Review of Web3 Blockchain Security Situation and Anti-Money Laundering Analysis in the First Half of 2023, and Summary of Key Regulatory Policies in the Cryptocurrency Industry
Web3 Blockchain Security and Anti-Money Laundering Review and Key Cryptocurrency Regulatory Policies in H1 2023*This report is jointly produced by Beosi n, SUSS NiFT, LegalDAO, Footprint Analytics, Biteye, and ShellBoxes.
Preface
With the accelerated global digitalization process, blockchain technology, as a new decentralized transaction method, is gradually becoming one of the core infrastructure of the digital economy. However, as the application scenarios of blockchain continue to expand, the security risks it faces are also gradually increasing. In this context, understanding the Web3 blockchain security situation and encryption industry regulatory policies has become one of the necessary measures to ensure the security and stability of blockchain applications. This research report is jointly initiated by Beosin, a blockchain security company, and the Blockchain Ecological Security Alliance established by SUSS NiFT. It analyzes and summarizes the global blockchain security situation, Web3 hot events, and key regulatory policies in the encryption industry for the first half of 2023, aiming to provide valuable reference and inspiration to readers and help the safe and healthy development of blockchain technology.
Chapter Author: Beosin Research Team Mario, Donny
- US SEC: How to Use Howey Test to Determine Whether a Cryptocurrency is a Security?
- Viewpoint | BITKRAFT Ventures: How Can Blockchain Games Attract Users?
- Evening Read | Cosmos’ Threat to Traditional Blockchain
1 Web3 Security Situation Overview in the First Quarter of 2023
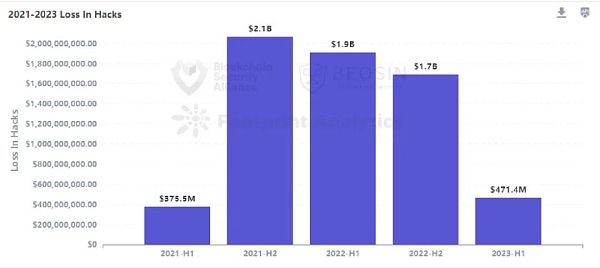
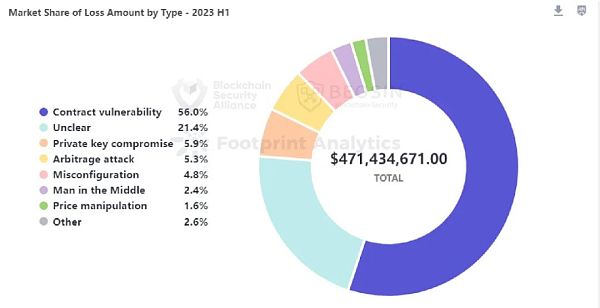
According to the monitoring of Beosin EagleEye security risk monitoring, warning, and interception platform, a subsidiary of blockchain security audit company Beosin, in the first half of 2023, the total losses caused by hacker attacks, phishing scams, and project side rug pulls in the Web3 field reached 655.61 million US dollars. There were 108 attack incidents, with a total loss of about 471.43 million US dollars; phishing scams resulted in a total loss of about 108 million US dollars; there were 110 project side rug pull incidents, with a total loss of about 75.87 million US dollars.

The total amount of losses caused by hacker attacks in the Web3 field has decreased significantly compared to last year. The total loss in the first half of 2022 was about 1.91 billion US dollars, and the total loss in the second half of 2022 was about 1.69 billion US dollars. In the first half of 2023, this value dropped to 470 million US dollars.
From the type of attacked project, DeFi is still the most frequently attacked and highest loss type. 85 DeFi security incidents resulted in a total loss of $292 million, accounting for 62% of the total loss.
From the type of chain platform, 75.6% of the loss amount came from Ethereum, about $356 million, ranking first among all chain platforms.
From the attack method
(according to the root cause), the most frequent and most damaging attack method is contract vulnerability exploitation. 60 contract vulnerability incidents resulted in a loss of $264 million, accounting for 56% of all loss amounts.
From the funding flow perspective, about $215 million of stolen assets have been recovered, accounting for 45.5% of all stolen assets. In addition, about $113 million of stolen assets have been transferred to Tornado Cash and other mixers.
From the audit situation perspective, about 49% of the attacked projects were not audited.
