One article revealed the mystery of the North Korean hacker team: the world is fighting the epidemic, but they are stealing Bitcoin?
"The most deadly may be the beast with its teeth and claws, or it may be the silent viper at its feet."
Recently, the whole world has been fighting the epidemic, but North Korea, a wonderful workman, is busy laundering money . No, two Chinese citizens were sued by the US Treasury Department for using Bitcoin to help North Korean government hackers launder money.
It is said that the two OTC service providers helped the North Korean hacker organization Lazarus Group to launder $ 100 million between December 2017 and April 2019.
To be honest, money laundering services have formed an industrial chain abroad, which is still quite common. But what caused Uncle Jian's curiosity is: North Korea actually has a hacker team, and is it still organized by the government?
- What else can Bitcoin bring us if we can't hedge?
- Story | From the eyes of others, I know Bitcoin
- BTC plunges again: during the avalanche, every snowflake adds leverage
In fact, although North Korea is a projectile land and has been blocked by the economy for many years, there are two worlds that are disturbing the world.
One is a nuclear weapon and the other is a hacker group.
In 2017, the case of the Bitcoin Ransomware virus that swept the world came from North Korean hackers. So today let's unravel the mystery of North Korean hackers.
Since North Korea conducted its first nuclear test in October 2006, the UN Security Council has passed ten resolutions to continuously increase sanctions against North Korea.
The content of sanctions has gradually expanded from areas such as weapons of mass destruction to economic areas.
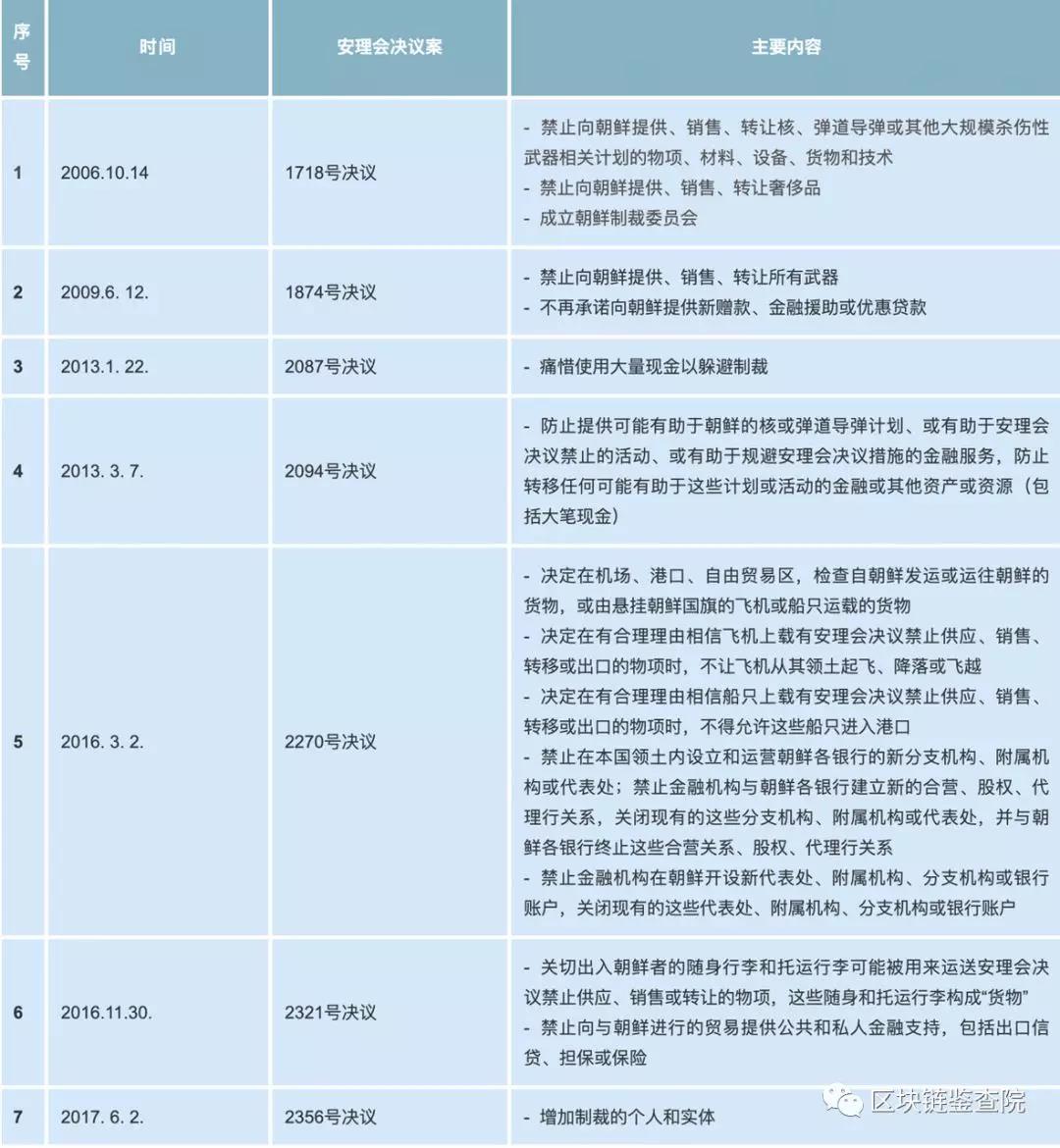
Ten resolutions of the United Nations |
Under such a predicament, North Korea has become more difficult to maintain domestic livelihood while continuing to develop nuclear weapons.
The poor thinks about change, so North Korea thinks about many ways to make money, which is really shocking to say:
▌Method 1: Drug Smuggling
In 1977, all members of the North Korean Embassy in Venezuela were deported by the government because of a drug trade.
In 1993, the Australian government intercepted a North Korean freighter loaded with $ 50 million in drugs near the Port of Melbourne.
These are just the tip of the iceberg over which North Korea smuggled drugs.
▌Method 2: Selling Weapons
