Assessment of the Decentralization Level of the Top 5 PoS Public Chain Validators
Assessing the Decentralization of Top 5 PoS Public Chain ValidatorsAuthor: Stephanie Dunbar, Messari Asset Diligence team; Translator: Blocking0xxz
Key takeaways:
-
Decentralization of PoS network operation can be evaluated through the geographic distribution of validators and staked assets across jurisdictions, node hosting infrastructure, and underlying software components.
-
Well-distributed variables and a more decentralized network are better equipped to withstand buggy code, political and corporate hostility, and physical infrastructure failures.
-
Standardized metrics like the Nakamoto coefficient help measure the degree of decentralization at a given point in time. But to understand the full picture, it’s important to qualitatively analyze factors that lead to concentration of stake and a network’s ability to recover from large-scale infrastructure failures.
-
Among all analyzed networks, Avalanche, Cardano, NEAR, Solana, and Aptos have significant room for improvement in enhancing long-term reliability and resilience.
When validators are well-distributed and decentralized, PoS networks are better equipped to withstand unexpected failures or adversarial attacks. This requires a sufficient number of untrusted operators distributed in a non-correlated environment. “Environment” includes the physical location of validators as well as the hardware and software components used to connect to the network. Any one common infrastructure failure in these variables that affects a large number of validators could cause an interruption, and with increasing severity, even completely compromise the network.
Operational decentralization refers to the geographic distribution of network validators and staked assets across jurisdictions, node hosting infrastructure, and underlying software components. Well-distributed variables and a more decentralized network offer several key benefits.
First, it enhances security by minimizing the risk of a single vulnerability or attack vector affecting critical parts of the network. Second, it improves network robustness by reducing the impact of local issues like regulatory action or infrastructure failures. Finally, it increases reliability. It signals that the network is able to withstand potential challenges and threats, thus contributing to its trustworthiness.
As a result, multiple generic Layer 1s with different architectural designs have emerged, each attempting to strike a balance between security, availability, and scalability. However, each different design inevitably faces trade-offs that impact its degree of decentralization. These design differences make surface-level comparative analysis of Layer 1 decentralization inherently challenging. To evaluate decentralization, standardized models must be sought and unique parameters of each network must be controlled.
Balaji and Lee’s early work established the standard for quantifying decentralization in a quantitative decentralization setting – the Nakamoto coefficient – a method for measuring the minimum number of entities required to disrupt a blockchain network subsystem. However, the initial calculation and parameters of the Nakamoto coefficient need to be updated to consider the consensus rules of Proof of Stake (PoS) networks and specifically focus on decentralized operation. In addition, there are some exogenous factors that can lead to concentration of staking and the network’s ability to recover from large-scale infrastructure failures.
This report aims to set new standards for measuring the distribution of validators and staking across infrastructure components. Based on the survey results, the report aims to provide actionable recommendations to support the decentralized operation of public PoS networks.
The Role of Validators
To measure the degree of decentralization of operations in a PoS system, it is necessary to first understand the core concepts of how validators operate and the factors that affect their operation and location.
Validators act as the backbone of a global compute platform, executing, validating, and recording transactions for permissionless user networks. They reach consensus on the state of the blockchain, which represents the network’s transaction history. To add blocks to the chain, the threshold of validators must agree. This ensures Byzantine fault tolerance, enabling the network to function even if some nodes behave dishonestly or fail. However, the activity, finality, and security thresholds of each network will ultimately differ based on its specific consensus algorithm and implementation.
 To facilitate network operation, validators lock or “stake” native assets of the network. This collateral serves as a security measure and can be deducted (“slashed”) to prevent behavior that is not in the best interest of the network. Such behavior includes poor performance (such as excessive downtime) or malicious behavior (such as attempting to generate invalid blocks). Validators receive a portion of user fees and network inflation as compensation for their services, depending on the network.
To facilitate network operation, validators lock or “stake” native assets of the network. This collateral serves as a security measure and can be deducted (“slashed”) to prevent behavior that is not in the best interest of the network. Such behavior includes poor performance (such as excessive downtime) or malicious behavior (such as attempting to generate invalid blocks). Validators receive a portion of user fees and network inflation as compensation for their services, depending on the network.
How Network Design Affects Operational Decentralization
While there are many subtle differences that affect operational decentralization, some key factors include:
-
Hardware and upfront capital requirements: The hardware cost of hosting nodes and the minimum staking amount required to operate validators profitably.
-
Ongoing operating expenses: The ongoing resource consumption and maintenance costs of validators.
-
Built-in delegation mechanisms: Whether token holders can stake to existing validators.
