Curve is deeply involved in a security incident, how to establish a defense mechanism to prevent hackers and trace funds?
How to establish a defense mechanism to prevent hackers and trace funds in response to Curve's security incident?Produced by|OKLink Research Institute
Author|MatthewLee
On July 31st, Curve announced on the platform that the stablecoin pool of Vyper 0.2.15 was attacked due to a vulnerability in the compiler. Specifically, due to the ineffectiveness of the reentrancy lock function, hackers were able to easily launch reentrancy attacks, allowing attackers to execute certain functions in a single transaction. Some of the funds on Curve were using an older version of the compiler, providing an opportunity for hackers.
(Reentrancy attack is a vulnerability caused by the combination of Vyper’s features and improper smart contract writing. It has occurred multiple times before, and OKLink’s security team has previously conducted detailed analysis of such cases. Click “Read the original article” in the lower left corner of the article to view, so this article will not display the attack details)
- Data Interpretation Holders reluctant to sell, Starbucks NFT series profitable across the board.
- Governance Methods and Solutions of Four Platforms under Curve Liquidation Crisis
- Opinion Could Swell become a strong competitor to Lido?
Shortly after, several other projects announced that they had also been attacked, including NFT collateral protocol JPEG’d, lending project AlchemixFi, DeFi protocol MetronomeDAO, cross-chain bridge deBridge, and DEX Ellipsis which uses the Curve mechanism, all suffered huge losses.
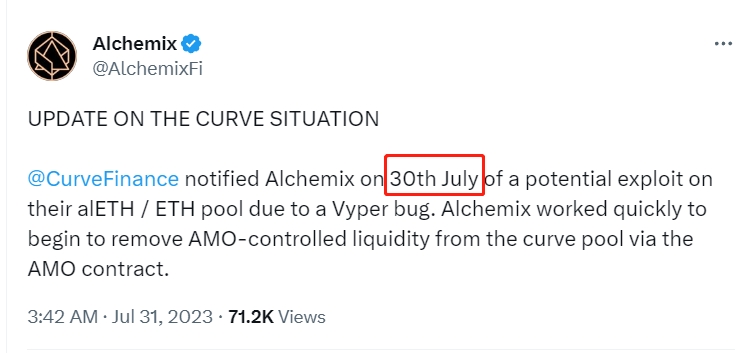
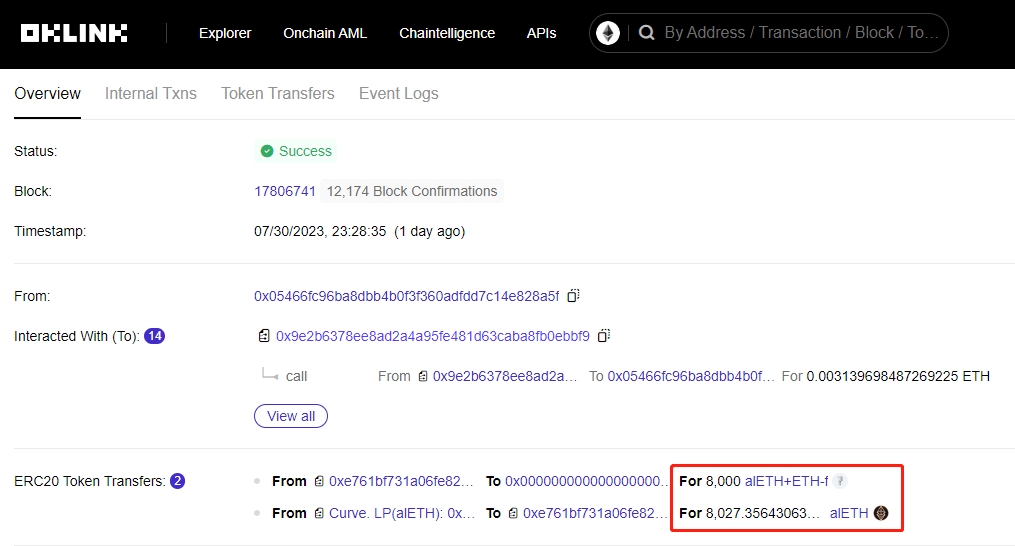
However, on July 30th, some project teams were already aware of the potential attack threat. Taking Alchemix as an example, they began to transfer assets on the 30th and successfully transferred 8000 ETH. However, during the asset transfer process, the remaining 5000 ETH in the AMO contract was still stolen by the attacker.
