Science | An article to understand the innovation in the Bitcoin technology stack over the years
Author: Lucas Nuzzi
Compilation: Bitcoin Xiaobai
Bitcoin has come a long way in the past decade. Compared to the first iteration of its software, the quality and reliability of the current implementation has been significantly improved. Quickly, Bitcoin can attract a large number of developers to invest thousands of hours to improve its underlying code base, sometimes even making improvements and providing some suggestions.
Despite this, Bitcoin remains the same. Just like the Constitution, the core consensus rule set that defines its monetary attributes (such as algorithmic inflation and hard-coded supply) remains unchanged. The villains have repeatedly tried to change these core attributes, but so far all hostile takeovers have failed. This is usually a painful process, but it highlights and consolidates two of the biggest advantages of Bitcoin:
- Babbitt live 丨 Zhang Laiwu: In the era of digital economy, digital currency and the sixth industry are the main battlefields of blockchain applications
- Babbitt live | I heard these "different" views at a conference attended by more than 100 blockchain investors
- Kelly Loeffler steps down from Senate seat, Bakkt welcomes new CEO
1. No one can decide how Bitcoin will evolve
2. Lack of centralized control can protect Bitcoin's monetary attributes
Interestingly, these rules have attracted cryptocurrency and institutional investors. These rules have made Bitcoin an unprecedented currency. However, these rules also make developing software on Bitcoin more challenging than any other digital asset. Essentially, Bitcoin's constitution grants developers a limited toolkit so that they don't violate their monetary policy. The risk of moving fast and destroying things is too great.
This means that Bitcoin innovation requires creativity, patience, and perhaps most importantly, self-minimization. After all, the basic rules embedded in the Bitcoin Constitution will eventually replace technology. That's why Silicon Valley has a hard time understanding Bitcoin's value proposition, not just technology, financial instruments or consumer applications. This is the entire monetary system supported by technology. Changing Bitcoin's constitution requires quasi-political procedures that may violate its monetary attributes, so technological innovation is implemented as a module.
As often pointed out, Bitcoin's innovative modular approach is similar to the development of Internet protocols, where layers of different protocols are dedicated to specific functions. E-mail is handled by SMTP, files are handled by FTP, web pages are handled by HTTP, user addresses are handled by IP, and data packet routing is handled by TCP. The 7-layer model of network protocols has allowed the Internet to develop for many years. These protocols have been continuously improved in development and can provide you with more convenient functions.
In an excellent article on the emerging Bitcoin technology stack in the Spencer Bogart series, he proves that we are now witnessing the beginning of Bitcoin's own protocol components. It turns out that the inflexibility of Bitcoin's core layer has led to the creation of several additional protocols specifically for various applications, such as the Lightning (Lightning Network) payment channel BOLT standard. Innovation is both dynamic and (relatively) secure because this modular approach minimizes systemic currency risks.
Too much has happened at many levels of the Bitcoin technology stack, and it is very difficult to track emerging solutions. The figure below is an attempt to draw all relatively new plans and show a more complete evolution of the Bitcoin technology stack. It is not exhaustive, nor does it endorse any particular initiative. However, it is impressive that innovation is being driven in all areas. Including but not limited to the current mainstream Layer 2 technology, Smart Contracts (smart contract) solutions, etc.
