Science | ConsenSys: Privacy Technology on Ethereum
Author: Dean Pierce (ConsenSys best of tune), Robert Drost (ConsenSys R & D), and Mason Nystrom (ConsenSys)
Translation & Proofreading: Zeng Wei & A Jian
Source: Ethereum fans
Editor's Note: The original title is "Popular Science | Privacy Protection Technology on Ethereum"
- Babbitt Column | Blockchain Essence: Performance Essence
- Dry Goods | Blockchain Economics: A Guide to Institutional Cryptography
- The MakerDAO rate has dropped to the lowest level in half a year. How to arbitrage from it?
In this increasingly connected world, the frequency with which our information is recorded, copied, disseminated, and sold is increasing, and it is not easy to maintain our expected level of privacy.
Most things are not black and white, and privacy is no exception. It is between full disclosure and full privacy. Therefore, when we talk about privacy, we must first understand the following three issues.
-
What privacy do users and businesses want to keep? -
Are people willing to pay for privacy? -
What do we need to weigh in to achieve a private transaction on the public chain?
The purpose of this paper is to briefly study the actual privacy requirements of the public chain and to explore the trade-offs of implementing privacy solutions at an abstract level.
Question 1: What is the importance of privacy?
Businesses often have strong business needs or compliance requirements for privacy. In contrast, users have always lacked privacy concerns and protection awareness. Still, users still want to protect their identity, credit card information and other sensitive data in case they are stolen or scammed. Sometimes, users want to be able to trade anonymously, which requires both parties to have privacy protection. Unfortunately, privacy is not a natural occurrence in our daily lives. Most people are willing to sacrifice their privacy in exchange for convenience or free benefits (such as accepting cookies, using free WiFi, tracking Internet records, etc.) ).
Question 2: Is privacy a pseudo-demand?
The privacy we often say in the context of communication refers to protecting the content sent between participants. In addition, privacy has been used in the wider architecture of communication channels and infrastructure layers. We can see this configuration from the evolution of public key cryptography to other secure key/transport layer protocols (IPSec v2, SSL) used in the key exchange mechanism to generate end-to-end. In addition, the existence of such constructs allows us to safely use DNS queries as well as Tor-based repeaters. There has been a lot of work in academic research from the field of general standards, and the results have been used by companies to maintain privacy and confidentiality in data transmission – but many of these technologies have been found in the retail user technology stack. The application scenario of its own – thus benefiting end users.
Let's focus on the blockchain field – although Zcash has been around for almost three years, only 5% of the existing ZECs are stored using SNARK technology (and nearly half of them are using older versions of SNARK technology). ). Approximately 95% of ZECs are stored in transparent addresses with no privacy. Through this phenomenon, we can infer that perhaps most users are not aware of the need to pay for privacy.
However, to promote the massive spread of blockchain technology, privacy is indispensable. The success of many built-in privacy layers (such as SSL) dedicated to making the Internet a trusted business medium suggests that users and businesses want to be able to natively build privacy into systems and applications.
Question 3: Privacy trade-offs
Question 3 is more technical and requires more in-depth research on how to balance privacy and the various mechanisms involved in Ethereum. Just as blockchain networks need to make trade-offs between scalability and decentralization, privacy mechanisms and technology itself also need to be weighed. Let's first examine the privacy practices that have been implemented in other privacy-conscious blockchains, and then discuss some privacy solutions on Ethereum.
Lessons from other major privacy blockchains (Monero and Zcash)
Before diving into Ethereum, let's take a look at two heavyweight players in the privacy coin world – Monero and Zcash. In the early Ark era, Monero was a bit different because its code base was not based on Bitcoin, but on Bytecoin (which is a reference design for the CryptoNote protocol) – a project that was completely unrelated to Bitcoin. The original CryptoNote design was to mix the sender's signature with other lure signatures. By combining this technology with covert address output, you can provide great privacy protection. The “ring signature” design was famous for its early built-in mixer, and the residual sound remained.