Contrary to the downward trend of hacker attacks in 2022, phishing scams and project Rug Pull events were more frequent in the first half of 2023 for ordinary users. According to incomplete statistics, these two types of events involve a total amount of at least $184 million. Due to the reduced threshold of phishing technology (for example, malicious toolkits can be purchased from phishing gangs through some channels, and profits can be shared after earning), phishing scams have increased significantly in the first half of 2023, becoming the main reason threatening the security of Web3 users.
2 Overview of attack incidents
108 attack incidents caused a loss of $471.43 million
In the first half of 2023, Beosin EagleEye Security Risk Monitoring, Early Warning and Blocking Platform monitored a total of 108 major attack incidents in the Web3 field, with a total loss amount of $471.43 million. Among them, there was 1 security incident with a loss of over $100 million, 7 incidents with losses in the range of $10 million to $100 million, and 23 incidents in the range of $1 million to $10 million.
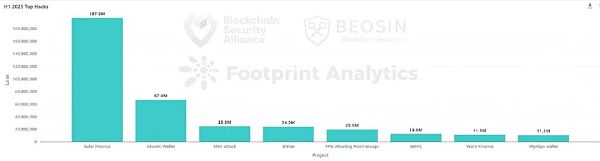
A list of attack events with losses exceeding $10 million (sorted by amount):
● Euler Finance – $197 million
On March 13th, the DeFi protocol Euler Finance was attacked, resulting in a loss of $197 million. On April 4th, Euler Labs announced on Twitter that after successful negotiations, the attacker had returned all stolen funds.
● Atomic Wallet – $67 million
On June 3rd, multiple Atomic Wallet users reported on social media that their wallet assets had been stolen. The stolen amount was found to be at least $67 million. The hacker has laundered the stolen funds through a mixing platform called Sinbad, and the reason for the attack is still under investigation.
● MEV attack – $25 million
On April 3rd, multiple MEV robots were subjected to malicious sandwich attacks, resulting in a total loss of approximately $25 million.
● Bitrue – $24 million
On April 14th, the hot wallet of the cryptocurrency exchange Bitrue was attacked, resulting in a loss of $24 million.
● FPG – $20 million
On June 11th, the cryptocurrency brokerage firm Floating Point Group (FPG) was attacked, resulting in a loss of approximately $20 million in cryptocurrency.
● GDAC – $13 million
On April 9th, the Korean cryptocurrency exchange GDAC was attacked by hackers, resulting in a loss of nearly $13 million.
● Yearn Finance – $11.5 million
On April 13th, Yearn Finance’s yusdt contract was attacked by hackers, resulting in profits of over $10 million for the hackers.
● MyAlgo Wallet – $11.2 million
In February, the MyAlgo wallet was attacked by a man-in-the-middle attack, resulting in a loss of $11.2 million.
3 Types of Attacked Projects
85 DeFi security incidents resulted in losses of $292 million
In the first half of 2023, there were 85 security incidents for DeFi projects, accounting for 78.7% of the total number of incidents. The total amount of losses for DeFi was $292 million, accounting for 62% of the total amount of losses. DeFi is the project type with the highest frequency of attacks and the highest amount of losses.
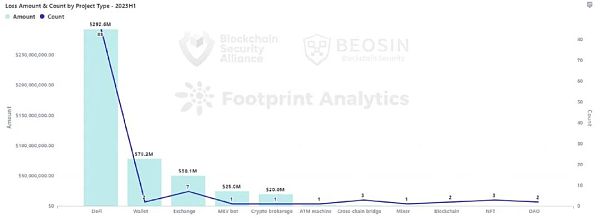
Out of the 85 DeFi security events, 51 were caused by contract vulnerabilities, resulting in losses of USD 249 million, which accounts for 85% of the total DeFi losses.
Wallet attacks caused losses of approximately USD 78.2 million, ranking second among all project types. Among them, the Atomic Wallet attack caused losses of at least USD 67 million, and the MyAlgo Wallet attack caused losses of USD 11.2 million.
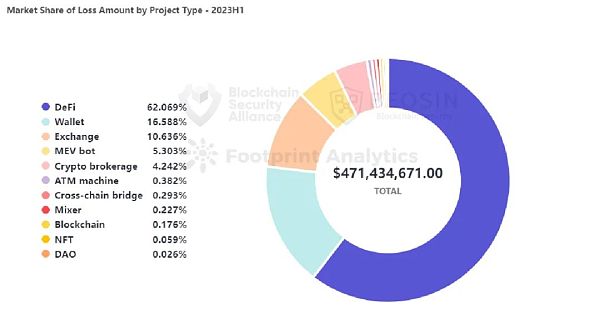
The third-ranked project type is exchanges, with losses of approximately USD 50.14 million. Exchange attacks ranked third in terms of losses in the 2022 data and continued to be frequent this year.