-
Active Validator Set Caps: A network constraint that limits block production to validators with the highest risk.
For example, expensive capital requirements and resource-intensive physical infrastructure may become barriers to entry, reducing operator diversity but ensuring efficient operations. Resource-intensive networks like Solana, with proven high TPS processing capabilities, and sharded networks like NEAR may require heavier infrastructure. As resource demands increase, validator operators may prefer the convenience of running nodes on hosted server solutions rather than purchasing and managing dedicated infrastructure locally.
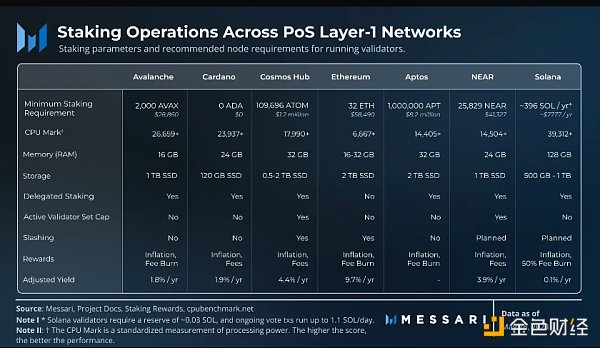 To increase stake participation, most networks adopt a delegation staking mechanism that allows users to submit stakes to existing validators rather than running their own validators. More stake allows validators to produce blocks and increase the chances of earning rewards for themselves and their delegators. However, the more stake validator operators attract, the greater the risk to the network if the validator fails. Networks like Cardano implement a pool saturation mechanism where validators attract over 70 million ADA to begin reducing their potential rewards. However, this does not prevent operators from running multiple validators, often using the same infrastructure. While Ethereum does not provide in-protocol delegation staking, this is similar to operators running multiple validators in increments of 32 ETH as defined.
To increase stake participation, most networks adopt a delegation staking mechanism that allows users to submit stakes to existing validators rather than running their own validators. More stake allows validators to produce blocks and increase the chances of earning rewards for themselves and their delegators. However, the more stake validator operators attract, the greater the risk to the network if the validator fails. Networks like Cardano implement a pool saturation mechanism where validators attract over 70 million ADA to begin reducing their potential rewards. However, this does not prevent operators from running multiple validators, often using the same infrastructure. While Ethereum does not provide in-protocol delegation staking, this is similar to operators running multiple validators in increments of 32 ETH as defined.
In addition, networks with a capped set of active validators limit active validators to those with the highest staking weight. This is to ensure that only the best-performing validators participate in network operations, but in practice, this often results in a monopoly of active validators with social capital, making it unprofitable or impractical for operating validators. For example, to participate in the active validator set for the Cosmos Hub, validators must own or attract nearly 110,000 ATOM tokens, equivalent to around $1.2 million at current prices.
Therefore, operating in a decentralized manner is very subtle; many factors determine who runs validators, where they run, and how they run. Some networks can be highly decentralized in one vertical while less so in other verticals. Standardized metrics like the Nakamoto coefficient help aggregate the operational decentralization between validator infrastructure and operational variables.
Beyond Satoshi: Measuring Decentralization in Operations
Method
Infrastructure centralization, validator distribution, and stake distribution all play a critical role in assessing the degree of decentralization in a network’s operations. To establish standardized baseline measurements, stake and validator distribution are evaluated across the following basic variables or “subsystems”:
-
Node software (client)
-
Node-hosting infrastructure
-
Geographic location
In the context of a PoS consensus algorithm, requirements for finality, security, and liveness are typically expressed as a percentage of total stake rather than the number of validators. As such, the Nakamoto coefficient for each subsystem is measured by stake weight.
The Satoshi coefficient defines the “operational threshold” as the percentage of failed stake required to compromise the network. In most PoS-based systems, when more than 33.3% of stake is compromised, it impacts the network’s robustness and fault tolerance. It becomes unstable and, in most cases, stops, losing liveness and finality (except for Ethereum, which remains alive at up to 50% faulty validators). It is important that the network always operates with over 2/3 of effective stake to ensure resilience against potential security issues and maintain overall network stability. Hence, 33.3% is used as the standard PoS operational threshold.
The Satoshi coefficient for a subsystem in which stake concentration exceeds 33.3% in a particular region is 1, as the failure of a single element would jeopardize the entire system. The higher the operational Satoshi coefficient, the greater the network’s resilience to potential infrastructure failures.
