CertiK Detailed Explanation of Vyper’s $52 Million Loss
CertiK's Detailed Explanation of Vyper's $52 Million LossA report has revealed that versions 0.2.15, 0.2.16, and 0.3.0 of Vyper have vulnerabilities, posing a risk of reentrancy attacks on many pools on Curve. This vulnerability allows attackers to call the add liquidity function during the removal of liquidity process.
Currently, a total of $69.3 million has been affected, of which $16.7 million has been recovered by white hat hackers. This means that $52 million has been stolen in this incident, making it the highest amount of funds stolen in a reentrancy attack so far in 2023.


- Don’t just focus on the RWA track, the oracle track is also worth paying attention to.
- Interpreting FTX’s preliminary restructuring plan Cash compensation is adopted, excluding FTT holders.
- LianGuai Morning Post | US Media Zhao Changpeng Once Attempted to Shut Down Binance’s Exchange in the United States
Summary of the Incident
On July 30, 2023, it was announced that versions 0.2.15, 0.2.16, and 0.3.0 of the Vyper compiler, a contract-oriented programming language designed for the Ethereum Virtual Machine (EVM), had a reentrancy lock failure vulnerability. Several DeFi projects were affected by this vulnerability, resulting in a total loss of $52 million.
CertiK has identified six addresses involved in this incident. The first one (0x172) failed to exploit the vulnerability in block 17806056. The initial exploiter of the vulnerability withdrew 0.1 ETH from Tornado Cash and continued to create attack contracts. However, a wallet (0x6Ec21) that was ahead paid more gas fees and executed the transaction first, obtaining approximately 6,100 WETH ($11.4 million).
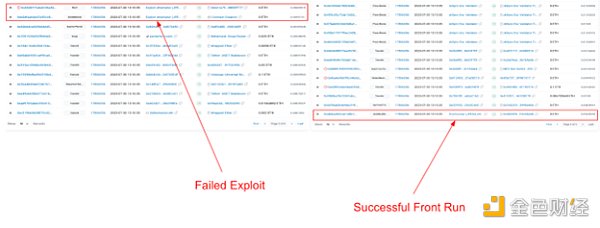
Source of the vulnerability that led to further losses: Etherscan
This vulnerability resulted in additional losses: EOA 0xDCe5d gained assets worth approximately $21 million. The details of the wallets involved are shown in the following figure:
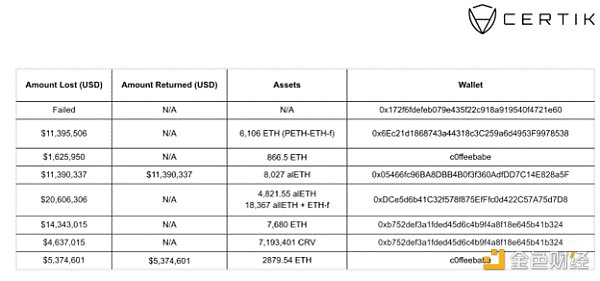
A total of six projects were affected, with approximately $69.3 million stolen, of which $16.7 million has been returned, resulting in a total loss of approximately $52 million.
What is Vyper
Vyper is a contract-oriented pythonic programming language for the Ethereum Virtual Machine (EVM). The testing version of Vyper has been around since 2017, but its first non-testing version was released in July 2020 as version 0.2.1.
Solidity is the mainstream language in the Ethereum ecosystem and has been around for much longer than Vyper. As a result, many community members have created tools specifically for Solidity. According to DeFiLlama, out of the total locked value (TVL) of approximately $70 billion in DeFi protocols, Vyper smart contracts account for $2.17 billion, while Solidity accounts for the majority, totaling $67.49 billion.
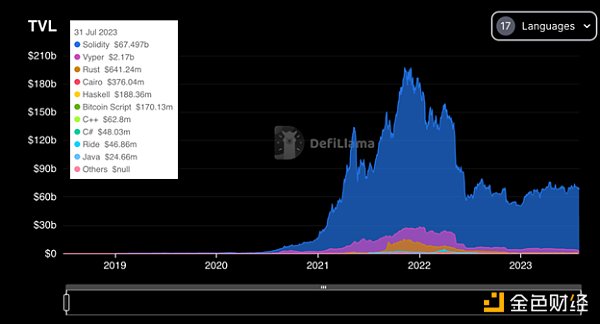
 Source of the total locked value by language: DeFiLlama
Source of the total locked value by language: DeFiLlama
As of May 10, 2023, Vyper’s dominance has dropped from its peak of 30% in August 2020 to 6.27%. Although Vyper’s TVL dominance is significantly lower than Solidity’s, this incident still resulted in $62 million being affected.