Image source: OKLink Explorer
Other project teams have also taken some measures, such as AAVE banning Curve from borrowing; Alchemix also removing liquidity controlled by AMO from the Curve pool; Metronome directly pausing mainnet functionality.
How to defend against hacker attacks from both the offensive and defensive ends?
Curve is not the first top-level DeFi project to be attacked by hackers. Ordinary project teams should pay more attention to both the hacker attack side and the contract defense side.
So what preparations can project teams make for the offensive end?
The OKLink team recommends that project teams use the on-chain labeling system to identify wallets with a history of misconduct in advance and prevent interaction with addresses that have had abnormal behavior. One of the attackers on Curve has a record of misconduct that was recorded by OKLink, as shown in the following figure:
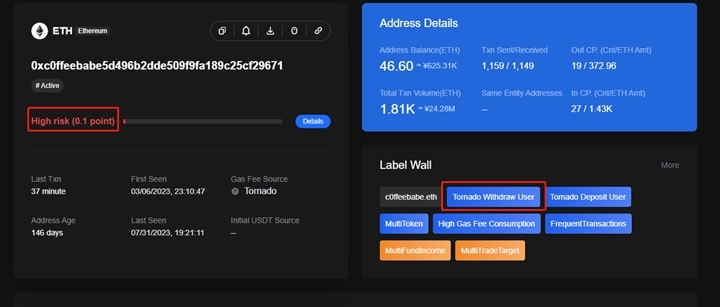
Image source: OKLink Chaintelligence Pro
Their behavior pattern also exceeds normal logic to a certain extent, as shown in the following figure, with transactions exceeding 100 in three days.
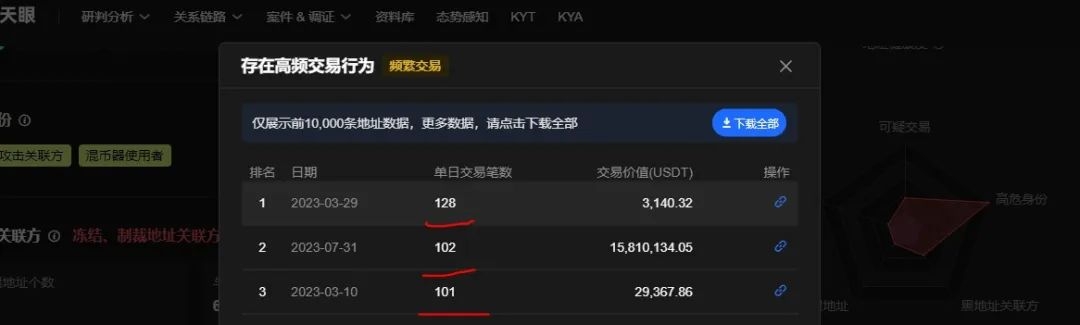
Image source: OKLink Onchain AML
How can project parties defend themselves on the defensive end?
In response to the above incidents, we have identified two issues that project parties need to address when dealing with such events:
1. Insufficient maintenance work. Most projects focus heavily on code writing and auditing, but maintenance work has always been neglected. The vulnerability in the Vyper compiler was discovered two years ago, but the attacked pool still used an outdated version of the compiler.
2. Too narrow code testing scenarios. Many test codes do not effectively test for problems. More complex testing methods, such as fuzz testing, should be added, and testing should be conducted from multiple dimensions, such as hacker attack routes, attack complexity, confidentiality, and integrity.
How can stolen funds be recovered?
In reality, it is difficult to recover most stolen funds. The following image shows the destination of the hacker’s transferred funds. It can be seen that the stolen ETH was not transferred externally, and the address is not associated with any physical institutions.