For Avalanche, Cardano, NEAR, Solana, and Aptos, a comprehensive “Operational Satoshi coefficient” will be calculated based on each network’s stake distribution across software clients, node-hosting infrastructure, and geographic location. General observations will be made for other well-known networks where applicable. The Operational Satoshi coefficient serves as the fundamental baseline measure representing the basic subsystems that represent decentralization in operations, but additional analysis is necessary to account for other interrelated variables.
Qualitative considerations
There are various other variables that can affect the degree of operation and overall decentralization of a network. Operational decentralization is not something that exists just on its own. These variables include the distribution of token ownership, operator staking, and developer activity, among others.
For example, if the network goes down and validator clients need maintenance to restart, operational decentralization will be defined by how many people are able to (are permitted to) and equipped (are experienced enough) to address the issue. Their location also helps to define the operational decentralization in terms of availability response when the network is compromised. The concentration of operator staking determines the degree to which a single entity can impact the network’s operation. If dominant operators with the same infrastructure hold a significant amount of stake, it directly affects the concentration of the infrastructure.
Other fundamental variables and factors that contribute to operational decentralization were also considered when analyzing the Satoshi coefficient for each network.
Considerations
For the current analysis, the method used provides a snapshot of each network at a given point in time. While the validator infrastructure won’t change quickly under normal circumstances, it will naturally evolve over time in response to protocol-internal and external factors. Additionally, sentinel or private node architectures, VPN usage, or IP-mixing services of operators may obscure the true location of validators. Therefore, the accuracy of hosted location and geographical distribution data will be impacted.
Finally, the ability of a network to recover after critical infrastructure failures is still not measurable. For example, stake migration may be more easily executed in response to such events for networks with simpler operational requirements.
Analysis Results
Client Diversity
A validator client is specific software that node operators run to facilitate network operation. It is essentially an application that connects operators to the network. Multiple implementations can be developed, each with different architectures and features. Diverse clients can make blockchains more accessible and user-friendly to meet different preferences. This concept is similar to email services like Gmail and Outlook, which utilize different clients to connect to email protocols like SMTP, IMAP, and POP3.
In the probabilistic world, the more diversity there is at the client level, the less likely a single code error or malicious attack will impact a large number of validators. Additionally, different implementations provide varying levels of performance optimizations, allowing node operators to choose the client that best suits their needs and hardware capabilities. This can lead to a more efficient and faster network overall.
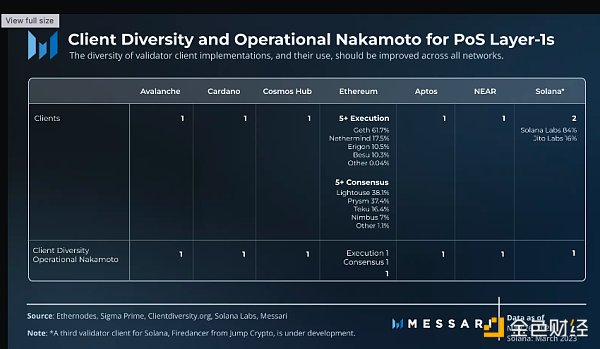 Most networks have a single point of failure at the basic software level, and only one validator client implementation exists for Avalanche, Cardano, Cosmos Hub, Flow, NEAR, and Aptos. Ethereum separates execution and consensus into two independent clients, each with a large number of developed and used implementations. Solana currently has two validator clients, with a third one in development. Despite the selectivity of these networks, there is still a significant degree of centralization.
Most networks have a single point of failure at the basic software level, and only one validator client implementation exists for Avalanche, Cardano, Cosmos Hub, Flow, NEAR, and Aptos. Ethereum separates execution and consensus into two independent clients, each with a large number of developed and used implementations. Solana currently has two validator clients, with a third one in development. Despite the selectivity of these networks, there is still a significant degree of centralization.
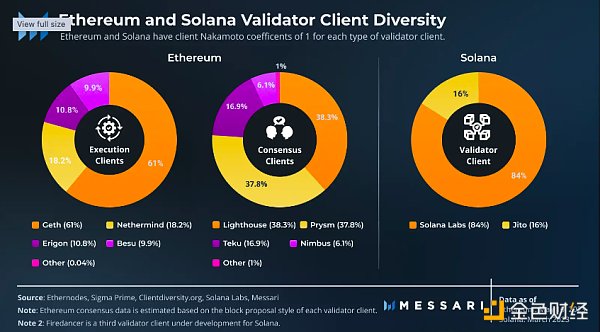 For Ethereum, most validators use Geth as the execution client, accounting for about 62% of the execution clients. Lighthouse and Prysm are the main consensus clients, accounting for about 38% of the consensus clients. Historically, Prysm has always been the dominant consensus client with a greater advantage, so the diversity of consensus clients has improved over time. Client centralization leads to instability in the PoS Ethereum network, with both before and recently when Prysm and Teku caused finality of the beacon chain to be lost for several epochs over two days. Ethereum is unique compared to most other networks in that its activity remains despite over 33.3% of damaged validators losing finality.