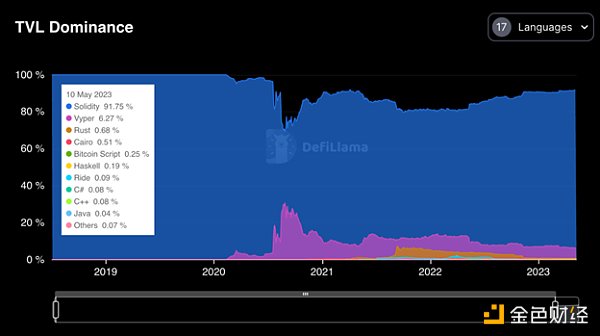
 Dominant Positions of Different Programming Languages in TVL Source: DeFiLlama
Dominant Positions of Different Programming Languages in TVL Source: DeFiLlama
Compiler Version
The compiler version refers to a specific version of a programming language compiler that converts human-readable source code into machine-readable code.
The compiler version is regularly updated to introduce features, fix bugs, and enhance security. Vyper currently does not offer a bug bounty program.
Versions 0.2.15 – 0.3.0
The vulnerabilities mentioned earlier were discovered in versions 0.2.15, 0.2.16, and 0.3.0 of Vyper, leading to reentrancy attacks on multiple DeFi projects.
The earliest vulnerable version of Vyper, version 0.2.15, was released on July 23, 2021. By the time version 0.3.1 was released in the same year, the previous vulnerabilities no longer existed.
Timeline
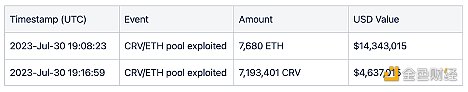
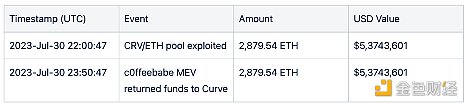
The event initially started at 9:10 PM Beijing time on July 30, when the attacker’s transaction against the JPEG’d pool on Curve failed due to front-running transactions.

At 10:00 PM Beijing time on July 30, it was confirmed that the pETH-ETH Curve pool had been maliciously exploited.
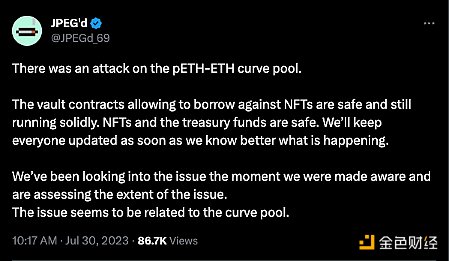
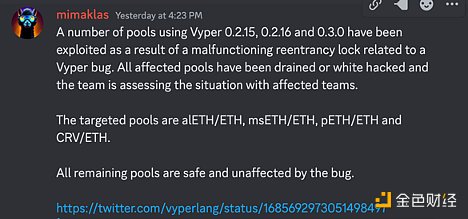
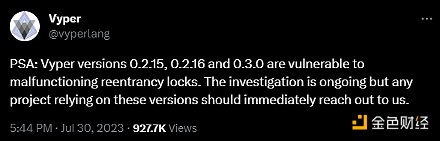
Subsequently, Vyper announced that versions 0.2.15, 0.2.16, and 0.3.0 included an ineffective reentrancy lock. After Vyper’s tweet, Metronome and Alchemix were also affected.
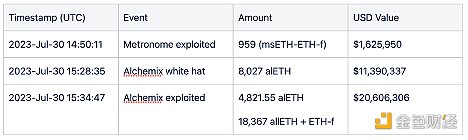
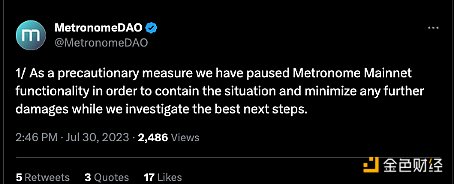
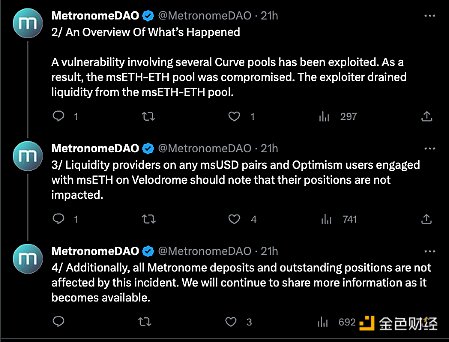
Metronome DAO announced the news:
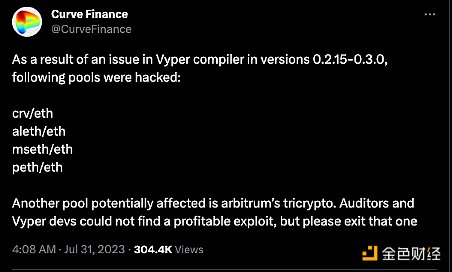
In the early morning of the next day Beijing time, Curve Finance announced on Discord that the remaining pools of funds were not affected by the Vyper bug and were safe.
