Without losing control and ownership, can you get rewards through data sharing in the blockchain?
Author / Li Ranhui
Production / Blockchain Base Camp
As of this year, the blockchain industry is continuously developing, and there are some new discoveries and application scenarios. However, in terms of some incentive policies, so far, there is currently no method to track " who is based on what purpose, to whom, when, and what data is shared ", and then give data owners corresponding incentives.
A platform that "allows data owners to control, delete, and reap the benefits of shared data" will be an important driver of user data sharing. So I propose a framework based on blockchain and smart contracts that allows users to store and share data locally without losing control and ownership.
- Multiple Youtube encrypted bloggers deleted a large number of videos without any notice
- Analysis: Why pay attention to the challenge of stable currency to sovereign currency?
- What kind of development will the crypto world usher in in 2020? Talk about three low-key product trends
I. Background
The birth of the Internet is to facilitate users to share data, including centralized (such as FTP) and decentralized ( such as email). In the Web2.0 model that focuses on user participation, it is very easy to share information through social networking sites (Weibo, WeChat, Jianshu and other tools).
In order to profit from business model innovation, some companies are collecting and sharing second-hand data related to users' personal information and behaviors in order to publish personalized advertisements targeted at users based on this information. Many data are provided voluntarily by users, and some data are obtained by the system from observations of user activities, or can be inferred through advanced analysis of voluntarily provided or observed data.
In different areas such as e-commerce, Internet finance, news aggregation, live video streaming, and dating services, data analysis and personalized recommendations have enhanced user interaction with the system and improved the overall quality of services provided to users. Applications that target personalization need to collect information about their users and create predictive models. The process of user modeling requires collecting user data and discovering patterns and similarities between multiple users of the service, or from user interaction. Abstract user characteristics and construct user profiles from the history of
To speed up user understanding, applications can share data about the same user with other applications, which requires sharing user interaction data and user profiles. This sharing has ethical risks and hidden dangers.
Although the "Personal Information Security Specification" issued by the National Information Security Standardization Technical Committee clarified the issues and trade-offs related to user privacy and data control , as well as maintaining fairness while maintaining data richness, these issues have not been addressed accordingly. Implementation of the technical framework and methods.
Especially in the field of scientific research, the practice of research data sharing is very necessary. Sharing research data can reduce repeated experiments and accelerate scientific discovery. In medicine and healthcare, personalized patient care and medical research can benefit from the sharing of patient and clinical trial data under the premise of respecting ethics and protecting privacy.
The mechanisms for obtaining, updating, using, and sharing data need to provide users with appropriate and meaningful incentives to benefit from data sharing and ensure that users know which data has been accessed by whom, for what purpose, and under what conditions.
Currently, there is no single trusted authority to ensure ethical user data sharing. Due to security, centrality, and credibility issues, when a centralized service provider stores and manages all data uniformly, it provides an attack target for hackers, which can easily cause data to be stolen, misused, or sold unethically. Third parties even cause the risk of destruction.
Recently, the Political Bureau of the Central Committee of the Communist Party of China conducted the eighteenth collective study on the current status and trends of blockchain technology development. In the collective learning, he emphasized: "Blockchain should be taken as an important breakthrough in independent innovation of core technology" and "accelerate the development of blockchain technology and industrial innovation." The forward-looking judgment at the highest level allows the "blockchain" to enter the public's perspective again and becomes the focus of common attention of financial capital, the real economy and social public opinion. From the Baidu search index, from the beginning of October to November, the search fever of the term "blockchain" rose rapidly.
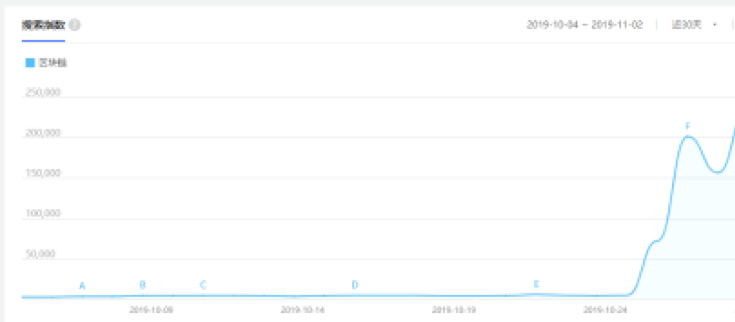
Figure 1. "Blockchain" search popularity
In the past few years, distributed ledger and blockchain technology have developed into a promising technical means, supporting in various use cases such as mutual recognition of medical results, traceability of product production, tax supervision, copyright protection, etc. Immutable and trusted records, the blockchain system provides a "smart contract" technology that allows the establishment of automatic verification of access to or modification of each data entity.
