Interpreting Namada A Modular Privacy Solution Serving the Multi-Chain Ecosystem
Interpreting Namada A Privacy Solution for Multi-Chain EcosystemsWritten by: Namada
Translated by: Deep Tide TechFlow
Historically, the architecture of decentralized systems has forced users to commit to using specific cryptocurrencies, chains, or dApps to access privacy features.

- RWA Potential Exploration The Next Large-Scale Application Track after Stablecoins?
- UBI Development History The Combination of Utopia and Fantasy
- Wall Street Journal Binance Empire on the Verge of Collapse
While functional, this independent structure inherently limits the scalability and extensibility of privacy solutions. Namada disrupts this status quo by introducing the concept of “modular privacy”, a bold reconfiguration aimed at expanding the applicability of privacy features in decentralized systems.
Namada Architecture Review
The Namada protocol operates as a layer 1 solution consisting of multiple components, but the cornerstone that enables modular privacy is two key functionalities: Unified Shielded Set (USS) and Shielded Actions (SA). These elements represent a reimagining of privacy implementation across chains and the wider crypto space, rather than just incremental upgrades.
Namada’s Unified Shielded Set (USS)
Traditionally, in the realm of privacy, shielded sets are specific to certain assets, just as Zcash’s Sapling architecture only supports ZEC. The larger the shielded set for individual assets, the stronger the privacy guarantee for each user. However, decentralizing privacy in a single asset pool diminishes the privacy guarantee for low-volume assets (such as NFTs) due to restrictions on inputs and outputs.
Namada overcomes these limitations with its Multi-Asset Shielded Pool (MASP), an evolution of Zcash Sapling technology. This forms the USS, an asset-agnostic unified shielded set that can accommodate a wide range of assets. As a result, users can privacy-enable assets from non-private chains (such as Cosmos Hub, Osmosis, Stargaze, or Noble).
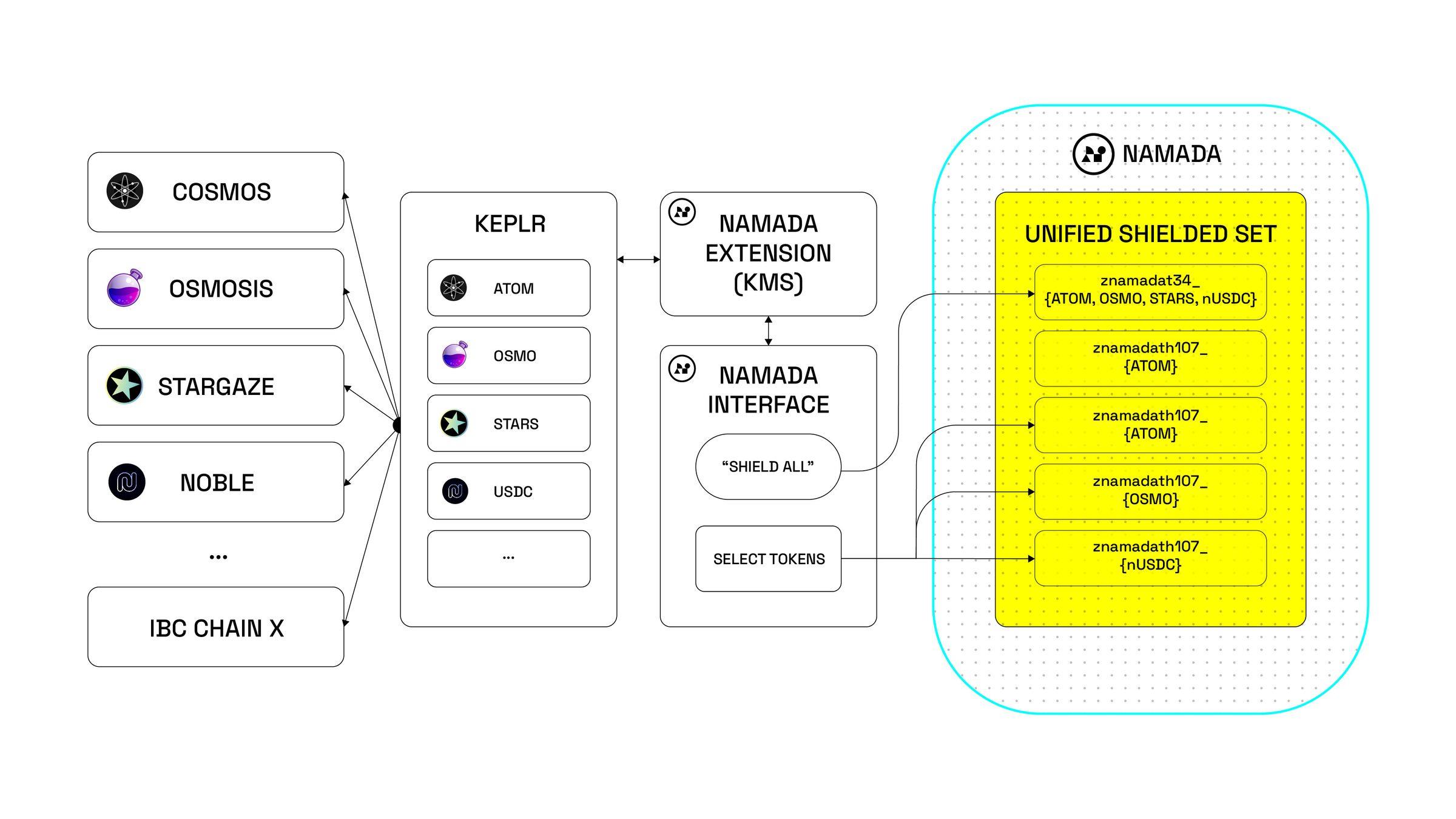
To optimize the user experience, especially for users interacting through Cosmos and IBC, Namada has developed browser extensions and a web interface. These platforms are fully compatible with Keplr key management and feature Namada-specific functionalities.
