Science | What is the blockchain?
Author: Mohit Mamoria
Translation & Proofreading: Ajian & Elisa
Source: Ethereum fans
Unless you are a caveman, I am sure you have heard about Bitcoins and blockchain. After all, they are hot spots, the favorite topic of the media these days, and the annual buzzword. Even the guys who have never heard of cryptocurrency and don't even know how it works are talking about it. Among my friends, there are more non-technical homes than technical homes. In order for me to explain this new buzzword to them, they have been harassing me for several weeks. I guess thousands of people have the same feelings as me. When this happens, it's time to write something so that everyone can wake up those confused eggs – this is the purpose of this push – written in plain English, so that any ordinary netizens can understand .
- Xiao Ge’s whimsy only used bitcoin to travel to Europe. In the first 40 hours, he didn’t like it…
- "I must come back to save this company!" Wu Jihan "forced the palace" to regain the position of the mainland
- A total of the wind! Babbitt goes online "Industry blockchain channel"
Blockchain: Why do we need something so complicated?
“Every complicated question has a clear, simple and wrong answer.” —HLMencken
Contrary to any other push on the Internet, we don't define what is a blockchain from the beginning, we will first understand the problem it is trying to solve.
Imagine Joe is your best friend. He is traveling overseas. On the fifth day of his holiday, he gave you a call, "Dude, I spent all my money, and the rivers and lakes were in a hurry."
You answer "Remove immediately" and then hang up.
Then you call the manager of your bank account:
"Please transfer $1,000 from my account to Joe's account."
Your account manager replies:
"Received, sir."
He opens the books and checks your account to make sure you have enough balance to transfer $1,000 to Joe. Because you are a local tyrant and have a large amount of balance on the account, he has registered an entry in the books, as shown below:
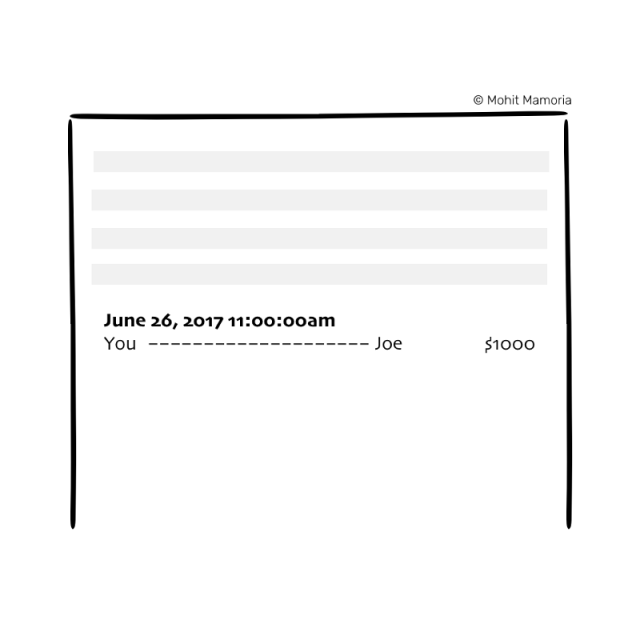
Note: We don't mention the computer, just to make the example simpler.
Call Joe and tell him:
"I have already transferred the money. The next time you go to the bank, you can take out the $1,000 I just transferred."
so, what happened? You know, that is to say, both you and Joe have entrusted the bank to manage your money. There is no actual flow of physical notes to transfer your money. All that is needed is just an entry on the books. Or more accurately, an entry on the books that is neither controlled by you nor Joe nor owned by you.
This is the problem with the existing system.
In order to build mutual trust between us, we rely on independent third parties.
For many years, we rely on these agents to trust each other. You may ask, "What are the problems with relying on them?"
The problem is that they are just numbers. If it is to cause a chaos in society, all it needs is nothing but a person or an institution that goes to corruption, whether consciously or unconsciously.
- What if the book that recorded the transfer was burned to a ash in a fire?
- If so, your bank manager is wrong, write a $1,500 instead of $1,000?
- If so, is he intentionally doing it?
For many years, we have kept all our eggs in one basket and are still baskets of others.
Is there a system like this, where we can transfer money without a bank?
To answer this question, we need to dig deeper and ask ourselves a better question (after all, only better questions lead to better answers).
Think about it, what does the transfer mean? It's just an entry on the books. The better question would be – is there a way to maintain that book among us instead of letting others do it for us?
Now, there is finally a question worth exploring. And the answer you may have guessed. Blockchain is the answer to this esoteric question.