In 2017, with the introduction of RingCT, the ability of ring signatures to hide transaction data was dramatically improved, and RingCT used a zero-knowledge proof to enrich the types of signatures that could be batched simultaneously. At the same time, the introduction of RingCT enforced the minimum blending requirements, which alleviated the linkability attack that plagued the early version of Monero. However, gold is not a perfect solution, and ring signature is not the perfect solution. One of its main problems is that it takes up a lot of disk space to store the Monero blockchain. In addition, ring signatures cannot be extended to large groups, and the current number of participants per group is limited to 10-15.
At the end of 2018, we saw the introduction of “Bulletproofs” on the Monero blockchain – an exciting new zero-knowledge structure that allows the number of signatures in the ring to be logarithmically expanded, thus reducing the exchange The storage that needs to be occupied. This improvement has allowed Monero to catch up with other blockchain projects.
Speaking of zero knowledge, Zcash is the first project to eat crabs. It is the first to adopt zkSNARK technology. Using this technology, users can send pure private transactions that are visible only to the recipient. For an external observer, the ZEC sent to the private address appears to disappear into a huge cryptographic black box when the recipient wants to transfer their ZEC back to a non-private address (and the standard bitcoin address is almost When exactly the same, the originally disappearing ZEC seems to appear out of thin air, and the observer never sees the connection between the sender and the receiver. But one thing to mention is that zero-knowledge proofs require more computing resources, which in turn makes the transaction more expensive.
Threat to "Fungibility"
The transaction on the Ethereum network has pseudo anonymity (ie, the address of the transaction is associated with the public key corresponding to the private key held by the user, not the username/password), at the same time, thanks to its distributed And the characteristics of transparency, many new technologies have been able to show their talents.
However, similar to Bitcoin, when using such techniques, such as transfer homogeneity (Fungibility, also known as "interchangeability", ECR-20 tokens and ETH can be considered homogeneous assets) digital assets In operation, if the user has no knowledge of the breadth of information shared by them, their identity may be exposed to Ethereum without knowing it. The exposure of the real identity corresponding to the public and private keys can seriously threaten privacy. Considering the openness of blockchains such as Bitcoin and Ethereum, when you naively trade with their native trading framework, the traces of all assets are easily traced like breadcrumbs – even if Homogeneous assets.
Privacy protection address generation Dafa
As privacy technologies continue to evolve, many more sophisticated threat models are being considered. In 2012, BIP32 introduced Hierarchical Deterministic keys, which allowed us to generate a myriad of “new” bitcoin addresses using a set of mnemonics. This means that users can generate a new address each time they receive a payment, and all of these addresses can be easily imported and exported between wallets. You no longer have to take a small copy of the randomly generated random records. The key is up, does it sound like a thief?
Ethereum also has the same function, although the newly generated address has to interact with the smart contract, you need to ensure that the Ethereum in the address is enough to pay the Gas fee. However, since many systems built on Ethereum associate users' real-world identities with their addresses in many ways, the problem becomes complicated. The extra large amount of metadata associated with the Ethereum address will make it easy to get anonymized attacks. Fortunately, while some smart contract features expose Ethereum to such threats, smart contracts can also be used by cutting-edge cryptography systems to provide users with secure and seamless privacy transactions.
Zero knowledge plan and trusted initial setup (Trusted Setup)
Many zero-knowledge scenarios require a "trusted initial setup." This means that the whole solution relies on the generation of special random numbers, and anyone who knows these random numbers can understand the internal operations and sounds like a very unreliable sample of paper… in order to partially alleviate this aspect. Worried, a complex random number generation process came into being to ensure the credibility of the structure. This process usually requires several honest community members to independently generate their own private random data, and then combine the data in some way. As long as any one of the members deletes the random data of the TA, the final calculated data is safe. of. Therefore, unless all participants collude, the relevant programs will not be at risk.
It should be noted that the bullet proof used by Monero does not require trusted settings, but the zkSNARK applied in Zcash is required. You can view Zcash's trusted setup process documentation in the current famous RadioLab article. Instead, STARK does not require any trusted settings, they use the choice of hash functions as their "set" instead of any special numbers. Various forms of trusted setup processes have been proposed, such as the Persistent Powers of Tau multiparty computing process.
Zero Knowledge Notes (ZK-Notes)
As a pioneer in the privacy of Ethereum, the AZTEC protocol uses a “zero knowledge ticket” system to track hidden assets. These notes (including the owner of the ticket) are posted on the Ethereum network, but unless you are the owner of the ticket, you are not aware of the amount in each ticket.