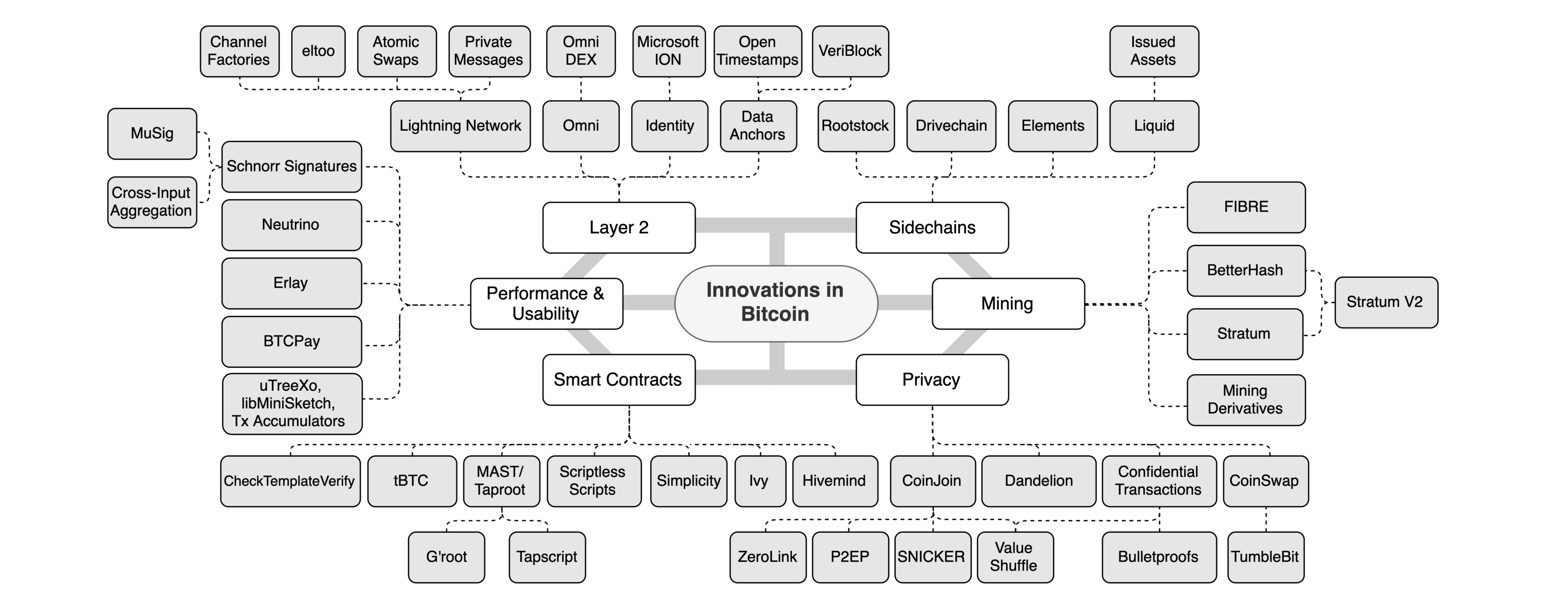
Layer 2
- There has been a lot of discussion about Lightning Network adoption recently. Bitcoin's most outstanding Layer 2 technology. Critics often point to a significant reduction in the number of channels and total BTC locked into Lightning. Two metrics often used to evaluate user adoption. Although the community has reached consensus on such indicators, it must be noted that, given the way Lightning works behind the scenes, they are fundamentally flawed.
- One of the most underrated advantages of Lightning Network is its direct privacy properties. Since Lightning does not rely on global verification of all state changes (ie its own blockchain), users can use other technologies and network overlays (such as Tor) to conduct transactions privately. At this point, we can estimate the private use percentage of the Lightning Network by analyzing the number of open transactions on the chain and comparing it with the number of public channels off the chain. Christian Decker estimates that 41% of Lightning Channels are private:
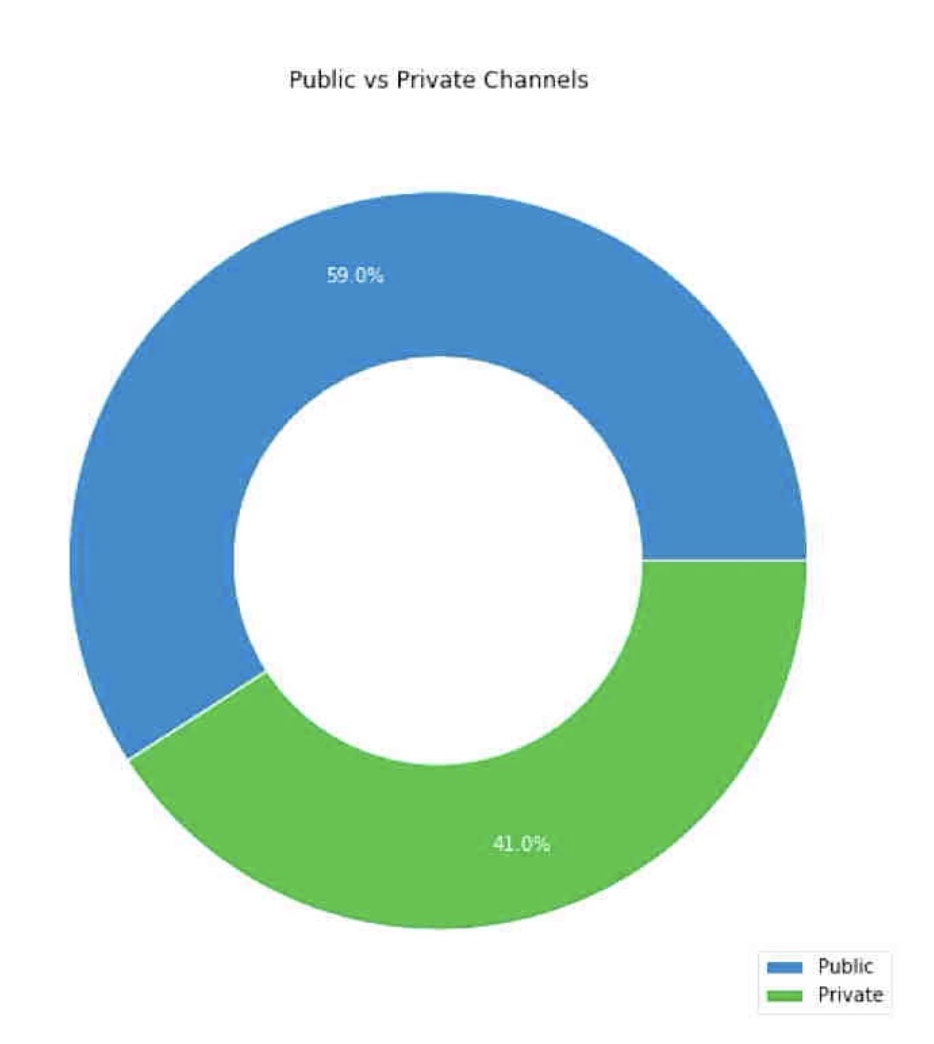
Source: Christian Decker
- Events that occur in these channels have not been captured by the popular Lightning Explorer. As a result, the increased use of Lightning by private individuals has led to a decrease in publicly measurable content, leading observers to falsely conclude that adoption has declined. It is true that the Lightning Network must overcome substantial availability barriers before it can be widely adopted, but we must stop using misleading indicators to assert the current state of the network. As Decker pointed out in his speech at the recent Berlin Lightning Conference, even the above estimates of private and public channels are flawed because the adoption of Schnorr signatures will make channel open transactions indistinguishable from regular transactions.
- Another interesting recent development in Layer 2 privacy is the creation of WhatSat, a dedicated messaging system on top of Lightning. The project is a modification of the Lightning Demon that allows the relay of private messages (messengers connected to the communication entity) to compensate for their services through small payments. LND's own innovations, such as the latest improvements to Lightning-onion (Lightning's own Tor routing protocol), implement this decentralized, anti-censorship and anti-spam chat security system.
