Behind the Internet of Things Security: Application and Exploration of Blockchain Technology

With the arrival of 5G, the Internet of Things era will usher in a new outbreak. The cooperation between things and things completely liberates people's hands. The Internet of Things can do a lot of things that humans can't do, more efficient, more convenient, and even safer. As a cutting-edge new technology, blockchain can solve many problems faced by the Internet of Things industry, such as data privacy and data storage security and integrity.
The blockchain technology is applied to the Internet of Things industry, and various innovators are actively exploring. So how can blockchain technology be integrated with the IoT industry? How to solve the security problem of the Internet of Things industry?
On April 11th, Tang Bo, chief scientist of Changhong Information Security Lighthouse Laboratory, Su Xiaokang, head of application research of blockchain of Weizhong Bank, and Yue Liangliang, head of Baosin Chengdu smart contract security, held the “Metroup 2019” event in the Golden Alliance. In the middle, the theme of “ Unlocking the security of the Internet of Things ” is combined with the corresponding practical cases for sharing.
- Interview with everyiToken: The main online line is less than a year, how do we reach cooperation with more than 300 projects?
- Research report | Bitcoin trend is stable, small and medium-sized currencies enter the differentiation adjustment period
- Staking funds are more than 5.6 billion US dollars, the annual income is up to 150%, is your coin "coin"?
IoT security under blockchain

According to reports, the number of global IoT terminals is expected to reach tens of billions in 10 years. By then, the number of devices per capita will reach double digits, and this number will continue to grow. Cooperative interconnection between devices will become more and more important.
Although smart homes can be connected to the Internet, the devices are smart, but the devices are not connected. Another point is that when using voice to interact with each smart device, it must give each device a different name, such as Xiaohong, Xiaobai, Xiaohuang, and if there are more devices, it will be very Convenience.
However, now, solutions such as Xiaomi, Amazon, Google and other well-known companies are based on centralization. Baidu's smart speaker, Xiaomi's Mijia, can control their own devices and devices connected with him. But there is also a problem. For the equipment manufacturer, one of his equipment may need to support the Mijia connection and support Amazon in order to make it sell well. Every support has a cost, and it consumes hard disk memory space. For terminal manufacturers, it faces a big problem. On the one hand, which platform should be supported? On the other hand, the more platforms you need to support, the higher the performance requirements for your hardware, and the manufacturing process for this device is also a challenge.
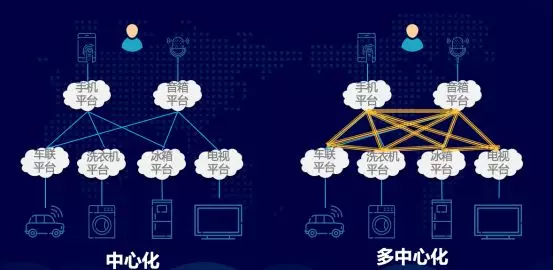
PPT screenshot
Interconnection between devices, the main problem security and trust issues, the relationship between the user and the device, the relationship between the device and the device, requires authentication and authorization mechanisms to protect.
In order to solve the problem of coexistence of multi-platform and multi-terminal in the Internet of Things, the linkage between devices is realized, and the problem of poor user experience is solved. We are the first to propose a cross-platform interconnection scheme based on blockchain. Through the alliance chain, the operational service platforms, regulatory agencies and testing organizations of each device are connected to each other to build a multi-centered core architecture, realize device interconnection and information sharing, and design a set of features of programmable and enforceable smart contracts. The combination of linkage contracts ensures the safe and reliable implementation of all links in the process of equipment linkage, and the fair will reflect the will of all parties.
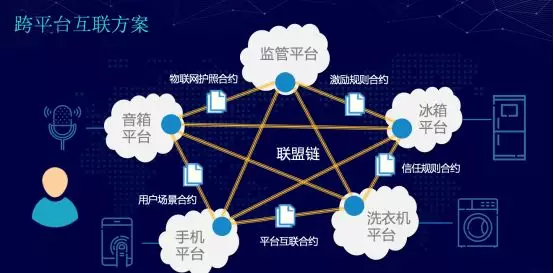
PPT screenshot
Based on such a contract, based on such a user scenario, based on such trust, in the environment of the Internet of Things, the security of an IoT device from one platform to another can be ensured, and at the same time, each platform can be guaranteed. The benefits can be controlled.
