Why do I always receive “Exchange Withdrawal” messages? Learn about the classification and protection measures of Web3.0 data leakage events in this article.
Discover why you receive "Exchange Withdrawal" messages and find out how Web3.0 protects against data leaks in this article.Author: Certik
In today’s society, the internet is an integral part of people’s lives, both for work and for personal use. While it’s possible to leave the house without a wallet, it’s almost unthinkable to do so without a phone, which has replaced physical cards for payments. Even panhandlers are starting to accept QR code payments.
It’s not hard to imagine that most of the threats faced by individuals, businesses, organizations, and their clients come from network vulnerabilities and attacks. Privacy concerns have also become increasingly important, and there are countless cases every year of sensitive data being lost due to vulnerabilities.
There have been numerous major security events in the history of Web3.0, ranging from the loss of private keys at centralized exchanges to the theft of investor data. This data can remain on hacker forums and dark web markets for years, meaning that those affected by a data breach might be at risk for a long time. CertiK analyzed 74 security events that occurred in centralized Web3.0 entities, and 23 of those events led to a high risk of long-term data loss. Of those 23 events, 10 resulted in data packets that were still available for purchase on dark web forums.
- Decentralization explorers of Rollup: Polygon, Starknet, and Espresso
- As the countdown to the debt ceiling negotiations begins, Biden and Republican leaders reassure the public that there will be no default.
- Is Binance joining ORC-20, marking the end of BRC-20?
While law enforcement efforts to target hacker forums can prevent some data from being extracted, such measures are ultimately treating the symptoms rather than the root cause.
This article will explain the categorization of Web3.0 data breaches and the measures that should be taken to protect one’s data.
Background
Hacker attacks, vulnerability exploitation, ransomware, and all other types of cyberthreats are increasing in scale and severity. What makes the Web3.0 ecosystem unique is that it provides malicious actors with various attack vectors that other technologies do not have, including vulnerabilities in smart contracts and new phishing techniques.
However, the story of Web3.0 security incidents is closely related to that of other industries. Similar security vulnerabilities exist in centralized projects and companies in non-Web3.0 fields.
We hope to closely examine the history of security incidents targeting Web3.0 and assess whether past events pose ongoing risks to members of the present community.
To achieve this, it is necessary to carefully analyze the differences between security incidents in this report and vulnerabilities caused by the use of smart contract protocols.
We have studied many events targeting Web3.0 companies since 2011, which can be roughly divided into two categories:
- Protocol malicious use: incidents that use smart contract code to obtain economic benefits
- Vulnerabilities: incidents in which attackers compromise the internal network of the target organization and use the obtained permissions to steal company data or funds
In terms of recent and long-term risks, there are several important differences between these two categories.
Protocol malicious use occurs within a certain time frame, from the attacker executing the exploit to when they exhaust all available funds, gas, or cause the target project to terminate. Some of these events may last for hours or days, and negotiations after the event may further extend this time period, while some projects may close immediately afterwards. However, the key is that these attacks have clear starting and ending points.
In contrast, vulnerabilities can be considered ongoing events (where attackers gain network access and remain in a “long-term squatting” state). The definition of a vulnerability is usually data leakage, which is used for attack utilization or subsequently sold on the dark web or online forums.
Network vulnerabilities can also result in significant financial losses. Most Web3.0 organizations are financial entities, with very large fund flows, which naturally makes them a target for hackers.
Data leaks can have huge destructive power and the risk can last for many years, especially when personal identity information (PII) is lost during the leak.
Given this, we have collected 74 past event samples, which we classify as violations that pose ongoing risks to community members (including only incidents where the company’s internal network was compromised, not data on protocol utilization).
We believe it is necessary to distinguish between incidents of sensitive data loss and incidents of only financial loss. In order to better assess the ongoing risks of these violations, we will focus on violations whose data can still be sold or obtained for free in other areas of the dark or light web, and express our views on the accessibility of these platforms.
Data Leaks and Fund Losses
To assess the ongoing risks associated with these events, we divide them into the following defined events:
- Theoretical retrievable data loss events, including PII and internal databases.
- Events in which funds or data are lost and the data cannot be retrieved.
The second category of unretrievable data loss events is primarily composed of violations that result only in the loss of funds or private keys. In such cases, the lost funds are typically irretrievable.
Anomalous events include those in which stolen data is never released, returned, or used for other purposes. For example, in June 2020, the centralized Japanese exchange Coincheck was attacked and PII of over 200 customers fell into the hands of the attacker. The attacker compromised Coincheck’s network and then sent phishing emails using the company’s internal email address, requesting that customers provide PII. But there was no specific database loss in this incident and the lost data was only the data of the customers who replied to those emails.
