How does DeFi cannibalize PoS security?
Foreword: Since the circulation of crypto assets on the chain is not required, it is more like a free market. Well, this means that if there is a better rate of return, assets will flow to where the rate of return is higher. Will this cause large-scale outflow of tokens from the equity pledge pool, thereby affecting the security of the chain? At present, many PoS chains adopt dynamic yield policies, which will be adjusted to a certain extent, and the token unlocking also has a long period. There is a certain buffer period here. Moreover, to push up the lending rate, it is also necessary to invest in pledged assets, and these attack costs will not be low. Can DeFi be used by attackers? To what extent is it available? More calculations are needed here, which cannot be easily achieved. Of course, this also puts higher requirements on the token economic model of the PoS chain. Designing a reasonable token economic model is the cornerstone of security. The author of this article is "Haseeb Qureshi", translated by "Coi" of the "Blue Fox Notes" community.
Today, on-chain lending has become the most popular application in the DeFi field. This year, more than 600 million US dollars of loans were provided on MakerDAO, Compound and dYdX. On-chain lending has the potential to overturn traditional mortgage lending. But it seems to be able to do more: it could undermine PoS consensus.
PoS is an alternative consensus algorithm for PoW. Its blockchain protects its security by collateralizing encrypted assets, rather than using hashing power. Many of the major networks released last year are PoS networks (Tezos, Algorand, Cosmos, etc.), and many more PoS networks will be launched next year.
The PoS system is secure when there are a large number of tokens actively pledged in the network. In most PoS algorithms, as long as 2/3 of all pledged assets are held by honest actors, the blockchain will be secure.
- New research: cost savings of $ 450 billion! What blockchain brings to supply chain management in Western Europe
- Crypto industry mergers and acquisitions observations: more than 350 transactions in the past 7 years, amounting to more than 4 billion U.S. dollars
- Director of Monetary Authority of Singapore talks about Ubin project: more than 40 cooperative institutions, looking forward to working with China
Now imagine, suppose you are an attacker trying to break through PoS systems. What would you do?
At a higher level, there are two attack paths: you can accumulate one-third of all outstanding equity, but this is very difficult and expensive. The second path is that you can persuade current equity pledgers to stop pledges and then take over much cheaper networks. The second method sounds attractive in principle, but how can you get current pledgers to escape equity pledges? There is an easy way: give them more attractive benefits elsewhere.
PoS is only effective when equity pledgers have the incentive to pledge, and they have an incentive to pledge only because the reward is large enough. However, if they can obtain higher returns from other places, then a rational equity pledger will lift the equity pledge of their assets and place them where they can earn higher returns. If this siphon sucks away assets from pledge of rights, the network will become unsafe.
Literally, on-chain borrowing competes directly with equity pledges, which means they compete directly with the security of the agreement. You may have an intuition, there is important interaction here to understand. But how to accurately analyze such a thing?
Simulated equity pledge game
The best way to model a complex economic system like Ethereum DeFi is through a technique called agent-based simulation. In agent-based simulations, you use a variety of strategies and risk profiles to model a large number of agents and then loosen them to each other. By observing the development of the emergency system (and playing the experiment thousands of times with different parameters), you can gain statistical confidence in the operation of the network in different scenarios.