It is a way of maintaining the books among us rather than relying on others to do it for us.
Can you keep up? well. Because many problems are now starting to explode in your mind, we will learn how this decentralized book works.
Ok, tell me how it works?
The requirement of this method is that there must be enough people who do not want to rely on third parties. Only in this way can this group of people maintain their books on their own.
“It might make sense to only get people to get bitcoin in the transactions that Bitcoin brings. Once there are enough people to think like this, it will become a self-fulfilling prophecy.”
——Zhong Bencong, 2009 How many talents is enough? At least three. For example, let's assume that 10 people want to abandon the bank and any third parties. According to the mutual agreement, they can always have each other's account information – but do not know the true identity of others.
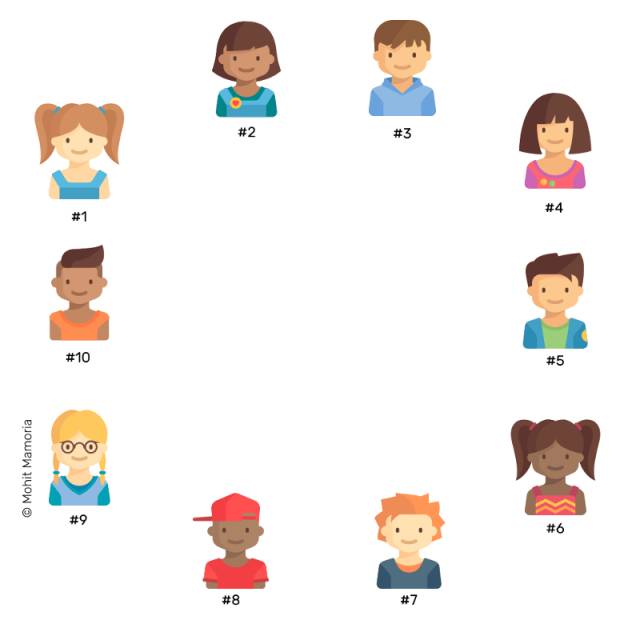
An empty folder
In the beginning, everyone had an empty folder. As we are going to do, these 10 people will continue to add paper to their current folder. And the collection of these papers will form a book of tracking transactions.
2. When a transaction occurs
Then everyone in this network will have a pen and paper in hand. Everyone is prepared to record any transactions that take place inside the system.
Now, let's say #2 wants to transfer $10 to #9.
In order to complete this transaction, #2 took a nap and told everyone:
"I want to transfer $10 to #9. Everyone is writing down on their own small books!"
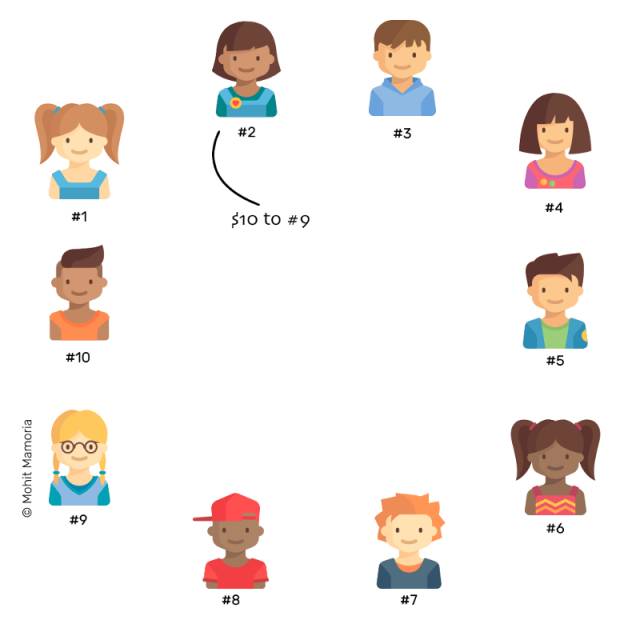
Everyone is aiming at #2 is there enough balance to transfer $10 to #9. If she had enough money, everyone made a record for the deal on their own blank page.