In another incident in June 2020, the Canadian centralized exchange Coinsquare also experienced a vulnerability attack, which led to the leak and loss of data involving 5,000 email addresses, phone numbers, and home addresses.
The attacker claimed that they would use the data in SIM card swapping attacks but would not attempt to sell them in order to “fish for bigger fish.” This type of event is also categorized as the second type of irretrievable event.
Of the 74 events we identified, 23 can be classified as retrievable data events, accounting for approximately 31%. The remaining 51 events were either anomalous events as described above, or events that suffered only financial losses.
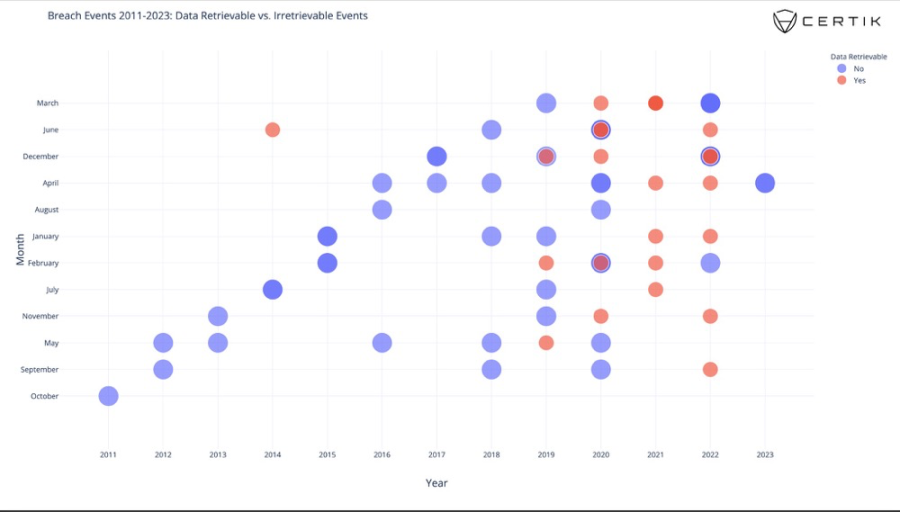
Chart: Data retrievable and non-retrievable events from 2011 to 2023 (Source: CertiK)
We can see a few points:
① The number of data events that are highly likely to be retrievable or recoverable after 2019 has increased significantly. This is proportional to the increase in hacker attacks and data leak incidents in various industries during the epidemic period.
② During this period, government assistance increased, some of which was injected into the Web3.0 ecosystem, coupled with the bull market in 2021, which may have provided attackers with more opportunities for ransomware and data sales.
Where does stolen data go?
The Dark Web and Telegram
Lost data typically ends up being sold or stored on the dark web (.onion websites) or clear net. If the data is suspected to have some economic value (PII and other data used for fraud), it will often appear frequently on the dark web markets and even on Telegram channels. If the attacker’s demands (via ransomware) are not met, the data will be dumped on blocking sites or hacker forums.
The ultimate destination of the data determines the long-term risk it poses to its original owners.
Compared to data that can only be purchased on the dark web, data dumped on hacker forums at very low or zero cost poses a higher risk of leakage.
The continued accessibility of such sites also “facilitates” the long-term risk of victim data leakage. In the following sections, we will take a deeper look at the sale of Web3.0 data found on these sites.
Online Forums
Online hacker forums have been around for years. Considering the growth of searchable data incidents since 2019, only a handful of forums are worth analyzing as case studies in this context. These forums include the Raid Forum, Breach Forum, and Dread Forum.
Multiple incidents of violations have chosen the Raid Forum as one of the preferred forums for dumping and selling illegal data. The Raid Forum began operation in 2015 and has been running on the clear net for many years. However, in 2022, the domain name of the Raid Forum was seized by US law enforcement agencies in cooperation with Europol.
Image: Notification removed by US and European law enforcement agencies from Raid Forum website
The Dread Forum was established in 2015 and appears to have remained active until the end of 2022, but there are many signs on social media that the forum may have also closed down. We tried to access the forum’s dark web (.onion) and IP2 versions, but it seems that these have also been shut down.
After the closure of the Raid Forum, the Breach Forum immediately went online.
For those users who were “homeless” due to the closure of the Raid Forum, the Breach Forum provided them with a reasonable place to stay.