In August 2016, a North Korean freighter was detained on the surface of Egypt, carrying 2.3 metric tons of iron ore and 30,000 North Korean rockets.
In the same year, a plane loaded with North Korean military communications equipment and military materials was intercepted while on its way to Eritrea, Africa.
This means that there is illegal military trade between North Korea and many countries.
▌Method 3: Labor output
North Korea has specialized labor and trade companies that have signed labor employment contracts with Russia, Africa, and other places to obtain labor remuneration by sending a steady stream of North Korean labor.
According to a study by the North Korean Human Rights Database Center, these migrant workers are usually men who already have children and families. If "the rules are broken," their family members in North Korea can be stabbed.
At this point, North Korea has gathered three major means of smuggling, drug trafficking and human trafficking. But these still have to deal with other countries, and it is easy to get caught.
So the North Korean hacker national team came into being. Their purpose is to free North Korea from its dependence on other countries and make money through the power of technology.
Speaking of North Korea, everyone will feel poor and backward, let alone the development of the Internet.
Indeed, in China, we can already choose to open a 5G package, but in North Korea, only 3 million people use 3G mobile phones, and the national coverage rate is less than 1/8 .
But in this poor land, there is an Internet force that gathers 1,800 top cyber experts: the Korean People's Army's 121st Bureau.
"The North Korean hacker has reached the top level in the world and is on par with the capabilities of Google or the U.S. Central Intelligence Agency, " North Korean Jang, who worked in 121 Bureau and later defected to South Korea, told the media .

Korean People's Army 121st Bureau with Kim Jong Un
I have to say that the North Korean government has made great determination to create 121 innings.
Everyone in the 121 Bureau is a cutting-edge talent who has been selected by the North Korean government for years in the field of mathematics, computers, etc., and has undergone rigorous training and selection.
It is said that the selection and elimination rate is as high as 98%, but as long as they are successfully selected, they can enjoy the highest level of treatment in North Korea, and their families can also be moved to the capital Pyongyang by the authority to settle.