- The growth of Lapps or Lightning applications attests to the widespread use of these innovations in consumer applications, from Lightning-based cloud computing VPS to image hosting services that share advertising revenue through microtransactions. That's just the Layer 2 innovation in Lightning. More generally, we define Layer 2 as a series of applications that use Bitcoin's base layer as a leader to coordinate external events and resolve disputes. Therefore, there will be more and more Lapps anchoring data on the Bitcoin blockchain. For example, giant companies such as Microsoft took the lead in developing a decentralized ID system on top of Bitcoin. These measures have increased the demand for chain reconciliation and contributed to the long-term development of the bitcoin charging market.
Smart Contracts
- There are also many projects that attempt to bring expressive smart contract functionality back to Bitcoin in a secure and responsible manner. This is a major advance, as some original bitcoin opcodes (determining what Bitcoin can calculate) have been removed from the agreement since 2010. Prior to this, a series of terrible mistakes caused Satoshi Nakamoto to disable certain features of the Bitcoin programming language script.
- For many years, it is very clear that highly expressive smart contract functions are actually accompanied by considerable security risks. A general rule of thumb is that the more features you introduce to a virtual machine (a collective verification mechanism that handles opcodes), the greater the uncertainty of its program, after all, there is no flawless code. However, recently we saw a new approach to the smart contract architecture in Bitcoin that minimizes unpredictability while also providing a wide range of features.
- The design of a new method for Bitcoin smart contracts called Merkleized Abstract Syntax Trees (MAST) has sparked a new wave of support technologies that try to optimize the trade-off between security and functionality. The most significant is Taproot, which is an elegant implementation of the MAST structure, enabling the entire application to be represented as a Merkle Tree, where each branch of the tree represents a different execution result. Along with Taproot is a programming language called Tapscript, which can be used to more easily express the spending conditions associated with each branch of a Merkle tree.