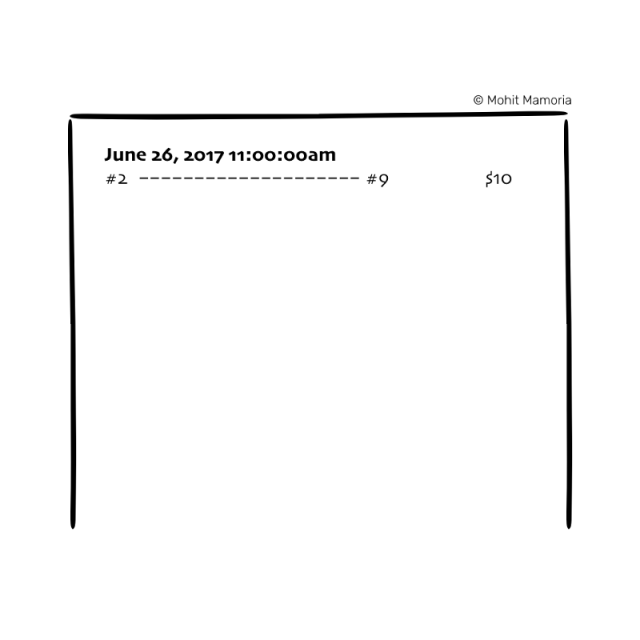
In this way, a transfer is considered complete.
3. The transaction continues to occur
Time flies, and more people on this network want to transfer money to others. Whenever they want to make a deal, they announce the deal to everyone else. Whoever hears this declaration, write it on his/her own paper.
This practice continues until everyone runs out of space on their current page. Suppose 1 page can record 10 transactions, and once 10 transactions are completed, everyone runs out of space.
When the paper is full
Then, it is time to save the page to the folder, then take out a new piece of paper and repeat step 2 above.
4. Store paper
Before you deposit this page into our folder, we need to seal it with the only key that everyone on the network agrees with. Through sealing, we can guarantee that once the backup of the page has been saved into each person's folder, no one can make any changes to it – not only today, not just tomorrow, but also more than one year later. Once in the folder, it will always stay in the folder – it will be sealed. Moreover, if everyone trusts this seal, everyone will believe in the content of the page. The sealing method of this page is the key to this method.
[The term box] This thing used to protect the content of paper is called "mine", but in order to simplify it, we still call it "seal."
Earlier, third parties/intermediaries gave us trust in the form that they could never be changed, no matter what they had written in the books. In a decentralized, decentralized system, like our system above, this seal will provide a trust replacement.
Because of the lack of Sting! So how do we seal this record?
Before we learn how to seal this page, we need to know how, in general, how the seal works. To do this, the prerequisite is to learn something, I like to call it…
Magic machine
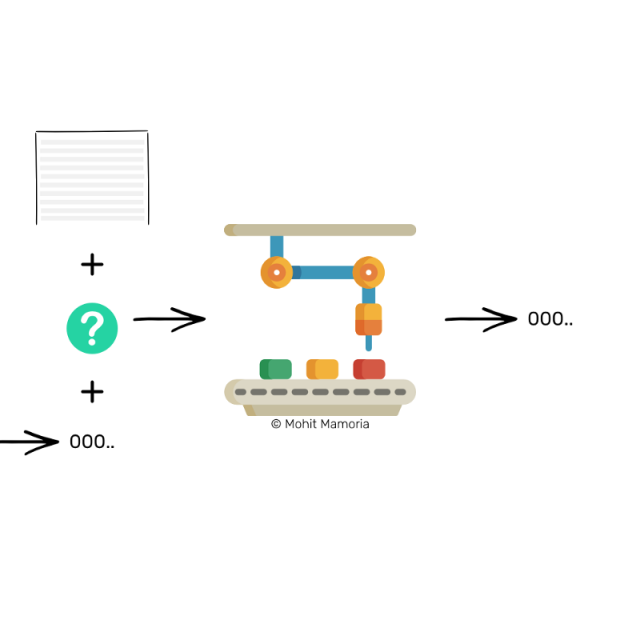
Imagine a machine surrounded by thick walls. If you put in a box with something on the left, it will spit out a box with something else.
[Terminal Box] This machine is called the “Hash Equation”, but we are not in the mood to be so professional. So today, they are called "magic machines."