121 event environment
And the most famous hacker team in the 121 innings is the Lazarus Group, transliterated as Lazarus. Lazarus is a character recorded in the Bible and the Gospel of John. resurrection.
Presumably, North Korea wants to use this to metaphor its tenacious vitality.
Combining several major cases of Lazarus, Uncle Jian felt that the name was worthy of the name.
▌1. Beginning of the show: surprise attack on Sony Corporation
In North Korea, the authority and image of "Kim Jong Un" is sacred and inviolable.
However, in 2014, Sony Pictures debuted the first trailer for the movie "Assassination of Kim Jong Un" on Youtube, which was immediately popular, and the feature film is also planned to be released in the United States at Christmas.
This action comedy tells the story of two American talk show hosts who went to Pyongyang to assassinate Kim Jong Un under instructions from the CIA.

Picture source: Stills of "Kim Jong Un"
North Korean officials certainly could not accept such an "insult" and immediately issued a tough protest through the Foreign Ministry. However, the United States was unmoved. President Obama even encouraged everyone to watch.
So one month before the movie was released, Sony was suddenly hacked and completely paralyzed. A warning page appeared on the computers of all staff members, stating "Hacked By #GOP" in bold red characters.
GOP stands for Guardians of Peace.
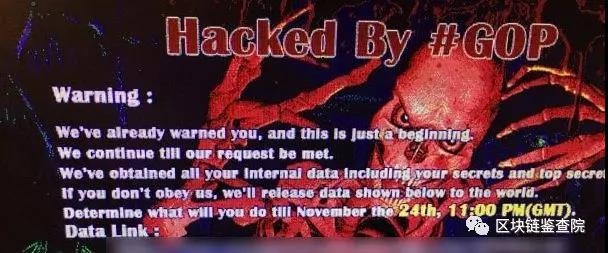
The hacker also issued a warning:
We already have all the network data of Sony Pictures, including employees' secrets and various high-level secrets.
If we do not comply, we will make all the data publicly available.
Subsequently, Sony Pictures was forced to announce that all staff members work from home, and in conjunction with the United States FBI for comprehensive network monitoring.
After a month of investigation, the US FBI identified that the attacker was from North Korea. Choi Sang-myung, a top security expert and former senior North Korean official, revealed that the hacking operations are similar to other previous North Korean attacks, including the number of lines of code, encryption algorithms, data detection methods, and compromised networks.
However, the North Korean side denied it, saying: GOP hackers are not our North Korean official designation, but no matter who does it, my great North Korea praises you as a heroic hero!
Such a response sparked a drool war between the US and North Korean governments for nearly a month.
As the world's top film and television company, Sony Pictures has made countless classic movies, but the imagination is not as shocking as the "big movie" in which it has participated.
In the end, the farce was endorsed by Sony and cancelled the screening of "Assassination of Kim Jong Un" .
However, Lazarus did not stop there. In 2016, he also invaded the central bank account of Bangladesh and committed the notorious bank theft, which stole nearly 81 million US dollars. The incident directly led to the sad resignation of Bangladesh ’s central bank governor Attilahman, and two deputy central bank governors were fired.
▌2. Technique upgrade: Global Bitcoin Ransomware Case
With the strengthening of the bank's financial system and the difficulty of transferring money in and out, Lazarus turned to Bitcoin. The anonymity of cryptocurrencies and the characteristics of circulation around the world make it easier for hackers to launder money.
Thus, the Bitcoin Ransomware case that swept the world appeared.
On May 12, 2017, Xiangshui County Public Security Bureau in Yancheng City broke the immigration formalities.

Notice issued by Xiangshui County Public Security Bureau in Yancheng |
Subsequently, the Public Security Bureau officially posted a Weibo saying that a virus called WannaCry was in the computer, and all documents were encrypted, and it was necessary to pay about $ 300 in bitcoin to unlock it.

Police in Xiangshui County Public Security Bureau helplessly face WannaCry virus | Figure
The policeman's heart is estimated to have collapsed.
That night, some Chinese universities were recruited, and the virus was suspected to have spread through the campus network.
