zkSci How is zero-knowledge proof applied in scientific research?
zkSci Applying zero-knowledge proof in scientific research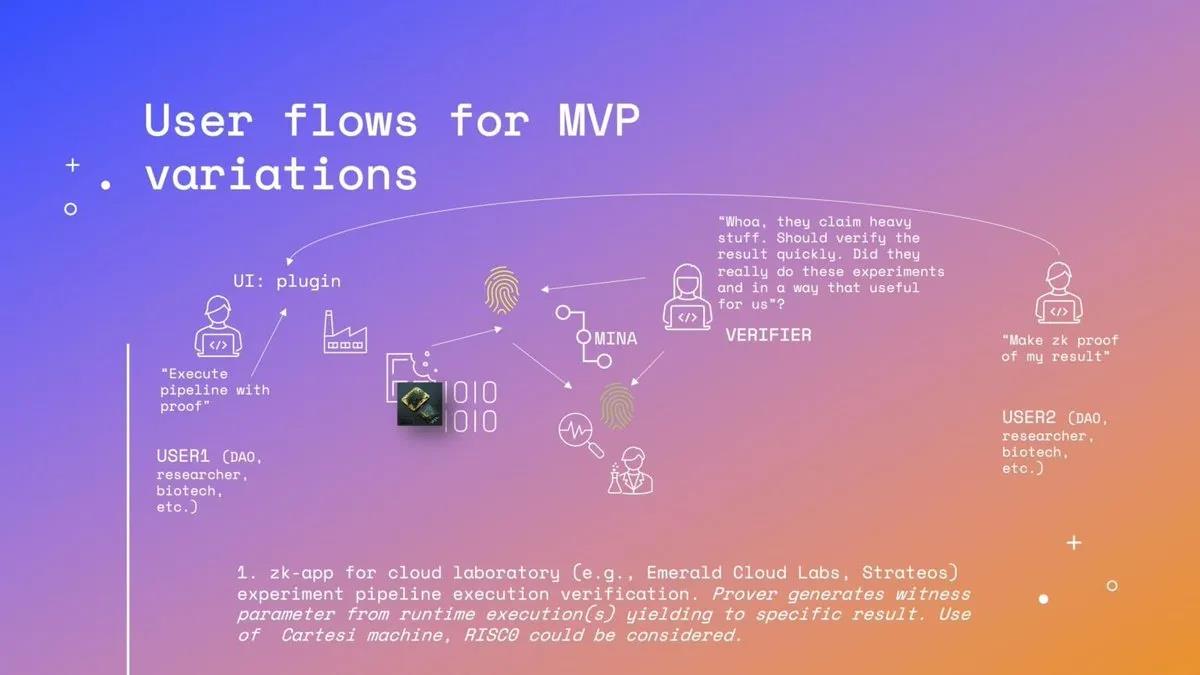
Written by: Samuel Akinosho
Translated by: TechFlow
The term “zkSci” came to my mind while I was drinking coffee at Starbucks and writing this article. I have previously written articles about DeSci because I am fascinated by the fusion of decentralization (blockchain) and science. A few months ago, I joined a new company that focuses on improving privacy in zero-knowledge proofs, which led me to delve into the field of zero-knowledge proofs and explore their potential connections with the scientific field. Here, I will share my research and discoveries so far.
- How to Report Being Scammed When Buying USDT Virtual Currency, Lawyer Teaches You
- Blockchain User Activity Survey Ethereum Still Reigns, Who is Using Litecoin and Tron?
- Trillion-level business opportunity In-depth analysis of the prospects of security tokens in Hong Kong
Zero-Knowledge Proofs in Scientific Research
Privacy has always been a major concern when sharing sensitive data in various research fields. Zero-knowledge proofs offer a promising solution in several practical application areas where secure and privacy-preserving data sharing is desired.
Medical Data Sharing
Medical research often involves collaboration among multiple healthcare institutions and researchers who need access to patient data for analysis. However, directly sharing raw medical data raises privacy and confidentiality concerns. Zero-knowledge proofs can overcome this challenge by allowing researchers to share aggregated statistical data or perform computations on the data without revealing individual patient records. For example, researchers can verify the effectiveness of a new treatment method without accessing the personal medical information of patients, ensuring privacy and compliance with data protection regulations.
Sound a bit unrealistic? Let’s delve into the process:
Sharing Aggregated Statistical Data: Researchers can use zero-knowledge proofs to demonstrate statements about aggregated statistical data. For instance, they can prove that the average age of patients with a specific disease falls within a certain range without disclosing any individual ages. By sharing such aggregated statistical data, researchers can still derive valuable insights without compromising the privacy of individual patients.
Privacy-Preserving Computation: Zero-knowledge proofs enable researchers to perform computations on encrypted or hashed data without decrypting or exposing the underlying values. For example, researchers can use encrypted medical data to compute the effectiveness of a new treatment method while completely concealing the actual treatment details and patients’ medical records.