Cross-chain bridge projects ranked first in terms of losses in 2022 (USD 1.89 billion), but in the first half of 2023, losses fell sharply to USD 1.38 million.
4 Losses by different chain platforms
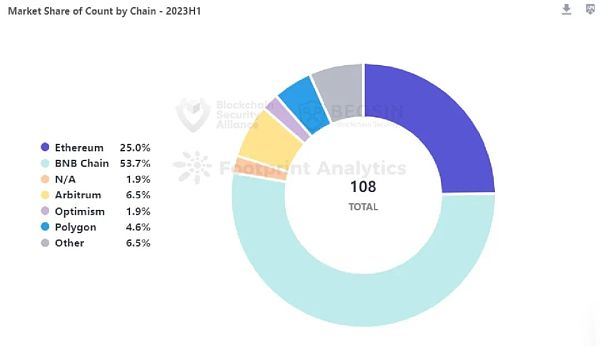
75.6% of losses occurred on Ethereum
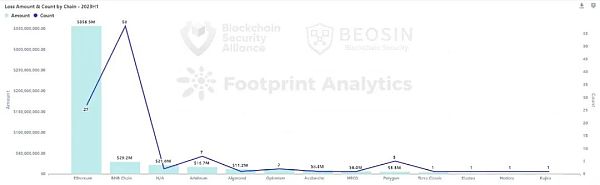
In the first half of 2023, there were 27 major attacks on the Ethereum chain, resulting in losses of approximately USD 356 million. Ethereum chain losses ranked first among all chain platforms, accounting for approximately 75.6%.
The most attacks were detected on the BNB Chain, with a total of 58 attacks, accounting for 53.7% of all events. Among the 58 attacks on the BNB Chain, 40 of the attacked projects were unaudited.
There were a total of 7 attack events on Arbitrum chain, resulting in losses of approximately USD 16.71 million. The number and amount of security events on the Arbitrum chain increased compared to 2022 (Arbitrum only had two major security events in the entire 2022).
Solana chain ranked third in terms of losses on all public chains in 2022, but no major attack events were detected in the first half of 2023.
5 Attack method analysis
Contract vulnerabilities are the most frequent and costly
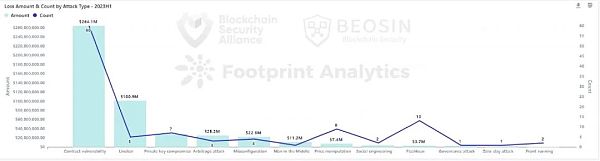 *Note: When multiple attack methods coexist, the classification is based on the root cause. Attack events with insufficient information or undisclosed reasons are classified as “unclear.”
*Note: When multiple attack methods coexist, the classification is based on the root cause. Attack events with insufficient information or undisclosed reasons are classified as “unclear.”
In the first half of 2023, the most frequent cause of attack and the most damaging attack technique was the exploitation of smart contract vulnerabilities. 60 smart contract vulnerability incidents caused losses of $264 million, accounting for 56% of all losses.
Approximately $100 million of security events involve unclear attack techniques, including incidents such as the Atomic Wallet being stolen $67 million and the cryptocurrency brokerage company FPG being attacked $20 million. These incidents involve large amounts of money and affect many users. It is recommended that project parties actively cooperate with third-party security companies to publish investigation results in a timely manner and take necessary repair measures to shoulder the responsibility for user asset security while investigating the cause of events.
In addition, there were 7 incidents of private key leaks causing losses of about $27.67 million. In 2022, private key leaks were also the third highest of all attack types. Private key leaks have always been a threat to project security. From the disclosure of some events, it is particularly important to strengthen the professional ethics and security awareness management of core members.
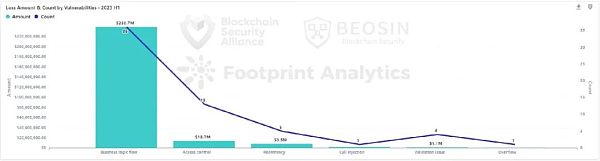
By vulnerability type, the top three causes of loss were business logic flaws, permission issues, and reentry. 36 business logic vulnerabilities caused about $239 million in losses, accounting for 90% of all losses due to smart contract vulnerabilities. Such vulnerabilities are the easiest problems for developers to overlook and the losses caused after being attacked are often large. The losses of 9 incidents exceeded $1 million. It is recommended that project parties seek experienced professional auditing companies for auditing.