When the owner of the ticket decides to perform the "joinSplit" operation, zero knowledge begins to exert its magic – the owner of the ticket can select any number of tickets it controls and create a set of outputs that do not necessarily belong to others. bill. This, combined with the covert address technology mentioned above, allows each new ticket created to be attributed to a completely new Ethereum address (an address that has never been used on the Ethereum network).
Let's look at a common usage scenario. A “zero-knowledge asset” contract can be linked to any ERM20-compatible token. Users can deposit tokens into this contract and get a zero-knowledge ticket as proof of deposit. To get back the deposit, simply "burn" the zero-knowledge ticket. With this mechanism, we can trade any assets that exist on the Ethereum network in a covert way. The proof used by the AZTEC protocol is easier to use than ZK-Snark, but the trusted start-up facility is still a hurdle for it.
Aztec is also using other novelty schemes to implement trusted initial setup. PLONK is a new type of efficient ZK-SNARK architecture that requires only one trusted setup and then all programs can reuse this setup. Moreover, because PLONK's demand for gas is not high, it is effective enough for practical use on Ethereum. Based on this trading capability, AZTEC CEO Tom Pocock believes that PLONK can write logically complex programs in a way that perfectly protects privacy.
Introduce secure multiparty computing to zero knowledge
This scheme was previously used in ZKBoo and has recently been applied to Ligero, which "compiles" secure multiparty computing protocols into the ZK-PCP system (the earliest probabilistic ZK system), which is implemented as a requester ( "In the mind" submits a copy of the secure multiparty computing protocol, and the verifier can then randomly evaluate the view of any participant. To put it bluntly, an entity with relevant data information can simulate a distributed calculation between multiple parties and then display a copy of the calculation at a random point of the evaluation. More importantly, the use of MPCs has created promises for creating privacy-based smart contracts.
Similar to ZK-STARK, the MPC-based proof has the following advantages:
-
Transparent – the generation of random numbers is public information -
Post-quantum security – relying on open randomness and the availability of hash functions make quantum systems unable to launch large-scale attacks -
Scalable – MPC-based proofs have (quasi-linear) proof time and verification time for efficient batch operations
When using this type of technology, you also need to consider how to weigh it in order to optimize small and medium "circuits" / problems – because this may give potential problems to the verifier.
Having said that, MPC-based technologies have not yet reached their full potential in the blockchain domain, and they may be more versatile than existing zero-knowledge technologies, especially when participants are required to retain confidential information related to actual computing. in the case of. For example, MPC technology can be useful when trying to run a credit scoring algorithm to assess user credit, because users and banks are reluctant to disclose their confidential information—users are reluctant to disclose their transaction history, and banks do not want to pay Weight information in their ML credit scoring model.
Hardware limitations
When Zcash first proposed using zk-SNARK to send transactions, people were still worried about the computing resources needed to generate hidden transactions, because it may take several hours to generate a transaction. But since then, we've made great strides, and now we can do similar tasks in just a few seconds on a browser or even a mobile device.
Privacy mixer
The coin mixer has recently received much attention. Time to return to May, Vitalik published an article explaining the motives and outlines of the next coin-operator design on the Ethereum network.
When a wallet or individual wants to conduct a native privacy transaction, the Ethereum coin can come in handy. The traceability of Ethereum gives bad guys the opportunity to get information on their wallets, accounts, etc. by tracking specific transactions. The coin can be anonymously traded by swapping the Ethereum.
Since then, many teams have been working around the clock to develop more practical Ethereum blenders. The table below lists the calculations and gas costs for the different currency schemes so far during the access process.