Smart contracts can be deployed to encode allowed data usage purposes, allowed software applications, people or businesses that can access the data, time restrictions, transaction prices, and more. Therefore, the blockchain provides a new type of platform that can be used to share user data-user models and user-contributed data or research data, and provide solutions to privacy, user control, and incentive issues.
Second, the core technology of the blockchain
Distributed ledger technology
Distributed Ledger Technology (DLT) is a data structure used to create a public or private distributed digital transaction ledger, rather than shared with a single provider. Blocks in the blockchain consist of multiple transactions, depending on the size of the block.
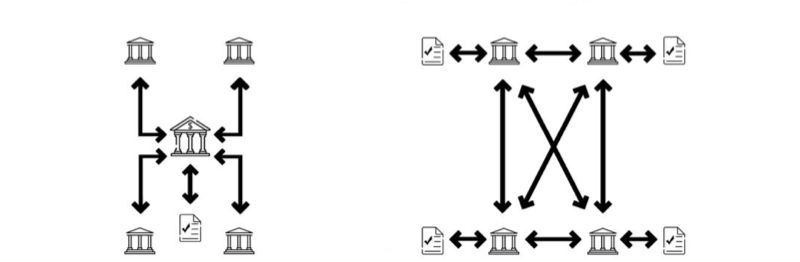
This block contains important information in its block header, such as the hash value of the previous block pointing to the previous block. It is computationally impossible for any damaged node to return and change history. There is no single point of failure in the blockchain because the redundancy of the system guarantees many backups, and the lack of central storage space ensures that hackers have no target. Figure 2 shows the principle of distributed ledger technology on the right, and traditional centralized ledger on the left.
In order to ensure the success of the blockchain platform, incentives play a very important role in encouraging participation . Generally, nodes receive mining rewards for participating in transaction verification activities. In addition, there are some suggestions to use blockchain in combination with access control measures to ensure the privacy of data while sharing off-chain files.
User modeling can benefit from platforms using distributed ledgers and smart contracts to ensure user-controlled privacy and data sharing policies encoded in smart contracts. Compared with centralized systems, blockchain technology is transparent to users, and it is very promising to motivate users to share data .
It also naturally supports the establishment of incentives to encourage users to share their data. In this way, users become the owners of their data and can decide how their data is collected and used, and how this data is shared. In addition, not only benefit from improving the personalized experience of the service, but also directly benefit, for example, a certain share of revenue from the revenue generated by the service provider.
2. Smart contract technology
Smart contracts are examples of contracts deployed on the blockchain, the purpose of which is to design e-commerce protocols between strangers on the Internet. Smart contracts store the following rules: negotiate contract terms, automatically validate contracts, and enforce agreed terms. Smart contracts are composed of different functions, which can be called from outside the blockchain or other smart contracts. The combination of blockchain and smart contract technology eliminates the dependence of both parties on the central system. Since smart contracts are stored on the blockchain, all related parties in the network will own their copies.
Third, the data sharing scheme based on blockchain
Some of the core functions of a system that enables users to store and share data are designed as follows:
1. Reward and punishment mechanism
Reward each participating entity (data owner, data producer, data provider, and data consumer) to perform their duties honestly or punish their malicious behavior.
2. Strict authorization
The system should define access policies and clarify the access rights and privileges of each party involved in the system.
3. Meet the specifications
The system should follow the personal information management specifications to identify and localize all personally identifiable information (PII), classify the data into PII and non-PII, and follow the corresponding data management specifications respectively.
4.Auditable
The system must provide complete auditing capabilities to track the status and path of the data. It should be possible to track every operation performed by the participants.
As mentioned above, blockchain-based solutions inherit key features of the blockchain, such as immutability, decentralized trust, non-repudiation, and availability. To ensure privacy, the solution does not allow any other participants to directly access the data, but instead provides query-based access.
Among them, smart contracts stipulate what kind of conversion is performed on the data to preserve privacy according to the wishes of users, use smart contracts to incentivize data owners to share their data, and ensure the integrity of all participants in the system by forcing participants to provide collateral.