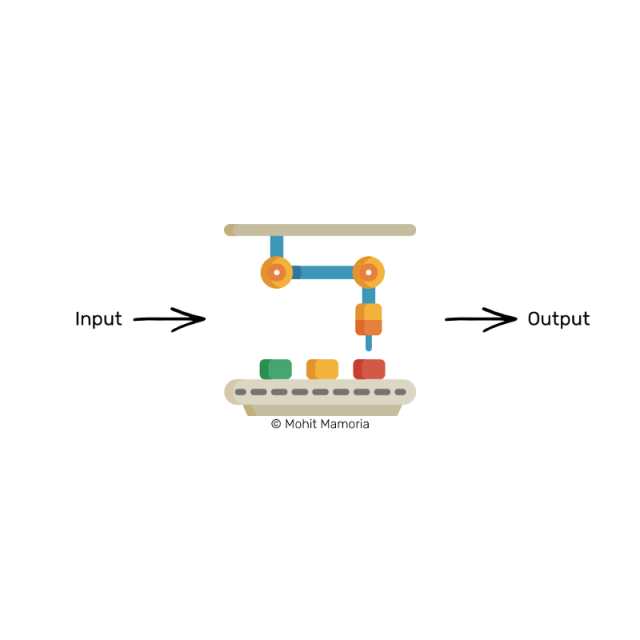
Magic machine (also known as hash equation)
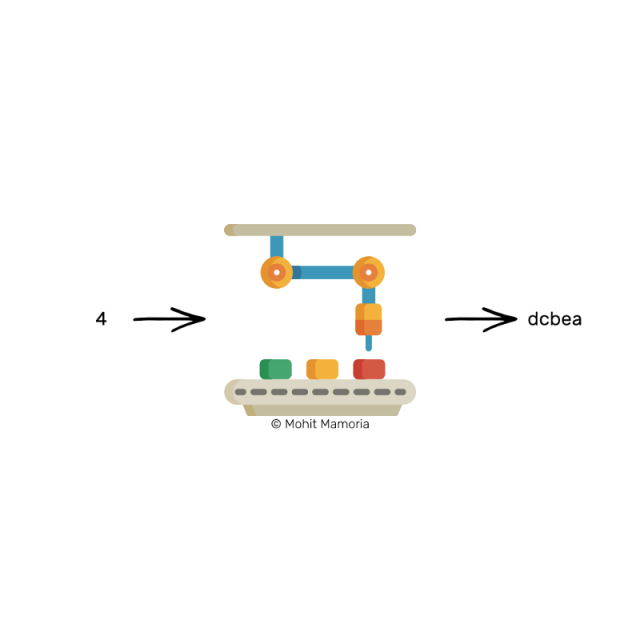
Suppose we put a number 4 in from the left and we will find that it spits out the following string on the right: 'dcbea'.
How is the number 4 converted into this string of characters? Nobody knows. Moreover, this process is irreversible. I got the string 'dcbea' and it is impossible to figure out what the machine received from the left. However, any time you enter the number 4 for this machine, it will always spit out the same character, 'dcbea'.
Try sending a different number into it. 26, how?
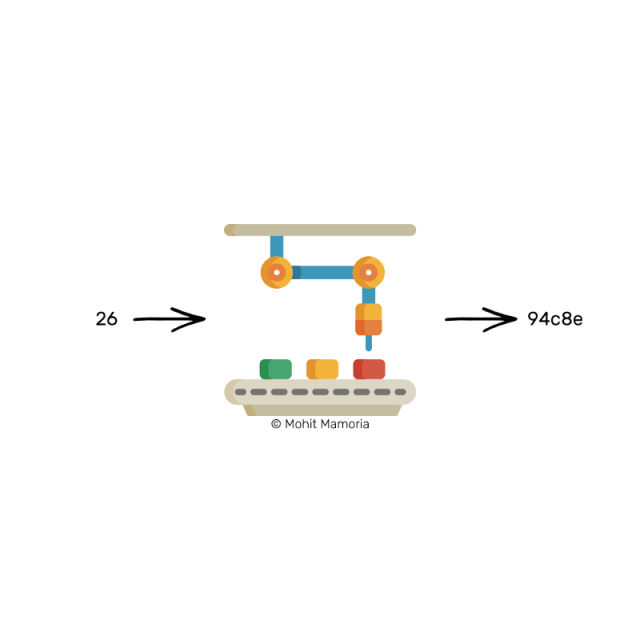
Hash(26)==94c8e
This time we got '94c8e' and it seems that the characters can also contain numbers. interesting!
If I ask you the following questions now, what will things become?
"Can you tell me that if I want to get a string of characters starting with 0 on the right side of the machine, what should I enter from the left side? For example, 000ab, or, 00098, or 000fa, or any other case. One."