- Another interesting innovation that has recently surfaced is a new architecture for implementing contract or spending conditions in Bitcoin transactions. The idea was originally a thought experiment proposed by Greg Maxwell in 2013 as a way to limit the way of balance, even if its guardianship changes. Although this idea has been around for almost 7 years, it was impractical to implement the covenant before Taproot. Now, a new opcode called OP_CHECKTEMPLATEVERIFY (formerly OP_SECURETHEBAG) is leveraging this new technology to potentially enable the secure implementation of smart contracts in Bitcoin.
- At first glance, smart contracts are very useful in the context of lending (or bitcoin-based derivatives) because they enable the creation of policies such as rebates to be attached to a specific BTC balance. But their potential impact on Bitcoin's availability goes far beyond borrowing. Smart contracts can implement things such as Bitcoin vaults. In the case of escrow, the second private key provided by the vault is equivalent to allowing a hacked party to "freeze" stolen funds. There are many other applications of this technology, such as non-interactive payment channels, congestion control transactions, CoinJoins, and it really deserves a separate feature. For more information, check out Jeremy Rubin's draft BIP.
- On the other hand, it should be noted that Schnorr signature is the underlying technology that makes all these new smart contract methods possible. After Schnorr is activated, it can even theoretically process some more advanced technologies, such as Scriptless Scripts, which can make a fully private and scalable Bitcoin smart contract be represented as a digital signature (as opposed to an opcode) ). Similarly, Discreet Log Contracts also adopted the idea of representing the execution results of smart contracts as digital signatures to achieve better privacy and scalability. Taken together, these new approaches enable novel smart contract applications to be built on top of Bitcoin, with Schnorr as the foundation.
Bitcoin mining
- There are also some interesting developments in Bitcoin mining protocols, especially those used by mining pool members. Even though the problem of centralization in Bitcoin mining is often exaggerated, it is true that the power structure reserved by the mining pool operators can be further decentralized. That is, the pool operator can decide which transactions will be performed by all pool members, thus giving them considerable power. Over time, some operators have abused this ability to inspect transactions without the trader's authorization, mine empty blocks and redistribute hashed output to other networks.
- Thankfully, some technologies are trying to disrupt this power structure. One of the most significant changes in Bitcoin mining is the second version of Stratum, the most widely used protocol in the mining pool. Stratum V2 is a complete overhaul that implements BetterHash (an auxiliary protocol) that enables mining pool components to determine the composition of the blocks they will be mining, not the other way around. Stratum V2 also implements some optimizations and allows the mining pool elements to better communicate and coordinate.
- Another interesting development in the mining pool industry that helps improve stability is renewed interest in hash rate and difficulty derivatives. These are especially useful for hedging transactions that want to hedge against fluctuations in the hash rate and difficulty adjustments. Although these derivatives have not yet been produced, this marks an interesting development in the industrialization of the Bitcoin mining industry.
privacy
- After we published a report on Schnorr signatures, some advocates of privacy tokens were outraged at the suggestion that sufficient privacy rights should be achieved in Bitcoin at some point. Although this proposal may challenge these views around the long-term value proposition of privacy assets, there are still many emerging protocols that can bring better privacy to Bitcoin. Although privacy in Bitcoin may continue to be an art rather than a science, there are some interesting innovations worth mentioning in this regard.
- Before we study specific privacy innovations, it is important to emphasize that the biggest obstacle to private transactions across digital assets is the fact that most solutions are immature. Focusing on the privacy of transaction methods usually ignores network-level privacy and vice versa. Both vectors lack maturity and utilization, which makes it easier to anonymize transactions through statistical traceability analysis at the P2P network layer or blockchain layer.