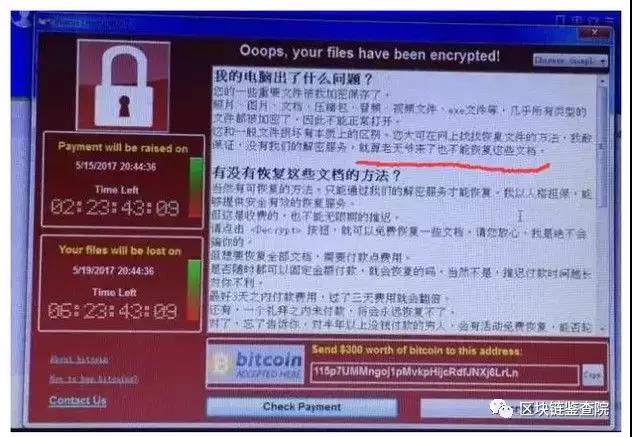
Since then, the global outbreak of WannaCry ransomware has attracted 300,000 users in at least 150 countries, causing losses of up to $ 8 billion, which has affected many industries such as finance, energy, and medical care, and has caused serious economic losses.
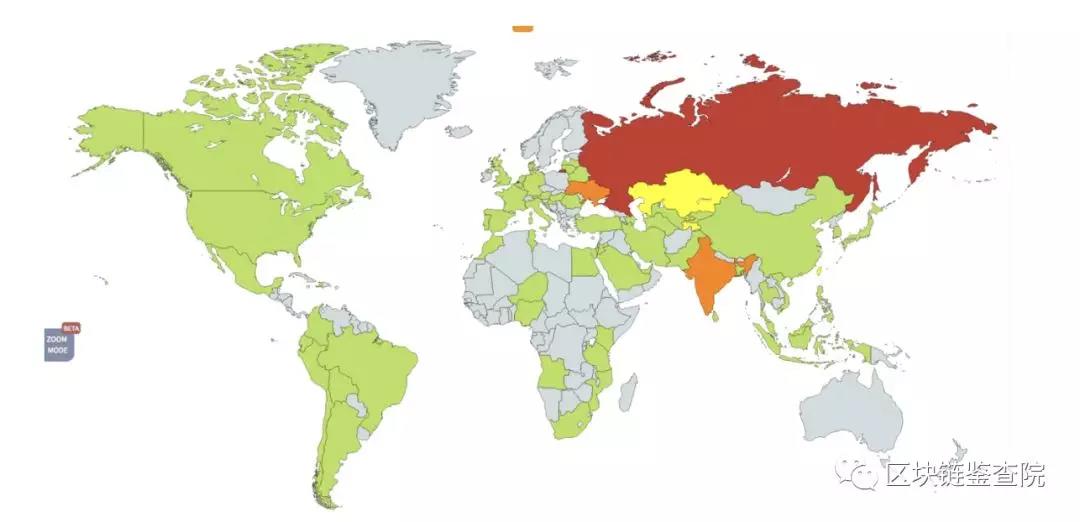
Heatmap showing WannaCry's reach in May 2017 | Graph
Remember the "Panda Burning Incense" that hit the country in 2006? Compared to WannaCry, Panda is still a younger brother.
Although no hacking organization claimed it after the WannaCry outbreak, after technical analysis, the United States, Britain, and Australia formally declared that North Korean hackers were behind the attack in December of the same year.