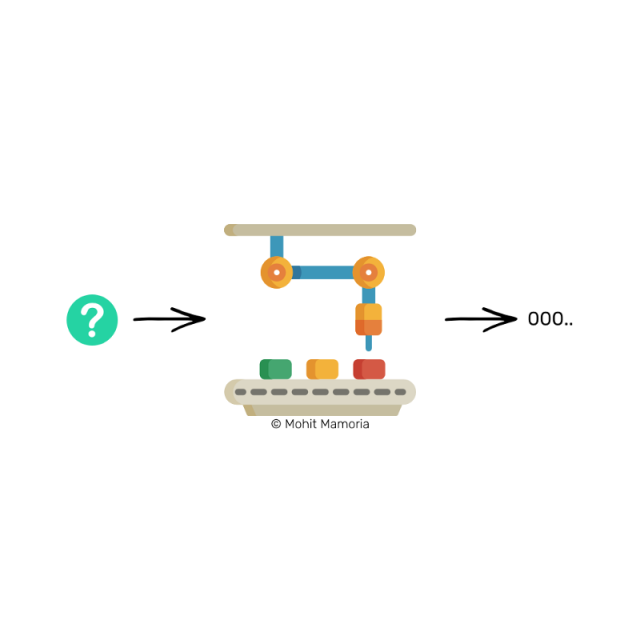
Think about this question.
I have already told you that this machine has a property: after we get the expected output value from the right side, we can't figure out what we have to type in from the left. Give us such a machine, how can we answer the question I asked?
I can figure out a way. Why don't we traverse all the numbers in the universe one by one until we get a string of characters starting with three zeros?
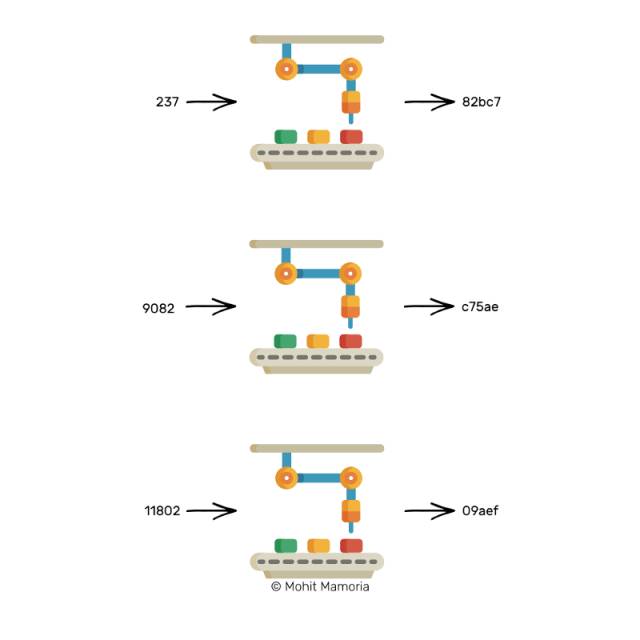
Try all the numbers to figure out the required input values
Optimistically, after a few thousand attempts, we end up with a number that will produce the required output value on the right.
It is extremely difficult to calculate the input value given the output value. But at the same time, it is extremely easy to verify if the predicted input value produces the desired output value. Remember to put in the same number, this machine will spit out the same characters every time.
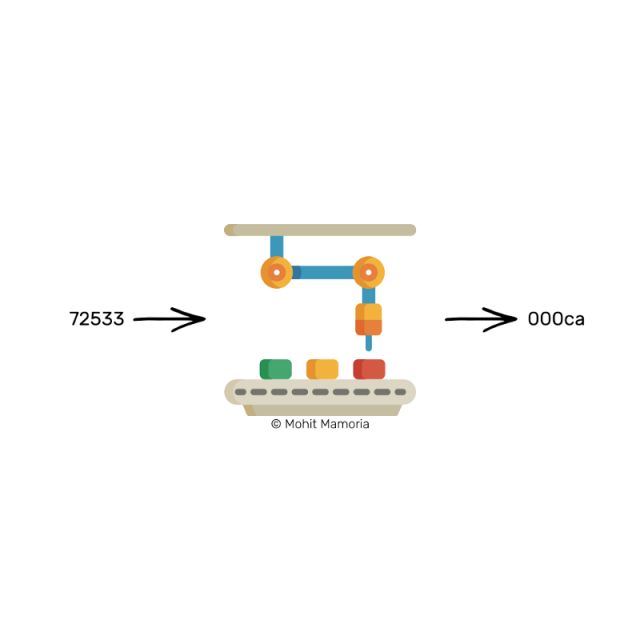
If I give you a number, such as 72533, then ask you a question: "This number, after entering this machine, will produce a string starting with three zeros?" How hard do you think it is to get an answer? ?
Everything you have to do is just throw in the number and see what we got on the right. that's it.
The most important attribute of such a machine is – "giving an output value, it is extremely difficult to calculate the input value. However, given the input value and output value, it is very easy to verify whether the input will cause the output. of."
