Is there a loophole in the Ethereum FAIRWIN smart contract? Detailed technical analysis is here
Recently, the issue of FAIRWIN smart contract has attracted the attention of all parties. FAIRWIN has been used as the most expensive mode of the Ethereum chain in recent days. There are still a lot of similar clone disks in the Ethereum chain. If there are hidden vulnerabilities, The public chain brings a large wind direction, so the Chengdu chain security personnel conducted an in-depth analysis of the FAIRWIN smart contract. The analysis results are as follows:
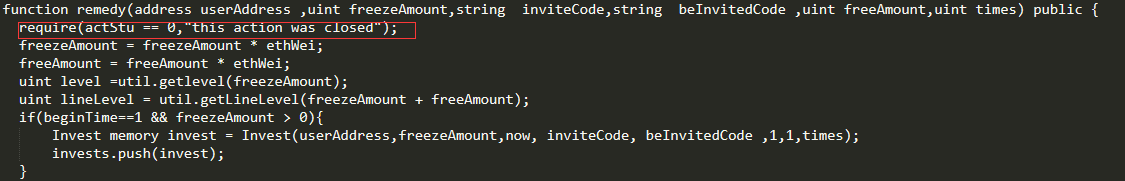
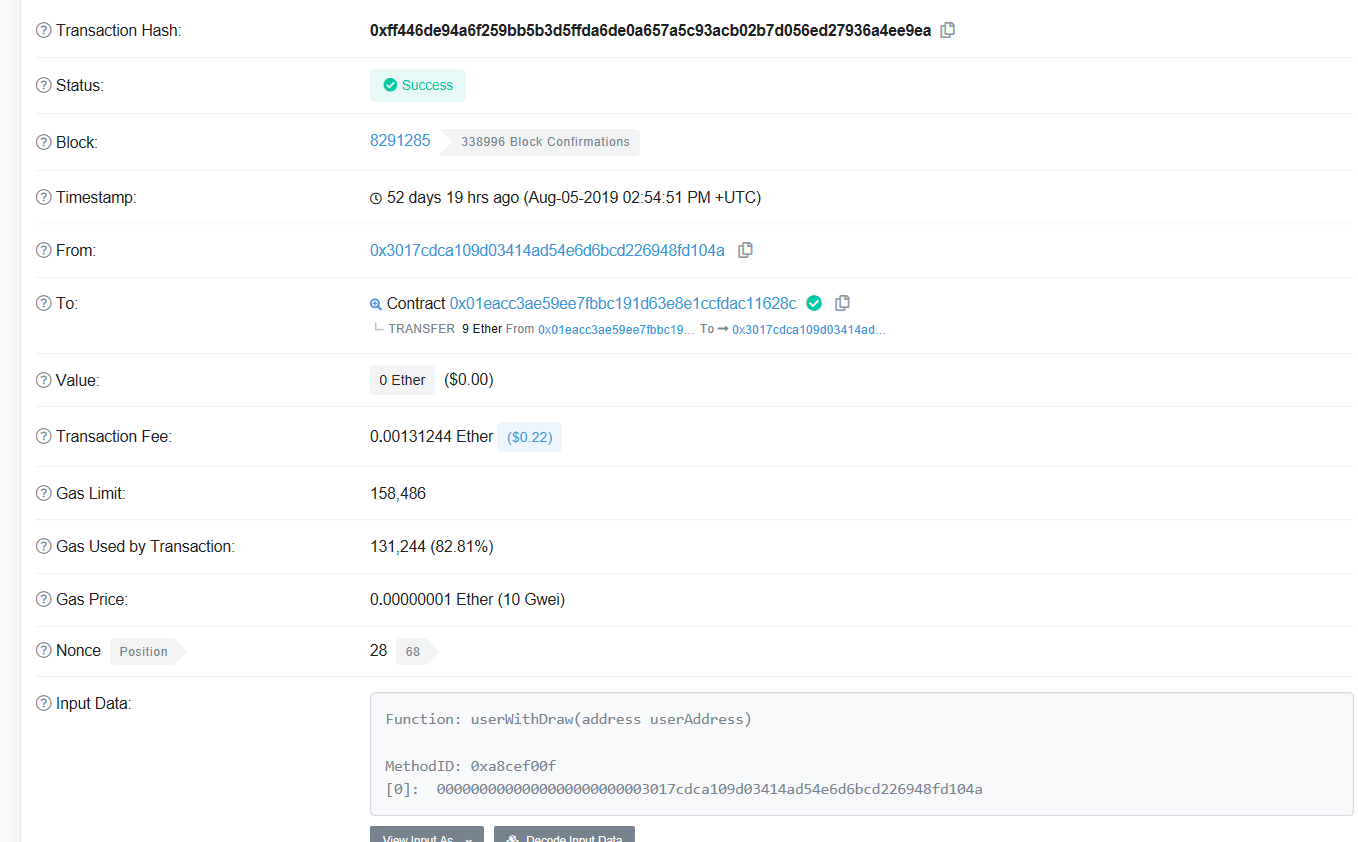
