Quick Look at the 13 New Projects Shortlisted for the ETHGlobal New York Hackathon Finals
13 New Projects Shortlisted for ETHGlobal New York Hackathon FinalsWritten by: ETHGlobal
Translation: Frank, Foresight News
From September 22nd to 24th, ETHGlobal held the ETHGlobal New York Hackathon in New York City, with a total of 13 projects making it to the finals, covering various fields such as blockchain gaming infrastructure, Telegram bots, AI, cross-chain interoperability, and more.
Among them are some interesting innovative projects, including F.A.S.T., a Telegram transfer bot that supports photo recognition, ConsciousNFT, which creates intelligent background stories for NFTs, A.S.R., which allows users to recover ownership of their smart contracts after losing their signing private keys, and more. This article will provide a brief introduction to the finalist projects.
- Inventory of 10 blockchain projects that recently received investments from well-known VCs Freatic, LianGuairallax, Socket…
- Sorry, we failed. Multiple projects have been shut down one after another. Is the shutdown wave coming to the cryptocurrency industry?
- Multiple projects announce shutdowns in succession, is the encryption industry ushering in a ‘shutdown wave’?
FRAMED!
FRAMED! is a fully on-chain and trustless hidden information game (Mafia) built on fhEVM, where an art thief steals a painting from a museum and players are randomly assigned roles such as citizen, thief, police, or detective. The goal of the game is for the thieves to eliminate the citizens, while the citizens must work together to identify and vote out the hidden thieves. Players need to engage in discussion and social deduction, and must cooperate and deceive each other.
What sets this game apart is its ability to store encrypted states directly on the blockchain. Fully Homomorphic Encryption (FHE) smart contracts allow for computations on encrypted data without the need for decryption. This innovative solution addresses privacy restrictions and guarantees.
F.A.S.T.
F.A.S.T. is a Telegram bot that uses image indexing technology, allowing users to register by taking a photo of themselves, and then make payments to someone’s wallet address using other people’s portraits (group photos, etc.).
ZeroTrustBounty
ZeroTrustBounty aims to address the challenges of traditional bug bounty platforms – enterprises must trust third parties with sensitive data, while white-hat hackers cannot guarantee payment for their services. In other words, white-hat hackers report a vulnerability to a bug bounty program but do not receive compensation.
ZeroTrustBounty solves this problem by using TLS attestation and the Lit protocol. Assuming there is an SQL injection vulnerability, ZeroTrustBounty allows white-hat hackers to hide the attacking HTTP requests, but show cryptographically verified HTTP responses, so that the affected enterprise can cryptographically verify the white-hat hacker’s report and understand its impact.
For the payment part, ZeroTrustBounty uses the Lit protocol to encrypt the HTTP requests/responses, and the enterprise can only decrypt them after making a payment to a specific address or holding an NFT. This way, if the enterprise intends to fix the vulnerability, it can ensure payment and eliminate issues such as white-hat hackers not receiving compensation or third-party services stealing vulnerability techniques/reports. It also solves the problem of enterprises disclosing sensitive information to third-party services.
Doom Arena
Doom Arena is a distributed DApp for managing and creating game competitions. It allows developers to host competitions, provides incentives for players, and generates revenue for developers. It introduces a novel approach to organizing game competitions, using the example of the original Doom game.
These competitions are completely based on blockchain and decentralized, creating a new avenue for economic creation for game developers. Game developers and influencers can initiate competitions through their games and provide attractive prize pools to motivate participation.
The host initiates the competition by funding the APE token as the initial prize pool. Players will use their ENS profiles to log in and pay APE to purchase tickets to enter the competition. 90% of the funds are used to increase the prize pool, while 10% goes to the host. On average, after 100 players pay tickets to participate in the competition, the host can recover the costs.
In summary, the project creates a decentralized platform for hosting game competitions and provides an innovative way for game developers to promote their works and attract players. It establishes a sustainable game promotion economic model. Anyone can initiate or participate in competitions and contribute to a vibrant game ecosystem.