6 Typical Case Attack Technique Analysis
6.1 Euler Finance Security Incident
On March 13, Euler Finance, a lending project on the Ethereum chain, was attacked by flash loans, resulting in a loss of $197 million.
On March 16, the Euler Foundation offered a reward of $1 million to collect information helpful to the arrest of the hacker and the return of stolen funds.
On March 17, Michael Bentley, CEO of Euler Labs, tweeted that Euler “has always been a project with a strong sense of security.” From May 2021 to September 2022, Euler Finance accepted 10 audits from 6 blockchain security companies, including Halborn, Solidified, ZK Labs, Certora, Sherlock, and Omnisica.
From March 18th to April 4th, the attacker began returning funds one after another. During this period, the attacker apologized through on-chain information, saying that they “disrupted someone else’s money, work, and life” and asked for everyone’s forgiveness.
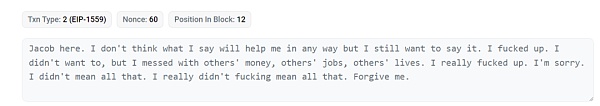 On April 4th, Euler Labs announced on Twitter that, after successful negotiations, the attacker had returned all the stolen funds.
On April 4th, Euler Labs announced on Twitter that, after successful negotiations, the attacker had returned all the stolen funds.
Vulnerability analysis: What insights does the Euler Finance $200 million theft case provide us with?
6.2 BonqDAO Security Incident
On February 1, the crypto protocol BonqDAO was attacked by a price manipulation attack. The attacker minted 100 million BEUR tokens and then exchanged them for other tokens on Uniswap, causing the price of ALBT to drop to almost zero, which further triggered the liquidation of the ALBT treasury. According to the token price at the time of the hack, the loss was as high as $88 million, but due to liquidity exhaustion, the actual loss was around $1.85 million.
Vulnerability analysis: Analysis of the largest hacker incident at the beginning of the year, the attack on crypto protocol BonqDAO
6.3 Platypus Finance Security Incident
e Safety Incident
On February 17th, Platypus Finance on the Avalanche platform was attacked due to issues with the function check mechanism, resulting in a loss of approximately $8.5 million. However, the attacker did not implement the withdrawal function in the contract, resulting in the attack proceeds being stored in the attack contract and unable to be withdrawn.
On February 23rd, Platypus stated that they had contacted Binance and confirmed the attacker’s identity, and stated that they would refund at least 63% of the funds to users.
On February 26th, the French national police arrested and summoned two suspects who attacked Platypus.
Vulnerability analysis: How to prevent flash loan attacks? Analysis of the $8.5 million attack on the Avalanche-based Platypus project
6.4 Yearn Finance Security Incident
On April 13, 2023, Yearn Finance’s yusdt contract was attacked by a flash loan attack, and the hacker made over $10 million in profit. yUSDT was likely misconfigured when it was deployed over 1,000 days ago, mistakenly using Fulcrum iUSDC deployment instead of Fulcrum iUSDT.
On May 26, the Yearn attacker transferred 4,134 ETH to Tornado Cash.
Vulnerability analysis: How did Yearn Finance become a target for hackers, resulting in the theft of over $10 million?
7 Typical Anti-Money Laundering Event Analysis Review
According to Beosin EagleEye Security Risk Monitoring, Warning and Blocking Platform, a blockchain security audit company, Atomic Wallet was attacked in early June this year, and according to the statistics of the Beosin team, the losses caused by this attack were at least about $67 million based on the known victim report information on the chain.
We will delve into the details of the money laundering in this hacker theft case, and use Beosin KYT virtual asset anti-money laundering compliance and analysis platform to track and analyze the hacker’s money laundering tricks.
Incident Overview
According to the Beosin team’s analysis, the chains involved in the stolen event so far include a total of 21 chains, including BTC, ETH, and TRX. The stolen funds are mainly concentrated on the Ethereum chain. Among them:
Ethereum chain
The stolen funds have been found to be 16,262 ETH worth of virtual currency, about $30 million.
Tron chain
The stolen funds known on the Tron chain are 251,335,387.3208 TRX worth of virtual currency, about $17 million.