In the rest of this article, we have to remember this property of this magic machine (or hash equation):
" Given an output value, it is extremely difficult to calculate the input value. However, given input values and output values, it is very easy to verify that the input will cause the output."
How to encrypt a file with such a machine?
We will use this magic machine to create a seal for our paper. By convention, we will start with an imaginary situation.
Imagine I gave you two boxes. The first box contains the number 20893. Then I ask you,
"Can you find a number, add the number in the first box, enter it, and eventually give us a character starting with three zeros?"
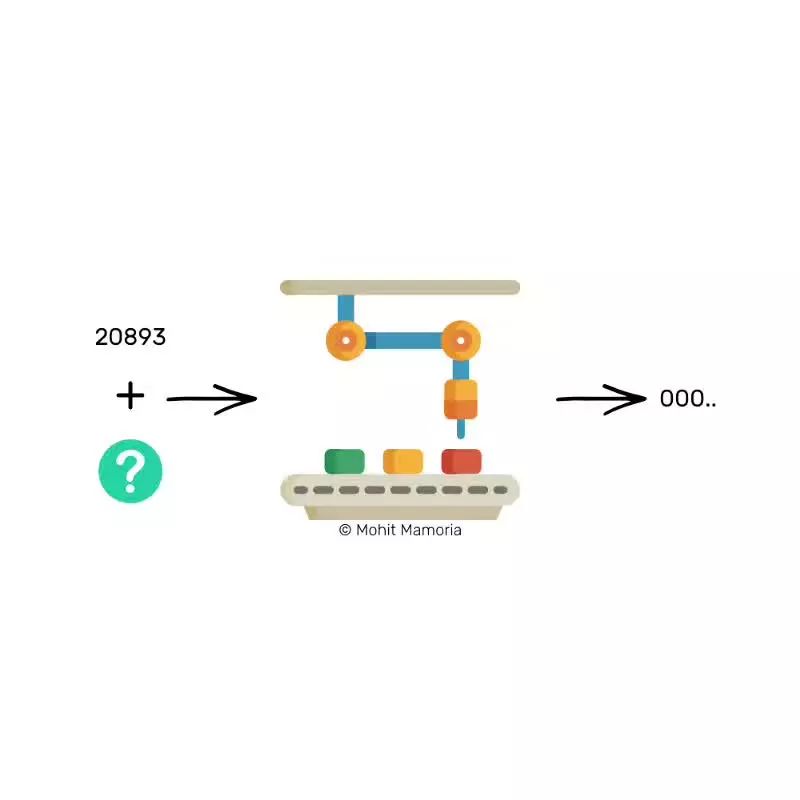
This situation is very similar to what we saw before, and we already know that the only way to figure out such a number is to exhaust every possible number in the universe.
After thousands of attempts, we will stumble upon a number, such as 21191, plus 20893 (for example: 21191 + 20893 = 42084) input machine, will produce a string of characters that meet our requirements.
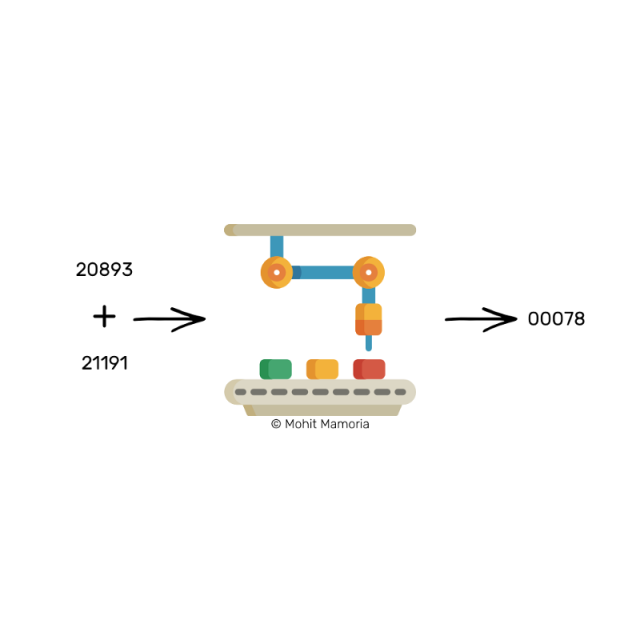
In this example, the number 21191 becomes the seal for the number 20893. Suppose there is a piece of paper now, the number 20893 is written on it. In order to seal this page (for example, so that no one can change the content of this page), we will put a badge with the label '21191' on it. Once the sealed number (eg 21191) is stamped on the paper, the page is sealed.
