Study on Dilation Effect: Contract Authorization Risks of Major Wallets such as Binance. Are Big Institutions Really Safe?
Dilation Effect Study: Are Large Wallets Safe? Examining Contract Authorization Risks in Institutions like Binance.This article is jointly published by Dilation Effect and Wu Shuo Blockchain.
Mainstream exchanges and institutions undoubtedly invest a lot of money and manpower in network security protection. Dilation Effect cannot know the security level and implementation details inside these institutions, but out of curiosity, we want to try to analyze these institutional wallet addresses through public information, to see whether there are potential security risks from the perspective of ordinary users and how large the potential risk exposure is.
All the data in this flash review comes from public services such as Etherscan and Debank.
1. Selection of Analysis Objects
- Reviewing the history of stablecoin crashes: An analysis of the potential risks of USDT
- How to identify “smart money” and track them?
- Another strong contender has arrived in the Ethereum L2 game: produced by the parent company of the Fox Wallet, zkSync is one of the strongest competitors.
View the Top 1000 Accounts on Etherscan and select the tagged institutional addresses.
2. Selection of Analysis Dimensions
Since we do not understand the technical details of how these exchanges and institutions generate and manage wallets, how can we analyze the security of addresses? The dimension selected by Dilation Effect this time is analyzing the contract authorization of these addresses.
Because it is common for addresses to be stolen by malicious contracts or contracts with vulnerabilities due to authorization. Limiting the authorization amount and regularly cleaning up authorization has become the best security practice. So how do these large exchanges manage their addresses? We randomly select a few addresses for analysis.
Case One
Address:
Binance 8 (0xF977814e90dA44bFA03b6295A0616a897441aceC)
This is the wallet address with the largest balance on Binance, with a total of 10 billion US dollars on the ETH chain and a total of 16.1 billion US dollars on other chains. The screenshot of some assets is as follows:
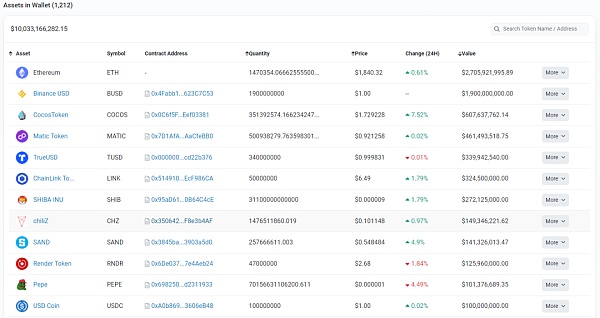
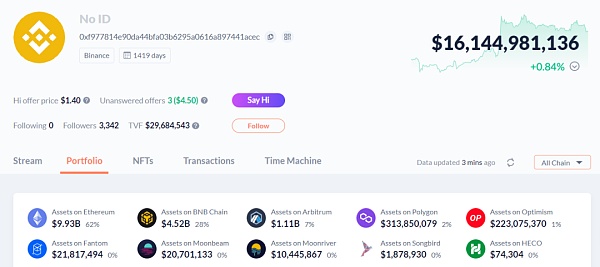
Checking the contract authorization situation of this address on the ETH chain, it is found that there is a risk of 3.2 billion US dollars. Of course, this does not mean that there must be deterministic security risks. This is only a possible description of potential risk exposure.
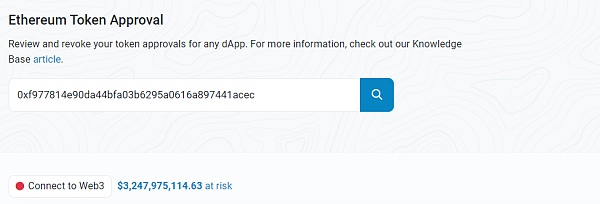
So let’s take a closer look at how this address is authorized, such as which currency is authorized to which contract, and how much is authorized. The following are some of the query results.