BTC chain
The stolen funds known on the BTC chain are 420.882 BTC worth of virtual currency, equivalent to $12.6 million.
BSC chain
The stolen funds known on the BSC chain are 40.206266 BNB worth of virtual currency.
Other chains
XRP: 1,676,015 XRP, about $840,000
LTC: 2,839.873689 LTC, about $220,000
DOGE: 800,575.67369797 DOGE, about $50,000
Ethereum
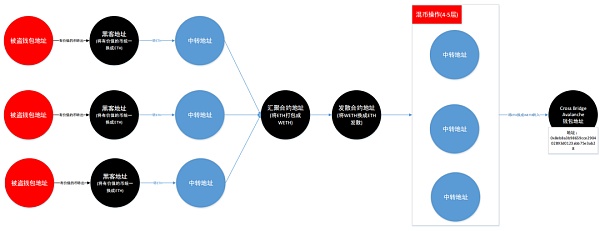
In the hacker’s operation on the stolen money, there are two main ways on the Ethereum attacked chain:
1. Use the contract to diverge and then use Avalanche to launder money across chains
According to the Beosin team’s analysis, the hacker will first unify the valuable coins in the wallet into the main coins of the public chain, and then use two contracts to collect them.
The contract address will package ETH into WETH through two layers of transfer, and then transfer the WETH to the contract used to diverge ETH. It will transfer to the wallet address used for cross-chain operation in Avalanche through up to 5 layers of transfer. This cross-chain operation does not use a contract and belongs to Avalanche’s internal accounting transaction type.
The schematic diagram of the Ethereum link is as follows:
Read the full article: A wallet theft case involving at least $60 million, Beosin KYT takes you through the hacker’s money laundering routine
8 Analysis of the flow of stolen assets
45.5% of stolen assets were recovered
In the first half of 2023, Beosin KYT’s virtual asset anti-money laundering compliance and analysis platform showed that about $215 million of stolen assets were recovered, accounting for 45.5% of all stolen assets. In 2022, only 8% of stolen assets were recovered. The chance of recovering funds increased significantly in 2023. In addition to negotiating with hackers to recover them, cases of recovering funds through security companies, law enforcement agencies, and community efforts are increasing. In addition, the improvement of the global regulatory system and the increase in law enforcement efforts have also played a deterrent role in hacker behavior.
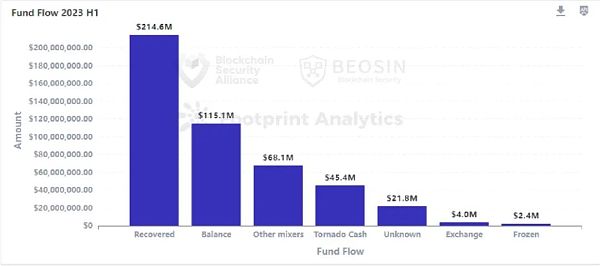
About $113 million of stolen assets were transferred to the mixer. Among them, about $45.38 million was transferred to Tornado Cash, and about $68.14 million was transferred to other mixing platforms. Since Tornado Cash was sanctioned by the US OFAC in August 2022, the total amount of money used by hackers for mixing with Tornado Cash has decreased significantly, and the usage rate of other mixing platforms has increased significantly, such as FixedFloat, Sinbad, etc.
9 Analysis of project audit situation
The proportion of audited and unaudited projects is roughly the same. Among the 108 attacked projects, 51 were audited and 53 were unaudited, roughly the same proportion. This ratio is also roughly the same as in 2022.
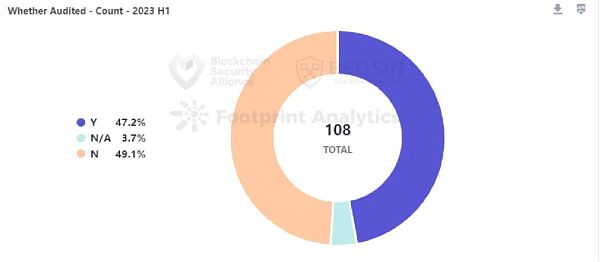
Among the 51 audited projects, 31 projects (60%) were attacked due to contract vulnerabilities. This ratio is higher than last year’s 45%, and the quality of the entire audit market is still not optimistic. It is recommended that project parties must find professional security companies for auditing.