 Sealed number
Sealed number
[Terminal Box] A sealed number is also known as a “workload proof,” meaning that this number demonstrates the effort that has been made to calculate it. For our purposes, we'd better call it "sealed numbers."
If anyone wants to verify that the page has been replaced, all he needs to do is to add the contents of the page to the sealed number and enter the value into the magic machine. If the machine gives a string of three characters starting with 0, the content is not changed. If the characters that appear do not meet our requirements, we can drop the page because its content is already hydrated and has no use.
We will use a simple sealing mechanism to archive all the records and eventually arrange them in our respective folders.
Finally, seal up our files
To seal the records that contain the transactions in our network, we will need to figure out a number that, after being added to the transaction list and entered into the machine, will allow us to get a string of three characters starting with 0.
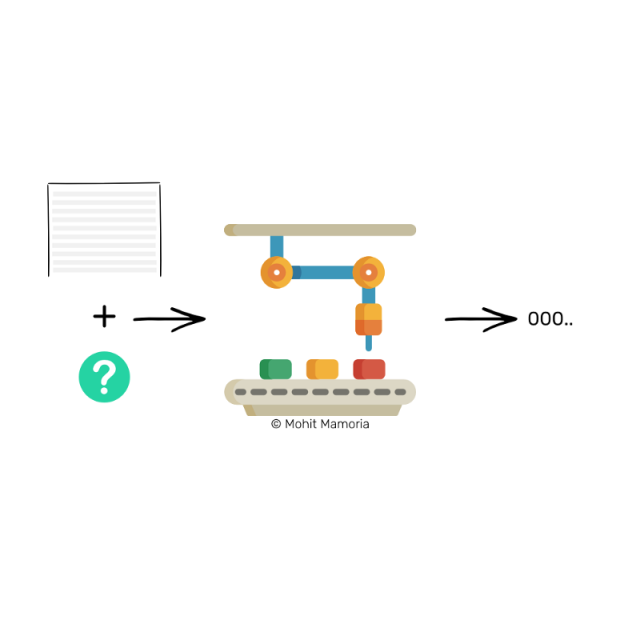 Note: I have been using the "three zeros at the beginning of the character", just an example. It illustrates how the hash equation works. The actual challenge is much more complicated than this.
Note: I have been using the "three zeros at the beginning of the character", just an example. It illustrates how the hash equation works. The actual challenge is much more complicated than this.
We will spend time and power on this machine, but once we figure out that number, the page is sealed by that number. Forever and ever, if someone tries to change the content on this page, this sealed number allows anyone to verify the integrity of the page.
Now that we know the way to seal records, we will return to the time when we have written 10 transactions on this paper and no space to write more records.
Once everyone had exhausted a page of paper and could not record further transactions, they began to work hard to calculate the sealed number of the page so that it could be hidden in a folder. In the network, everyone performs this calculation, and the person who first calculated the sealed number will announce the number to everyone else.
After hearing the sealed number, everyone immediately verifies that it produces the required output value. If so, everyone marks the paper with their number and puts the paper in a folder.
However, what if you are not able to produce the required output value for someone, such as #7, the declared seal number? This situation is not uncommon. Possible reasons are:
- He may have misunderstood the transaction announced on the network before.
- He may have miswritten the transaction announced on the network before
- He may try to cheat when recording a transaction, for personal gain, or to please some people on the network.
Whatever the reason, #7 has only one option – to abandon his record and get a copy from someone else so that he can also put the paper in a folder. Unless he does not put his paper in the folder, he will not be able to continue to record further transactions, which will therefore prohibit him from becoming a member of the network.
The sealed number that most people agree with, whatever it is, will become that credible sealed number.
However, if they know that others will figure it out and then announce it, why do everyone spend resources to calculate? Why not sit back and wait for your thighs?
good question. This is where the motivation is added to this picture. Members of each blockchain are eligible for awards. The first person to calculate a sealed number will receive free money as a reward for his efforts (eg, CPU power and power paid).
Simply imagine that if #5 calculates a sealed number for a one-page record, he gets some free money as a reward, assuming a dollar that is cast out of thin air. In other words, #5's account balance has increased by $1, while no one has reduced their account balance.
This is how Bitcoin becomes a reality. It is the first currency that is traded on a blockchain (eg, a decentralized ledger). At the same time, people are rewarded with Bitcoin as a reward so that on the web, efforts to calculate sealed numbers will continue.
When enough people hold Bitcoin, Bitcoin will appreciate, making more people want Bitcoin; this will further increase Bitcoin; this appreciation will make more people want Bitcoin; this desire further makes the bit The appreciation of the currency; this cycle.