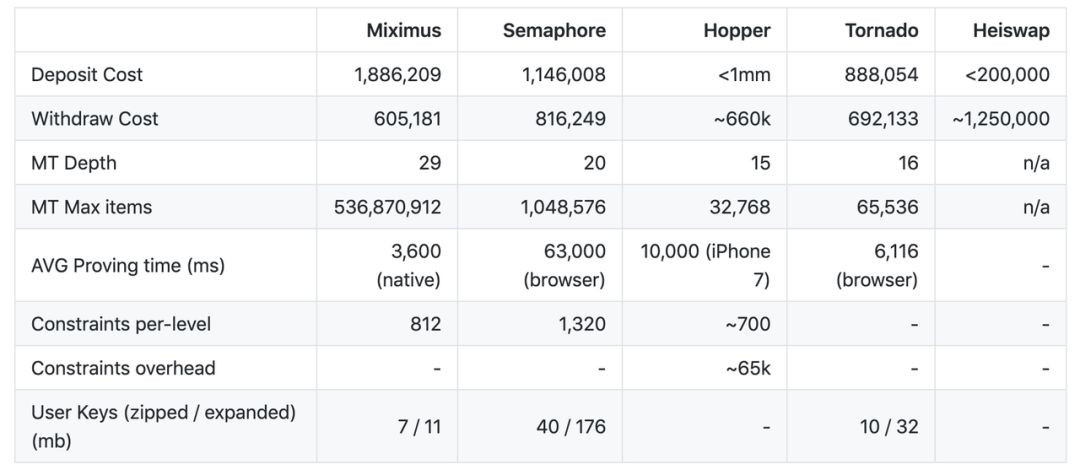
– View the types of Ethereum blenders and their respective calculations and gas costs via the GitHub status of the blender –
An independent mixer at the application level can never guarantee 100% user privacy and can only provide probabilistic guarantees. However, this is more than enough to meet the needs of the vast majority of individuals and businesses.
Who will pay for Gas? Relay risk
There is a fatal flaw in the various solutions mentioned above, that is, in the end, someone must pay the gas fee for the output. Where do these ether coins that can be used to pay for gas come from? If the bad guys can track some users through this part of the Ethereum, how are these users anonymous? This is not a waste of effort!
So, a familiar script with "chicken or egg first" was staged on the stage of privacy protection. Want to receive anonymous Ethereum? You must have an anonymous Ethereum in your wallet! Is it funny? In an original article on coin blenders, Vitalik proposed using a simple relay registration contract to solve this problem – the relay operator can register an HTTP endpoint for anonymous publishing of any transaction.
Finally, don't forget to consider the security of the wallet's interaction and operation. The default settings of the wallet need to be secure to protect the user's privacy, but it doesn't make the user feel too much trouble to get started. As for how to achieve this, everyone is still working hard. In order to achieve the desired privacy protection, all of these cooperator solutions require a large number of participants, so the tool must be easy for the public to get started, but any shortcut can lead to serious privacy violations. For a simple example, a user mixes some Ethereum with a coin and then uses some of them for privacy purposes. After a while, he forgets which wallet has sent a private transaction, and then Turning the remaining Ethereum in the wallet that has sent a private transaction back to a public address directly related to its identity… is simply a failure: (
From the above mentioned technologies and many other technologies that are working in this field, it is easy to see that privacy technology on Ethereum is gaining more and more attention, and these advances may soon be promoted on a large scale. . While it seems somewhat contradictory to implement privacy on a public chain, zero knowledge and other privacy technologies will make new cutting-edge games possible. At the same time, with these solutions, users no longer have to worry about financial privacy.
Looking to the future
Although this article does not provide a complete overview of all the privacy practices of Ethereum, it also examines the various ways to achieve corporate and user privacy. The anti-censorship technology that brings freedom has inspired many projects in the cryptocurrency ecology. In order to create a native encryption world, the ability to anonymously trade or protect personal information is critical. We don't have any panacea to protect privacy, but there are many ways and mechanisms to provide privacy for specific use cases.
(Finish)
(A lot of hyperlinks are provided in the article, please click to read the original text to get the EthFans website)
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- QKL123 market analysis | Bitcoin adjustment is nearing the end, or will start the slow cattle market (1104)
- Speed reading | Bitcoin S17+ new mining machine revenue evaluation; exchange wallet holds 6.7% of all bitcoin
- What are the major impacts of the accelerated development of the central bank's digital currency?
- Failed to pay 500,000 bitcoins, CSW violated the settlement agreement, litigation restarted
- The first anniversary of the Uniswap agreement, how is this alternative Ethereum DEX developed?
- Research report | Libra is still on the line, the project development is hot
- Weekly data on the BTC chain: data on the chain began to fall, and the exchange traded frequently




