The strongest and most brain-burning anti-eavesdropping cryptography in history: Quantum key distribution
Bohr said that if someone heard the quantum theory for the first time, he was not annoyed, indicating that he did not understand.
This sentence shows that everything related to quantum becomes complicated, anti-conventional, counter-intuitive, that is, it is not easy to understand.
The following movie pictures just add some relaxation before the class, the following content is still very brainburn, please don't lose seriousness because of entertainment. I hope that we will unite and be nervous and hope that the atmosphere will be serious and lively.

- Holding $7.6 million, Ethereum's most gas-consuming contract, FairWin, is accused of being a Ponzi scheme.
- Science | What is cDai?
- “I am sorry, we are not “traditional banks””

There are always eavesdropping plots in the movie, and the decent factions are all in use, but the cryptography in the movie is relatively simple, that is, the high-performance military bugs, and the anti-reconnaissance is generally suspected, with the detector to find, this Is the practice of very weak chicken, how to anti-eavesdrop? The best anti-eavesdrop is that once someone eavesdrops, I immediately know that someone has eavesdropped. Here is what we are talking about, and it is the most advanced way of playing human beings: quantum communication.
The previous article talked about a lot of encryption, but there is a problem that is not solved, that is, the communication problem, the key is complicated to make it difficult for others to crack it, such as Enigma machine encryption; the overall security is another One thing, such as this encrypted key is known to others, this person is someone other than the recipient.
Review the basic principles of cryptography
A (alice) wants to transfer a word to B (bob), so she thought of the shift replacement encryption method I learned in the previous article. For example, the word is btc, "letter plus one" is cud, meaning nothing or true. The meaning is not the meaning of the original text.
The word Btc is the original text or plain text, and the actual output text is cipher text. What is the secret key? The letter plus one, for the information received Bob knows the secret key, so he subtracts one letter for each cud, you get the original BTC, so that is decrypted.
The transmitted thing is called the key (secret key). This key is theoretically possible to be cracked. Even the key that can't be cracked now, if the key is eavesdropped, it will be directly cracked.
So cryptography has two pieces of content: the secret key and the pass key. Both are safe and truly safe.
If there is a measure, as long as someone else has eavesdropped on your key, the key will change after the eavesdropping, and the transmission will be very safe.
Quantum communication
This is a very complicated problem. Today we are only talking about the quantum key distribution mechanism in quantum communication, which does not involve quantum entanglement and quantum computing . The earliest mechanism of this mechanism is the BB84 protocol, the first key distribution protocol in quantum cryptography, proposed by Bennett and Brassard in 1984. It is also one of the most used and quantum key distribution schemes (there is an improved version later, The general principle is close, belonging to the same category).
This protocol is implemented with two channels, a classic channel and a quantum channel . The classic channel is to ensure the information exchange of sending and receiving information, such as email, telephone, etc. In the context of this article, the classic channel is not related to eavesdropping; quantum channel, as its name implies, is the quantum state.
The following is two explanations about the distribution of quantum key. The reason for writing two explanatory models is that you can understand the magical key distribution by one of them or by combining the two models.
The first explained simplified model
Simplified elaboration of the uncertainty principle
For example, photons have a circular polarization state and a linear polarization state, left-handed, right-handed, up-and-down (vertical), left and right (horizontal).
The weird thing is coming, and the measurement process affects the measurement of the photon polarization state.
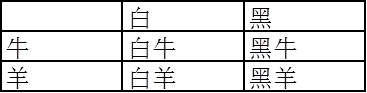
For example, there is a shed, I will observe it. In order to make a more realistic analogy, normal humans suddenly see that this is a white cow. So, we can see through the hole in the wall of the cowshed, only one can be seen at a time. The small area, for example, first saw it is white, then moved the lower angle to see that it is a horn. Then there is a white cow.
Whether I look at the color first or look at the corner first, the final conclusion is the white cow. It won't be a black sheep, a white sheep, or a black cow. But in the quantum world, this is not the case. What you see may be a cow – this is a joke, you may see an Aries, a black cow, etc., because the relationship between the two is random.
The results of measurements inside the quantum are related to the measurement process. It is entangled before it is observed. It is not clear what state it is, and it is not known what state it was before the measurement.
For example, if you measure a photon, the state of the photon is simplified: circular polarization and linear polarization. You observe the circular polarization first, then measure the linear polarization, and you get a left-handed horizontally polarized light. As you look at the species after looking at the color as seen above, you get the white cow.
However, if you look at the circular polarization and look at the circular polarization first, you may get various states that are random. The analogy macro phenomenon is that you look at the species first, then look at the color, not necessarily white cattle, you may get black cattle, white sheep, black sheep.
This is quite strange. And after the measurement, the state of the photon changed. Before the measurement, it was an entangled state. Similar to Schrödinger's cat, I didn't know if I died or not. After the measurement, it changed. Similar to a white cow in the shed, you become a black sheep after reading it.
The order of observation affects the observations.
Ok, the theory is explained, now let Alice send Bob another message. Just make sure that the secret key is safe for Bob, and the ciphertext can be sent to Bob publicly.
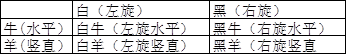
Alice emits some photons to Bob, for example six photons. She went to measure as shown in Figure A.

At this time, Bob also received the photon. He also measured it according to his own method, such as the B picture.