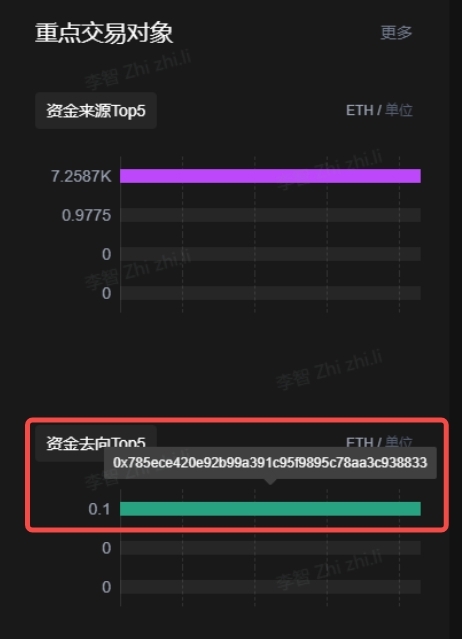
Image source: OKLink Chaintelligence Pro
Some addresses are associated with physical institutions, such as the address 0xb752DeF3a1fDEd45d6c4b9F4A8F18E645b41b324 (2,879.54 ETH has been returned). By reporting and negotiating with physical institutions, we can recover the funds for similar addresses associated with physical institutions.
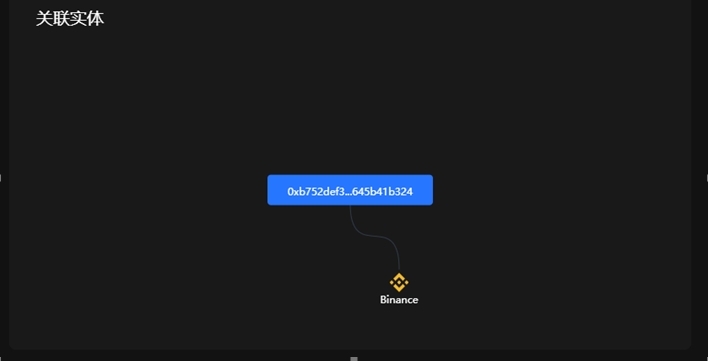
Image source: OKLink Chaintelligence Pro
The correct approach to this incident is to use the warning and tracking functions of OKLink or other technical service providers to wait for the subsequent fund movements of the settled addresses before taking further action. However, the best method is for the industry to unite and establish a response mechanism based on security incidents, which will better combat abnormal behaviors.
Warning for us
Security incidents such as reentrancy attacks will continue to occur. Therefore, in addition to the efforts we need to make on both the offensive and defensive ends, project parties need to have emergency plans to respond promptly to hacker attacks and minimize the losses for project parties and users. Contributors to Vyper also suggest that for public products like Vyper, we should strengthen public incentives and actively search for critical vulnerabilities. OKLink calls for the early establishment of a set of security response standards to make it easier to trace funds from black/gray addresses.
Just as OKLink’s product plays a role in preventing hackers and tracking funds in such incidents, project parties should consider the additional value that third-party technical service providers can bring when building the security module of their platforms, thus quickly and effectively fortifying the security of the project.
This article was also helpful by Raymond Lei and Mengxuan Ren from OKLink Blockchain.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Coinbase’s estimated revenue for the second quarter of 2023 non-transactional revenue surpasses its transactional revenue for the first time.
- Why is Starknet friendly to blockchain games it reduces redundant calculations, thereby reducing gas fees and increasing TPS (transactions per second).
- Bloomberg Analyst Probability of Spot BTC ETF Approval Soars from 1% to 65%
- Podcast Notes | Conversation with Polygon Co-founder From Matic to POL, the endgame of Polygon 2.0
- After Bald quickly became the leader of running away, can Base ecosystem recreate the Meme craze?
- Breaking the dilemma of poor user experience How does intent computing change Web3 interaction?
- Bald Runaway How a Low-Level Scam Deceives Everyone