User data is first hashed and encrypted before being uploaded to off-chain storage, and then stored in off-chain storage, or using a trusted system as a gateway assistant to perform this operation. The trusted system runs on the cloud of a trusted execution environment, mainly providing users with computing and key management services, and performing off-chain data operations negotiated by both the data owner and the data consumer.
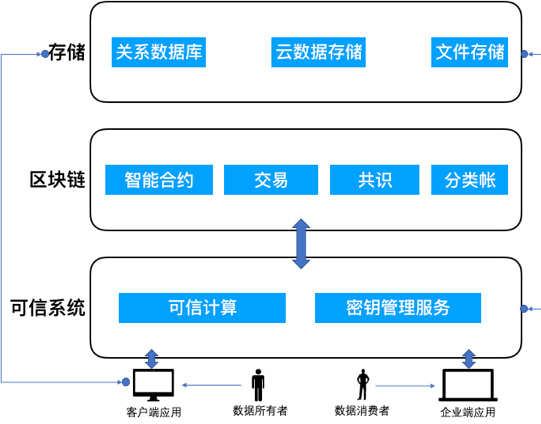
Figure 3. Solution architecture design
Terms and conditions for accessing user data and metadata of the data should be coded together in smart contracts and published on the blockchain platform. Data hashing on the blockchain prevents tampering with the data. When a data consumer calls a smart contract to access user data, only the successful call of the contract can release the key used to decrypt the user data. The trusted system then retrieves the data from off-chain storage, decrypts it, and publishes the data to the data user, while determining the incentives for the data owner.
Blockchain and smart contracts can ensure complete transparency of the people, time, and purpose of accessing their data, allowing users to specify a series of purposes for data sharing, types of data that can be shared, applications that can access data, etc., and follow the contract's Provides payment for use of data.
The blockchain-based data sharing solution provides the underlying off-chain user data storage mechanism, which can be a centralized data storage hosted by a trusted party, or a decentralized platform. In the worst case, centralized storage can be affected by centrality issues, such as deliberate deletion of user data or failure to transfer user data due to technical failure. Therefore, the decentralized transmission mechanism provides a better service, and participating nodes do not have to rely on any separate system to obtain data.
In order to protect user information security, three types of blockchain streams combining symmetric and asymmetric encryption are used. One is a public key stream , which participants use to distribute their public keys under the RSA public key cryptosystem. The second is the Items stream , which is used to publish a large amount of data, and each data is encrypted using a symmetric AES encryption scheme. The last one is an access flow that provides data access. For each participant who should see a piece of data, a flow entry is created containing the data's secret password and encrypted with that participant's public key.
Smart contracts are used to automatically verify the access conditions of each data entity, which naturally also supports the establishment of a reward mechanism to encourage users to share data under the rewarded conditions. Whenever a contract is issued, it becomes part of the transaction on the blockchain and has an address.
Each transaction has a message, which is a container object that can hold metadata. Therefore, another simple contract needs to be created to submit the ID and metadata related to blockchain research to the blockchain. By providing users with transparent contracts with the state, functions, modifiers and events of smart contracts.
When a large amount of data and complex calculations are required, it can be executed in a trusted execution environment, which is constrained by the smart contract on the chain. Once the on-chain smart contract grants permissions, it can remotely authenticate the off-chain trusted execution environment to establish trust.
However, in the trusted execution environment outside the blockchain, there are still some problems in ensuring the credibility of off-chain execution related to contracts, some key technologies have not yet been overcome, and the lack of operating systems, networks, databases, and application software. specifications. Therefore, more work is needed in the future to formulate corresponding mechanisms and standards and make new contributions to this field.
Do you have any idea? Welcome to chat with us in the comments area.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- 8 Questions | Luo Mei, Tsinghua University: The most knowledgeable person in the field of accounting, the most knowledgeable person in the field of blockchain
- Against the halving market, 6500 at the end of this year is 3200 at the end of last year
- Miner prices fluctuate more than currency prices? Two things to understand before understanding the trend
- Dry goods: how to profit by “moving bricks” in the cryptocurrency market?
- Bitmain's three-line axe bets halving the market, and the mining industry behind the gamble needs to turn around?
- Subway Line 1 "Code" is about to open! Lanzhou applies blockchain technology to access two-dimensional code of rail transit
- R3, IBM, JP Morgan Chase grab Singapore, seize new fortress of blockchain trade finance





