Characters | From the founder of Hyperledger to the creation of a safe $7.5 billion financial technology empire, "pragmatic" thinker Lu Yifan
Produced | blockchain base camp (blockchain_camp)
He was one of the first two founders of the IBM Hyperledger Fabric, the drafter of the Hyperledger white paper; he brought a team of less than 10 people to the current blockchain to more than 80 people today, as a financial valuation of more than $7.5 billion One of the products of the credit account;
He and the team's blockchain underlying platform to achieve cross-validation and four calculations in full encryption, optical single-chain can reach 50,000 pen / sec TPS, and can multiply TPS by multi-chain technology. At the same time, the current time of the current affairs transaction is less than 0.01 seconds.
- Viewpoint | The Way to Success in Digital Money: Valuation Models and Network Effects in Chaos
- The US Congress blocks the truth and opportunity for Facebook to issue digital currency
- Eth2 progress: Eth2 test network is coming!
He clearly opposed the characteristics of privacy protection, decentralization and data traceability in the blockchain , and led the team to develop a 3D zero-knowledge proof, claiming that it is more than 10,000 times more efficient than zkSNARKs. There are multiple controversial security assumptions for zkSNARKs.
His team provides solutions for 20 domestic and international blockchain inspection projects such as Hong Kong Blockchain Trade Network (eTradeConnect) and China Customs Tianjin Port.
He is the general manager of the blockchain business and R&D department of Ping An Financial Accounts : Lu Yifan.
Not long ago, the battalion commander interviewed him at the Shenzhen Pingan Group headquarters to discuss the technology behind the security blockchain and the topics related to cryptography . He also puts forward valuable thinking on the current blockchain industry and applications in a highly speculative and sharp language.
Next, let's come together to get close to the blockchain of Ping An and the person behind the billion business line.
Founder from Hyperledger Fabric
To the helm of the blockchain business in Ping'an District
Campmaster : You can't get around with Hyperledger Fabric when you chat with them . After all, it is one of the benchmarks of the alliance chain in the industry. Can you share some of the stories behind the birth of this project?
Lu Yifan: I was supposed to be in 2013, when I was responsible for the strategic development plan of the WebSphere series products at IBM's middleware CTO office. At that time, we had an idea to develop some gamification things to IBM's BPM (Business Process). Manager) and middleware products, such as scores or medal rewards, and the result gradually evolved into a Coin.
At that time, it was the first time that the value of the Bitcoin was greatly increased. At the time, Amazon also made an Amazon Coin. We are inspired to think that this mechanism can also be applied to our BPM gamification.
Initially, this project was only responsible for the other two people, Binh Nguyen. We first found some interns to do an experiment. At the time, the 0.x Ethereum trials showed a demo that allowed game makers to exchange game coins with each other. Scenes. Later, in 2015, we began to develop from such an experiment into a later Hyperledger Fabric.

Earlier photos of the Hyperledger Fabric team (Luo Yifan, right three)
There are also some interesting episodes here. After the project was established, I and Binh’s then boss Jerry Cuomo only applied for five places. We internally said that these five people have Golden Tickets.
Campmaster : What was the reason for letting you drop the Hyperledger Fabric and choose peace?
Lu Yifan: I first received a call from a headhunter. I wanted to recommend a super account book to them. Later, I want to say what I am impressed. I think there are two main points.
One is that I am very curious about what kind of environment is working in China , because the WebSphere BPM development team was mainly in China at the time, and IBM was one of the few teams that put core software development in China at the time. I will communicate with them from time to time. I feel quite interesting.
The second is that I was always wondering where the value of smart contracts is. Ping An said that they support my research in this area, and more than 30 domestic subsidiaries can let me practice my ideas.

Leaving the Hyperledger Fabric team to go to the farewell lunch before the safety, most of the main staff of the Fabric team
Campmaster: Does your later research really prove that smart contracts are worthless?
Lu Yifan: The value is very limited. According to long-term practice, I now think that smart contracts are a big poison in the development of the alliance chain. The reason is that the smart contract itself is a string of code that can run in multiple organizations, and the logic of the code requires data to run through. But in a business environment, data sharing is impossible. No one will give you data at all. Smart contracts require data to run, and each participating compute node needs it. So this creates a contradiction in the use of smart contracts in commercial organizations, which is unrealistic.
In addition, I think the data hashing itself is also a major security hole.
Campmaster: What is the feeling after returning to work?
Lu Yifan: All said 996, our team rarely worked overtime. When I returned from lunch at 7 o'clock every day, most of the team was not getting off work. (laugh)

“95% of projects are ineffective blockchain projects, and a considerable proportion of serious security vulnerabilities exist”
Battalion commander: You have a clear-cut attitude on the concept of being blocked in the blockchain industry, such as decentralization, data traceability, etc. What do you think are the root causes of these problems?