Curve Finance announced on Twitter that a pool on Arbitrum may be affected, but there are no profitable vulnerabilities for malicious actors to exploit, meaning the pool is unlikely to be attacked. CertiK has also not detected any other attacks exploiting the Vyper vulnerability.
Attack Process
Here is an example transaction targeting JPEG’d:
Attacker: 0x6ec21d1868743a44318c3c259a6d4953f9978538
Attack contract: 0x466b85b49ec0c5c1eb402d5ea3c4b88864ea0f04#code
1. The attacker borrows 80,000 WETH (approximately $149,371,300) from Balancer:Vault
2. Then, the attacker swapped WETH for ETH and called pETH-ETH-f.add_liquidity(), adding 40,000 ETH (approximately $74,685,650) to the pETH-ETH-f pool. In return, the attacker received 32,431 pETH (pETH-ETH-f).
3. The attacker called remove_liquidity() to remove the liquidity added in Step 2. 3,740 pETH and 34,316 ETH were transferred to the attack contract, triggering the fallback() function of the attack contract and transferring control to the attacker. In the fallback() function, the attacker added liquidity of 40,000 ETH to the pETH-ETH-f pool and received 82,182 pETH.
4. The attacker called remove_liquidity() again, withdrawing 10,272 pETH and receiving 47,506 ETH and 1,184 pETH. Then, the attacker exchanged 4,924 pETH for 4,285 ETH in the pETH-ETH-f pool.
In total, the attacker obtained 34,316 ETH from Step 3 and 47,506 ETH and 4,285 ETH from Step 4, totaling 86,107 ETH. After repaying the 80,000 ETH flash loan, the attacker had 6,107 ETH left (approximately $11,395,506).
Vulnerability
This vulnerability allows attackers to call the add liquidity function during the process of removing liquidity. Although these functions should be protected by @nonreentrant(‘lock’), tests on the add_liquidity() and remove_liquidity() functions prove that it does not prevent reentrancy attacks.
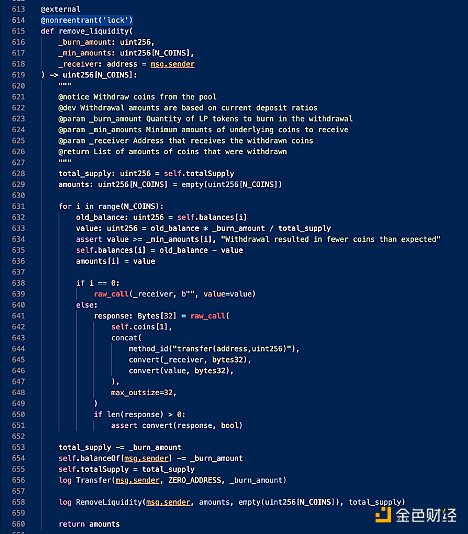
Vyper_contract for Curve.fi Factory Pool data source: Etherscan
Following the exploits of JPEG’d, Metronome, and Alchemix, versions v0.2.15, v0.2.16, and v0.3.0 of Vyper indeed have a vulnerability that fails to protect against reentrancy attacks.
Solution
Projects using vulnerable versions of Vyper should contact Vyper for assistance in mitigating the issue. Projects should also upgrade to the latest version of Vyper that does not have this vulnerability.
Summary
The Vyper attack incident is the largest reentrancy vulnerability detected by CertiK in 2023. In terms of financial losses, this attack accounts for 78.6% of such incidents.
The two largest reentrancy vulnerabilities this year were both in contracts written in Vyper, although the vulnerabilities were not the same.
Currently, the losses caused by reentrancy attacks in 2023 have exceeded $66 million. This is approximately $4 million more than the entire year of 2020 and only $1 million less than the losses in 2021. It is worth noting that the total for 2023 is also 259.45% higher than the losses caused by reentrancy attacks in 2022.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Messari Development Overview of Polygon in the Second Quarter of 2023
- What impact will the detailed analysis of the Curve attack incident bring?
- Are the 10 Web3 directions released by LianGuairadigm really the future of the industry?
- LD Capital An Analysis of KasLianGuai, a POW Public Chain Based on the GHOSTDAG Protocol
- How far can a decentralized sorter go?
- The Battle of Tech Giants Digital Identity, Payments, Social Graphs, AI, and Universal Basic Income
- Messari Overview of SandBox Development in Q2 2023