Of course, the analogy of changing the above type to black and white and cow and sheep is the same.
Then Alice gave Bob a call and said that your 1, 5 and 6 measurements are the same.
Then, the results of 1, 5 and 6 should be the same. Don't worry about other strategy methods.
Different states can be easily recorded as 1 and 0 in front of the computer. For example, the left-handedness is 1, the right-handedness is 0, the vertical is 1, and the level is 0. At this time, the key of the above figure is 111. This photon number is more. Some, so you can get a set of random numbers, and then this is the secret key. It is possible to come out with a string of numbers such as 101010000010100010.
At this time, the eavesdropper name C appeared, called Caocao. At this time, he "eaves" the photon 1, he also measured the circular polarization and found that it was left-handed. At this time, Bob received photon 1, and his measurement was also circularly polarized. The result is unchanged. Bob won't find this.
However, caocao does not know how a and b are measured. Caocao goes to measure photon 1 with linear polarization. At this time, the result is horizontal. At this time, Bob receives the photon, and then the circular polarization state he measured is not necessarily left-handed. Because, according to the above, the measurement process will affect the measurement results , then his results are different from Alice, and then he knows that he has eavesdroppers. Caocao can't guess every time when eavesdropping. After such a string of numbers reaches a certain length, as long as there is an eavesdropper, A and B will know that their information has been eavesdropped after some comparison. Change a set of passwords.
A simplified model of the second interpretation:
The BB84 protocol also has a more general classic explanation.
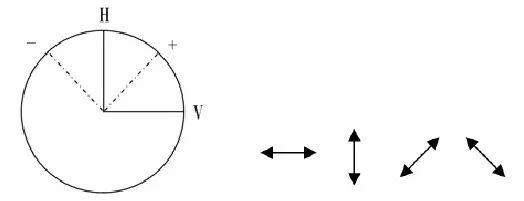
Four different polarization states of photons, 0 degrees, 90 degrees, 45 degrees, 135 (the two states of linearly polarized photons and circularly polarized photons are orthogonal to each other, but the states between linearly polarized photons and circularly polarized photons are not correct. Cross, so there are different angles, this can be associated with the first explained model, as shown above.
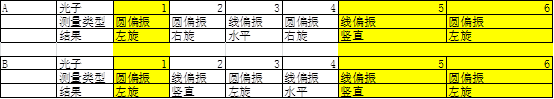
1, Alice can randomly select the polarizer, and the + or x-shaped polarizer randomly generates a polarization state;
2, the photon of the selected polarization direction is sent to B through the quantum channel;
3, Bob also randomly selected + or x-shaped polarizers to measure the polarization direction of photons;
4, B will keep the measurement results confidential, and at the same time, tell the Alice through the classic channel;
5, A contrast and B used polarizers, then the classic channel tells B those who are the same as her, those are not the same;
6, B discards the results of the different polarizers used with A, and retains the same polarizer results as A, which statistically shows that it should be thrown away by half.
The polarizer is randomly arranged, and after the A is aligned, the key is formed and the encryption process begins. It is stipulated that what state corresponds to 0 and what state corresponds to 1 can easily correspond to a key composed of 0 and 1.
In simple terms, the quantum key is prepared by utilizing the polarization of photons . Is this safe? Yes, at this time, C appeared to be eavesdropping. After intercepting the photon, he began to measure with a polarizer. At this time, his error rate is also 50%. After the measurement, he sends it to B, B does not know, and then eavesdrops on the classic. The information of the channel knows how to discharge the correct polarizer, but it is not right, because when he measures the photon, the photon has changed. If the two check the measurement results, they will find that B is not secret, then this shows that This path has been eavesdropped.
Of course, you have to ask C that after eavesdropping on the photon, you can not measure it, but generate a photon of the same photo, and then send the original photon to C. Isn't that okay? Does this also make the quantum state change? However, it is impossible, because quantum, there is another feature that is not clonal, and it is impossible to generate another identical photon.
To put it more bluntly, in fact, the transmission and generation of quantum keys occur simultaneously .
Because B accepts the photon, the classic channel tells A, what kind of measurement method he uses (cross or cross-polarized polarizer), A will use the same order of polarization as B to encrypt the information. When B receives no photons, the secret key has not yet been generated.
All of the above are one of the basic ways of quantum key distribution. Quantum encryption is currently the world's highest-end encryption method, but there are applications that have not yet been applied on a large scale . Note that the above is just the principle of secret key distribution in quantum encryption, not the encryption of the key itself. Recently, vocabulary such as quantum computing, quantum encryption, etc. have become commonplace, and this concept has also entered people's field of vision.
What about quantum computing? Is it possible to crack our bitcoin private key, is my encrypted asset already unsafe?
Don't worry, don't worry, the exchange is in a hurry. Let's just say, if someone can use the quantum computing power to encrypt and decrypt, then people can't see the tens of thousands of bitcoins in your wallet (if you have one), directly It would be great to attack the global financial system.
Quantum computing is more complicated, and the next article will talk about the recent concept of this.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Read the relationship between Filecoin and IPFS in one article: Is Filecoin really the next gold mine?
- Viewpoint | Reward points are meaningless compared to blockchain rewards
- The financial structure of the Ethereum Ecology: How does it work?
- Popular Science | Long-distance attack problem of PoS protocol
- Former Federal Reserve official 怼 Bank of England Governor: The idea of cryptocurrency replacing the US dollar is unreasonable
- Analysis: What opportunities, challenges and risks will be brought by blockchain technology for digitalization of securities?
- Stable currency analysis: Most stable coins will not be used for large transactions except USDT