It had a similar interface, member reputation rating system, and high activity levels as the Raid forum, with user numbers reaching 60% of the original Raid forum user group (about 550,000 users). Just one year later in March 2023, the FBI arrested Conor Brian FitzBlockingtrick, who operated the Breach forum, and after an internal drama about redeploying the website, the site collapsed.
Less than a week after the Breach forum collapsed, another replacement emerged, which was reportedly operated by a self-proclaimed former Anonymous hacker named Pirata (@_pirate18). However, it only had 161 members, meaning that this replacement failed to absorb those veteran forum players.
During this downtime in late March, many other forums popped up. Some of them were shut down as typical illicit forums, so it is reasonable to speculate that the remaining ones may have been disguised by law enforcement agencies.
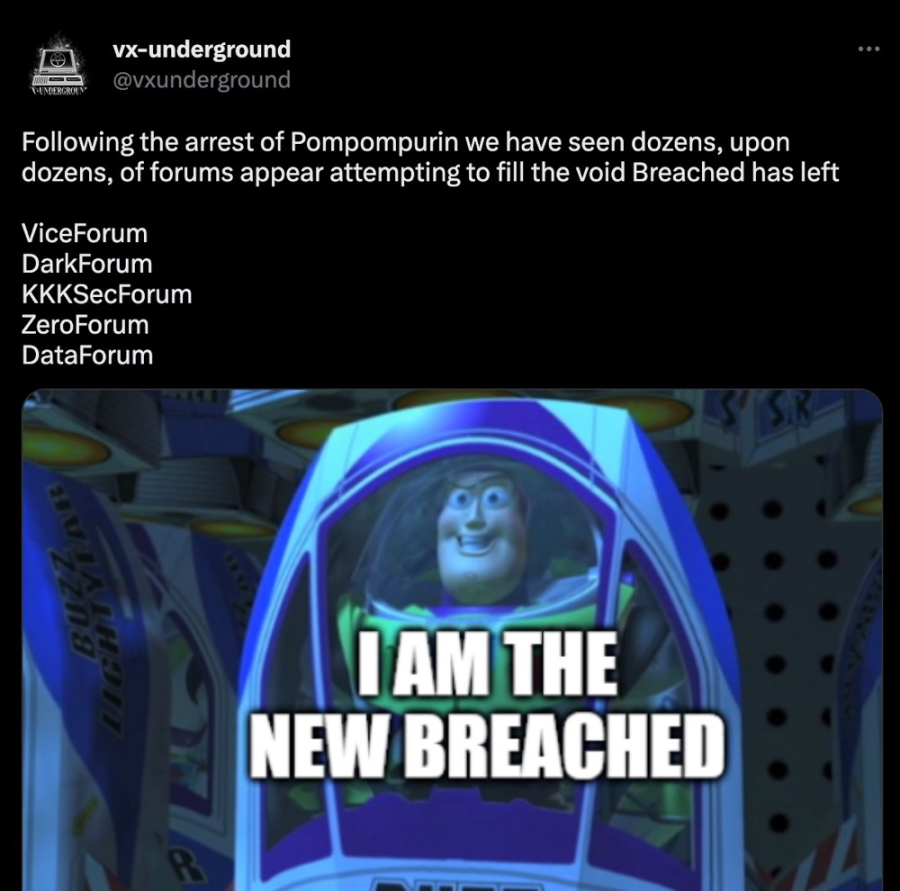
Image: VX-Underground forum list after the closure of the Breach forum (source: Twitter)
We can only confirm that some Web3.0 data exist on one of the forums.
According to reports, the ARES forum absorbed some activities from other closed forums, but the specific number is unclear. The forum is reportedly associated with ransomware groups and other malicious actors, and also operates a public Telegram channel which advertised data sales in its locked VIP sales channel. The channel was launched on March 6th and placed hundreds of ads (including two posts related to centralized exchange databases).
