Weekly Update | Web3 Security Incidents Result in Approximately $1,996.3 Million in Losses
Weekly update Web3 security incidents cause $1,996.3 million in losses.Overview
According to the SlowMist Blockchain Security Incident Database (https://hacked.slowmist.io), there were a total of 10 security incidents with approximately $19.963 million in losses from August 14th to August 20th, 2023.
Specific Incidents
MEV Bot
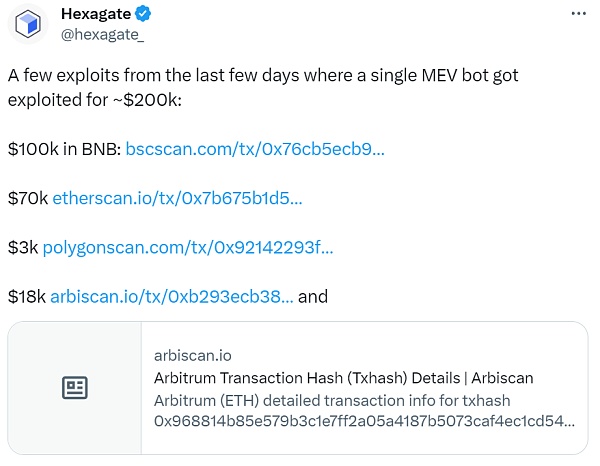
On August 14th, 2023, Hexagate tweeted that a single MEV Bot had been exploited for approximately $200,000 in the past few days, including BNBChain, Ethereum, Polygon, and Arbitrum.
- Hover Research Next Generation Lending Protocols | Part One
- A Quick Look at the Top Ten Winning Projects of ETHGlobal Superhack 2023
- What is happening in the intent-centric track? Which projects are worth paying attention to?
Zunami Protocol
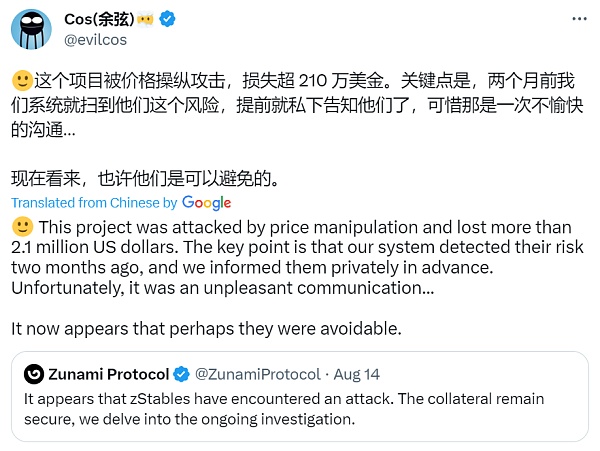
On August 14th, 2023, the Zunami Protocol on Ethereum suffered a price manipulation attack, resulting in a loss of 1,179 ETH (approximately $2.2 million). The attack was caused by a vulnerability in the contract where the LP price calculation depended on the contract’s own CRV balance and the exchange rate of CRV in the wETH/CRV pool. The attacker manipulated the LP price by depositing CRV into the contract and manipulating the exchange rate of the wETH/CRV pool. According to MistTrack analysis, the ETH has already been transferred to Tornado Cash.
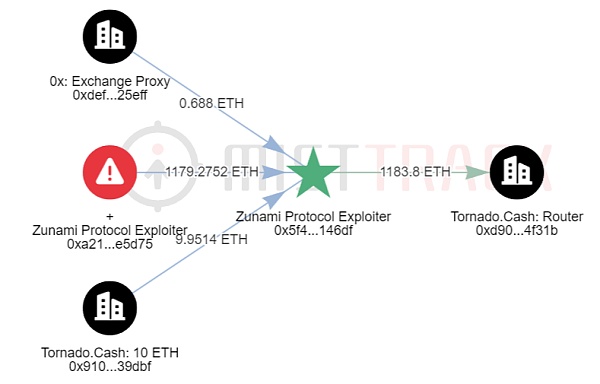
It’s worth mentioning that our system detected this vulnerability earlier, and we kindly alerted the project team about it. However, they did not take it seriously, and it was too late when the incident occurred.
Metis
On August 15th, 2023, the official Twitter account of Metis, an Ethereum scaling solution, was hacked. According to the official statement, a team member fell victim to a SIM swapping attack, allowing the malicious actor to take control of the account for approximately 30 hours.
