Concept and Application of Threshold Signatures
Threshold Signatures: Concepts and ApplicationsThis lecture will introduce the concept and application of threshold signatures in four parts: In the first part, the concept and classification of digital signatures are introduced, and its basic algorithm components and application functions are elaborated. In the second part, the threshold signature concept is introduced to address the risk of single point failure in digital signatures, and its technical advantages and features are described. In the third part, threshold signatures and multi-signatures are compared, and the advantages of threshold signatures in flexibility, anonymity, and scalability are explained. This is also the reason why it has become a research hotspot in the field of cryptography today. Finally, the typical application of threshold signatures in the field of blockchain is introduced, demonstrating how it can empower different application scenarios and generate core value.
Blockingrt 1: Concept and Classification of Digital Signatures
Digital signatures are not the digitization of signatures
In the early days, handwritten signatures and seals were commonly used to sign contracts, documents, and treaties. However, after the advent of computer networks, how to sign electronic documents and files became an urgent problem to be solved. The strong application demand also gave birth to the solution to the problem, which is digital signatures.
- Overview of the NFTFi ecosystem
- Derivatives DEX Battle: Kwenta and Level Surpass GMX in Weekly Trading Volume
- Meme Topic Issue 1: May’s Winner
Digital signature is a new type of message signature that is transmitted or stored in electronic form, which is different from traditional handwritten signatures, and is not “digitization of handwritten signatures”. Academically, digital signature refers to an algorithmic scheme that can verify data integrity and confirm the identity of the data sender, and can determine the authenticity of the signature and the signed data by a third party.
Representation of the Five Elements of Digital Signatures
By abstracting and formalizing the operation principle of digital signatures, the five-element representation of digital signatures can be obtained, namely (M, K, S, SIG, VER):
M: Message collection, generally the hash digest of the signed object;
K: The key set, that is, the range of keys that digital signatures can use, generally a 256-bit random number set;
S: Signature set, the output of the signature algorithm, which can be verified by the verification algorithm;
SIG: Signature algorithm, defined as K × M→S, with message and key as inputs, and output signature;
VER: Verification algorithm, defined as MS{True, False}, to verify the consistency of message and signature, and of course, this process also requires the public key corresponding to the signature key as input.
Classification of Digital Signatures
Digital signatures can be classified based on different dimensions, such as based on mathematical problems, number of signature users, whether the digital signature is recoverable, whether the signer can see the message, and whether the signature supports delegation, as shown in the figure below.
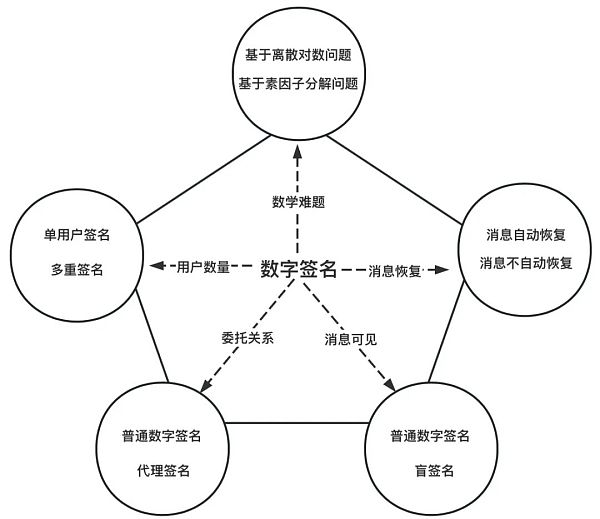
Currently common digital signatures include Shamir backpack digital signature, Rabin digital signature, GOST digital signature, ElGamal digital signature, Schnorr digital signature, RSA digital signature, ECDSA digital signature, BLS digital signature, etc.
Blockingrt 2: The Birth and Technical Features of Threshold Signatures
The Achilles’ Heel of Digital Signatures
Achilles is a hero in Homer’s epic, he is invincible in battlefields, and he has no fear, but such a powerful warrior also has his fatal weakness – his ankle, and he eventually died from an arrow shot in his ankle. Similarly, the same applies to digital signatures, as a powerful cryptographic tool, it can prevent counterfeiting and repudiation, but all this is based on the security of the signing private key. Once the private key is leaked, the attacker will easily complete malicious activities such as identity forgery and unauthorized access.
Under the traditional digital signature scheme, the private key of the signature is controlled by a single entity, usually stored by encryption or hardware protection (U disk), but still has great usage risks.
-
Security of the private key: Attackers can invade the signer’s computer through network attacks, and even if it is encrypted and stored, they can capture the private key in memory during the signing process, thus stealing the signing key;
-
Availability of the private key: Regardless of whether it is hardware or software storage, there is a risk of single node failure (Single Point of Failure). Once the signature private key is lost, it cannot be recovered.