Leveraging zero-knowledge proofs in medical research offers significant advantages, improving scalability and collaboration in the industry. Zero-knowledge proofs empower multiple institutions and researchers to efficiently and scalably share data in large-scale medical research collaborations. This collaboration enables researchers to access aggregated data without exposing sensitive information or compromising patient privacy. It strikes a delicate balance between data-driven discovery and individual confidentiality, paving the way for transformative advancements in medical science while upholding the highest standards of data privacy and ethics. The collaborative environment fostered by zero-knowledge proofs accelerates research and promotes innovation in the medical field, ensuring that patient privacy is protected throughout the process.
In addition to medical research, various research collaborations involve sharing sensitive information such as proprietary algorithms, intellectual property, or confidential government data. Zero-knowledge proofs provide a powerful mechanism to verify the authenticity or correctness of shared information without revealing the actual content. This capability enhances collaboration and trust among the parties involved in research projects without compromising confidentiality.
Secure Remote Computing
Secure remote computing is an important aspect of scientific research that requires handling sensitive data without exposing it to third parties. Zero-knowledge proofs (ZKPs) are particularly applicable in the following areas to achieve secure remote computing:
Secure Genome Analysis: Genome research involves large-scale analysis of genetic data to understand the relationship between genes and various diseases. However, genomic data is highly sensitive and contains personal information about an individual’s genomic composition. Using zero-knowledge proofs, researchers can perform secure computations on genomic data without transmitting the actual data to centralized servers. This means that different research institutions can collaborate on genome analysis without sharing the raw genetic data, ensuring privacy, maintaining data ownership, and advancing personalized medicine and disease treatment research.
Environmental Research: Environmental research often involves collecting data from various sources such as private companies and government organizations. Zero-knowledge proofs enable researchers to verify the accuracy of data provided by these entities without revealing proprietary information.
Climate Science and Climate Modeling: Climate research involves complex models and simulations that are typically run on distributed systems. Zero-knowledge proofs can be used to verify the results of these simulations without revealing underlying data or algorithms.
Benefits of Avoiding Data Transmission to Third Parties
By not transmitting actual genomic data to centralized servers or third parties, zero-knowledge proofs enhance data privacy and security, reducing the risks of data leakage and unauthorized access.
This protects data integrity and ensures compliance with data protection regulations such as HIPAA or GDPR. Furthermore, zero-knowledge proofs enable secure collaboration between research institutions, allowing participants to compute on their data and only share encrypted proofs of computation results. This collaboration fosters trust and data privacy among the parties involved.
Additionally, zero-knowledge proofs reduce data transmission overhead in genome research, as only the proofs of computation results need to be exchanged instead of the raw data. This optimization simplifies collaborative genome analysis while protecting sensitive genomic data and promoting scientific advancements in personalized medicine and disease treatment. Overall, zero-knowledge proofs, as a transformative approach, facilitate secure and privacy-preserving genome research and enhance trust and efficiency in cross-domain research collaborations.
Proof of Origin
Proof of Origin is a key application of Zero-Knowledge Proofs (ZKPs) that ensures the authenticity and integrity of scientific papers, research data, medical records, and other documents. By leveraging zero-knowledge proofs, organizations and individuals can establish verifiable sources and histories of data, ensuring trust and reliability in an era filled with misinformation and data tampering.
Ensuring the authenticity of scientific papers, research data, and medical records: With the rise of online publishing and the abundance of digital content, ensuring the authenticity and integrity of scientific papers, research data, and medical records has become crucial. Researchers can use zero-knowledge proofs to generate cryptographic proofs that verify the source and authorship of scientific papers and research data. By doing so, they can demonstrate that their work has not been tampered with or distorted, enhancing the credibility and reliability of their findings, which is particularly important in an age of information manipulation and increasing misinformation.
Unfinished Conclusion
I firmly believe that zkSci has tremendous potential to improve scientific research. The power of zkSci lies in its ability to ensure data privacy and security, enabling researchers to collaborate, share sensitive information, and perform computations on encrypted data while protecting individual privacy and data ownership. This innovative approach has the potential to accelerate progress in various scientific fields, including genomics, medical research, and environmental studies, among others.
As I delve deeper into the world of zero-knowledge proofs, I am pleased to see ongoing research and development actively addressing the challenges related to computational costs and scalability. This fills me with hope for more researchers and institutions adopting ZKP as a privacy-preserving technology, paving the way for a future where data privacy and scientific advancement coexist harmoniously.
If you are a developer or entrepreneur interested in contributing to zkSci, the Mina protocol provides practical resources and tools such as SnarkyJS (a TypeScript-based framework) that allow you to create zero-knowledge applications without cryptographic expertise.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Unable to guard against Why are a large number of encrypted Twitter accounts hacked and used to publish phishing links? How to prevent it?
- Tornado Cash founder arrested, what original sin did the mixer commit?
- Why are Layer2 tokens not used for paying network GAS?
- Is an encrypted market maker the ‘behind-the-scenes dealer’?
- a16z Why It’s Said that Stateless Blockchain Cannot Exist
- a16z Research on the Impossibility of Stateless Blockchain
- a16z Crypto Partner discusses NFT Royalties How it Works, Evolution, and Solutions