Understanding the Distributed AI Computing Network Gensyn
Gensyn: Understanding Distributed AI ComputingOn June 12th, Gensyn, a blockchain AI computing protocol based in the UK, announced the completion of a $43 million Series A financing led by a16z. Gensyn is the first to deliver a response to the AI revolution.

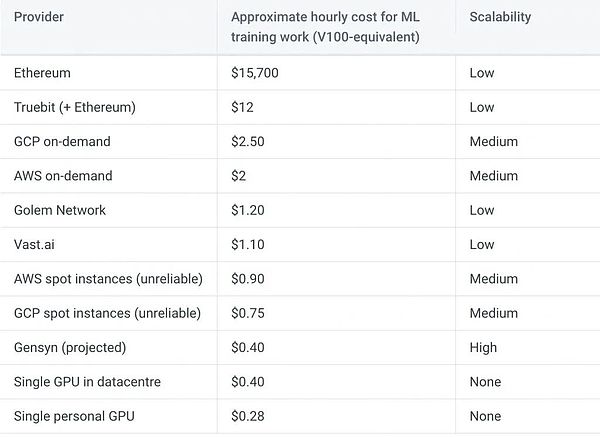
Gensyn is essentially a first-layer proof-of-stake blockchain based on the Substripe protocol that can use smart contracts to facilitate task assignment and rewards for machine learning, enabling rapid learning of AI models and reducing the cost of deep learning training. The cost of a single training session for GPT-3 in 2020 was about $12 million, more than 270 times higher than the estimated value of GPT-2 training in 2019 of about $43,000. Generally speaking, the model complexity (size) of the best neural network is doubling every three months. The hourly cost of Gensyn’s machine learning training work is about $0.4, far lower than the required costs of AWS ($2) and GCP ($2.5), among others. Gensyn wants to use blockchain and other technologies to achieve an efficient computing protocol for decentralized and large-scale distributed deep learning, with probabilistic learning proofs and cryptocurrency incentive mechanisms.
- Office of the New York Attorney General Provides Tether-Related Documents in Response to CoinDesk
- How should investors hedge their risks during the “storm” of encryption?
- Uniswap v4: What’s Next for the Top DEX?
Gensyn connects developers (anyone who can train machine learning models) with Solvers (anyone who wants to use their own machines to train machine learning models). By utilizing idle computing devices with machine learning capabilities from around the world (such as small data centers, personal gaming computers, M1 and M2 Macs, and even smartphones), it connects to a global machine learning supercluster, increasing the available computing power for machine learning by 10-100 times. At the same time, Gensyn achieves large-scale and low-cost neural network training without trust through innovative verification systems and computing power supply.
1. Innovative Verification System
The core challenge of Gensyn is to verify whether the computational task executed on the device has been executed correctly and to trigger payment via tokens. The Gensyn system mainly addresses the verification problem through three concepts, including probabilistic proof-of-learning, graph-based precise positioning protocols, and Truebit-style incentive games.
It consists of four main participants, including Submitters, Solvers, Validators, and Whistleblowers. Submitters are the end users of the system, providing tasks to be calculated and paying for completed work units. Solvers are the main working part of the system, performing model training and generating proofs for Validators to check. Validators link the non-deterministic training process to deterministic linear calculations, replicate a portion of the Solver’s proof, and compare the distance to the expected threshold. Whistleblowers are the last line of defense, checking the work of Validators and challenging to win cumulative prizes.
The system can perform all of these tasks without the need for trust, and the cost remains unchanged in proportion to the size of the model, thereby maintaining the verification cost. The innovation of the system lies in combining model training checkpoints with probability checks that terminate on the chain, effectively solving the problem of state dependence in training arbitrary-sized neural networks.
2. New Computing Power Supply
The Gensyn system will utilize underutilized and unoptimized computing resources. These devices include game GPUs that are currently unused, as well as GPU mining machines from the pre-Ethereum PoW era. Because the protocol is decentralized, it will eventually be managed by a majority of the community and cannot be “turned off” without the community’s consent, making it censorship-resistant. The innovation of this protocol lies in making full use of underutilized computing resources, providing the community with more computing power, and also providing a new source of income for those who have unused devices. Furthermore, the Gensyn protocol provides costs similar to those of GPUs owned by data centers, and its scale can exceed that of AWS.
In summary, Gensyn’s core goal is to democratize AI through decentralized planning, allowing more people to participate in the innovation and application of AI technology. The core idea of the plan is to utilize underutilized computing device resources, improve the efficiency and accuracy of AI models by building an open, decentralized verification system, and provide more opportunities and possibilities for AI entrepreneurs. It is an innovative and forward-looking plan that is expected to play an important role in the future AI field.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Evening Reading | USDT Faces Serious Selling Pressure: Are Market Makers Exiting?
- Is USDT facing severe selling pressure due to market makers exiting?
- How can the development path centered around application chains avoid the pitfalls of Polkadot and Cosmos?
- How can we participate in interactions now that the re-collateralization agreement EigenLayer has officially launched on the mainnet?
- How can Prisma, who calls themselves “LST Endgame,” create a growth flywheel?
- Interpreting the Maverick Protocol DeFi Protocol
- Two Sides of a Digital Being: Aging in the Metaverse, Rebirth in AIGC