Incentive rules are a solution we think of that can guarantee this ecological balance. This program will be motivated in three ways. First, capacity incentives. The computing power of the devices cooperates with each other; second, service incentives. Service import and collaborative drainage provided by the service; third, ecological incentives. The combined ranking of equipment and services.
This is an architecture based on the sensing layer, network layer and application layer of the Internet of Things. Based on this, authentication, authorization and trust, including linkage, grading and synchronization, the upper application will realize resource sharing and realize trust management. security audit. It is worth noting that the lower layer of the alliance chain, we use the blockchain security suite and chip security services, based on these core technologies, improve the security level through hardware, thereby enhancing the reliability of the device certification and authorization process.
Public Alliance Chain Application Exploration – WeIdentity
WeIdentity is a distributed multi-center entity identity authentication and trusted data exchange solution. A distributed multi-center identity identification protocol conforming to the W3C DID specification and a verifiable digital voucher technology conforming to the W3C VC specification are implemented, which not only enables distributed multi-centre identity registration, identification and management, but also through the organization. The user authorizes the legally and compliant completion of the exchange of trusted data.
Now, there is still much controversy about the ownership of data. In fact, we believe that this data belongs to the entity. This entity can be a social person or an IOT device. We all know that there is no value in generating data if it is not in circulation or exchange, but if it is to be circulated and exchanged, can it provide a safe and credible environment, which is a very core goal that this program has to achieve.
Digital identity is also a trend in the future. First, the market demand is very huge . Everyone is paying more and more attention to digital identity, and government agencies and enterprises are promoting digital identity and data exchange in various fields such as government service, financial industry, and Internet of Things. Second, policy encouragement. The Ministry of Industry and Information Technology and government agencies believe that they should form a cross-industry, cross-domain, and cross-regional data application. Third, the industry is in a period of development. From the second half of 2018 to the present, more and more companies and individuals and organizations have begun to invest resources to do digital identity. Fourth, privacy leaks are frequent. Personal privacy data has been abused by some unscrupulous organizations, and it has caused great harm to the public and individuals, but it has also aroused the people's attention to personal privacy data and enhanced the public's awareness of data protection.
At this stage, a large amount of data is not actually circulated and exchanged, forming data islands and data oligarchy.
The traditional data exchange solution, the first is difficult to form an international standard . It is possible that an organization, an enterprise, can easily uniquely identify its users, and assign an ID to the user, but this ID is not an internationally-used ID. Once it is involved in circulation and circulation across organizations, it is very It is difficult to use different scenarios for different industries, lack of standardization, and no international standard.
The second data has a high security risk . In the process of transmitting data and sharing data, the traditional solution generally uses a centralized platform or third-party software, but because of the introduction of a third party, the data is hacked and dragged. The possibility that the library will even be abused by unscrupulous institutions is also high, so its security risk is relatively high.
The third lacks a user authorization system. The traditional B2B data exchange, the user does not have any sense of participation, so the user does not know how to participate in the process of this data exchange.
The fourth is that the credibility of the data is not high. As a recipient of the data, the data issuer gives me the data. How do I judge whether the data is true, whether it has been changed, or whether it is authoritative? Therefore, these four problems are difficult to go with traditional solutions. solved.

PPT screenshot
This program did three very important things. First, features such as entity identification (WeID) are used . A globally unique ID that conforms to the International Code (DID) is generated on the blockchain for each entity (person or object). This is also considering the scalability in the future, a bit similar to the fact that we used a http protocol to make a web page. This page is also subject to international specifications, so that it is very easy to get through other domain name resolution or website service. Business.
Second, verifiable electronic credentials (Credential). Electronically document the paper in the physical world and use the intangible features of the blockchain to wind up the Hash of the original data and attach the signature of the authority (Issuer) to ensure that the data is unforgeable and verifiable .
Third, and very important, is the authorization of the user (Authorization). The cross-institutional transmission of the original data needs to be authorized by the user, and the authorization record is linked by the User Agent, which is in line with the GDPR. By unique ID, similar to the CA certificate, the user can easily put a piece of authorized certificate on the blockchain through the private key signature means, so that the participating organizations of the blockchain can know that the data circulation is legal and compliant. . How to prove that it is the user's authorization? We have a unique logo, the signature of the data can not be forged, this is the three very important things we do in this program.

PPT screenshot
With the advent of the 5G era, the Internet of Things society is constantly upgrading and updating. In addition to people, the source of data generated in the future can generate data. For example, have you encountered some complicated problems in the operation of air-conditioning equipment, whether it has reported some data and whether it is running well. The IOT device itself can generate a lot of data, and the nature of data generation also needs to have a unique ID for each device, so the Internet of Things has a very strong fit with our solution.