For Ethereum, most validators use Geth as the execution client, accounting for about 62% of the execution clients. Lighthouse and Prysm are the main consensus clients, accounting for about 38% of the consensus clients. Historically, Prysm has always been the dominant consensus client with a greater advantage, so the diversity of consensus clients has improved over time. Client centralization leads to instability in the PoS Ethereum network, with both before and recently when Prysm and Teku caused finality of the beacon chain to be lost for several epochs over two days. Ethereum is unique compared to most other networks in that its activity remains despite over 33.3% of damaged validators losing finality.
On the other hand, Solana has experienced multiple serious crashes and shutdowns, partly due to its reliance on a single validator client developed by Solana Labs. In response, the Solana community forked the Solana Labs client to create the self-maintained Jito Labs client. Jump Crypto is also developing a third client, Firedancer. It is worth noting that these clients will have built-in fault-tolerance mechanisms that allow validators to switch to another client if one does not respond. This feature should help improve the future network reliability of Solana.
The Satoshi Operating Index of Client Distribution
In all analyzed networks, the Satoshi Operating Index of client distribution is 1, indicating that over 33.3% of the stake runs on a single validator client for each network.
Hosting Distribution
In almost all analyzed networks, the vast majority of validators and stakes run on hosted server solutions. This can be attributed to the convenience of professionally managed infrastructure and the difficulty of self-hosting validators due to high infrastructure and operational requirements. Validator operators prioritize cost-effectiveness by running nodes on hosted servers, where they can take advantage of economies of scale and reduce operating costs.
While this approach is practical for many networks, concentrating nodes and staking on a limited number of infrastructure providers increases sensitivity to single points of failure and increases the risk of vendor lock-in. Currently, dominant cloud providers AWS, OVH Cloud, Hetzner, and Google Cloud represent the majority of staking for most networks analyzed. Considering the current distribution of staking among providers when launching validators can help reduce concentration risk.
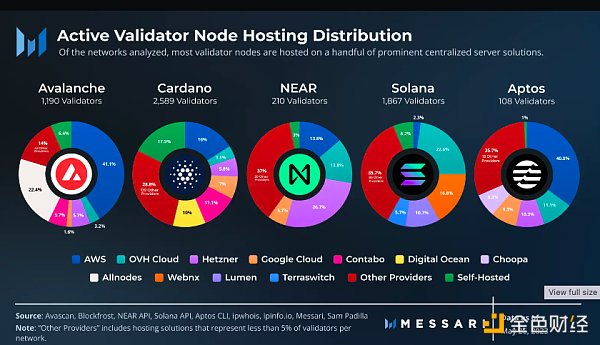 Among the networks analyzed, Cardano has the lowest reliance on hosted server solutions, which may be due to its lower upfront costs to run a validator, making it more affordable to run a validator from home. Notably, 452 validators (17.5% of Cardano validators) are self-hosted, connected to the network through 183 different internet service providers (ISPs). While we did not identify a representative sample of Ethereum validators, we identified at least 1,679 self-hosted Ethereum validators distributed across over 300 different ISPs.
Among the networks analyzed, Cardano has the lowest reliance on hosted server solutions, which may be due to its lower upfront costs to run a validator, making it more affordable to run a validator from home. Notably, 452 validators (17.5% of Cardano validators) are self-hosted, connected to the network through 183 different internet service providers (ISPs). While we did not identify a representative sample of Ethereum validators, we identified at least 1,679 self-hosted Ethereum validators distributed across over 300 different ISPs.
In terms of staking distribution, Cardano’s 17.5% self-hosted validators account for only about 6% of staked ADA. Nonetheless, it is still the network with the most self-hosted staking among those analyzed. It is also the network with the most diverse set of non-dominant node hosting providers, with 143 identified providers representing over 25% of staked ADA.