China's top hacker and head of Tencent's Xuanwu Lab TK also reposted in the circle of friends: "Based on software homology analysis and other technologies, multiple researchers have reached the same conclusion: WannaCry ransomware may be North Korean hacker Lazar The road is dry. "
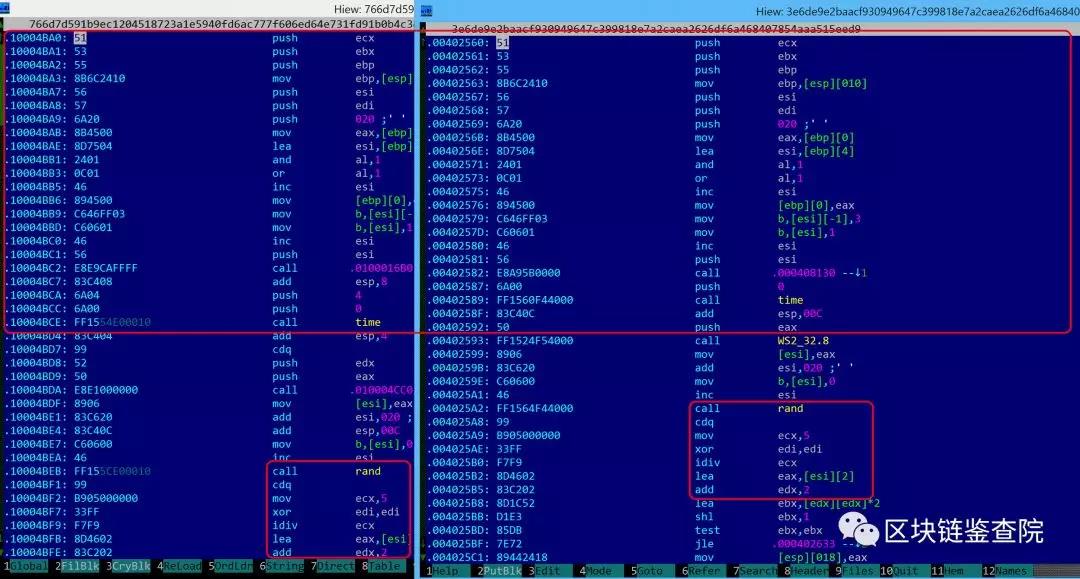
Software homology analysis for WannaCry | Figure
At this point, Lazarus is notorious worldwide.
▌ 3. Double extortion and commit crimes everywhere
In the early years, Lazarus's attack targets were mainly South Korea and Japan, and mainly DDoS attacks. It was enough to defeat the other system.
Even though WannaCry's scope spread throughout the world, Lazarus didn't make much money from it, accumulating only 52 bitcoins, and the market value at that time was less than 1 million yuan.
But in recent years, they have indiscriminately attacked 18 countries, financial institutions, casinos, cryptocurrency companies, including India, Malaysia, Poland, Uruguay, Ethiopia, etc., and went straight to the money.
The following are several real robberies in Lazarus, which can be said to be white wolves with empty gloves and a lot of money:
① In 2017, South Korean cryptocurrency exchange Bithumb was hacked, 8 billion won was stolen, and a large amount of user information was leaked. Later, South Korean lawmakers pointed out that this was done by North Korean hackers.
② On December 9, 2017, Youbit, an old cryptocurrency exchange in South Korea, suddenly declared bankruptcy. It turned out that it was successively attacked by hackers in April and December, losing 4,000 bitcoins (about RMB 34.47 million at that time) and % Of exchange assets. After investigation by the Korean National Intelligence Agency, there are clear signs and historical evidence that Lazarus in North Korea is behind the hack of Youbit.
③ In March 2019, DragonEx announced on Telegram that it had been hacked. The hacker stole and transferred 7 million US dollars of cryptocurrency, and Lazarus was also accused of behind the attack.
In fact, hacking the user's money is only the first step. The more important thing is to make these money gods unaware of their own accounts.
If there is a clue left, it is to tell the world: people are in North Korea, come and catch me. So Lazarus has also developed very mature money laundering techniques.
▌Step 1: Use the mixed currency service to hide the funds
In the early days, Lazarus's method was relatively clumsy, mainly relying on increasing the number of accounts to disturb the tracker's sight. Through the figure below, we can see a transfer method of Lazarus in 2018.