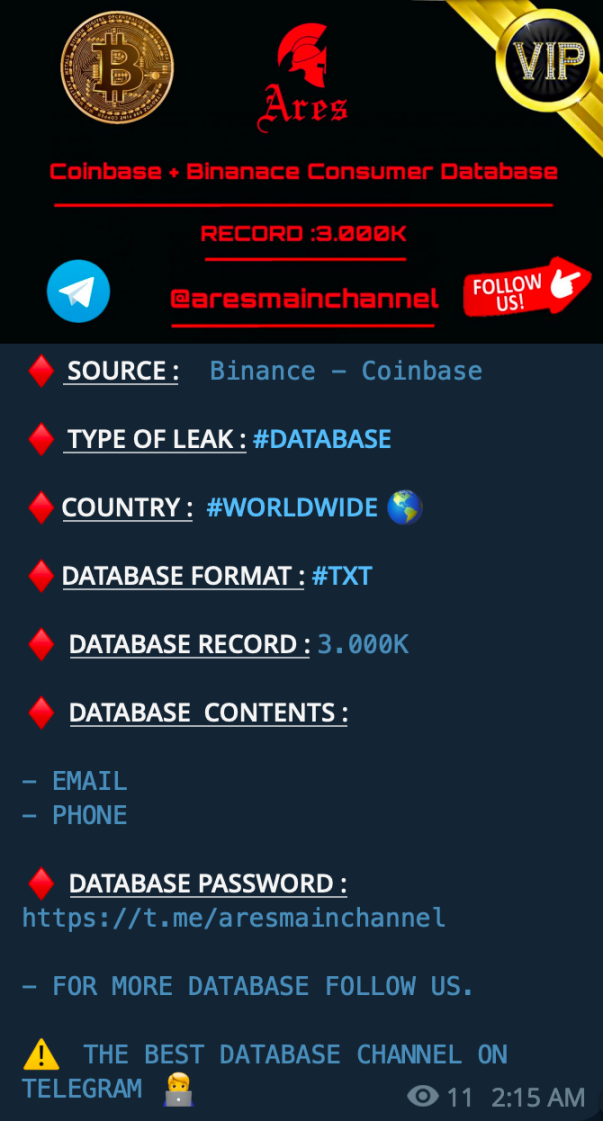
Image: ARES forum's Telegram centralized exchange data channel advertisement (source: Telegram)
Overall, the hacker and data dump forum community is currently quite messy. Traditional forums have no clear replacements, and international law enforcement agencies have stepped up their crackdown on these groups, so it is almost certain that forums will not be the preferred route for any major data (including Web3.0) leaks in the short term.
Data leaks on .onion websites on the dark web
For a long time, dark web markets and forums have been a place for people to dump or sell data.
These ecosystems also face crackdowns from law enforcement, although these crackdowns are more aimed at markets that facilitate drug sales. That being said, data leaks seem to be very common or at least heavily advertised even in lesser-known markets. This difference is now particularly evident compared to online forums that also stored data but have since shut down.
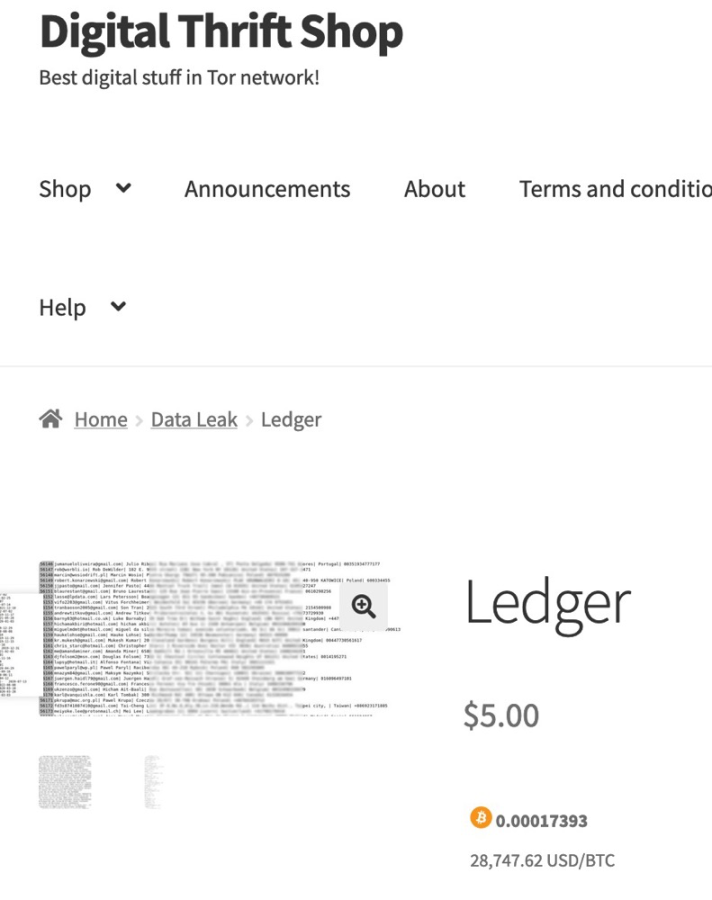
Picture: Classified ledger customer data for sale on dark web markets (source: Digital Thrift Shop)
Looking back, of the 74 data leaks we identified as samples, 23 were data that could be searched with some probability. Among these 23, we were able to find 10 active data sales ads (43%). These samples are highlighted in green on our previous chart:
Chart: Confirmed instances of leaked data for sale on dark web markets highlighted in green (source: CertiK)
The addition of paid data sales in this chart indicates several things. First, we cannot obtain any data sources for any misconduct that occurred after 2021.
