How does Worldcoin specifically handle privacy?
How does Worldcoin handle privacy?Author: Sydney, Cryptocurrency KOL; Translator: LianGuaixiaozou
Worldcoin has launched. How does it protect privacy? Let’s take a closer look at the Semaphore protocol and ZK-SNARKs.

Worldcoin uses Orbs specialized hardware that can scan users’ irises to verify their identity. Worldcoin is an L2 solution running on Ethereum, extending Semaphore (which will be explained in detail later) and using ZK-SNARKs.
- The US Senate Includes Cryptocurrency Provisions in Defense Bill
- Struggle between Ripple and the SEC What Will Happen Next? Experts Assess 4 Possible Outcomes
- Analyzing the Current State of the Solana Ecosystem from On-chain Data

With Worldcoin’s use of Zero-Knowledge Proofs (ZKP), users can prove ownership of their database private keys without revealing the corresponding public keys. This means that no one can link any operations to a specific identity.
Orb scans your iris and generates a hash value. It is not a typical SHA256 hash value. It uses an algorithm based on Gabor filters, as two photos of the same iris are not exactly the same.
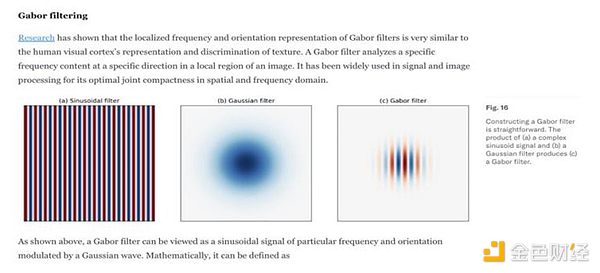
Unless approved by you, the original biometric data does not leave Orb, and the hash value is stored separately from your profile or wallet. In the worst case scenario, if an attacker scans your iris, they can only know whether you are in the database.
The Semaphore protocol is an anonymous identity verification tool, which works as follows:
(1) Users create an identity;
(2) The identity is submitted to a Merkle tree;
(3) When a user wants to perform an operation, a ZK-SNARK is generated;
(4) Anyone can verify based on the root of the Merkle tree.
Worldcoin extends Semaphore using ZK rollup, as follows:
(1) Identity commitments are forwarded to the signup sequencer;
(2) The signup sequencer inserts the commitment into a queue;
(3) A single fixed batcher processes the queue (current) and computes a Merkle tree update proof;

(4) The Prover computes a Groth16 proof using the initial root, final root, and insertion start index;
(5) The Batcher creates a transaction and submits it to a relayer;
(6) The Relayer allocates fees, signs the transaction, and submits it to blockchain nodes;
(7) The World ID contract verifies transactions from the sequencer;
(8) The Groth16 verifier contract checks the integrity of the ZKP;
(9) The old root is deprecated and the new root is placed into the contract.
In his blog post about Worldcoin, Vitalik Buterin made two suggestions for improving privacy:
· The first is to improve the iris hash algorithm to reduce scan variances. This will reduce the amount of stored data by using “helper data” instead of storing the complete hash value.

· Secondly, the iris hash database is stored in a multi-party computation (MPC) system that can only be accessed by Orbs. This makes the data inaccessible but introduces governance complexity.
Personally, I wouldn’t scan my eyeballs, but this technology is interesting. I do think the current doomsday discourse is a bit exaggerated.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Exploring Sidechains and Rollups Differences and Similarities in Architecture, Security Guarantees, and Scalability Performance
- Fed raises interest rates to the highest level in 22 years, Powell warns that there will be no rate cuts this year.
- LianGuai Morning News | Insider The United States may reach a comprehensive framework agreement on stablecoins.
- How to handle the confiscated virtual currency worth 400 billion yuan involved in the case?
- Is the hype around AI Agents that Silicon Valley giants are talking about real or just a bubble?
- Be vigilant of the hidden rug pull caused by contract storage leading to a run-off.
- Variant Partner Why is UniswapX said to be a boost for Uniswap?