Tarun Chitra from Gauntlet did exactly that in his latest paper, "Competitive Equilibrium Between Equity Pledge and On-chain Borrowing." In this article, he assumes that equity pledgers are economically rational and analyzes how on-chain lending interacts with PoS equity pledges. (Economic rationality means that each agent has its own asset portfolio, either lending, pledge of equity, holding, or trading, and each agent's risk profile is slightly different. They will restructure their investment asset portfolio Assets to maximize their risk-adjusted returns)
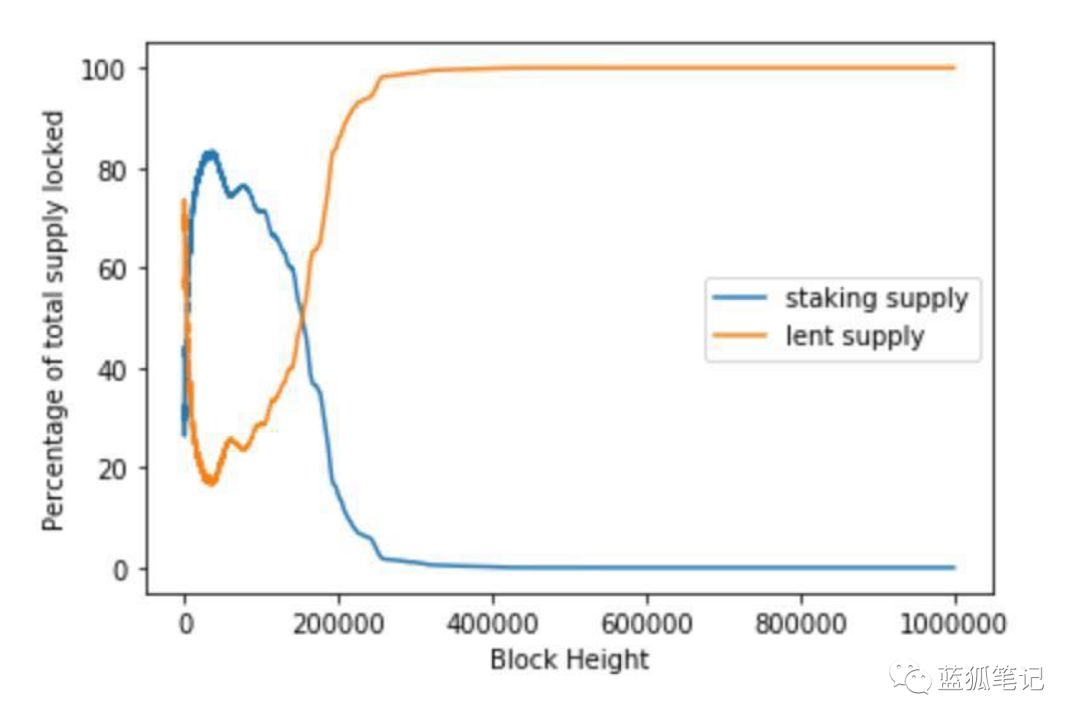 ETH Pledge Supply vs ETH Borrowing Supply Over Time
ETH Pledge Supply vs ETH Borrowing Supply Over Time
The above picture is just a single simulation. It assumes that Bitcoin-like deflationary block rewards, how the ETH (orange line) in Compound and the ETH (blue line) in pledge change over time.
The above picture is basically saying: Initially, most ETH holders pledged their ETH in equity, but as time passed, the block reward decreased, and the return on equity-pledged ETH decreased. Compared to lending on Compound, the Attractive, so almost everyone transfers their ETH into Compound (because it is randomly initialized, you can ignore the original flip between borrowing and pledge).
Tarun made several theoretically closed-form predictions and verified them with simulations. But the most important point is that the PoS chain cannot safely adopt a deflationary monetary policy. If the reward return of the PoS block decreases over time, then from a long-term equilibrium perspective, most of its assets will flow to borrowing rather than pledge. (Blue Fox Note: This conclusion is actually nothing new. Even PoW's monetary policy, once it is deflationary, needs to solve the problem of reducing block rewards, otherwise there will be security issues. In addition, many PoS chains such as Ethereum Currently, it takes the form of dynamic pledge rate. If the contemporary currency pledge is too low, its return will be improved. It has a balanced consideration. There is also a certain period of pledge withdrawal. It also needs to be considered. If the future network ecology is up, the transaction If the fee market can rise, the benefits of pledge are not limited to block rewards.)
But let's go one step further and what can an attacker do if they understand this?
If an attacker subsidizes the lending market on the chain and pays better long-term interest rates, this will drive the pledger out of equity pledges and turn tokens into the lending market. After that, once most of the on-chain pledged tokens flowed out, the attackers took advantage of it to control the barren pledged market. (Blue Fox Note: It is not easy to consider raising the interest rate of the lending market here. As tokens flood into the lending market, in order to increase the interest rate of the lending market, attackers need to mortgage more tokens to complete the lending. Generally, (Pledge rates are all over 100%, and the cost here won't be too low.)
Of course, in Compound, the way to reduce the borrowing rate is simply to borrow from the asset pool (Blue Fox Note: The original text was estimated to have a clerical error, which should be to raise the borrowing rate. Increasing borrowing is to increase demand, resulting in oversupply, so the interest rate rises). The risk model then automatically adjusts interest rates upwards. As attackers continue to borrow and interest rates rise, more and more pledgers will transfer tokens from the pledge pool to the lending market, so the security of PoS is gradually eroded.
This may lead to a snowball effect: as onlookers observe that the total amount of pledged tokens is decreasing, they are now trying to short ETH, further increasing the demand for loans on Compound. As you can imagine, pledged networks are like sweaters, and attackers are pulling a line: interest rates. As the attacker pulls, the sweater responds to pressure, and the drawn line becomes longer and longer. Eventually, the attacker pulls out the entire sweater line.