Lu Yifan: I think it is the lack of research and development capabilities of domestic companies. Now everyone's attention is on technical issues such as block, smart contracts, agreements, etc., and real scientific research problems are rarely tried. In fact, as long as you read the blockchain project publicity press release, you will find that 95% of the projects are not as straightforward as the database to trace or digital signature tamper-proof.
For example, data can be traced, and data can be easily tracked by tagging. Why do you still need to use blockchain to solve this problem today?
There is also a database. In Bitcoin, the data is processed in batches. Before each block, it is necessary to determine the block by the labor quantity certificate, which causes the bitcoin to be inefficient.
The most terrible thing is the hashing. If a malicious person knows the approximate range and format of the data, it can easily collide with the data itself. The participants in the alliance chain know the data range and format. The hashing is actually equal to The data is half public.
Most blockchain projects feel like they are hot spots, and they are not practical or pragmatic.
Campmaster: So, what do you think the blockchain really should solve?
Lu Yifan: Decentralized ecology, but not at the expense of data sharing because no one shares data with you, uses chain separation and other methods to rebuild data islands.
Campmaster : Encrypting all data with cryptography seems to be a feature on FiMAX. What is the reason for this?
Lu Yifan: In fact, it is fundamentally putting an end to data privacy issues. The reason is that we found that most of the privacy protection programs are not ideal now. At present, the main privacy protection schemes have the following three categories:
The first category: the chain. The chain is originally to open the data island, but in practice, it is found that the chain is essentially equal to re-creating a data island. It is better to connect directly to the point-to-point. If you are afraid of data loss, you can use messaging. If you are afraid of tampering, you can add a digital signature.
The second category: hashing. Some banks have hashed their customers' address information. In fact, if you know that there are 1.4 billion people in China, everyone has an address. In an hour, I can hash 1.4 billion addresses on my laptop and then collide to get the raw data.
The third category: the secret key. The information is encrypted with the public key and the private key, and the public key is given to the other party, and the encrypted information can be opened. I don't think this has any value. The traditional TLS protocol has long solved this problem and has been widely used.
Campmaster: So, how do you protect privacy and solve these problems?
Lu Yifan: We have developed 3D zero-knowledge verification, which implements any relationship and calculation check of any ciphertext through two types of algorithms: zero-knowledge relationship verification and zero-knowledge full-synchronization verification. All data on FiMAX is encrypted.
Through 3D zero-knowledge verification, the "greater than", "less than", "equal" relationship and countless "add", "minus", "multiply", and "divide" calculations of different ciphertext data can be calculated and verified. Such operations are very useful for some scenarios, such as trade finance.
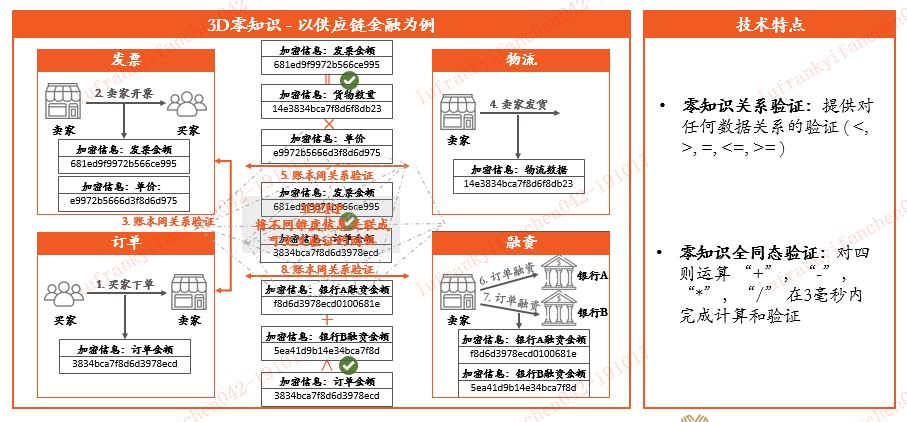
If I sell 1 million goods, I need to use 500,000 yuan of raw materials to finance, but because the data of each bank is actually not open, the company can take 500,000 to go to Bank A for financing, and then take 700,000 to pledge to Bank B for financing. .
Because Bank A will not tell Bank B that I have pledged 500,000 for this company, and once Bank B pledges it to 700,000, there is actually a big risk because the company is not able to repay so much. If Bank B conducts a ciphertext transaction through the blockchain network, it can be detected through zero-knowledge verification that the financing of the enterprise is actually a repeated pledge.
Campmaster: Multi-party secure computing ( MPC) seems to be able to verify the ciphertext. What is the difference between the two?
Lu Yifan: MPC is a relatively simple and rude implementation, but the problem is that the efficiency is particularly poor and there is no scalability, usually there will be multiple interactions at a time.