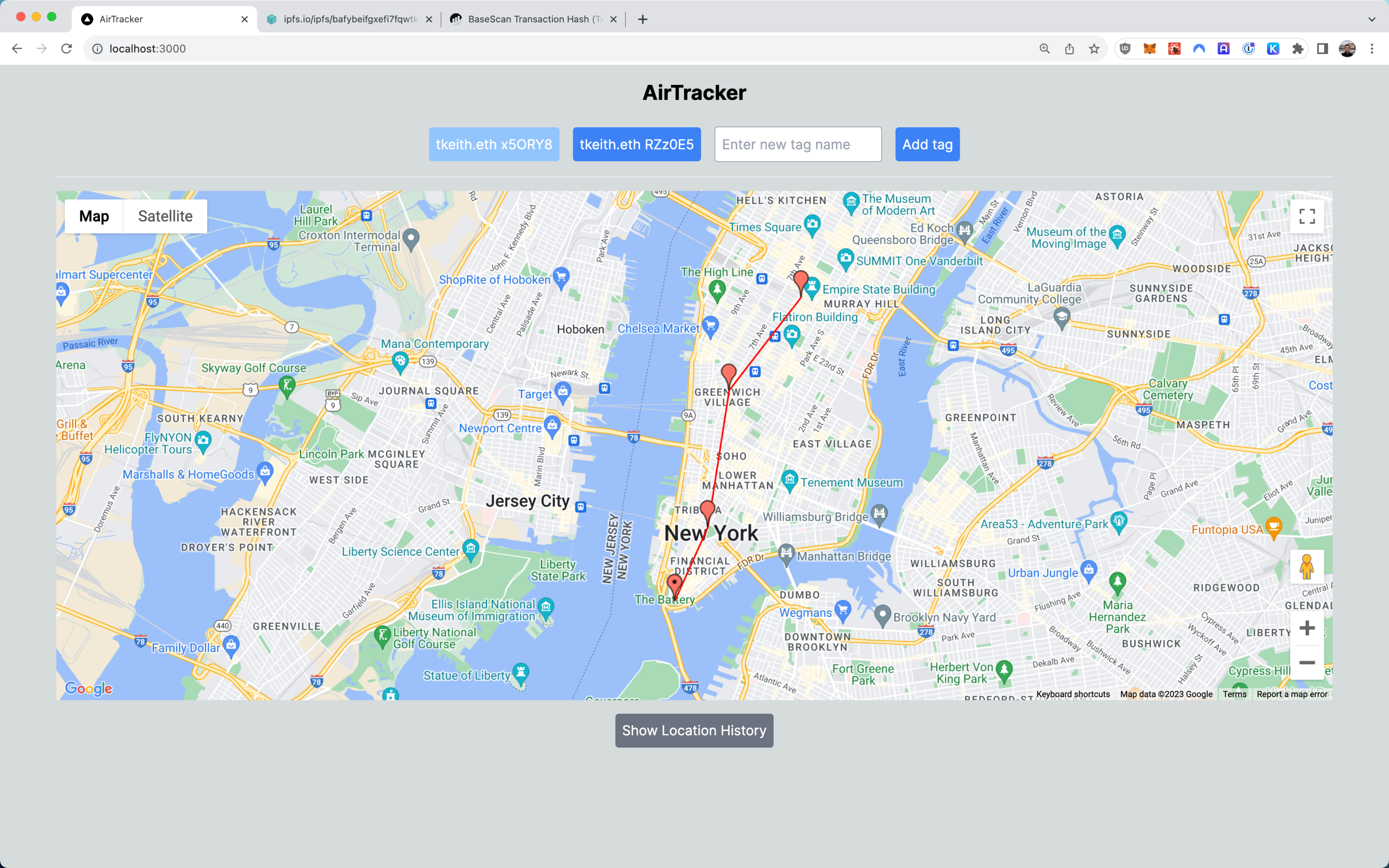
AirTracker
AirTracker uses AirTags and blockchain to store and transmit messages for decentralized physical asset tracking. It first captures the location data of each AirTag asset through Apple devices and stores it on the chain and IPFS. Location updates are also sent via XMTP and ENS lookup is performed using AirStack.
Users can log in to the Web UI to view the historical locations of each asset on the map, as well as specific time and location updates. In addition, users can share the asset’s location with anyone or any application by simply sharing the randomly generated tag name (also known as the location encryption key).
SafeCreate2
SafeCreate2 uses a single-chain Safe to protect multi-chain smart contract deployment, allowing a Safe on a single chain to deploy smart contracts to the same address on all chains without bridging ETH. It also allows a Safe on a single chain to perform management functions on any multi-chain contract.
It uses Axelar to send and receive cross-chain messages to ensure no address conflicts, and each Safe on each chain receives a unique deployment namespace. It also implements a CrossChainOwnable contract, which allows applications using this tool to inherit the contract, enabling Safe to securely manage multi-chain contracts on a single chain.
ConsciousNFT
ConsciousNFT is an AI tool for NFT projects that awakens the conscious identity within NFTs. It provides an AI engine toolkit for founders and owners of NFT projects to collaboratively build rich internal worlds, giving NFT artworks unique personalities, background stories, conversational abilities, and narrative depth, making them conscious characters.
These include creating challenges and tasks, allowing NFTs to compete and receive generative NFT rewards; writing interactive narratives to establish relationships, engage in battles, or seek adventures within conscious NFTs.