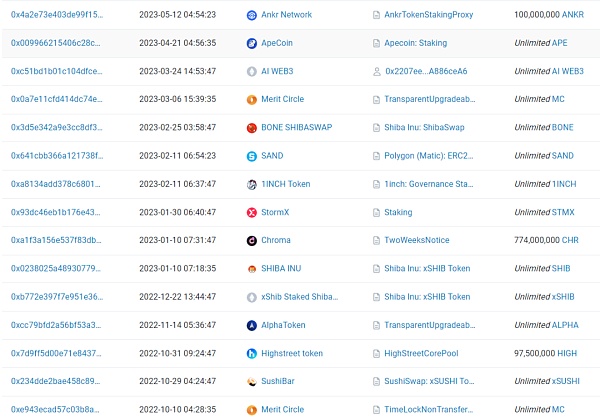
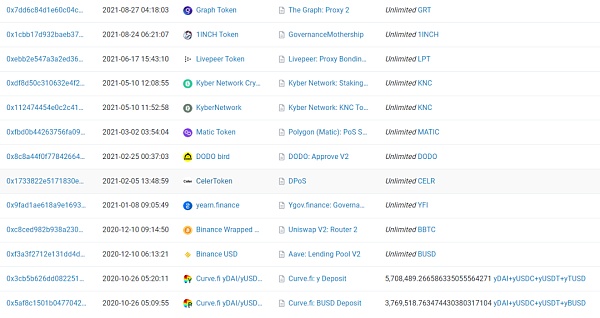
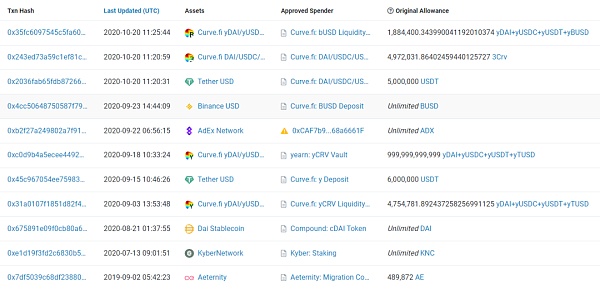
At this point we noticed a strange phenomenon, which is that some currencies on this address have limited authorization limits, while others have no limit at all. The authorization limit rules do not seem to be uniform. We pay particular attention to BUSD, Matic, SHIB, and SAND, which have relatively large balances on the address, with balances of 1.9 billion US dollars, 460 million US dollars, 260 million US dollars, and 140 million US dollars, respectively. The relevant authorization records are as follows:
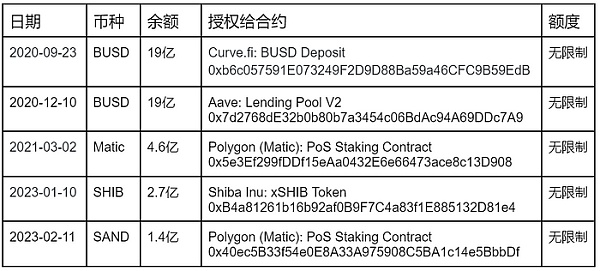
There are several obvious problems here:
First, the authorization for the contract is not regularly cleaned up. For example, the contract authorization for BUSD has not been cleaned up for more than two years, either because it was not noticed or because it was not considered necessary. This indicates that Binance lacks systematic coverage of this area in its internal security management. Some might say that the relevant authorization contracts have been analyzed and found to have limited operations, which are relatively safe. But what we want to say is that this is not just a technical issue, but more of a security management issue. That is, how Binance can manage the risks brought by third-party contracts comprehensively and systematically, we believe that it can be more stringent and in-depth. In fact, if you look closely, you will find that Aave: Lending Pool V2 is an upgradable proxy contract, and if (I mean if) the Aave contract is attacked, there will be a loss of 1.9 billion U.S. dollars here.
Second, a large number of currency authorization limits are unlimited. Once the corresponding contract is attacked in an extreme situation, if the authorization limit is restricted, the risk will be correspondingly reduced. This also exposes the lack of systematic coverage of this area in Binance’s internal security management. Of course, you may say that these are all extreme situations, but for the crypto industry, many low-probability events have happened in history. It is very necessary to increase risk sensitivity and maintain extreme aversion to risk.