By auditing the FAIRWIN contract code, we found that there is a remedy() interface in the contract. If the contract owner does not close the interface through close(), the interface can be called by any user, and the bet data can be forged through this interface. If you don't use any funds, you can fake the recharge record, and then the attacker can enjoy the dividend, or use the UserWithDraw() to submit the balance.
- Decentralized "short" agreement dYdX's hope and hope
- Ant Block Chain Yunqi Conference: 2020 to use the blockchain to serve 100 million Chinese
- We have forgotten that Bitcoin does not yet have a globally recognized story.
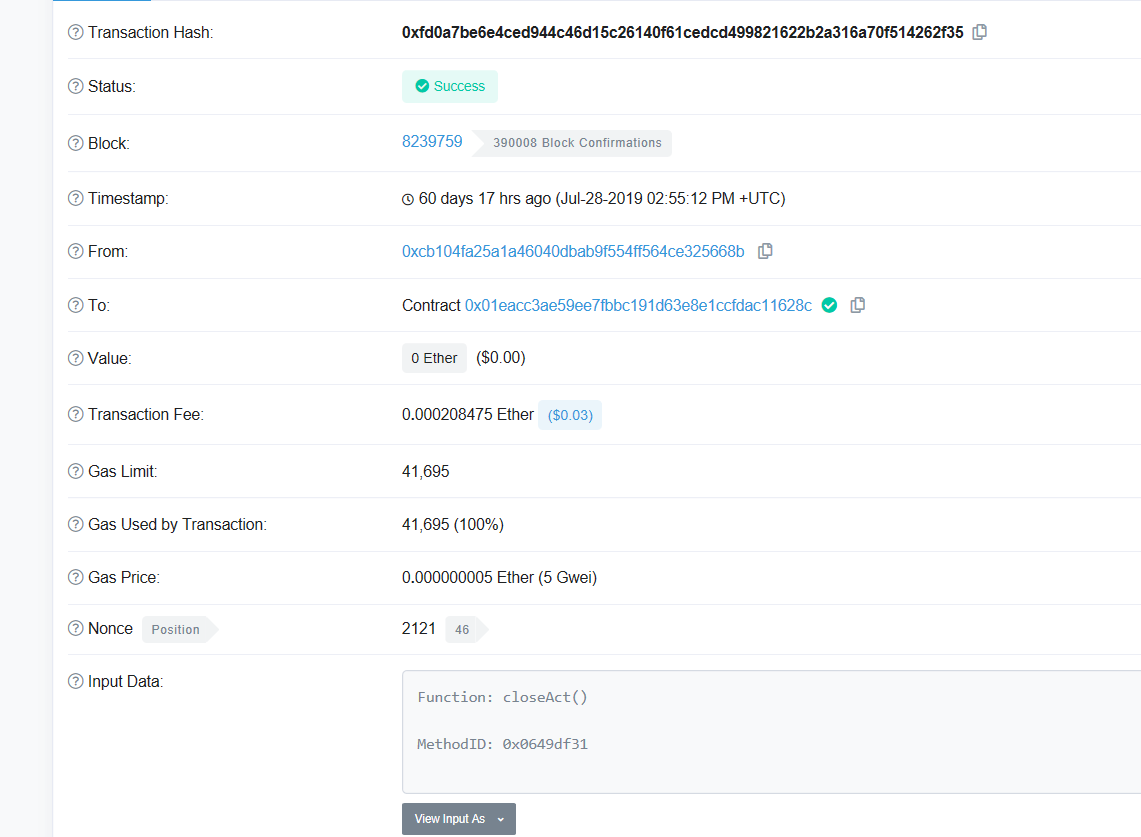
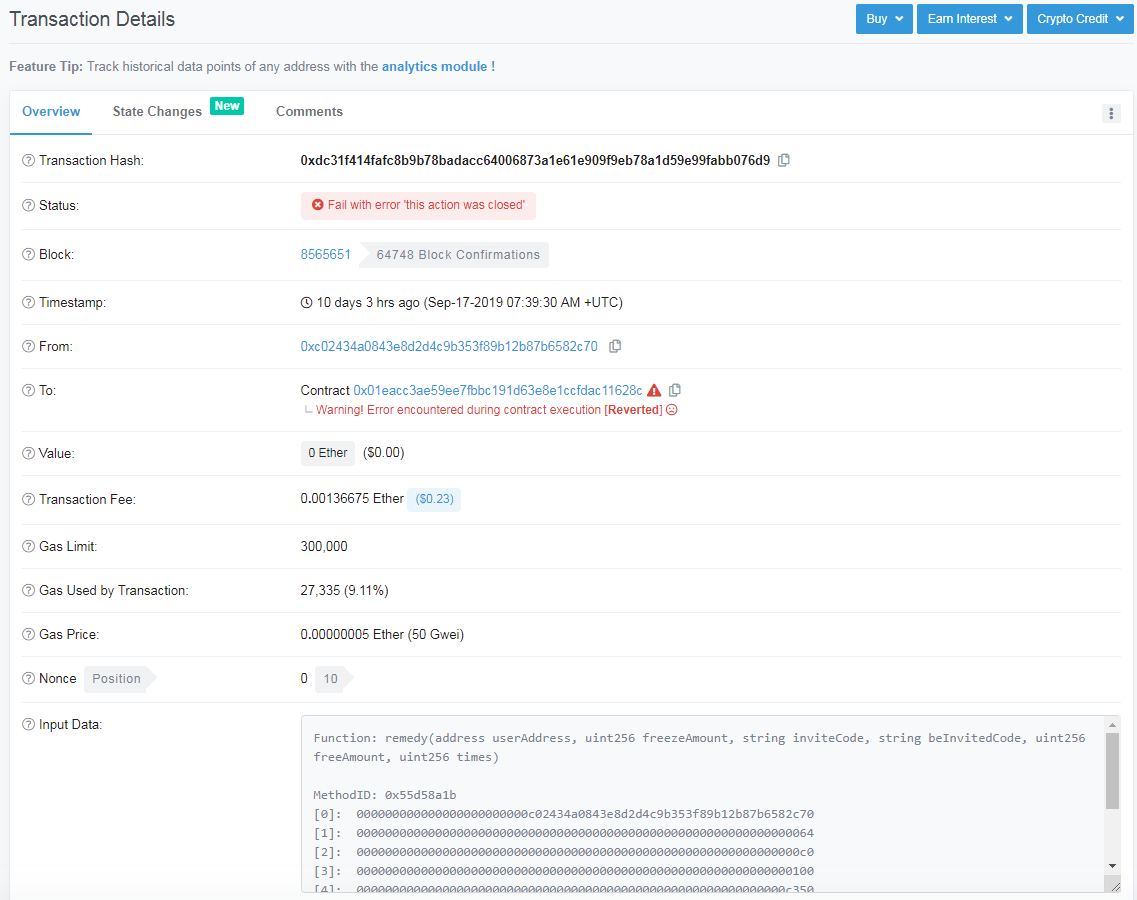
Through the chain record, we found that the project side closed the interface by closeAct() on July 28, 2019 (the second day of the contract). Through the Chengdu Chain An-Beosin-AML system to analyze all the transaction records of the project side, we further analyze whether there is already a successful attacker inserting the bet data. The analysis found that the vulnerability has been seriously abused. From ten days ago until now, there have been accounts trying to call the remedy () interface to insert bet data, but since the operation has been closed, the insertion of data failed, you can see that the insertion amount is tens of thousands of ETH.