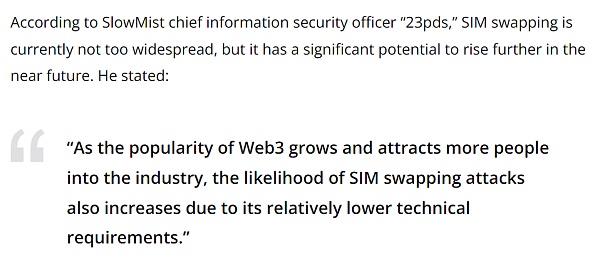
The purpose of a SIM swapping attack is identity theft, where the attacker takes over the victim’s phone number, enabling them to access bank accounts, credit cards, or crypto accounts. SlowMist’s CISO stated in an interview with Cointelegraph, “With the popularity of Web3 and the entry of more people into the industry, the possibility of SIM swapping attacks has increased due to its relatively low technical requirements. Such SIM swapping attacks are also common in the Web2 world, so it is not surprising to see them in the Web3 environment.”
(https://cointelegraph.com/news/crypto-sim-swap-how-easy-is-sim-swap-crypto-hack)
Since SIM swapping attacks do not require high technical skills from hackers, users must be vigilant about their identity security to prevent such attacks. To protect against SIM swapping attacks, we recommend using multi-factor authentication, enhancing account verification (such as additional passwords), or establishing secure PIN or password for SIM cards or mobile accounts.
Sei Network
On August 15th, 2023, the official Discord server of Sei Network was compromised.
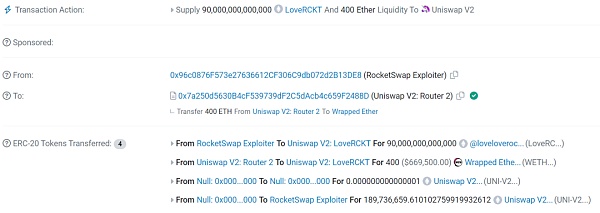
RocketSwap
On August 15, 2023, RocketSwap, a Base ecosystem project, was attacked. The attacker stole RCKT tokens and converted them to approximately $868,000 worth of ETH, which was then cross-chain transferred to Ethereum. The hacker then created a memecoin called LoveRCKT, possibly intending to manipulate market sentiment with the stolen assets for personal gain.
This incident has also raised doubts about RocketSwap, particularly regarding deployment processes and private key storage. However, the team denies any internal involvement and attributes this behavior to a third-party hacker. RocketSwap states, “The team needed to use offline signatures and store private keys on the server when deploying LaunchLianGuaid. Currently, it has been detected that the server was breached through brute force, and due to the use of proxy contracts in the farming contract, multiple high-risk permissions exist, resulting in the transfer of farming assets.”
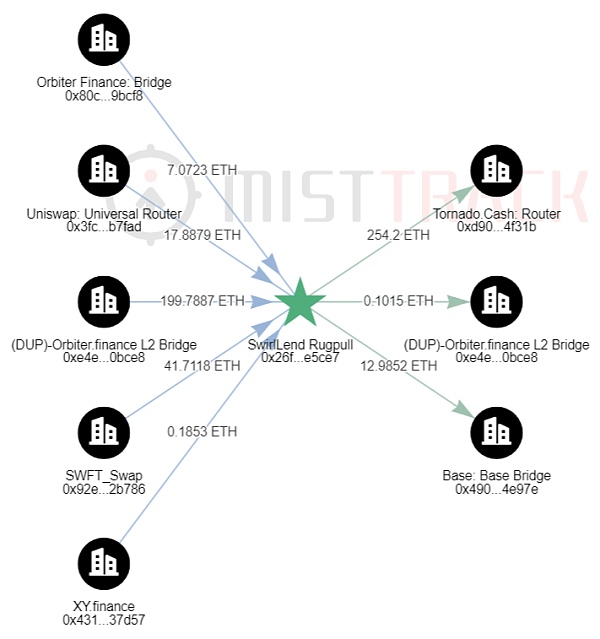
SwirlLend
On August 16, 2023, the SwirlLend team stole approximately $2.9 million worth of cryptocurrencies from Base and $1.7 million worth of cryptocurrencies from Linea. The stolen funds were cross-chain transferred to Ethereum. As of now, the deployer has transferred 254.2 ETH to Tornado Cash. SwirlLend’s official Twitter and Telegram accounts have been terminated, and its official website is also inaccessible. According to MistTrack analysis, the deployer used SwftSwap, XY Finance, Orbiter Finance, and other platforms. Additionally, the following IPs were discovered: 50.*.*.106, 50.*.*.58, 50.*.*.42.
