempool, Intent system designers face some problems. The current dilemma is whether to propagate Intent to permissioned parties or in a permissionless manner so that any party can execute Intent.
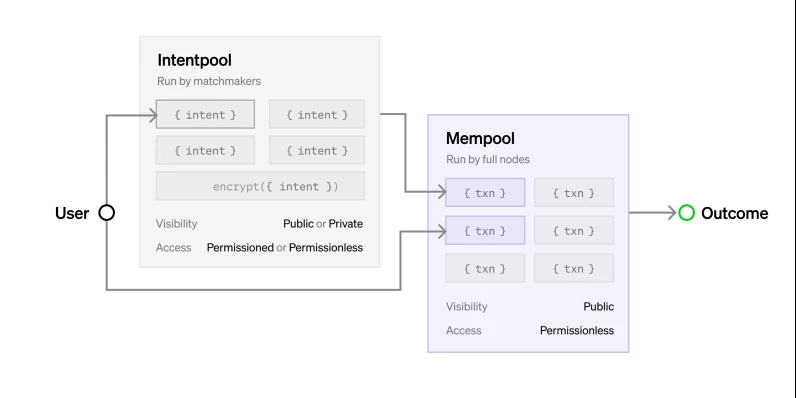
As shown in the diagram, Intent flows from users to permissioned/permissionless public/private Intent pools, then is converted into transactions through matchmakers, and eventually converted into the public Mempool or directly displayed on the chain through MEV Boost-type auctions.
Permissionless Mempool
One design that is being attempted is a decentralized API that allows nodes in the system to broadcast Intent through gossip, providing permissionless access to executors.
For example, in the 0x protocol relay, gossip broadcasting is done for limit orders to find matches and put them on the chain. In the context of a shared ERC4337 Mempool, this approach is also being explored to counter centralized and censorship risks. However, the design of this permissionless Intent pool also faces the following challenges:
DoS resistance: Developers may need to limit the functionality of Intent to avoid potential DoS attacks.
Dissemination incentive measures: For many applications, executing an Intent is a profitable activity. Therefore, in theory, nodes operating Intentpool have the motivation not to propagate Intents in order to reduce competition in executing Intents.
MEV: Since the quality of Intent execution depends on the good behavior of off-chain participants, there are some difficulties in using public, permissionless Intentpools. If execution is profitable, permissionless Intentpools may attempt to arbitrage against users. This is similar to the “sandwich attack” in the current Ethereum Mempool and will be a common problem for Defi-related Intents. A possible improvement could be the creation of permissionless Intentpools that perform encrypted processing.
Permissioned Mempool
Trusted centralized APIs have stronger resilience against DOS attacks and do not require Intent propagation. This trust model provides a basis for addressing MEV concerns. As long as the trust assumption holds, execution quality can be guaranteed. Trusted intermediaries may also have reputations associated with them, providing incentives to faithfully execute operations.
Therefore, permissioned Intentpools are attractive to Intent-based application developers in the short term. However, the strong trust assumption has inherent flaws and somewhat contradicts the original spirit of blockchain.
Hybrid Solutions
There are also hybrid solutions that combine the above two cases. For example, there is a case where the propagation process is permissioned but execution is permissionless, and vice versa. A common example of a hybrid solution is order book auctions.
The idea behind such designs is that users of counterparties may need to distinguish between better and worse counterparties in order to transact at more favorable prices. The design process typically involves a trusted party who obtains Intents (or transactions) from users and facilitates the auction on their behalf. Participation in the auction is permissionless. These designs also have drawbacks and are likely to face various interferences in permissioned Intentpools.
The bottom line of this solution is that Intent-based applications not only involve new message formats for interacting with smart contracts, but also require propagation and counterpart discovery mechanisms in the form of an alternative to mempools. The most critical aspect currently is to design an incentive-compatible and decentralized Intent discovery and matching mechanism.
Risks and Mitigation Methods
Although Intent is an exciting new transaction paradigm, its widespread adoption also means a trend of greater user activity shifting to alternative mempools. If mismanaged, this transition may harm Ethereum’s decentralization and lead to excessive power of trusted parties. There are several potential risks:
Order flow: If Intent execution is permissioned but users are careless in their choices and migrate it from the public Mempool, Ethereum block production may become centralized.
Trust: Since many solutions require trust in intermediaries, the high entry barriers hinder the development of new Intent-based architectures and slow down innovation and competition in order to ensure the quality of Intent execution.
Transparency: Since many Intent architectures require users to give up some control over their chain assets and permissioned Mempool as a compromise, this means that there is a certain degree of impermeability externally, so there are opaque risks in the established system. In this case, it is unclear how user expectations are met and whether there are undiscovered ecosystem threats. Even the middleware and Mempool ecosystems that develop between users and the blockchain will become opaque.
So how to reduce the above risks? We know that the space of the Ethereum Mempool is limited. For certain applications, the risk is due to their lack of privacy, so they cannot support a wider range of message formats. This puts wallet and application developers in a dilemma because they must find a way for users to connect to the blockchain while avoiding the above risks.
An ideal system should be permissionless so that anyone can match and execute Intents without sacrificing too much execution quality. The system should be generic so that new applications can be deployed without the need to establish a new Mempool. The system should be transparent so that the process of executing Intents can be publicly reported, and data for quality audits can be provided when privacy guarantees allow.
Although teams like FlashBots and Anoma are working hard to meet the requirements of the above generic solutions by combining privacy and permissionlessness, it is difficult to create such a perfect system in the near future. Therefore, users need to weigh the options and choose different solutions for different applications. Similarly, applications that initiate Intentpool need to seek universality without permission and carefully choose intermediaries with permission.
Intent-based application designers need to consider the off-chain implications of their applications comprehensively, because they not only concern their user base, but also involve a wider community, which requires a wider community to pay close attention to the off-chain ecosystem around Ethereum.
Summary
Due to the clear market demand for Intent applications, many Intent-based applications have been widely used for several years. More and more Intents are driven by ERC4337, which may accelerate the transition from the Ethereum Mempool to new locations. The adoption of Intent represents a shift for users from a “forced operation” paradigm to a “descriptive” paradigm, which is expected to greatly improve user experience and efficiency.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Weekly Selection | Market Weakness, TG BOT Track Has a Unique Landscape; MakerDAO Wants to ‘Defect’ from Ethereum; Lido Faces Centralization Doubts Again
- Understanding Zan, the latest Web3 brand of AntChain, in one article.
- Flashbots Research Report A Beam of Light for MEV, Piercing the Dark Ethereum Night Sky
- Cartridge A new player in the gaming industry, advancing together with infrastructure and game development.
- Interpretation of the ‘Tokenization of Hong Kong Bonds’ Report Using Evergreen ‘Green Bonds’ as an Example, Reviewing the Theory and Practice of Bond Tokenization.
- Blockworks From the Blockchain Impossible Triangle to the Big Convergence
- Beyond Ethereum – Third Generation Blockchain Will Drive Mass Adoption