Key factors for the future large-scale adoption of DID and specific investment directions
Important factors for widespread DID adoption and investment opportunitiesAuthor: Avant Blockchain Capital
Translation: Qianwen, ChainCatcher
In the modern digital era, various kinds of data make up everyone’s digital identity. An individual’s identity can be viewed as legal identity, social identity, online identity, etc. Essentially, these identities form a unique data point network, usually stored in a centralized manner, interconnecting across devices, applications, and third-party services. This setup makes individuals unable to selectively share personal data, thus increasing the potential risks of data leakage and network threats. Most importantly, individual users do not have control over others’ access to this data.
Web3 marks a major step forward, inventing a new user-centric online market. This digital vision is built on the principles of blockchain technology, which can operate independently without any intermediary platform monopolizing user IDs, paving the way for a truly decentralized internet. In this new framework, everyone can have complete ownership of their own data.
- Is the father of ChatGPT’s ambition to solve AI threats with cryptocurrency by airdropping to one billion people grand or is he just trying to make a quick buck?
- Sui Explorer Browser User Manual: Quickly Understand the Development of the Network
- The Sustainable Path of Integrating Environment and Finance: Can ReFi Reshape Web3?
The beauty of Web3 is that it empowers users, allowing them to customize their profiles and securely store personal data in a single account. Imagine being able to use this account for all online activities, whether participating in social media networks or accessing cryptocurrency wallets. It can provide a seamless, user-centric experience, which is exactly what we expect from the future.
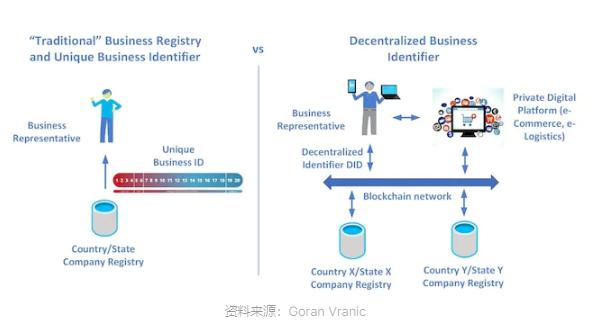
The Principles of DID
DID is a new digital identity verification method aimed at providing a secure, decentralized, and verifiable way to prove an individual’s online identity – it enables users to selectively disclose information, provide verifiable credentials, and simplify online interactions. The mechanism of decentralized identity relies on some form of decentralized storage to contain the individual’s decentralized identifier (DID) – which can be thought of as an identity vault that the user owns. This vault can take the form of an application, browser extension wallet, or smart contract, enabling users to forge decentralized identities and determine the level of access third-party service providers can have. In this model, users have exclusive ownership of relevant public and private keys.
DID startups have developed different technologies to address the traditional problems of DID, but no consensus has been reached so far. Some wallets have adopted alternative authentication methods, such as pairing users’ certificates with real-world verification data (such as biometrics) and ensuring their security on the blockchain. When authentication is required in Web3, users can sign transactions with their private keys or biometric data on decentralized identity authentication supported applications. Then, the service provider uses the shared decentralized identity to find the corresponding unique DID on the blockchain. This user-centric innovation returns power to users, safeguards personal data, and enhances digital experiences.
DID is a unique identifier (URI) that enables entities to create and control their identifiers in the digital world, with the following key attributes:
- No centralized identity registry
- Decentralized ledger or network (though not required)
- Permanent identifier
- Verifiable through cryptography
- Links a DID subject to a DID document
- Interoperable if compliant with W3C specifications
Above are the classic features of DID, though there are also other alternatives in the market.
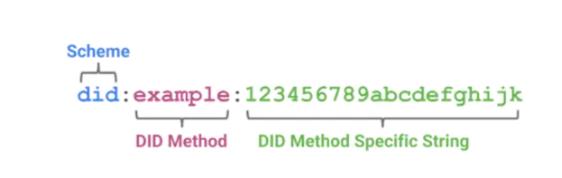
DID tags transactions with the association to a DID as a Uniform Resource Identifier (URI). “Methods” are the second part of the DID architecture. This involves a verifiable registry and an execution protocol that specifies how to look up a DID. This part contains many methods, mainly focusing on create, read, update, and delete procedures. The DID method operates similarly to how DNS addresses work in a compute environment. DID methods are typically associated with a verifiable data registry, which is a system that unifies DID, DID documents, and DID methods. Verifiable data registries come in various forms, such as trusted databases, decentralized databases, distributed ledgers, or government ID databases, such as DigiLocker.