Made by Apes
On August 16, 2023, on-chain analyst ZachXBT tweeted that SaaSy Labs APl, the on-chain licensing platform launched by BAYC, had a problem that allowed access to personal details of MBA applicants. This issue was reported to Yuga Labs before disclosure and has now been fixed. Yuga Labs responded that they are unsure if there has been any data misuse and are contacting anyone who may have had their information exposed. They will provide fraud and identity protection to any affected users if necessary.
(https://twitter.com/zachxbt/status/1691514780119343104)
Exactly Protocol
On August 18, 2023, DeFi lending protocol Exactly Protocol suffered an attack, resulting in a loss of over 7,160 ETH (approximately $12.04 million). The attackers used two contracts to launch the attack by repeatedly calling the kick() function and transferred the deposits to Optimism using a developer contract on Ethereum. Eventually, the stolen funds were transferred back to Ethereum. It is understood that the root cause of the attack on Exactly Protocol was insufficient_check. The attacker bypassed permission checks in the DebtManager contract’s leverage function by directly passing unverified false market addresses and changing _msgSender to the victim’s address. Then, in an untrusted external call, the attacker re-entered the crossDeleverage function in the DebtManager contract and stole collateral from _msgSender. Exactly Protocol tweeted that the protocol has been unsuspended, and users can perform all operations without any liquidation occurring. The hacker attack only affected users utilizing the peripheral contract (DebtManager), and the protocol is still functioning normally.
Harbor Protocol
On August 19, 2023, Harbor Protocol, a cross-chain stablecoin protocol in the Cosmos ecosystem, tweeted that it had been exploited, resulting in some funds in the stable-mint, stOSMO, LUNA, and WMATIC treasuries being depleted. According to the information collected so far, the attacker used the following address to execute all operations: comdex1sma0ntw7fq3fpux8suxkm9h8y642fuqt0ujwt5. It is reported that Harbor Protocol lost 42,261 LUNA, 1,533 CMDX, 1,571 stOSMO, and 18.6 trillion WMATIC tokens in the attack.
Thales
On August 20, 2023, Thales, a derivatives market, announced that a core contributor’s personal computer/Metamask was hacked, and some hot wallets that served as temporary deployers ($25,000) or admin robots ($10,000) were compromised. Please do not interact with any Thalesmarket contracts on the BNB Chain and revoke any pending contracts. All funds on Optimism, Arbitrum, Polygon, and Base are safe. Thales stated that it will officially abandon support for BSC due to this attack.
Summary
There were two incidents this week caused by private key leaks. Incidents resulting in losses due to improper management of project party private keys are also common, such as the Ronin Network incident with a loss of over $610 million, the Harmony incident with a loss of over $100 million, and the Wintermute incident with a loss of over $160 million. There are many reasons for private key theft, and the security of project party private keys mainly involves three aspects: private key cracking, social engineering attacks, and ecological security. Due to the importance of private keys, raising the security storage level (such as hardware encryption chip protection) and eliminating single points of failure are important means of preventing attacks. It is also possible to consider reducing single points of failure in the backup of private keys/mnemonic phrases and using secure backup methods, media, or processes. For specific details, please refer to SlowMist’s cryptocurrency security solution: https://github.com/slowmist/cryptocurrency-security.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ethereum Ecosystem Privacy Use Cases and Project Overview
- LianGuai Observation | TVL exceeds 200 million in the first month. Why do both old and new projects love Base chain?
- Optimism Feast is Coming? A Comprehensive Overview of OP Stack Ecological Projects
- Why has RWA suddenly become popular this year? What are the players?
- The first Bitcoin Sovereign Rollup project Rollkit.
- The New Narrative of Cryptocurrency Investment in a Bear Market Unibot Project Analysis
- Cosmos ecosystem’s living water Entangle and Tenet, the dual heroes of the whole chain LSD.