Of course, attackers need to borrow assets in Compound to raise interest rates, which means they must provide pledged assets to borrow. But if they use USDC or tokenized BTC to pledge, then when attacking the network, the attacker does not have ETH price risk exposure. (Blue Fox Note: This means that there is no need to worry about the liquidation problem caused by the decline in mortgage assets due to the decline in the value of ETH due to the attack)
Such a similar attack in the PoW chain will require a large number of short positions to be taken off-chain (Blue Fox Note: By shorting arbitrage, short positions need to be set). But in PoS, an attacker can perform such an attack, at the same time, avoid all price risks, do not require anyone's permission, and all can be completed on the chain.
This is a surprising result. It seems that DeFi and consensus are completely orthogonal, but the competitive lending market actually has a significant impact on the security of PoS. (Blue Fox Note: Orthogonal, in this article, it means independent of each other. Orthogonal English is orthogonal, which means vertical in geometry. In linear algebra, two vectors are orthogonal, meaning that the inner product is 0.
So what does this mean for PoS?
First, let's take a moment to reflect on: nonsense, Turing's complete blockchain is complex. Adding smart contracts to the blockchain seems to be purely a decision at the application layer. But smart contracts support complex markets like Compound, which interact with the underlying security of the chain in non-obvious ways.
We often talk about "layer1" and "layer2", but unlike the traditional computing OSI model, the blockchain is full of leaked abstractions. It also reminds us: we cannot always pretend that the blockchain is a closed system, and we cannot pretend that its incentive mechanism exists only in the agreement. The blockchain is too complex and interconnected to analyze in a vacuum. In this regard, little is known about the actual security of PoS.
As long as the PoS network is an open ecosystem, any lending market on the chain can erode its security by providing higher returns. In fact, even if the system does not directly support smart contracts (like Cosmos ATOM), if the pledged assets can be tokenized and cross-chain circulation is realized, the tokenized lending market on other chains may also have the same effect . (Blue Fox Note: The lending market of other chains will also affect the asset circulation of a certain chain.)
Worrying about this stupid?
We were talking about the case of active attacks, and perhaps the cost of capital is too high. However, even if no one actively initiates a malicious attack, it may happen similar to an active attack. It may just be that VC-funded projects subsidize their own interest rates, trying to compete with competitors, in the process unintentionally reducing cybersecurity. The end result is the same: a dangerous, unsafe consensus layer.
How to prevent PoS system?
At a higher level, the equity pledge network has two options to respond to: either force the on-chain lending market to limit its interest rate, or compete with the lending market to provide better returns to pledgers.
The first strategy is similar to capital controls. This is obviously impossible on a blockchain without permission. Even if regulation can be achieved, borrowers and lenders can simply build the same market off-chain, or use the interoperable chain to build the same market.
The only realistic way is to use dynamic monetary policy to provide competitive interest rates when necessary. Any fixed inflation mechanism is vulnerable to this type of attack, because attackers can know exactly how much money they need to subsidize to enter the lending market to eat away pledgers. (Blue Fox Note: Ethereum 2.0 adopts dynamic monetary policy)
This defense is similar to a central bank adjusting interest rates to achieve its economic goals. PoS networks must use their issuance rate as a tool to adapt to real-time market pressures.
In this sense, the foundation of Ethereum is actually good, because it does not promise any fixed monetary policy. But looking forward, all PoS networks must pay attention to this trade-off. Not only on-chain governance, but also off-chain governance methods can work, but if the PoS protocol wants to maintain long-term security, it must adopt an adaptive monetary policy.
Risk warning: All articles of Blue Fox Note can not be used as investment advice or recommendations. Investment is risky. Investment should consider personal risk tolerance. It is recommended to conduct in-depth inspection of the project and make good investment decisions.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Learn about Bitcoin's new technology innovations in this article, involving Layer 2, smart contracts, mining, and privacy
- Featured | Ten disasters in the history of Ethereum; how DeFi cannibalize PoS security
- QKL123 Research Report | ahr999 Indicator-Choosing Opportunities in Long-Term Trends
- New York regulator NYDFS issues SoL's virtual currency trading license BitLicense, giving consumers more options
- BTC daily line continues to close overcast, short-term retracement continues
- Monthly Report | Cryptocurrency Financing in November: STO and IEO with stagnation of ICO
- From technology open source to industry connection, Babbitt Academy and Weizhong Bank hold blockchain open course