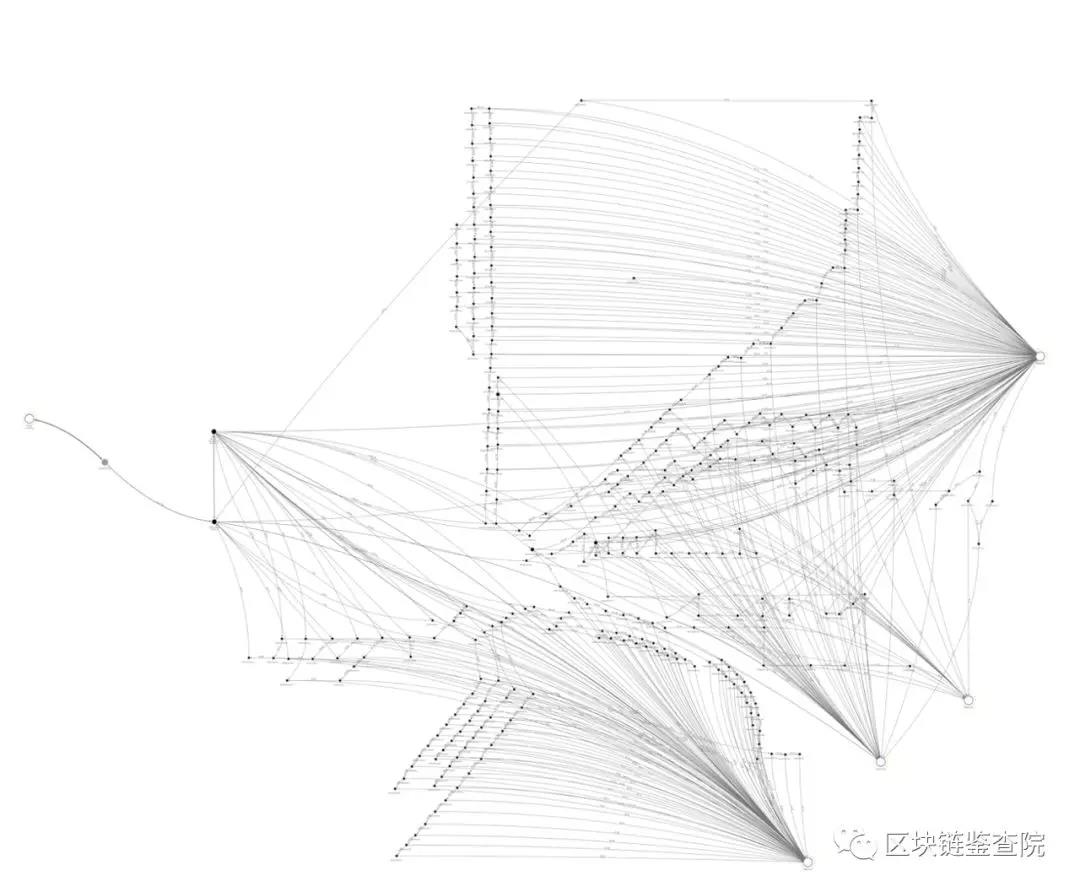
Lazarus's roadmap for transferring funds in 2018 |
In simple terms, the funds are transferred from the Victim Exchange wallet on the left, through multiple wallets in the middle, and eventually dispersed to different exchanges on the right to realize cash.
Although the path to funding is long, it is easy to sort out the lines.
But in the later period, the birth of privacy coins and coin mixing services provided great convenience for money laundering.