Threshold Signature – Eggs are never put in one basket
Threshold signatures are the solution to the security risk of centralized control of digital signature private keys. The core idea is that the private key is no longer controlled by a single node, but is split into multiple fragments and controlled by multiple nodes, thereby achieving high security and availability of the private key. Specifically, threshold signature is the result of “thresholdization” of ordinary digital signature. It decentralizes the signing power to a group of nodes, and only requires cooperation from more than the threshold number of nodes to complete the signature generation. Therefore, the signing process of ordinary digital signature algorithm can be considered “centralized”, while the signing process of threshold signature algorithm can be considered “distributed”.
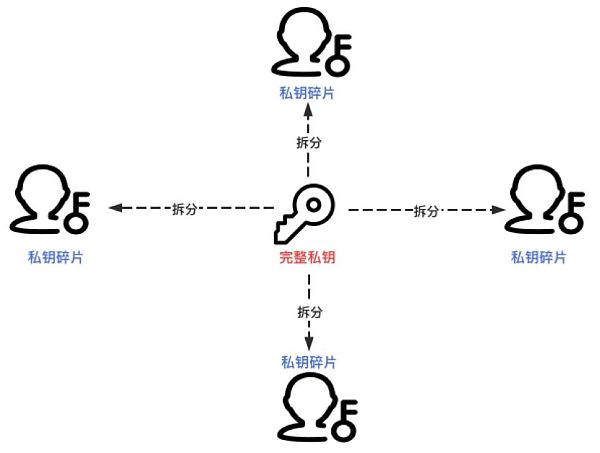
Composition of the threshold signature algorithm
The signature generated by the threshold signature algorithm is the same and indistinguishable from the signature generated by the ordinary signature algorithm, and the signature verification process of the two is the same. Therefore, the focus of the threshold signature algorithm is on its key generation process KeyGen and signature process TSig. A (t,n) threshold signature algorithm contains the following two processes:
KeyGen : Takes the security parameter as input and outputs the signature public key pk and n private key fragments (sks 1 , sks 2 ,…, sks n ). Each private key fragment sks i is only known to node P i , and the n private key fragments collectively constitute the (t,n) secret sharing of the signature private key sk. It should be noted that sk only exists theoretically and will not appear in the key generation or signature process;
TSig : Takes the message to be signed and no less than t private key fragments as input, and outputs a legal signature.
Comparison and Advantages of Threshold Signature and Multi-Signature
In addition to threshold signatures, another way to prevent single-point failure is multi-signature. Simply put, in the multi-signature mechanism, the public key of the signature is no longer one, but there are multiple public keys, and only collecting more than the threshold number of signatures is considered a successful signature. Although multi-signature can achieve application value equivalent to threshold signature to some extent, threshold signature still has advantages in flexibility, anonymity, and scalability. The following will explain these three advantages from the perspective of blockchain:
Flexibility
In the process of implementing multi-party management of accounts, the flexibility of multi-signature is significantly lower than that of threshold signature, which is reflected in two aspects: first, under the multi-signature mechanism, the public key and other information of the signer jointly determine the account address. Once the control logic of the account changes (such as adding or reducing signers), the account address will change, and funds need to be transferred from the old account address to the new account address, which is less flexible; secondly, in Bitcoin, the number of public keys in multi-signature is subject to upper limit requirements, so multi-party account management scenarios exceeding the upper limit cannot use multi-signature.
In the threshold signature mechanism, the change of the signer’s identity will be reflected in the redistribution and generation of the account private key shares (Reshare), and the account address will not change; at the same time, n and t in the threshold signature can be set arbitrarily without any restrictions, and can support any scenario requirements.
Anonymity
The anonymity of blockchain is a core feature, where account addresses on the chain cannot be associated with real-world identities. However, the use of multi-signature can lead to a significant reduction in user anonymity, reflected in two aspects: first, although account addresses on the chain cannot be associated with real-world identities, their related transactions are publicly visible. Under the multi-signature mechanism, the public key of each signer is exposed, causing different accounts to be associated through public signers, which destroys account privacy and anonymity. Second, the exposure of the multi-signature public key set, as well as the number of signatures attached to the complete transaction, can effectively deduce the control logic of the account, and even tie it to real-world business, reducing anonymity.
Under the threshold signature mechanism, the resulting transaction is indistinguishable from a normal transaction data structure, and the signing process is completed off-chain, without causing any anonymity risks.
Scalability
Under the multi-signature mechanism, all signers’ digital signatures need to be attached to the final blockchain transaction, so the transaction size is linearly related to the number of signers. The more complex the control logic (such as an increase in the number of signers), the larger the data size of the final transaction. This feature has two consequences: first, the blockchain transaction fee is tied to the transaction size, so using multi-signature will increase the transaction fee, increase its usage cost, and is not suitable for some high-frequency business scenarios. Second, the increase in transaction space occupation will also increase the running load of the entire blockchain, indirectly reducing the efficiency of the system.