Third, the currency authorization rules are not uniform, and some currencies have limited limits, while others have no limit at all, and the actions are not uniform. This indicates that Binance’s internal security management operations are unclear, or the internal team has not done a good job in division of labor and cooperation.
In addition, we are also very curious why addresses with such huge asset balance scales need to participate in Defi contract operations frequently? Can Binance make more granular address planning and isolation design?
Case 2
Address:
Kucoin 6 (0xD6216fC19DB775Df9774a6E33526131dA7D19a2c)
This is the address of Kucoin exchange, with $1.7 billion on the ETH chain and $1.9 billion on other chains. The asset screenshot of this address is as follows:
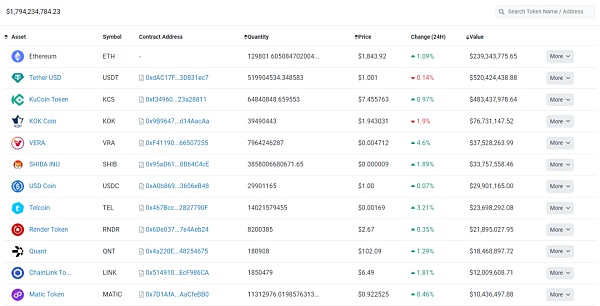
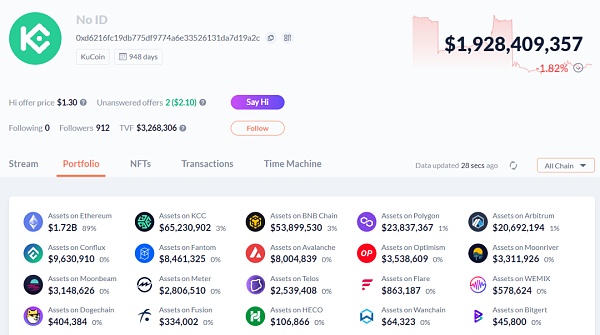
Checking the contract authorization of this address on the ETH chain, it is found that $1.1 billion has risks. Similarly, this does not necessarily mean that there is a security risk, but only describes the possibility of potential risk exposure.
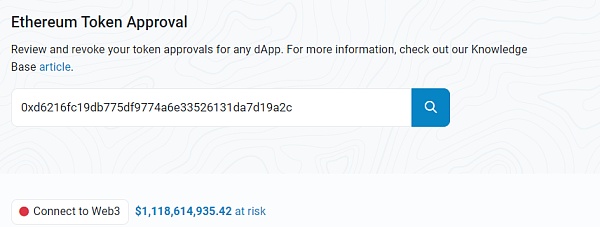
Now let’s take a look at the authorization of Kucoin’s address.
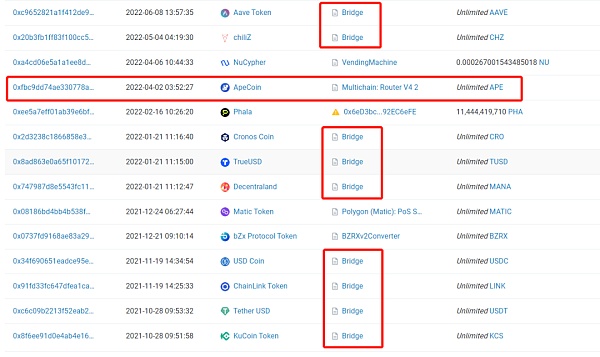
Wow! We have found something interesting again.
1. The APE currency of this address has been authorized to the cross-chain Router contract of Multichain on April 2, 2022. Everyone should know that Multichain had an event of force majeure a few days ago, but Kucoin did not cancel the authorization of the Multichain contract at the first time. This reflects that Kucoin still has room for improvement in emergency response to risks.
2. The large amount currencies USDT ($500 million), USDC ($290 million), KCS ($480 million) authorized by this address are all authorized to the contract named Bridge, and the authorization amount is completely unlimited. After a simple analysis, it is found that Bridge is the cross-chain bridge contract of KuCoin community chain KCC, but no security audit report was found on the official website of KCC, which makes people panic. Do you still remember the 2 million BNB attack incident on the BNB Chain?