Based on the nature of the 2022 targets, there is a reasonable possibility that the data may have appeared on a forum that no longer exists.
However, this is difficult to prove, especially when these datasets do not appear on any forums that can replace Raid and Breached. Secondly, these datasets have clearly not appeared in any dark web markets that we can see from 2019 and earlier – possibly because the markets from which we obtained this data were very early and obscure. We cannot assess whether these data sets are still actually available through these suppliers, but these ads still exist.
Do these data leaks pose long-term risks?
It is difficult to try to quantify long-term risks, but data loss risks can at least be compared with non-data-related events in this sample. Note that we can classify the risks of violations that only result in direct financial losses as low risks, because:
Losses are immediate and can be measured by the statutory or Web3.0 currency lost.
All data lost in this process is replaceable. If a leak occurs, the private keys, passwords, and privileged network access points must be changed to fix the problem.
A breach event of lost sensitive data (especially customer data) does bring greater long-term risk
This data is mostly sold or offered for free on the dark web or clear web, extending its long-term availability.
Customer’s personal data points, such as phone number, name/surname, address, and transaction data are difficult or impossible to change. Therefore, even if someone changes their personal information due to information leakage, all data of other individuals involved in the leak event still carries risk.
The impact of this type of violation is difficult or impossible to measure. Depending on the lost data, the victim may become a target of multiple frauds or may not be targeted at all.
In a violation event we discovered in 2014, data for sale was found. This particular data point further demonstrates the difficulty of measuring long-term risk. In 2014, hackers attacked the now-defunct cryptocurrency exchange BTC-E, which was seized by U.S. law enforcement in 2017 – in fact, the risk associated with this data loss was much lower than other risks.
However, it is clear that the risk remains ongoing, and this data may be matched with data from newer violations, increasing the long-term risk for individuals participating in Web3.0 during this period.
Overall, data lost after 2019 (especially data that can still be easily sold on the dark web market) is highly likely to present the highest sustained long-term risk. From 2022 onwards, affected individuals will almost certainly face significant risks of their data being used for fraudulent activities (even if this data cannot be physically located). While many online forums have been shut down, we should assume that all lost data, especially recent data breaches, is likely still available somewhere and can reappear at any time.
Conclusion
The reality is that security vulnerabilities cannot disappear 100%. When data is stored and processed by a centralized entity, the remedial measures available to most users affected by data breaches are extremely limited.
However, we can reduce exposure risk by limiting the use of centralized services, including centralized exchanges. Individuals should also use two-factor authentication whenever possible to help prevent unauthorized exchange wallet activity or the use of PII to access or modify account details.
Depending on the nature of the leak, we may even consider attempting to change some of the information exposed in the leak event, such as email addresses or phone numbers.
In Web3.0 data leaks, if you plan to operate anonymously, your identity will face additional leak threats.
Other measures can also be taken to protect data and investments. For example, by distributing assets in self-custody wallets and hard wallets to reduce investment and financial risk.
Of course, data can also be protected in the following ways:
- Reduce the number of centralized Web3 investment institutions or exchanges that share personal data with you
- Do not use duplicate passwords across platforms
- Enable two-factor authentication on all accounts
- Monitor websites that report data leaks, which will tell you if your email address is involved in the leak
- Use credit monitoring services to monitor attempted identity theft and bank-related fraud
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Understanding the business model and product components of Centrifuge, one of the leading companies in RWA
- Deep Analysis: Exploring Hooked’s Ambitious Goals in Web3 Education through Collaboration with Animoca
- Is the ultimate goal of AI Web3? “Father of ChatGPT” launches encrypted wallet World App
- Why has Cosmos become the first choice for many developers in application chains?
- Dark Side of NFT History: Reviewing the Darkest Moments of 5 Blue Chip Tokens
- Conversation with Coinbase Protocol Director: How is Base, as a highly anticipated new Layer2, building its ecosystem step by step?
- How does ERC-6551 change the game by turning NFTs into Ethereum accounts?