Therefore, USS provides Zcash-like privacy for all IBC tokens. Additionally, unlike traditional privacy models where tokens are typically locked, USS allows tokens to flow and transfer within the shielded set.
To incentivize contributions to the shielded set and enhance user privacy, USS incorporates shielded set rewards, a unique feature of the MASP/CC circuit. Namada governance determines which tokens are eligible for shielded set rewards and the target amount.
Shielded Actions
The second cornerstone of Namada’s modular privacy is Shielded Actions (SA). This feature not only empowers users to perform transactions but also supports complex, carefully orchestrated operations across multiple blockchains, app chains, and dApps while maintaining privacy through USS. Its purpose is to provide users with the ability to leverage more functionalities offered by Namada itself through a unified interface that protects privacy.
The design of SA is very refined and provides a new layer of automation in the user interface. This feature allows users to perform multiple interactions in parallel, greatly reducing complexity for end users. This design is in line with the innovation around cross-chain accounts (ICS-27) in the IBC and Cosmos environment.
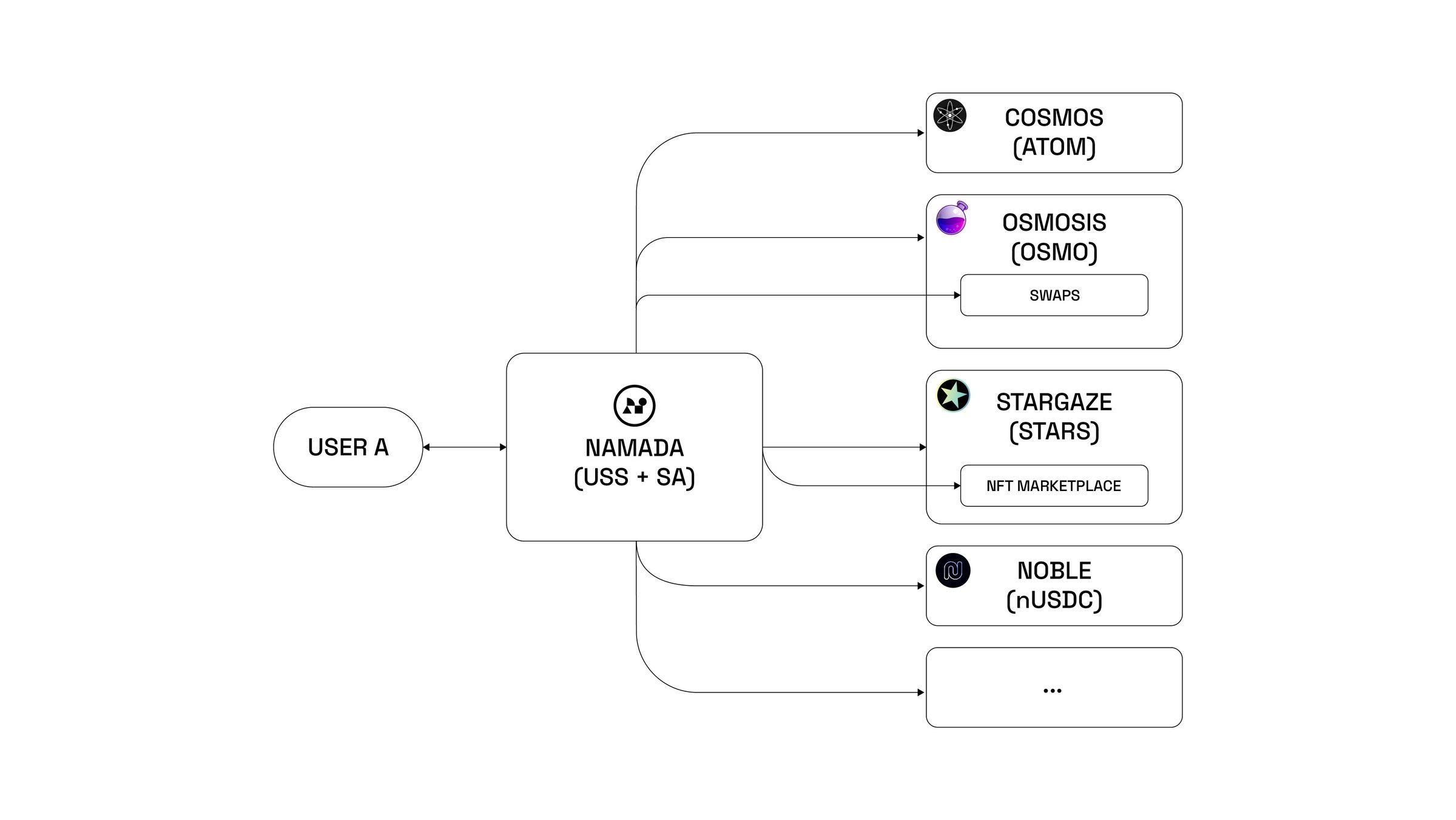
The starting point of any shielding operation is centralized in a unified shielding set. This ensures that user identities remain shielded, making it extremely difficult for external observers to determine the origin of the shielding operation. All they can see is that an operation is initiated from Namada USS. The rule is simple: the larger the USS, the stronger the privacy mechanism.
To interact with applications on other chains, users do not sign simple transfers, but sign a series of instructions from Namada. This opens up a range of use cases, such as:
Shielded staking on Cosmos: Users can unshield ATOM, transfer it to the Cosmos Hub, and then stake it.
Shielded swapping on Osmosis: SA allows users to unshield OSMO tokens, transfer them to Osmosis, swap the tokens to get ATOM, then move the newly acquired ATOM to the Cosmos Hub, and finally return them to Namada where they are reshielded. The whole process takes only a few seconds.