Through ConsciousNFT, users can mint trained LLM models onto the blockchain to preserve interactive character identities for NFTs, giving each PFP a conversational personality, authorizing PFPs to cultivate fan communities, and transforming static NFT art into sentient digital characters, and more.
SLianGuaice Guardians
SLianGuaice Guardians aims to develop secure solutions for the social key recovery scheme MetaMask Snaps + Cryptosat Satellites, addressing management issues related to notification and audit tracking to reduce the possibility of collusion among guardians.
It utilizes the MetaMask Snaps framework and integrates it with the backend API of Cryptosat Satellites digital twins (lab/testing environment) for storage and event auditing. The repository includes frontend web products and backend APIs.
A.S.R.
A.S.R. (Anti Social Recovery) is a design pattern that allows users to recover ownership of their smart contracts after losing the signing private key.
It enables users to deploy smart contracts that are associated with their unique identity proofs (e.g., World ID). After verification with the World ID, users can deploy the contract and then take over ownership from different EOAs.
This design pattern can be applied to various use cases and is suitable for any smart contract role (Minter, LianGuaiuser, Burner, etc.). Additionally, World ID can be exchanged with different identity proof providers, and considerations are made for applying it to ERC20 tokens, allowing users to claim balances from new addresses.
The currently supported operations include:
- Login with a wallet;
- Verify identity with World ID;
- Deploy smart contracts as an owner;
- Import existing smart contracts;
- Transfer smart contract ownership to a new EOA address held by the World ID holder.
MEVictim Rebate
MEVictim Rebate identifies MEV victims using historical on-chain data and airdrops an ERC-721 token to grant access to the token-gated Uniswap v4 pool on Scroll, thereby designing better market incentives.
Specifically, the project identifies MEV victims on ETH Goerli and grants these victims an ERC-721 token. When the holders provide liquidity to the Uniswap v4 pool on Scroll, they are eligible for rebates. Ultimately, the project incentivizes better interaction behavior on Scroll based on users’ historical chain data on ETH Goerli.
The subgraph of ETH Goerli transactions is used to identify MEV victims (individuals affected by frontrunning, sandwich attacks, etc.). Then, the transaction hashes and log IDs are provided as inputs to the Axiom circuit.
Axiom Circuit uses transaction hashes to prove whether a wallet address is indeed a victim of MEV attacks. If the conditions are met, the corresponding wallet address will receive an ERC-721 token, which can then be bridged to Scroll.
RealReturn
RealReturn is an open leaderboard for verified real investment returns. It allows anyone to publicly prove their investment returns without having to share their credentials with anyone or any entity.
It employs cryptographic techniques such as third-party TLS and MPC to handle TLS sessions between users and application servers. Although the session content remains visible only to the user and the application server, a notary can generate something on the side to prove that the records have not been tampered with.
Abstract Wallet
Abstract Wallet uses Solidity FCL to implement Userop driven by WebAuthn. Users only need to have a smartphone to use the account abstraction feature with a key, enabling users to log in with a single click.
With just a single click, users can generate key credentials, smart accounts, and mint NFTs. When users click to create an account, it uses the biometric feature of the smartphone to generate a FIDO key.
This FIDO key is stored in the smartphone’s secure enclave, providing protection for the private key (unlike browsers that store it in an insecure memory area). The derived public key from the key credential is pushed to the main contract on the chain, and subsequent transactions will use this key for authentication.
XSafe
XSafe optimizes the multisig process of Gnosis Safe for cross-chain usage, with the core goal of reducing the time and complexity involved in performing the same management functions across multiple blockchain networks.
Users only need to sign once, and the signature will automatically propagate to all connected blockchain networks to execute a single transaction across multiple networks. The workflow includes:
- Initialization: Users integrate X-Safe as a custom module through Gnosis Safe UI (one-time setup);
- Transaction creation: Users or administrators create transactions that need to be executed across multiple blockchain networks;
- Signature generation: Users sign the transaction using their private key through the X-Safe interface;
- Signature propagation: X-Safe propagates the generated signature to the corresponding Gnosis Safe contracts on all integrated blockchains;
- Transaction execution: Once the required number of signatures is collected, X-Safe triggers the execution of transactions on all chains simultaneously or in sequence according to user settings;
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Inventory of Binance Labs’ sixth season incubation projects
- 12 New Projects A Summary of Binance Labs’ Sixth Season Global Incubation Program
- 12 New Projects Binance Labs’ 6th Season Global Incubation Program Projects Overview
- Overview of the 12 incubation projects in the sixth season of Binance Labs
- Quick look at the first batch of 24 selected projects for the Variant Founder Fellowship.
- Eclipse Mainnet Architecture Introduction Ethereum SVM L2
- Banana Gun Research Report How did this sniper rifle make its way to the top of the TG BOT queue?