Another exploration of our alliance chain is the distributed event-driven architecture – WeEvent
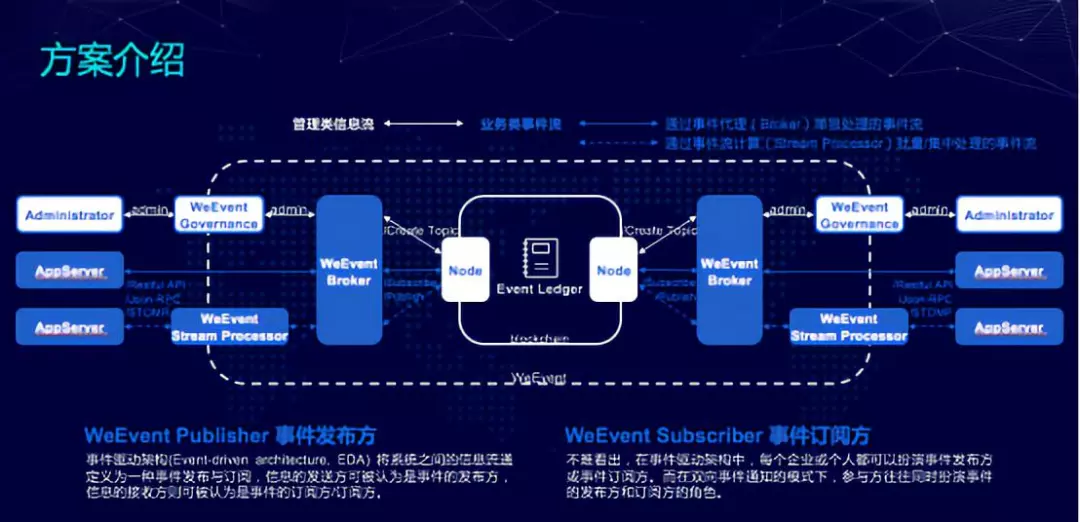
PPT screenshot
WeEvent is an inter-agency, cross-platform event-driven architecture where event publishers interact with event subscribers in an event-driven manner. In addition, WeEvent can be programmablely extended by the stream processor when some complex business logic needs to be processed.
The entire WeEvent solution has great applications in energy, communications, logistics, finance, retail, manufacturing, whether it is industrial IoT or smart home, especially when it comes to intelligent control, and the IOT device itself generates data release events and There are very strong application scenarios in these areas across platforms.
Smart contract security
Blockchain technology uses blockchain data structures to validate and store data, use distributed node consensus algorithms to generate and update data, use cryptography to ensure data transfer and access security, and utilize intelligent script code A new distributed infrastructure and computing method for contracting to program and manipulate data.
The following is a security analysis of multiple levels of FISCO BCOS (2.0) in line with the "full ecological security" service concept:
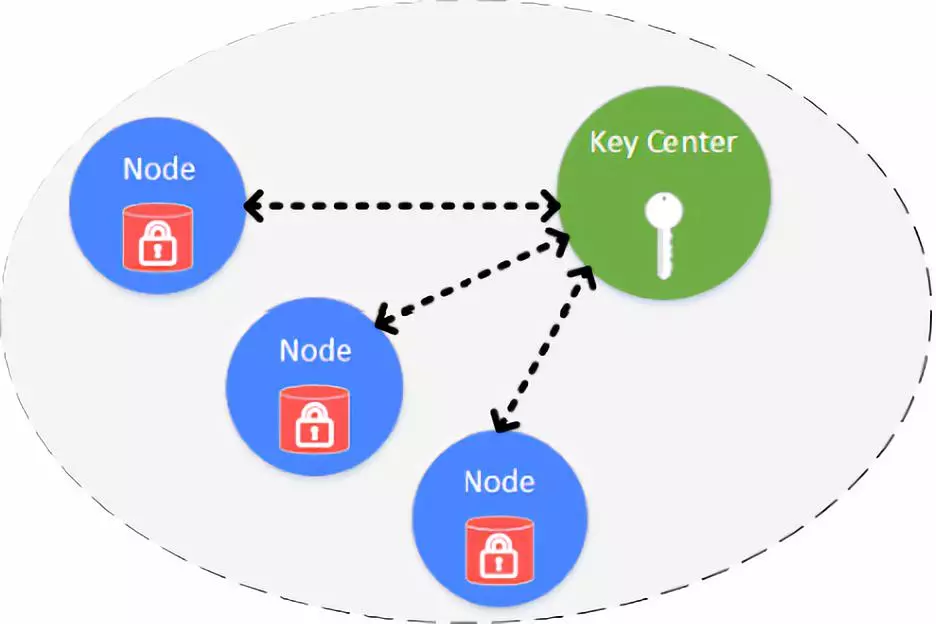
Data layer: Storage of node data. At present, the main application scenarios of the FISCO BCOS chain are the financial and depositing industries, so the storage security and effective confidentiality of data are the key points. The data encryption currently used is mainly: asymmetric encryption, homomorphic encryption; in addition, the corresponding national secret version is specifically released for data encryption.