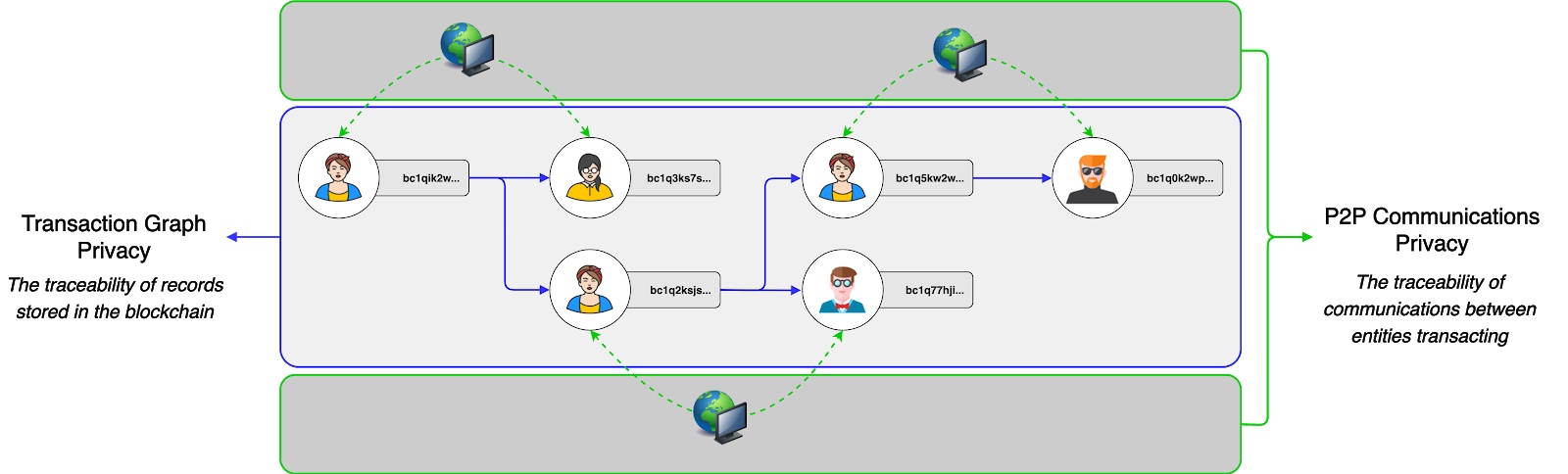
- Thankfully, several projects have put forward new requirements in both areas.
- When it comes to transaction privacy, solutions like P2EP and CheckTemplateVerify are interesting because privacy has become a by-product of efficiency. As a novel method of CoinJoin, these solutions can increase user adoption of private transactions, which is driven entirely by lower transaction fees. Although the privacy guarantee is still not the best option under the CoinJoin model, unblocked sending amounts can still benefit because they retain the auditability of Bitcoin supply and free circulation.
- If lower transaction fees become an incentive and lead to an increase in the anonymous set of Bitcoins (the percentage of UTXO output by CoinJoin), then anonymization through statistical clustering analysis will be more optimistic than it is now. Some blockchain analysis companies have been able to deceive law enforcement agencies and convince them that it is highly likely that UTXO belongs to a specific user, but the underlying model is already very subtle and fragile. If most UTXO becomes CoinJoin output, it may break existing clustering methods.
- Before that, a lot of work needs to be done in terms of usability so that all Bitcoin users, regardless of technology savvy, can use the privacy mechanism equally. In addition to P2EP and CheckTemplateVerify, the latest development in usability is the proposal of SNICKER (Simple Non-Interactive CoinJoin Reuse with Reuse Key), a novel way to generate CoinJoins with untrusted peers. SNICKER combines multiple technologies to grant users access to CoinJoin transactions without having to trust or interact with their peers.
- Progress is also evident in protocols designed to improve the privacy and efficiency of P2P communications. During 2019, the privacy protection network protocol Dandelion has been successfully tested on multiple encrypted networks. Even in terms of overall P2P communication, privacy in transaction propagation is not a panacea, but protocols like Dandelion can still meaningfully improve user privacy by hiding the original IP addresses of the nodes broadcasting the transaction.
- It is worth mentioning that the ultimate development of the Bitcoin network stack is a new transaction relay protocol called Erlay. Although Erlay is still in the early stages of development, it is an important innovation because it can greatly reduce the bandwidth requirements for running a Bitcoin full node. If implemented, Erlay's increased efficiency will enable users to participate in bandwidth-intensive transaction relays and continue to verify the chain, especially in countries where Internet service providers have capped bandwidth.
to sum up
The above technologies are just the tip of the iceberg in the iteration of Bitcoin technology. It is very difficult to track all the innovations that have occurred in Bitcoin, and this article is only a small part of the surface. This brings us to the main content of this article: Overall, Bitcoin is a set of evolving protocol components. The development of Bitcoin, like the Federal Reserve, is slowly improving the entire system without being affected by the outside world, and has developed into a clear stream in the digital currency world.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Regarding the Ethereum Istanbul hard fork, we need to understand these (with user guide)
- Holding money or using DeFi to manage money, who is more profitable?
- Babbitt site 丨 Li Lin: Upgrade Huobi Cloud to provide digital financial solutions based on blockchain digital currency issuance and payment
- Bitcoin Mining 60 Days Visit: Recording the Mysterious Nugget Paradise
- The funds were cheated under the name of the public chain. Where is the way out for the public chain?
- Securities Daily: Multi-regional efforts to promote blockchain technology innovation industry layout have their own focuses
- How long do analysts look at the market outlook?