On the other hand, there is no such concern with threshold signature, because its final output is consistent with ordinary digital signatures, and only requires related communication and calculation among nodes during the signing process.
Specifically, under the threshold signature mechanism, the transaction data structure still only contains one signature, which is no different from a normal transaction, so the transaction fee is lower and will not add extra burden to the blockchain system.
Application of Threshold Signatures in the Blockchain Field
Ensuring Blockchain Account Security
In recent years, encryption digital currencies represented by Bitcoin have developed rapidly and gradually entered the lives of ordinary people as a new payment method. Unlike traditional payment systems, there is no centralized operating agency in the encryption digital currency system, and all payment operations are completed by sending transactions with digital signatures from accounts. Therefore, the security of encrypted currency accounts is equivalent to the security of signature private keys. The leakage of private keys will directly lead to the theft of assets in the account. However, the security of user encrypted digital currency accounts is facing huge threats: hackers control user computers by sending Trojan-containing emails to steal account private keys, and then send transactions to transfer the encrypted currency to the exchange for profit. Therefore, ensuring the security of encrypted digital currency accounts is urgent.
The threshold signature algorithm is an effective means of ensuring the security of encrypted digital currency accounts. Instead of a single node generating and storing a user account’s private key, n nodes cooperate to generate an account address, with each node storing a fragment of the account’s private key. When a transaction is sent, one of the nodes constructs the transaction and sends it to the other nodes. Then, all nodes run the threshold signature algorithm to cooperatively generate a valid signature for the transaction. Finally, one node broadcasts the signed transaction to the blockchain network. An attacker needs to successfully attack at least t nodes to recover the account’s private key. Users can flexibly determine the total number of nodes n and the value of the security threshold t according to their actual needs. Therefore, the threshold signature algorithm can effectively improve the security of encrypted digital currency accounts.
Locking Cross-Chain Assets
Cross-chain technology allows digital assets to flow freely on different blockchains, breaking down information silos between different blockchains. An important premise of cross-chain is “asset conservation,” which means that when digital assets are transferred from one blockchain to another, the digital assets on the original blockchain need to be locked. To ensure decentralization, asset locking is often completed by a group of nodes, and unlocking can only be completed by cooperation of more than a certain number of nodes.
For blockchain platforms that support smart contracts such as Ethereum and EOS, asset locking logic can be written as a smart contract, and users can complete locking by transferring assets to this specific contract. For blockchains that do not support smart contracts such as Bitcoin, asset locking depends on establishing a multi-party custody account, and users can complete locking by transferring assets to this account.
As mentioned in the third section, although multi-signature can also complete multi-party custody of accounts, threshold signature has advantages in flexibility, anonymity, and scalability, making it more suitable for cross-chain asset locking scenarios. In terms of flexibility, n and t can be set arbitrarily to meet different scenario requirements; in terms of anonymity, the locking account generated by the threshold signature algorithm has the same data structure and usage as a normal account, and a valid signature cannot reveal the information of the node participating in the signature process; in terms of scalability, each transaction is consistent with a normal transaction and only needs to carry a digital signature, reducing transaction costs.
Design of Consensus Mechanism
In Byzantine Fault Tolerance (BFT) consensus protocols, consensus nodes need to vote on the content to be agreed upon, and the vote exceeds a certain proportion (such as two-thirds) to reach consensus. In the algorithm process, “voting” needs to verify the identity of the voter and prevent replay attacks. The solution adopted is to digitally sign the consensus content and then broadcast it. Analyzing the entire consensus process, its core logic is very consistent with threshold signature, that is, when more than a certain threshold value of nodes agree, it is considered a successful consensus/signature. Therefore, instead of consensus nodes needing to collect enough signature information in the network, it is better to construct a common public key based on threshold signature, and then each consensus node holds a private key fragment, which can calculate the signature fragment when recognizing the consensus content, and more than the threshold number of consensus nodes need to participate to obtain the complete digital signature. This design pattern can effectively reduce the space occupied by consensus results.
This is an empty HTML document with an empty `
` tag.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- What happened to the Move2Earn game that was popular in 2022 in 2023?
- Path to Web3 Identity
- How much does it cost the well-known DeFi protocol MakerDAO per year to maintain the normal operation of its network?
- a16z: Decoding the Key Elements of Decentralization in Web3 Protocols, Driving Decentralization Tools
- Understanding Neon in Six Questions: Scaling Ethereum dApps on Solana
- Hong Kong’s new regulations on virtual assets have been implemented, opening up the golden age of Web3.
- Quick look at Blockingradigm’s Q1 2023 investment landscape