Posting shielded data on Celestia: Users can unshield TIA tokens, then transfer TIA and specific data to Celestia, where they can post the data and handle fees, all done under privacy protection.
And so on.
Although SA utilizes IBC not only for transfers, it is important to note that any interactions on IBC are transparent (they reveal the transaction graph). To maximize privacy between Cosmos and IBC, it is best to always keep assets shielded in USS unless needed for a particular operation, and avoid using easily linkable amounts on IBC.
SA is key to modular privacy as it allows users to continue interacting privately with the tokens, applications, and chains they are currently using without requiring any changes to the chains or applications.
Summary
Lastly, Namada’s modular privacy is not constrained by Cosmos and the cross-chain ecosystem. The architecture of this protocol is scalable and ready to seamlessly integrate into various blockchain domains.
The implementation of Namada’s trustless bidirectional Ethereum cross-chain bridge serves as concrete evidence of its adaptability, facilitating the expansion of Namada’s modular privacy to tokens and dApps beyond its underlying ecosystem.
As blockchain technology matures, the demand for robust, scalable, and private interactions becomes increasingly urgent. Namada not only adapts to this future but is also helping shape it.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- A Shenzhen University alumnus who graduated just a year ago donated 50 million yuan to his alma mater, and his first bucket of gold may have come from cryptocurrency.
- Binance He Yi’s Open Letter Perseverance and a Light Boat Will Cross Ten Thousand Mountains
- Andre Cronje The Lone Ranger’s Network Odyssey
- Popular Token Simple Rating CRV Achieves the Best Performance, OP Only Has Speculative Value
- Mixin’s aftermath of being stolen about 200 million US dollars Compensation plan includes bonds, Li Xiaolai’s Weibo questioned Where is the users’ money?
- Market value doubled within a year, will Azuki be knocked down How much longer can Pudgy Pengunis remain popular?
- Hot discussions among peers, uncovering the little-known stories of market maker DWF Labs and Lianchuang.