Data storage inherits Ethereum storage while introducing distributed storage. Part of the data is stored locally to the node by means of a traditional database. Drop-on encryption is done inside the organization. In the organization's intranet environment, each organization independently encrypts the hard disk data of the node. When the hard disk of the machine where the node is located is taken away from the organization and the node is started on a network outside the intranet, the hard disk data cannot be decrypted and the node cannot be started. In turn, the data on the alliance chain cannot be stolen.
PPT screenshot
Network layer: How to interact between nodes and nodes, how to interact between clients and nodes. The FISCO BCOS blockchain is composed of P2P network nodes and mainly uses SSL encryption. The mechanism of single-link multi-books introduces the concept of group, which expands the chain/slave from the storage/execution mechanism of the original one-link book to the storage/execution mechanism of one-chain multi-book, and implements the same chain based on the group dimension. Data isolation and confidentiality. A group mechanism is introduced to subdivide the same blockchain network into different group networks.
Consensus layer: FISCO BCOS currently supports the following two consensus mechanisms:

PPT screenshot
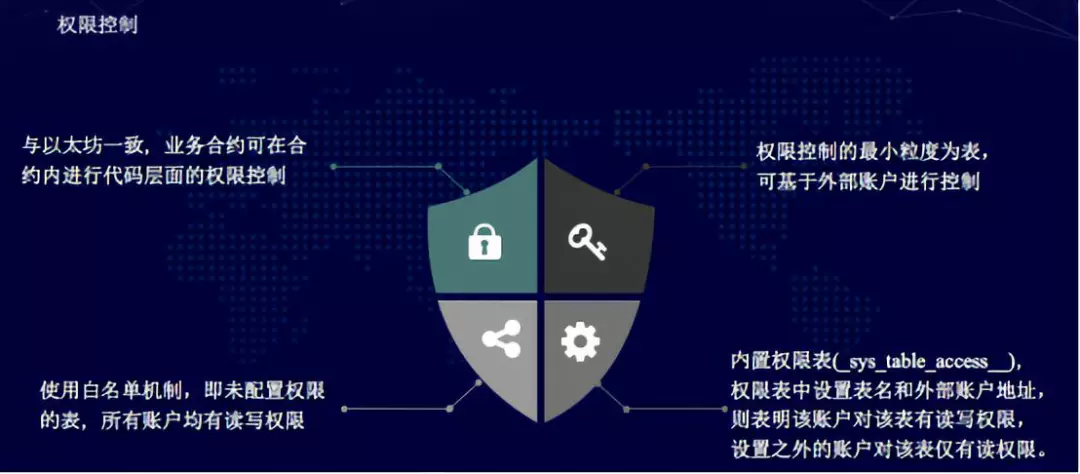
Contract layer: Program code management data. At present, FISCO BCOS uses the Ethereum virtual machine EVM. The current business contract is still mainly based on Solidity.
PPT screenshot
Text: Aubrey
Editor: Wang Qiao
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- The Ethereum Alliance China's first show, all answered questions from all parties
- Haidian District promotes “one network through” by means of blockchain technology
- From Alipay to Chow Tai Fook: What level of blockchain application has it reached in Hong Kong? (with full picture of Hong Kong financial technology companies)
- Twitter selection: Twitter row csw is getting stronger and stronger, cz joins the battle; Youtube first network red stationed in the blockchain live broadcast platform
- Can blockchain technology avoid the recurrence of visual Chinese events?
- People leave money to stay! Xu Xing stepped down as an OKCoin legal person, but still controls nearly 80% of the shares
- Breaking through the blockchain is impossible triangle (2) – an attempt on top of Bitcoin POW