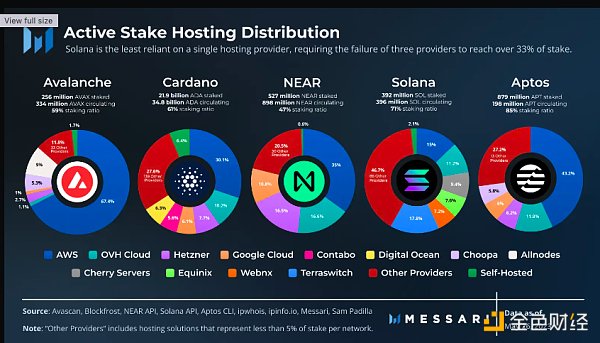 Solana has the lowest reliance on mainstream server solutions, with over 70% of staking hosted by non-mainstream providers. This is in stark contrast to all other networks, which rely on AWS, OVH Cloud, Hetzner, and Google Cloud and have approximately 55% and 80% of staked tokens hosted on those clouds, respectively. This may be attributed to Solana’s use of high-performance bare-metal servers, which require dedicated hardware for higher throughput over traditional cloud solutions that are shared with other users. Notably, Solana nodes were previously heavily hosted on Hetzner, but all active Solana validators migrated away from Hetzner after its announcement to ban crypto in August 2022. Hetzner remains a prominent hosting solution for NEAR, Cardano, and Aptos, representing 16.5%, 7.7%, and 6.2% of staked tokens for these networks, respectively.
Solana has the lowest reliance on mainstream server solutions, with over 70% of staking hosted by non-mainstream providers. This is in stark contrast to all other networks, which rely on AWS, OVH Cloud, Hetzner, and Google Cloud and have approximately 55% and 80% of staked tokens hosted on those clouds, respectively. This may be attributed to Solana’s use of high-performance bare-metal servers, which require dedicated hardware for higher throughput over traditional cloud solutions that are shared with other users. Notably, Solana nodes were previously heavily hosted on Hetzner, but all active Solana validators migrated away from Hetzner after its announcement to ban crypto in August 2022. Hetzner remains a prominent hosting solution for NEAR, Cardano, and Aptos, representing 16.5%, 7.7%, and 6.2% of staked tokens for these networks, respectively.
Compared to the distribution of validators, Avalanche, Cardano, and NEAR have more concentrated staking. Except for Avalanche and Aptos, where over 40% of validators are hosted on AWS, most other providers, including AWS, have no more than 25% of validators on each network. Overall, AWS has the largest share in these networks, accounting for 67.4% of AVAX, 43.2% of APT, 35% of NEAR, and 30.1% of ADA. This contrasts sharply with Solana, where AWS represents only 2.3% of validators and about 15% of staking. For Avalanche, the network’s use of AWS may be partly attributed to its partnership program, which uses AWS server solutions to promote enterprise, institutional, and government adoption of blockchain.
Hosted Satoshi Index
Avalanche, NEAR, and Aptos have a hosted Satoshi coefficient of 1, considering that over 33.3% of staking is hosted on AWS on each network. Cardano’s hosted Nakamoto coefficient is 2, slightly ahead of 30.1% of staking hosted on AWS, with the other four providers representing over 5% of staking. Finally, Solana has a hosted Satoshi coefficient of 3, as over 33.3% is hosted on TeraSwitch, AWS, and third-party providers.
Geographical Distribution
A well-distributed network across multiple regions can reduce the risk of local issues, such as natural disasters or infrastructure failures. Additionally, it ensures that the network can withstand potential scrutiny or geopolitical pressure from specific jurisdictions.
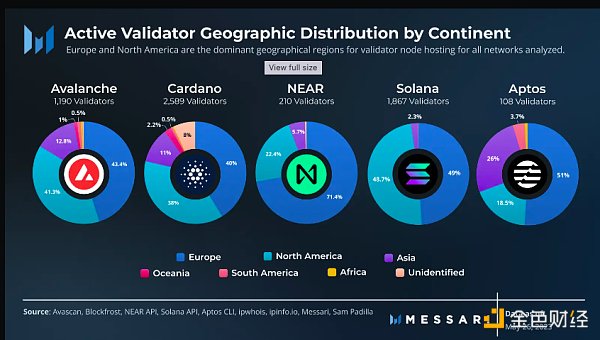 Overall, each network analyzed has a significant impact in Europe and North America. Asia, overall, is represented in most of the networks, but to a lesser extent, with Oceania, Africa, and South America accounting for less than 4% of validators and less than 9% of staking in each network. For some countries with low representation, this may indicate a lack of tangible infrastructure or the ability to pay capital costs. It may also indicate a tendency for people to host on servers in different locations to take advantage of better pricing and the network effects of validators running close to each other, especially for chains with significant MEV activity. Typically, the default hosting location for most users tends to be the cheapest. For example, hosting a validator on AWS in South Africa, rather than the default US East data center, costs nearly three times as much.