10 Rug Pull Analysis
110 Rug Pull incidents took away $75.87 million in the first half of 2023 in the Web3 field.
From a monetary perspective, 14 Rug Pull incidents (12.7%) involved amounts over $1 million, a total of 41 incidents (37.3%) occurred in the range of $100,000 to $1 million, and 55 incidents (50%) involved amounts less than $100,000.
The largest Rug Pull incident in terms of amount was the Fintoch project, which took away approximately $31.6 million in assets.
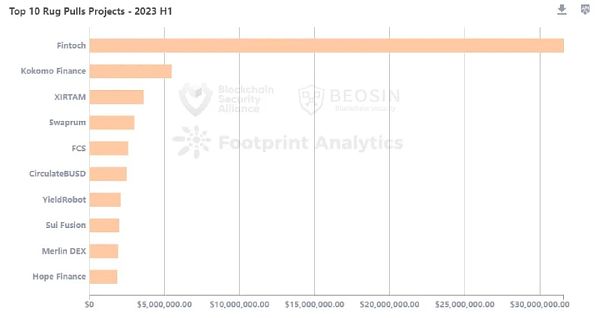
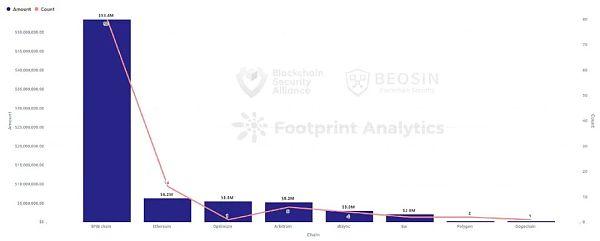
From the perspective of blockchain platforms, 80 Rug Pull incidents occurred on the BNB chain, involving $53.37 million, significantly higher than other public chains.
2023 H1 Security Situation Summary
Overall, the total amount lost in Web3 field hacking incidents in the first half of 2023 decreased significantly compared to 2022. In the first half of 2022, the total loss from attacks was approximately $1.91 billion, and in the second half of 2022, it was approximately $1.69 billion. However, this figure decreased to $470 million in the first half of 2023, and approximately $215 million of stolen assets were recovered. The trend of hacking attacks is showing a significant slowdown, with the main reasons being the gradual improvement of global regulatory systems, increased law enforcement, improved security awareness of project parties, sanctions against mixer Tornado Cash, and the improvement of AML anti-money laundering technology and procedures. In addition, cases have occurred where community forces have been used to locate hacker identities through off-chain intelligence and force them to return stolen assets.
Even with a significant slowdown in hacking attacks, contract security issues cannot be ignored. In the first half of 2023, the most frequent and damaging attack method was exploiting contract vulnerabilities. 60 contract vulnerability incidents caused losses of $264 million, with the majority of vulnerabilities exploited being business logic issues. Some more complex business logic vulnerabilities require experienced professional audit companies to discover. The Beosin audit team conducts in-depth analysis of every hacking attack incident (Twitter @BeosinAlert), ensuring that the experience and technology summarized from these incidents are applied to the project audit process to deal with possible hacking attacks.
Contrary to the trend of decreasing hacker attacks, phishing scams against ordinary users are becoming more frequent. In the first half of the year, a series of wallet drainer groups led by Venom Drainer appeared. They developed malicious toolkits for sale and shared profits with buyers after successful phishing scams. Such phishing scams have a wide range of impact on users, with at least 15,000 victims from just the Venom Drainer group alone. For ordinary users, it is best to pay attention to security company alerts, systematically learn some knowledge of anti-phishing and anti-theft, and install some anti-phishing plug-ins, transaction pre-execution tools, etc. for reminders (but cannot rely solely on tools, strengthening their own security awareness is always the first priority).
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ethereum EIP Review: How Does the Ethereum Community Conduct Open Governance?
- Exploring Interoperability of Modular Blockchain: What Are the Solutions?
- Can AI Trigger the Fifth Technological Revolution? (Part 2)
- Comprehensive Explanation of the Shoal Framework: How to Reduce Bullshark Latency on Aptos?
- Financing Weekly Report | 18 public financing events; Gensyn, a blockchain-based AI computing protocol, completes $43 million in Series A financing, led by a16z.
- Blockchain Capital: Looking Ahead to the “Consumer Era” of Cryptocurrencies
- AI in the Web3 Era: Exploring the Infinite Potential of Blockchain and Artificial Intelligence






