Why don't exchanges delist BTG and ETC that were attacked by 51%?
Written by Ashwin Ramachandran and Haseeb Qureshi, the former is a junior partner of Dragonfly Capital, a blockchain venture capital agency, and the latter is a managing partner of Dragonfly Capital
Source: Chain News
Compile: Zhan Juan
The 51% attack fundamentally violates the proof-of-work security model, but the exchange is unwilling to remove the attacked cryptocurrency because it is still profitable for the exchange.
- The Bank for International Settlements and the Federal Reserve are concerned about digital currencies, and international supervision is becoming more active
- Bitcoin stock in Coinbase cold wallet is about to exceed one million
- Scanning the data on the Bitcoin chain in January (Part 1): Unexpected currency price breakthrough
On January 23, Bitcoin Gold (BTG) was attacked by 51%, and $ 72,000 was double spent. This is the second time that Bitcoin Gold has been attacked, and its consequences have left many people wondering: Why are Bitcoin Gold and other PoW tokens vulnerable to 51% attacks not delisted by the exchange?
The answer is simple. But first, let's take a look at how this attack was performed.
Bitcoin Gold is a Bitcoin fork coin that uses the ASIC-resistant ZHash mining algorithm. ZHash is optimized for efficient GPU mining, which increases the difficulty of ASIC development due to its high memory requirements. Due to the commoditization of GPUs and the large supply relative to ASICs, they are widely used for rental, so it is easy for an attacker to lease enough hashing power to gain the dominance of the Bitcoin gold network. Mining pools such as NiceHash and MiningRigRentals have significantly reduced the cost of executing 51% attacks, and similar markets are emerging (see Warihash, Luxor, etc.) .
NiceHash Hash Market
The recent attack on bitcoin gold required an upfront capital cost of $ 3,400 (restructuring 29 blocks requires 0.4 bitcoin cost) , but note that these costs are compensated by the block rewards on the restructuring chain. Due to the low overall cost, this attack can fully use the spot GPU rental market. In addition, as the GPU leasing market becomes more liquid, the cost of surpassing GPU minable networks is decreasing (see Nice Hash pricing) . Therefore, the upfront funds that attackers need are nothing more than the bitcoin gold they want to spend, plus the cost of hashing power. If the BTG attacker double spends $ 72,000 , it is estimated that they only need to pay $ 3,400 (approximately $ 4,200 through block rewards) , bringing their return on investment to about 96.6% , which makes the attack a huge profit.
Of course, the main victims of 51% of attacks are exchanges . This attack usually goes like this: the attacker deposits tokens on an exchange, and these tokens are used to exchange some other liquid tokens, such as Bitcoin, and then withdraw Bitcoin. The original deposit was recovered by 51% of attackers after the transaction was completed, allowing them to take back their original deposit, essentially doubling their money. Due to this vulnerability, the exchange needs to wait for a confirmation period (the initial confirmation period for Bitcoin Gold on the Binance platform is 12 blocks) before allowing the withdrawal of tokens. However, although these confirmation periods increase security, they cannot completely prevent attacks. To learn more about the mechanism of the 51% attack, check out @ hoseeb's comment on a series of tweets published during the Ethereum Classic (ETC) attack last year.
The 51% attack on bitcoin gold is the second in two years (the first bitcoin gold attack was much larger) , but BTG is still trading on exchanges such as Binance. Naturally, the question arises: why does Binance not delist BTG?
Currently, BTG / BTC's trading volume is approximately USD 4.13 million per week. Therefore, only BTG / BTC trading pairs-assuming an average charge of 20 basis points per transaction (pending orders / bills) and low BNB usage-Binance's total annual profit is approximately $ 429,000 .
After calculating the profit of all PoW tokens with low and medium market capitalization, we can see that a trend is beginning to emerge. For Binance , it is more profitable to list PoW tokens with lower market value and midstream , even if they may suffer losses due to a 51% attack.
The chart below shows an estimate of the percentage of hash power available for rent and Binance's estimated profit (assuming current market prices) .