MPC generally needs to talk about data splitting and then split the data plus noise. The split data is calculated by a single or multiple third parties according to the scenario. Because the original encrypted data itself is split and there is noise, so the collaboration The calculation party will not know the original text. But here are a few big questions:
- It is necessary to prevent participants from obtaining some available information from the available data;
- It is necessary to coordinately confirm that the data after each spin-off is indeed from the original data;
- It is necessary to confirm that the result of the participant's calculation is indeed calculated from the data that it has assigned;
- There must be a certain defense to prevent a certain number of collaborative computing participants from "collusion" to get the raw data.
These problems can be solved by algorithms, but they all directly lead to the underlying efficiency of MPC.
In order to make MPC usable, some organizations are forced to add some "trusted" computing nodes by sacrificing security. But even this efficiency is still very poor. The 3D zero-knowledge protocol is not only 100 times more efficient than traditional MPC, but also non-interactive. It does not need to sacrifice security to improve scalability.
Campmaster: So, in the acquisition of data, how do we determine the authenticity of the data, rather than being falsely authorized by a third-party platform?
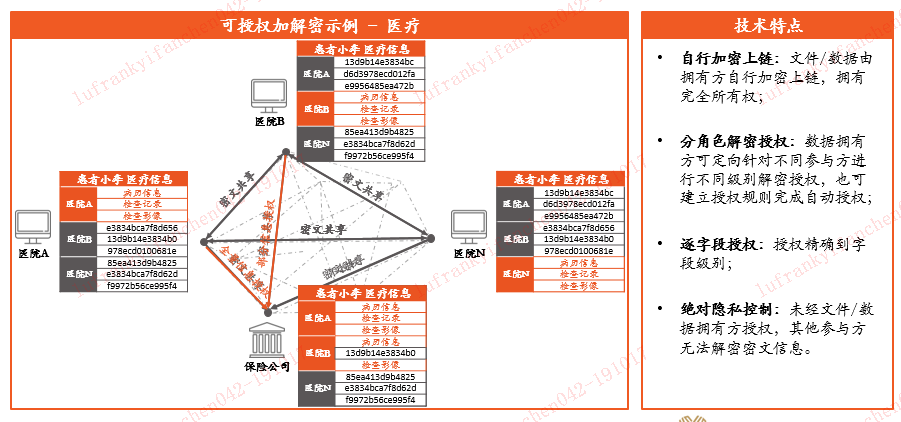
Lu Yifan: Let us take the medical data as an example. If Alice's case information and medical information are transmitted on the Internet, but they are all ciphertext, if Pharmacy X wants Alice's visit data, then Alice will open the data to the drugstore, which is no problem. But if the pharmacy does not pass Alice, but asks the hospital directly for data, how does the hospital determine that the pharmacy is not a pyramid scheme that steals data?
At this time, we use another technology, which is simply to turn a personal mobile phone into a virtual blockchain node, generate a unique personal key in the personal mobile phone, and then perform CA authentication to determine that the key must belong to Alice. At this time, the authorization request is sent to the hospital through the data network . The hospital knows that the request comes from Alice instead of the third party, and then the data can be opened to the drug room X.
Campmaster: What is the composition of the technical team in the current blockchain?
Lu Yifan: Our technical team is half of the underlying R&D and solution development. Our main technical framework is called S3C, and S refers to Sparrow, which is mainly used as an application solution. 3C refers to Cathaya, Core, and Concord, which are responsible for the encryption module, the underlying kernel, BNaaS, and CA, respectively. So the function of our team is basically built around these business positioning.
Cryptography and product differentiation
Campmaster: You have said that there are too few top cryptography research institutions in China, and some teams are not recommended to touch cryptography. In fact, cryptography is a very large subject. In this discipline, what are the branches related to the blockchain?
Lu Yifan: In fact, it is involved, but symmetric encryption , asymmetric encryption , digital signature , and hashing are now more mature solutions in the blockchain . I think that the industry is not well solved. It is zero knowledge and full homomorphism . These things have high bottlenecks. Many cryptography professionals with years of work experience can't even understand it.
Campmaster: What do you think is the most important thing in your current job?
Lu Yifan: Differentiation. The basics are never differentiated, because I am a product manager, so the three words I care most about every day are "differentiation."
Technical things can always be found in the market, and what can be found in the market is not differentiated. Achieve differentiation.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Babbitt column | Last night, the central bank back pot 21 times, Xiao Zha rescue Libra hit the Chinese card
- The price of the currency has fallen sharply, the difficulty of mining has increased, and why is the bitcoin power not falling?
- Sharp interpretation of Zuckerberg’s testimony: avoiding heavy weight, not fundamentally answering why the approval of Facebook
- Why do I say that the encryption market is far from cool?
- A paper on how cryptocurrency reforms the traditional derivatives exchange clearing mechanism
- Digital currency of Chinese listed companies (middle)
- Ten experts took turns to accept Meng Yan's sharp question: How many points do you give to the development of the current blockchain?