In summary, DID includes a unique identifier used to retrieve the DID document associated with a DID subject. The document is stored on one or more decentralized storage platforms, such as IPFS or STORJ. The workflow is as follows:
- The DID subject decides to create a DID and share it with others (including the document itself);
- A timestamp is created;
- Metadata related to delegation and authorization;
- Validated proof with a public key;
- Using the DID service list;
- Verifying the integrity of the document using JSON-LD signatures (off-chain proof, i.e., on-chain proof held in a JSON file or smart contract).
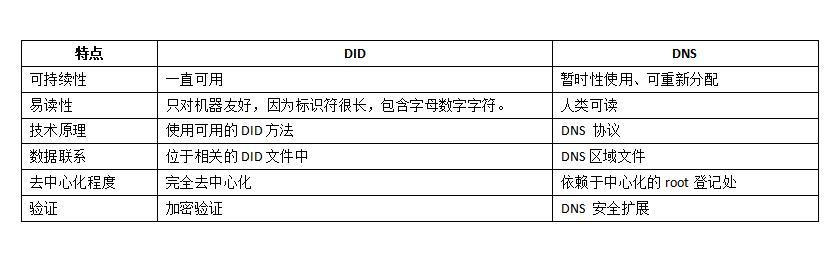
Below are the key differences between DNS and DID:
Key to DID Adoption
We believe that the adoption of DID will continue in the Web 3 world, but considering the usage challenges that users may face in many current solutions, end-users may not necessarily adopt pure on-chain DID solutions. Generally speaking, we believe the adoption of DID will be determined by the following key factors:
SDK
DID systems often come with an SDK that makes it easy for developers to onboard users to an identity system. In the past, interoperability and developer-friendliness of many DID systems have been lacking, hindering the adoption of these protocols. For example, the Lens protocol is a composable, decentralized social graph protocol that has developed the LensClient SDK, built with TypeScript, making interaction with the API easier. Systems that are able to develop intuitive and easy-to-use SDKs will see significantly higher adoption rates.
Compliance and Regulation
Governments and regulatory bodies are increasingly recognizing the importance of digital identity, privacy, and security. For example, the European Union’s General Data Protection Regulation (GDPR) is addressing the “right to be forgotten,” allowing users to request that companies remove all traces of their data from their systems. As a result, companies will face significant costs to restructure their data management systems to accommodate such requests. If regulation continues in this direction, sovereign DID identity methods will be an area of focus for companies, or else they may face consequences for non-compliance.
Artificial Intelligence
Artificial intelligence enables users to have a more personalized customer experience both in terms of content and consumption. This data layer should be composable and open. With the development of deepfakes and artificial intelligence, verified identities will become increasingly valuable. There must be efficient ways to establish relationships between valid identities and content.
Interoperability Needs
DID systems were designed with interoperability in mind, allowing for seamless communication between different identity systems. The value of this technology will increase as it connects with other systems. Various forms of reputation systems will emerge to adapt to more seamless integration, leading to greater adoption in real-life scenarios.
Some General Technology Directions Worth Investing In
Authentication
Authentication involves using cryptographic methods to verify ownership and control of DIDs. This process often relies on decentralized public key infrastructure (DPKI), rather than centralized certificate authorities. Instead, DID owners generate their own public-private key pairs, allowing them to securely prove their identity and authenticate themselves without relying on third parties. This approach enhances the security, privacy, and user autonomy of digital identity management.
Aliases and ID Aggregators
Aliases and ID aggregators are important components of the DID ecosystem. Aliases provide human-readable identifiers that can be associated with DIDs, making it easier for users to manage and share their decentralized identities. These aliases can be linked to DIDs while protecting privacy and remaining under the control of the user. ID aggregators act as intermediaries and facilitate the discovery, exchange, and verification of identity data and credentials within the DID ecosystem. They can help users manage their various DIDs and related data across different environments and platforms. By using ID aggregators, users can maintain the privacy and security of their digital identities while simplifying their interactions with various online services and applications.
Proof of Personhood
Proof of personhood usually refers to an encryption mechanism to verify that someone is a unique individual, ensuring that the verified object is a single, unique person. This is often done to prevent Sybil attacks, where an entity creates multiple false identities to gain more influence or manipulate the system. Proof of personhood does not necessarily need to reveal personal information, but rather focuses on ensuring that each participant is a unique individual.
There are two types of proof of personhood projects:
Federated identity projects: These solutions use fundamentally trusted third parties to issue valid identities. Currently, applications are more inclined to use existing identities rather than issue new ones, so the market prefers global federated identity projects.
Emerging identity projects: Emerging identities come from existing data structures, such as social graphs or user behavior. Emerging identities can be obtained by integrating existing credentials from actions taken or calculating user connectivity in social groups.