Overall, each network analyzed has a significant impact in Europe and North America. Asia, overall, is represented in most of the networks, but to a lesser extent, with Oceania, Africa, and South America accounting for less than 4% of validators and less than 9% of staking in each network. For some countries with low representation, this may indicate a lack of tangible infrastructure or the ability to pay capital costs. It may also indicate a tendency for people to host on servers in different locations to take advantage of better pricing and the network effects of validators running close to each other, especially for chains with significant MEV activity. Typically, the default hosting location for most users tends to be the cheapest. For example, hosting a validator on AWS in South Africa, rather than the default US East data center, costs nearly three times as much.
Avalanche has the most active stake in underrepresented regions, accounting for 8.2%, followed by Cardano at 2.6% and Aptos at 0.6%. We found no active NEAR stake in these regions, with only one active Solana validator. Overall, Avalanche has the largest stake distribution on the continent, while Solana is the poorest.
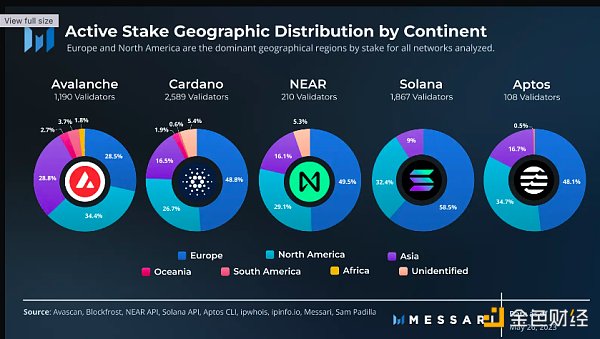 In terms of countries, the United States and Germany have the most validators and stakes in all networks. The United States is the country with the most validator hosting, with the most validators for Avalanche, Cardano, and Solana. NEAR and Aptos have slightly more validators hosted in Germany.
In terms of countries, the United States and Germany have the most validators and stakes in all networks. The United States is the country with the most validator hosting, with the most validators for Avalanche, Cardano, and Solana. NEAR and Aptos have slightly more validators hosted in Germany.
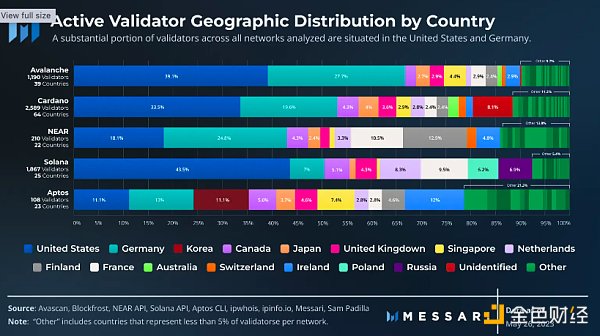
In terms of stake, Avalanche, NEAR, and Solana have more representation in the United States, while NEAR and Aptos have more representation in Germany. All networks are clear that validators and stakes are concentrated in a few dominant countries. In the 69 countries/regions we have identified, most network operations occur in only 10-15 countries/regions for each network, with most being the same countries/regions across all networks analyzed.
Comparing validator and stake distribution maps, in underrepresented regions, a small number of validators exist with significant diversity, especially for Avalanche and Cardano. On the other hand, stakes are more concentrated in fewer countries. This suggests that underrepresented regions are more likely to host validators with less stake.
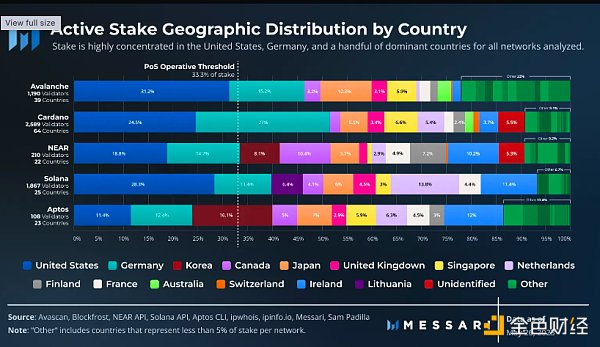
The outlier is Aptos, whose validator and stake distribution are highly similar. This does not necessarily mean a fairer distribution, but rather takes into account that Aptos’ infrastructure launch partners are deliberately distributed globally, and smaller operators may run Aptos validators due to minimum stake requirements exceeding $8 million.
Among the networks analyzed, Cardano has the most representative countries. However, it is also the network with the highest concentration of stakes in the United States and Germany. Cardano validators are distributed in 64 countries, while Avalanche is distributed in 39, Solana in 25, Aptos in 23, and NEAR in 22. We also identified at least 66 different countries with Ethereum validators.