Insert failure record:

Through the full trace, we found a total of 503 successful transaction records (500 addresses), and the insertion date is before the project side closes the interface. According to statistics, all 503 transactions were initiated by the address 0xcb104fA25a1a46040DBaB9F554FF564CE325668b.
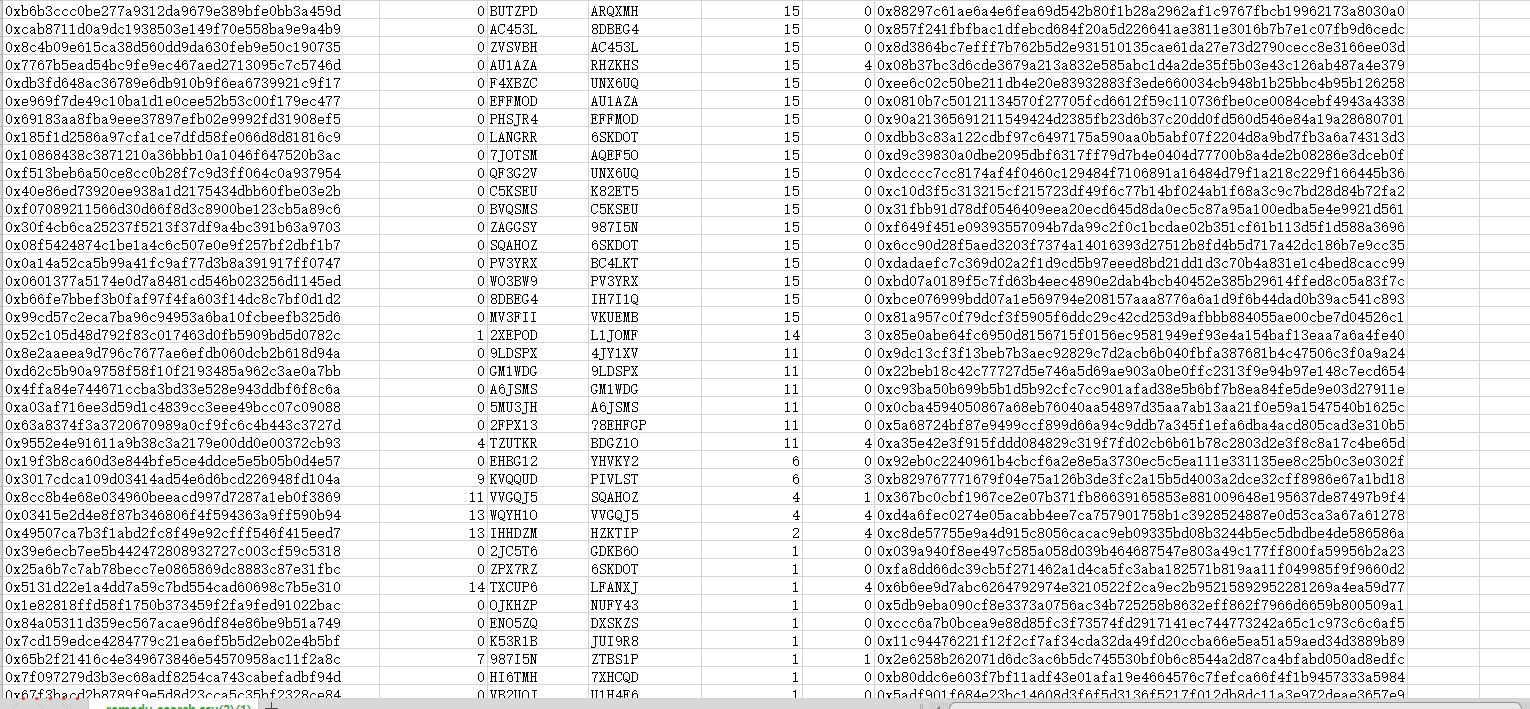
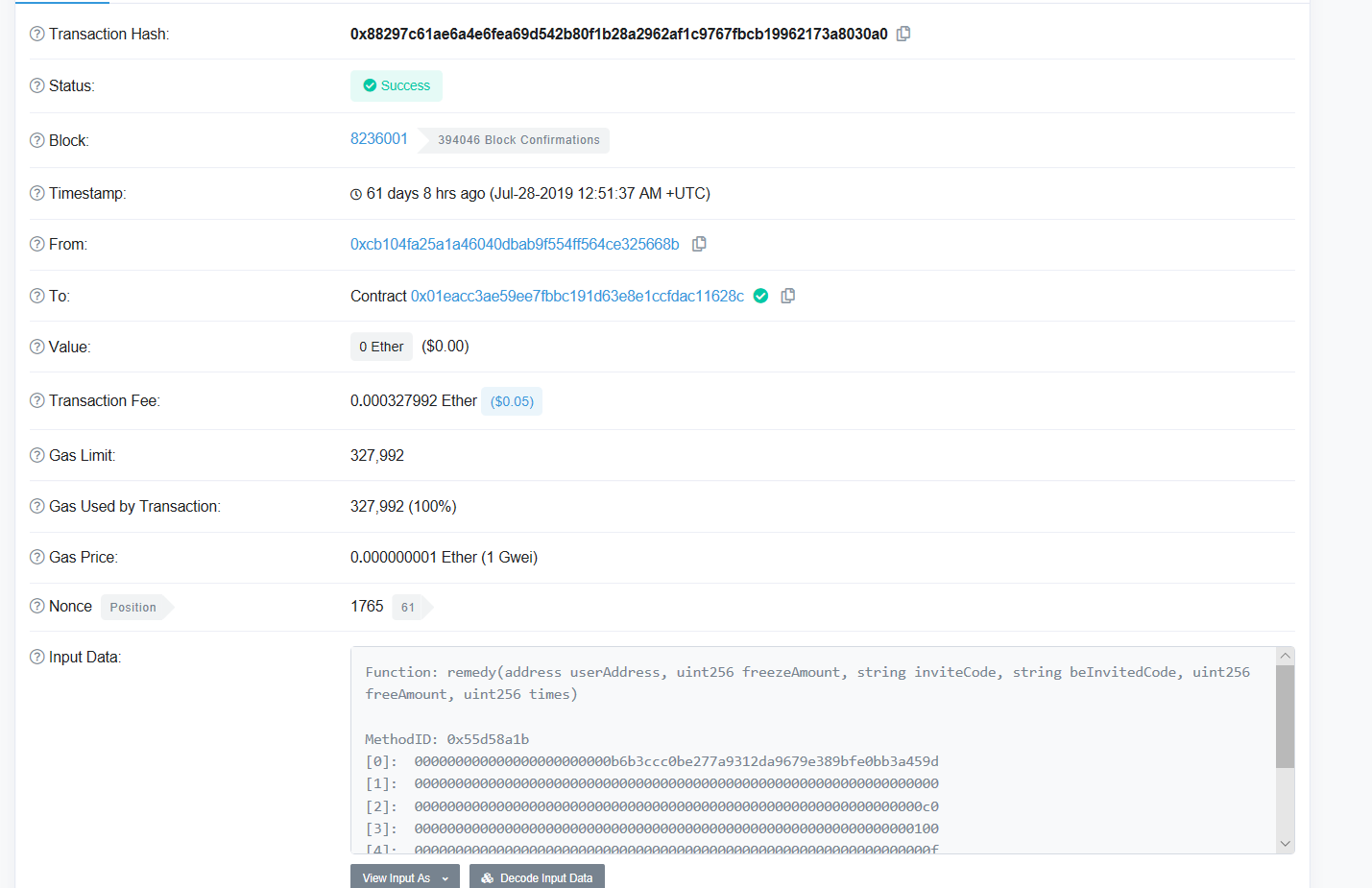
A total of 5093 ETHs were inserted by statistics, including 4711 frozen ETHs and 382 unfrozen ETHs. And the attacker has already performed the cash withdrawal operation by inserting more than 500 trumpet settings set by the bet record.