Two Types of Proofs:
Off-chain proof: In this arrangement, the proof is transformed into a JSON file, stored off-chain (preferably on a decentralized cloud storage platform, such as IPFS or Swarm). But the hash value of the JSON file is stored on the chain and linked to the DID via the on-chain registry. The relevant DID can be the issuer or recipient’s DID of the proof.
On-chain proof: The on-chain proof is stored in an Ethereum blockchain smart contract. The smart contract (as a registry) will map the proof to the corresponding decentralized identifier (public key) on the chain.
Soul-Binding Tokens
Soul-binding tokens are another solution that could be used as a new way to represent and manage a person’s digital identity. Soul-binding tokens should be unique, non-transferable, and ensure that each token is permanently associated with a specific individual identity. This will prevent tokens from being traded, sold, or stolen. Soul-binding tokens should be designed to seamlessly integrate with existing DID infrastructure, including decentralized identifiers (DIDs), verifiable credentials, and decentralized key management systems. Soul-binding tokens could be used to represent various aspects of a person’s identity, such as interests, achievements, or affiliations. This will enable users to personalize their digital identities and give them meaning.
Alternatives to Wallets
In the SSI community, there are many known DID methods, but most of them require users to have a digital identity wallet that saves a seed (private key). Using a digital wallet can be tricky for beginners because they have to install wallet software on their laptop or phone. An alternative is to reduce the dependency on wallets and facilitate the transition from Web 2 to Web 3 through smart contracts, among other means.
DID Issuance and Tooling
DID issuance and tooling refer to the process and technology used to create, manage, and use decentralized identifiers (DIDs). DID issuance involves generating unique, persistent, and verifiable identifiers that can be associated in a decentralized way with individuals, organizations, or objects without relying on centralized institutions. DID tooling includes a range of software and hardware solutions that facilitate key management, authentication, and interaction with decentralized identity ecosystems. These tools can include wallets, SDKs, APIs, and libraries to simplify the integration of DIDs into applications and services. They enable users to securely manage their digital identities and interact with various Web3 platforms, bringing greater privacy, security, and user autonomy to the digital world.
Outlook
We believe that the adoption of DIDs will continue in the Web 3 world, and that opportunities for certain key technologies (listed below) are the most promising. We focus on the following two technologies in particular: 1) those that can lower the barrier to entry for first-time users, and 2) those that have the potential to become core layers for verification service providers. Specifically, we have the following recommendations:
New Information Distribution Protocol
These tools can better define who we are through data analysis of DIDs. Sovereign identity systems supported by new IDPs can not only authenticate users, but also enable users to control how, when, and where their data is used. In an increasingly complex digital ecosystem, the ability for different systems to work together (interoperability) is critical. New IDPs that promote this interoperability may be highly attractive. (e.g., RSS3, 0xScope).
On-Chain Passports
Compared to other authentication systems (such as traditional authentication methods), on-chain passports provide a more comprehensive, secure, and user-centric solution. Investing in this technology means investing in a solution that not only meets current security needs but also aligns with the direction of digital identity management. Verification service providers such as Gitcoin Blockingss and link3.to are good examples.
Super ID
We should look for “Super ID” in the DID world, which will encourage us to find the most widely recognized and adopted integrators. For example, SBlockingceID, Dmail, ENS, Worldcoin.
Alternatives to Tools and Wallets
One of the main obstacles to adopting the DID approach is still the high learning curve and difficulty in connecting Web2 and Web3 users. Currently, there are only over 200 million Web3 users, while Instagram has over 2 billion users. The team building products that can simplify or skip the entire wallet onboarding experience (seed phrases or KYC) will help further adoption of DID and Web 3.
In addition, building complete open-source tools and interoperability standards, decomposing authentication, and rebuilding from first principles will bring new DID solutions. Tooling projects will make more DID solutions appear.
Decentralized digital identity as a breakthrough technology can further promote the Web3 revolution. This innovation enables users to seamlessly browse all their accounts without having to remember multiple usernames and passwords, and to obtain higher security and data protection in the metaverse. At the same time, it enables companies to provide personalized services to users while protecting their privacy. The adoption of this technology may be earlier than expected, as emerging startups and mature companies have integrated systems to supervise the validation, security, and management of identity and access rights.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- What is the purpose of the world coin that features iris authentication, global airdrops, and the creator of ChatGPT?
- Can the combination of decentralized derivative exchanges and account abstraction open up the next incremental entry point?
- US House Stablecoin Hearing: State and Federal Regulatory Authority Dispute Focus of Both Parties
- Conversation with Sui Developer Relations Manager: How to start developing on Sui from scratch?
- Analysis of Dune: A powerful and practical free on-chain analysis tool
- Will modularization become the ultimate solution for cross-chain?
- Themis Protocol: An all-in-one DeFi platform, powering the full growth of Filecoin