Case 3
Address:
Jump Trading (0xf584F8728B874a6a5c7A8d4d387C9aae9172D621)
This is the address of the institution Jump Trading, with $140 million on the ETH chain and $150 million on other chains. The asset screenshot of this address is as follows:
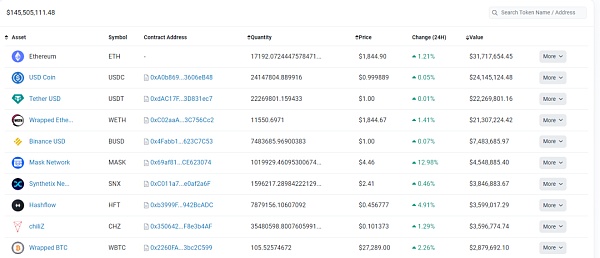
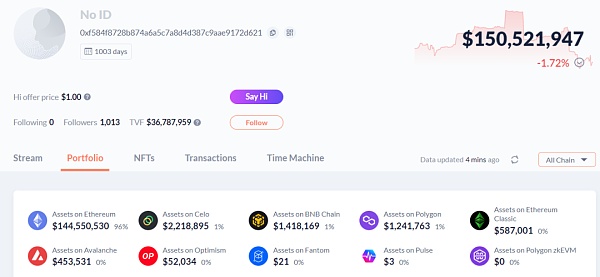
Checking the contract authorization of this address on the ETH chain, it is found that $25 million has risks. Similarly, this does not necessarily mean that there is a security risk, but only describes the possibility of potential risk exposure.
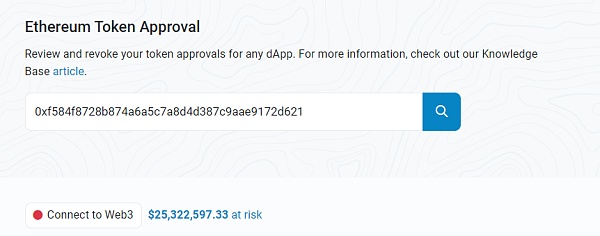
Let’s take a closer look at the authorization status of the address for Jump Trading.
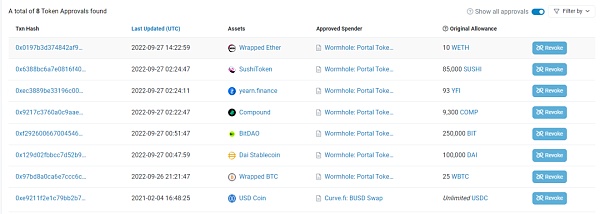
It can be seen that there are not many authorizations for the currency on this address, and the vast majority of authorizations have set limits, so the overall management is still good.
However, the USDC currency was authorized to the Curve contract on 2021-02-04, with no limit set, and it has not been canceled. This needs to be reminded, and if there is no corresponding contract operation needed, it is recommended to cancel the authorization for this contract immediately.
Summary
This flash review is over. Dilation Effect randomly selected several exchange and institutional addresses for analysis. From the results, it can be seen that these institutions are not doing very well in terms of contract authorization. We hope that our analysis can provide reference for relevant institutions. Exchanges and institutions that were not selected can also refer to the analysis process in the previous text to check for similar issues.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- zkSync’s Road to Mass Adoption: The Ecosystem is Still in its Early Stages with Many Variables in the Future
- Opinion: Exploring the Development Potential of the Ordinals Ecosystem from ORDI to OXBT
- Explaining dYdX Indexer in detail
- Hong Kong’s new anti-money laundering regulations have taken effect. Here are the key compliance points:
- Origin and Development of ZKP: From the 1980s to Present
- 【Exclusive from ChainDD】Analysis of 525-page EU Regulatory Regulations: Step-by-Step Guide to Writing White Papers, Only 3 Types of Cryptocurrencies Approved
- Comprehensive analysis of the .sats domain