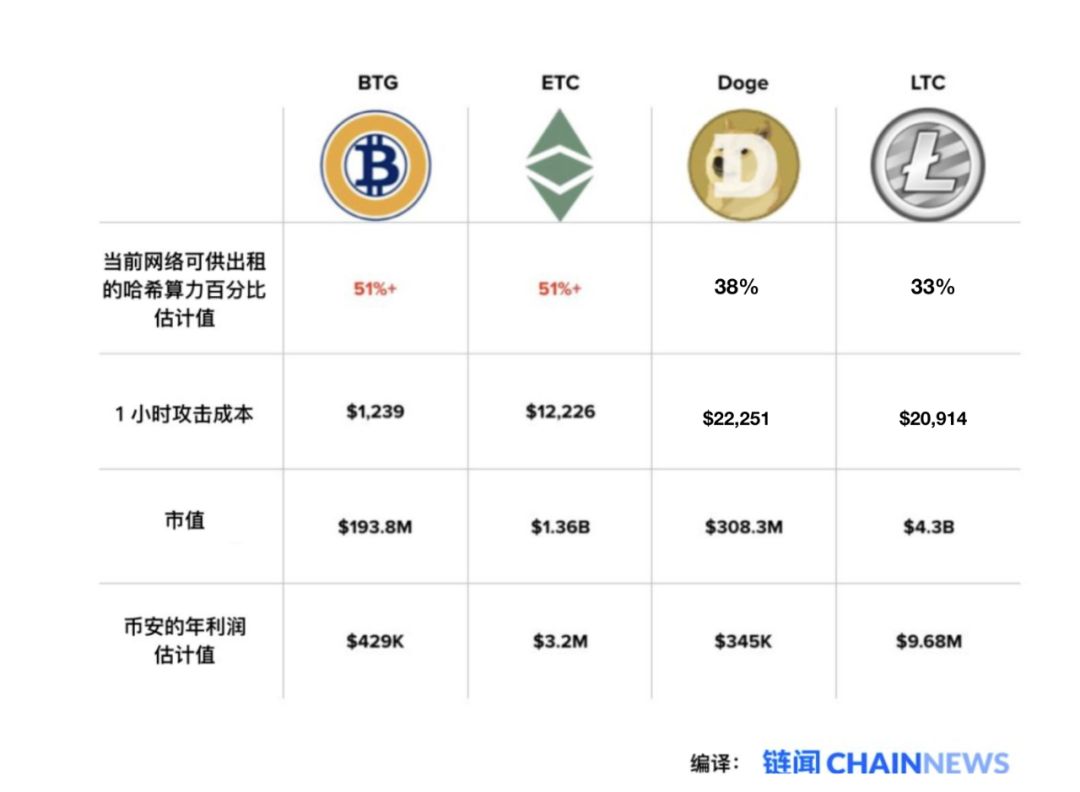
Assuming PoW tokens that are vulnerable to current exchange rates, sources: Binance API, NiceHash, MiningRigRentals.com
Note: All leased hashing power will increase the total computing power of the network. Therefore, an attacker must obtain 100% or more of the current hashing power to successfully launch a 51% attack. Hash hash power acquisition estimates are also susceptible to falling market prices, which could significantly increase attack costs.
We can summarize the listing / delisting decisions of the vulnerable PoW tokens into the following simple formula:

Annual profit> Revenue (51% attack) * (average attack profit)
Profit must exceed potential attack losses
As long as the above situation persists, we expect Binance and other lucrative exchanges to continue trading those vulnerable PoW tokens. Exchanges can reduce the probability of a 51% attack by increasing the number of confirmations required to withdraw (Binance increases the number of BTG confirmations from 12 to 20 after the attack) .
But of course, this does not completely prevent the attack, but only increases the cost of capital for the attacker. Through careful anomaly detection of low-market-value PoW tokens deposited by users, the exchange can further carry out attack prevention work. Please note, however, that renting hashing power will not cause the hashing power on the chain to decrease in any way. There is no way to detect a 51% attack directly before the attack occurs.

The most recent Bitcoin Gold attack was worth about $ 72,000, but Binance expects to make a profit of $ 429,000 from Bitcoin Gold this year. Similarly, a 51% attack on Ethereum Classic allowed the attacker to make a net profit of about $ 1.1 million, but Binance is expected to earn $ 3.2 million from its transaction fees. This is another reason why tokens do not die after being attacked by 51%.
Even so, the 51% attack is still a mystery. They seem to fundamentally violate the proof-of-work security model. However , cryptocurrencies attacked by 51% will continue to be traded on top exchanges, and after the attack, they can sometimes increase prices strangely (see ETC, BTG and XVG) . We can think of the 51% attack as a tax on exchanges, and we can mimic its inherent motivation to continue trading vulnerable cryptocurrencies, thus partially explaining the phenomenon. But as for why cryptocurrencies that have suffered 51% attacks sometimes rise, unfortunately, this remains a mystery.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- After the epidemic trust crisis broke out: the "anti-epidemic" of the blockchain has just begun
- Babbitt Column | America First? Discrimination of the attitude of the Federal Reserve's two parties to the CBDC
- OKEx announces the destruction of all 700 million OKBs that have not yet been issued, and OKB is up nearly 40%
- Analysis: What caused Bitcoin to soar above $ 10,000 over the weekend?
- Blockchain Weekly Report | New Crown Inspiration: Creating a Blockchain Infectious Disease Early Warning System
- Mutual treasures use blockchain to process New Crown virus claims, can it subvert traditional insurance companies?
- Study | Charities in Epidemic Need Blockchain More