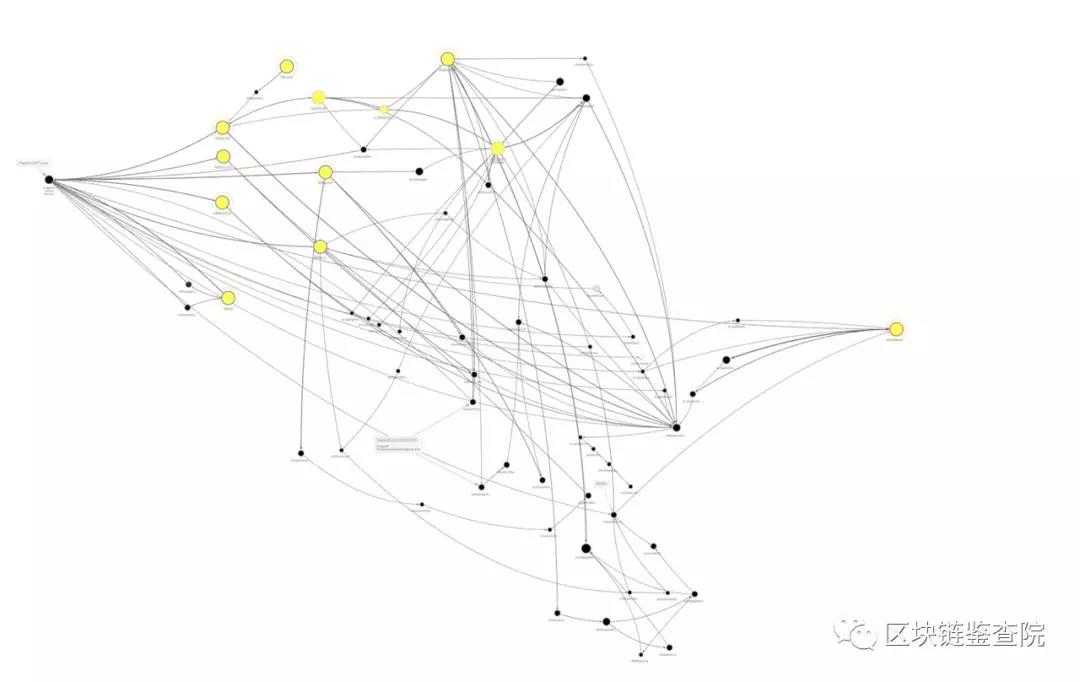
Lazarus's roadmap for transferring funds in 2019
As shown above, we find that the steps are much less, but the wiring is more complicated.
In 2019, Lazarus transferred all the stolen crypto assets to major exchanges and exchanged them for Bitcoin, then withdrew it to the Bitcoin privacy wallet Wasabi, and finally washed these Bitcoins through a hybrid protocol.
So how does the hybrid protocol get washed away?
To put it simply: the hybrid protocol is like a big dye tank. Everyone deposits dirty coins and mixes them together. As long as they can prove that you have deposited coins with zero knowledge (without issuing any private information), you can withdraw coins smoothly. Coins can no longer tell who is who.
North Korea officially used the mixed currency wallet Wasabi Wallet to complete money laundering and cleared the suspect.
▌Step 2: Cash through OTC exchange service
Remember the two Chinese people charged by the US mentioned at the beginning?
They may have helped hackers monetize Bitcoin without their knowledge. Because at this time, you can no longer know the relationship between these Bitcoins and stolen assets.
Currently, Lazarus is becoming more efficient in money laundering. In 2018, Lazarus took up to 500 days to cash out the assets, but by 2019, it had been reduced to 60 days.
Sometimes, I really don't know who has benefited from the development of technology?
Faced with economic sanctions, Iran chose rigid and Venezuela chose petroleum coins.
North Korea, with its light mind, chose hackers to illegally plunder wealth around the world.
Maybe you think it's cool to be a hacker, but think about exchanges that went bankrupt under hacking, such as Mentougou, Youbit, etc. Behind them are thousands of investors who have suffered losses.
Why did your hard-earned coins become a hacker's sponsor?
So even if we sympathize with North Korea again, this is not an excuse for their illegal plunder. It also undermines the dignity of a country.
As the saying goes, riches and riches cannot be lascivious, poor can't be moved, and majesty can't be yielded.

We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Will Bitcoin halved in price, plunge again?
- Bitcoin Secret History: Who is Cobra who wants to change the Bitcoin white paper and consensus algorithm?
- Why did Bitcoin fall below $ 5,000? Will it rebound? What about miners?
- The tragic world under the epidemic, who is the next safe haven myth?
- Bitcoin plummeted 10% again, is the "halving market" over?
- Bitcoin rebounded to surpass $ 9,100. Is it expected that the big market in mid-March will arrive earlier?
- Did you know the "bull rule" in the Bitcoin halving market?