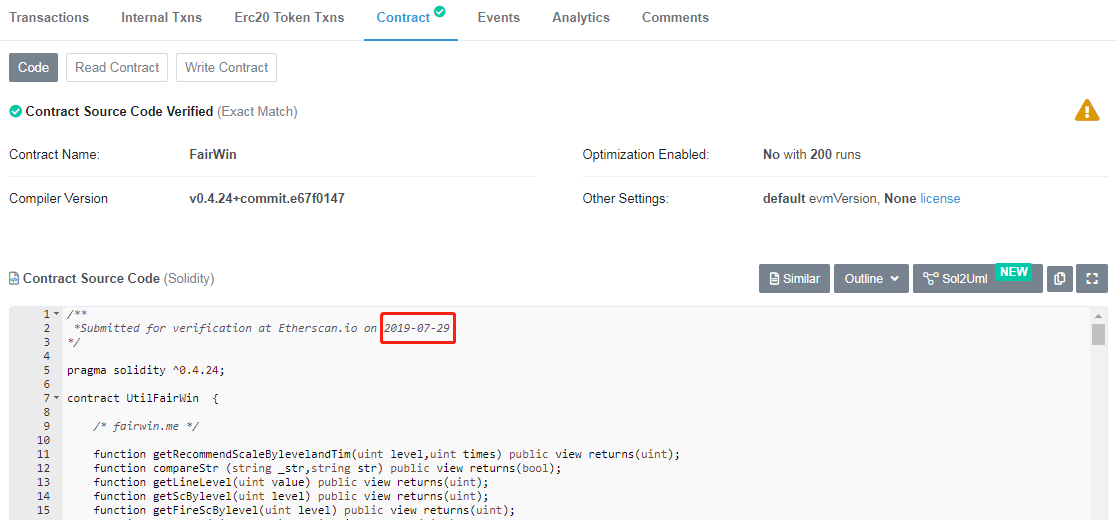
By further analyzing the contract deployment situation, it was found that the day before the project party closed actStu, that is, on July 27, 2019, the project party had just deployed the FAIRWIN contract. Within a short period of time, the project contract was out of nothing. More than 5,000 ETHs. On July 29th, the Ethereum browser display contract was open source.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ling listening to the notice | What is the bottom of the ant Jinfu layout blockchain?
- Will Libra become the “UN coin”? Libra Association: We can help the UN achieve many sustainable development goals
- 13 countries, the United States, China and other 13 countries cryptocurrency supervision pattern
- The market is diving again, but the short-selling power is attenuating
- The life-saving grass of cryptocurrency, the big country dream of Turkey
- Ethereum 2.0 shard development is basically completed, the first shard simulation will be demonstrated at the next developer conference
- Platform-as-a-service company StrongSalt receives $3 million in financing, and will soon release an encrypted API platform