There is a significant concentration of staking in the United States, with a considerable amount of staking being hosted on AWS servers. The most common way to run validators for Avalanche, Cardano, and NEAR is in AWS data centers located in the United States. Although equity has been staked on AWS servers in over 15 countries/regions, a large portion of it is located in the United States and Ireland. Considering AWS’s current dominant position in total staking, greater distribution between its servers could help drive geographical decentralization.
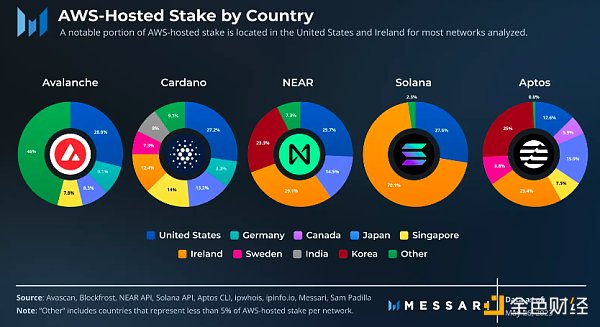 Most of the staking hosted on AWS is located in Amazon’s US East data centers. These data centers are known for managing large amounts of internet infrastructure and activity. This trend appears to be consistent in most of the networks analyzed, possibly due to the price advantage of being the default data center and the low latency advantage of being closer to other network nodes for efficient operation.
Most of the staking hosted on AWS is located in Amazon’s US East data centers. These data centers are known for managing large amounts of internet infrastructure and activity. This trend appears to be consistent in most of the networks analyzed, possibly due to the price advantage of being the default data center and the low latency advantage of being closer to other network nodes for efficient operation.
The Satoshi Index of Operational Geography
To calculate the Satoshi Index of operational geography, we measured the distribution of staking between countries, as this better reflects potential political power or concentrated infrastructure failures compared to larger regions. Four out of five networks have a Satoshi geography coefficient of 2, with staking highly concentrated in the United States and Germany. Aptos has a Satoshi geography coefficient of 3, which is only slightly different from Aptos, with a significant portion of staking in Korea in addition to the United States and Germany.
Final Results
To calculate the comprehensive Satoshi coefficient of operation for Avalanche, Cardano, NEAR, Solana, and Aptos, operational variables were weighted by the severity of potential harm.
-
Node software (client): 0.4
-
Node hosting infrastructure 0.3
-
Geographical location: 0.3
Considering the potentially catastrophic level of concentration at the validator client level that high concentration of validators can bring if the dominant validator client suffers from an error or malicious attack, client diversity is given a higher weight. On the other hand, if a country or node hosting provider is hostile to cryptocurrency, the direct risk to network security may not be so severe. Historically, miners and validators have been able to migrate to other solutions without significant network instability, such as China’s ban on Bitcoin mining in May 2021 and Hetzner’s complete ban on crypto operations in August 2022.
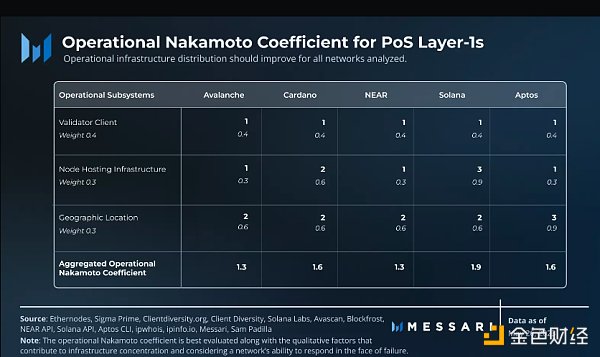 All analyzed networks have relatively low overall Nakamoto coefficients. Avalanche and NEAR reach 1.3, Cardano and Aptos reach 1.6, and Solana barely surpasses other networks with 1.9. On average, no network reaches a state where at least two unrelated failure points are required to interrupt the network. A common theme for all networks is operator preference for infrastructure-like solutions that are typically dependent on early customer development, AWS, and representatives in the United States and Germany. Another common observation is that staking is almost always more concentrated than validators, indicating that a small number of organizations represent a large amount of staking.
All analyzed networks have relatively low overall Nakamoto coefficients. Avalanche and NEAR reach 1.3, Cardano and Aptos reach 1.6, and Solana barely surpasses other networks with 1.9. On average, no network reaches a state where at least two unrelated failure points are required to interrupt the network. A common theme for all networks is operator preference for infrastructure-like solutions that are typically dependent on early customer development, AWS, and representatives in the United States and Germany. Another common observation is that staking is almost always more concentrated than validators, indicating that a small number of organizations represent a large amount of staking.