This kind of reward makes everyone in the network work without stopping.
Once everyone has folded a page into the folder, they will take out a blank sheet of paper and repeat the process again – forever.
*[Terminal Box] * Think of a page as a block of a transaction, a folder as a paper (block), and as a result, it becomes a blockchain.
Old iron, this is how the blockchain works.
however. I still have a little thing that I didn't tell you.
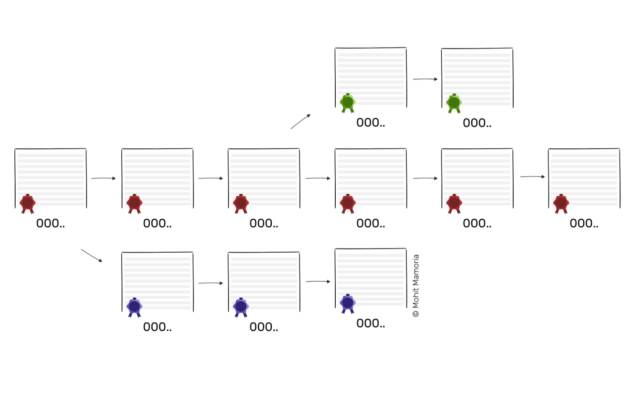
Imagine that there are already five pages in the folder – all encrypted with a sealed number. What happens if I go back to the second page and change the transaction history for personal gain? Sealing the numbers will make anyone aware of the contradictions in the transaction record, right? Then, if I go further, calculate a new sealed number for the revised transaction record, and poke this substitute on paper? To prevent this problem, that is, someone backs up and modifies the paper (block) and the seal number, there is an explanation here about how a sealed number is calculated.
Prevent modification of sealed numbers
Remember how I told you? I gave you two boxes – one with the number 20893 and the other empty for you to calculate? In fact, in order to calculate the sealed number on the blockchain, there are three boxes instead of two – two pre-installed ones, one being used for calculation.
When the contents of all three boxes add up and enter the magic machine, the answer from the right side of the machine must meet the required conditions.
We already know that a box holds a list of transaction records, and a box will contain sealed numbers. The third box, with the magic machine output value of the previous paper.
With this elegant care machine, we can guarantee that every page of paper depends on the paper before it. Therefore, if someone wants to modify a history, he will also have to change the content and seal numbers of all the papers after the page to keep the chain consistent.
If someone, not the 10 people we envisioned at the outset, tried to cheat and modify the contents of the blockchain (the folder that holds all the transaction history list papers), he would have to adjust multiple pages of paper for all of them. The paper calculates a new sealed number. We all know how difficult it is to calculate sealed numbers. Therefore, a bad guy in this network can't bully nine honest people.
What will happen is that from the night the dishonest guy tries to cheat, he will create another blockchain in the network, but that blockchain will never catch up with the trusted blockchain— – Just because a guy's effort and speed can't beat the effort and speed that nine people have accumulated. Therefore, this guarantees that in a network, the longest chain is a trusted chain.
The longest chain is the chain of honesty and trustworthiness.
The longest chain is the honest and trustworthy chain
When I tell you that a dishonest guy can't bully nine honest people, does it wake you up?
In case, not one, but six people do things?
In this case, the agreement will fall through and surface. It is known as the "51% attack." If most people on the network decide to become dishonest and deceive the rest of the network, this agreement will not achieve its goals.
At any time, if the blockchain is likely to fall, this is the only reason for its vulnerability. Knowing this, it is unlikely to happen. However, all of us must know this weakness of this system. It builds on the assumption that most of a group of people are always honest.
Old iron. This is everything about the blockchain. Any time you find someone feels backward and confused, "What the hell is the blockchain?" You know you can guide them where to go.
Make a bookmark for this link.
I thought that some people should read this now? The "Share" button is in your hand.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Viewpoint | The essence of blockchain is a variety of data governance ideas
- Countdown to 10 days, grab the ticket Raiders! World Blockchain Conference · Wuzhen is worse for you
- Bakkt will partner with Starbucks to launch bitcoin payment business
- In order to verify the credibility of the data, Dell, the Linux Foundation, etc. jointly developed a distributed platform.
- ICBC took the lead in testing the digital currency wallet service. When will other banks follow up?
- The FOMO effect is coming! Following China, the Korean government is committed to supporting blockchain technology
- Viewpoint | What is the experience of the Internet development process for the popularization of blockchain?