Solana differs in several ways from the other networks analyzed. First, despite receiving a Nakamoto coefficient of 1 for client operations, Solana will soon have three different implementations on the mainnet. Validators will need to utilize these newer clients to improve the network’s client diversity. Secondly, although a large portion of staking is hosted through infrastructure providers’ solutions, Solana has the least dependence on major providers AWS, OVH Cloud, Hetzner, and Google Cloud among the networks analyzed, which may be due to its bare metal server requirements. The Solana Foundation’s delegation plan may also contribute to this, as only data centers that host 10% or fewer validators are eligible to become validators. Finally, in terms of the number of countries represented, Solana ranks second only to Cardano among the networks analyzed. However, Solana still has room to improve its international reach, as only one active validator was found in Oceania, South America, and Africa.
Recommendations for Security and Decentralization
The Nakamoto coefficient helps us understand the vulnerability of the network, but it does not explain the constantly changing ecosystem and development of the network. Ultimately, it is up to the network’s stakeholders to determine the network’s ability to withstand potential infrastructure failures and external threats. Decentralization of operations is critical to ensuring the network’s long-term resilience, and all types of stakeholders can contribute to improving and incentivizing validator and staking distribution.
Validator Operators
Validator operators should aim to self-host nodes where feasible, switch to non-dominant server solutions, or at least run validators on data centers in different geographical locations with the same hosting service provider if economically feasible. Doing so will help mitigate risks associated with political or corporate hostility affecting specific regions, infrastructure failures, and natural disasters.
Additionally, operators may consider using Distributed Validator Technology (DVT) to enhance infrastructure redundancy. By running validators across multiple setups in a fault-tolerant way, DVT can increase network security and reliability. It adds to the number of operators beyond current limits, making it more resilient to technical and societal failures and attacks.
As decentralized hosting solutions such as Ankr, Akash, and Pocket become more stable, operators may consider using these platforms. These projects allow individuals and existing infrastructure providers to monetize unused computing power. As an open market, their rates are determined by market demand rather than business-driven decisions. A growing supply side may help validator operators access servers in underrepresented areas at a lower cost. Given that providers can join these networks without permission, monitoring the source of computation to avoid centralization is also important.
Delegators
Delegators are encouraged to consider multiple operational factors when choosing validators, rather than simply considering earnings or staking weight. By supporting validators that contribute to the decentralization of the network, delegators can play a role in its long-term survival.
Ecosystem builders, researchers, and infrastructure providers
The network will benefit from ongoing monitoring of operational decentralization. Visual effects such as real-time dashboards help the community understand the health of the network and areas for improvement. By raising awareness and educating stakeholders on the benefits of decentralized operation, the ecosystem can cultivate a culture that values and supports the long-term resilience and success of the network. Doing so may incentivize the development of new and redundant infrastructure, such as additional validator client implementations, to diversify network risk. Builders are encouraged to continuously improve existing protocols and infrastructure by identifying and addressing obstacles that may hinder broader network participation.
Conclusion
Operational decentralization can be measured by the distribution of software components, node hosting infrastructure, and geographical locations through validators and stake. It ensures that the network can withstand faulty code, political and corporate hostility, and physical infrastructure failures. To make the network antifragile, it must exhibit operational decentralization. There is significant room for improvement across all analyzed networks (Avalanche, Cardano, NEAR, Solana, and Aptos) to improve long-term reliability and resilience.
Continuously monitoring and standardizing metrics can help us understand the current decentralized state of the network, but ultimately it is up to the network community to build systems that are resistant to single points of failure. Developing incentives to decentralize power and operations on public global compute platforms may be one of the most overlooked but critical tasks of our time. This will be key to ensuring the long-term survival of permissionless programmable blockchains. Without sufficient decentralization, the network is vulnerable to unforeseeable vulnerabilities or bad actors. Therefore, success ultimately depends on improving existing systems and future validation against potential threats.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Hong Kong’s new regulations on virtual assets are officially in effect, marking a historic moment for Web3 in Hong Kong.
- Will Sam bring surprises to Web3 from ChatGPT to WorldCoin?
- Exploration of Legal Issues Arising from “Digital Collections” in Practice
- What is the current state of development of on-chain government bonds? We have studied 5 agreements.
- Interpretation of Trust Minimization Middleware by Distributed Capital Researcher: Consensus Verification and Bridging
- Yuga Labs May Data Report: The Darkest Moment for NFT Industry Leader?
- Celestia: Modular Data Availability for OP Stack






